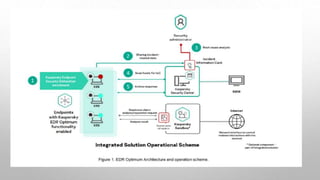
This document discusses malware analysis tools used by Team 8. It defines malware analysis and the different types - static and dynamic. It describes use cases for malware analysis like detection and research. It then discusses technological solutions for detecting and preventing firewall malware. It outlines the endpoint security stack and how endpoints are protected. It defines a sandbox and how it is used to detect malware behavior in a virtual machine. Finally, it lists some tools that can be used for malware analysis.