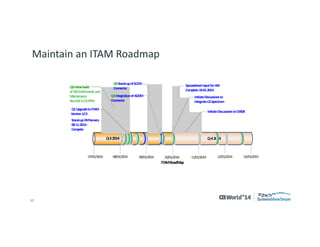
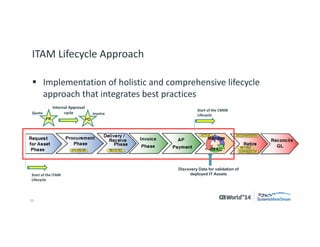
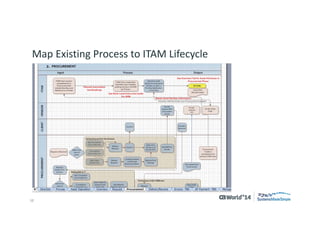
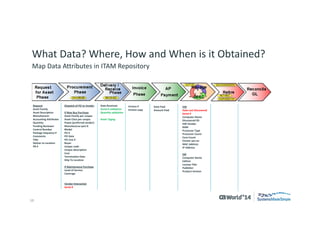
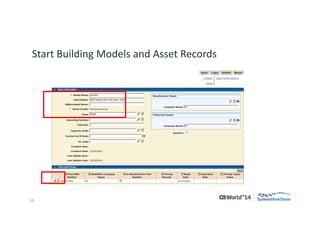
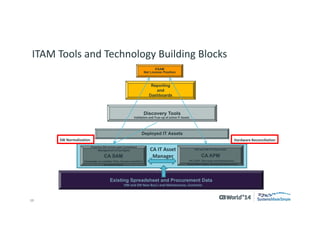
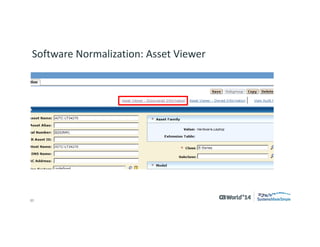
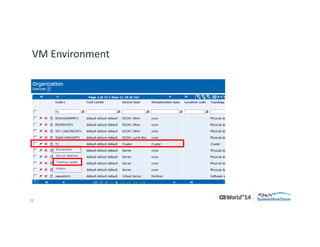
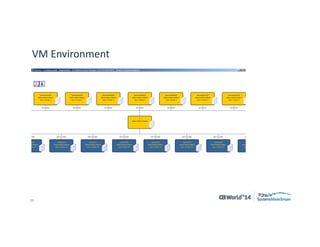
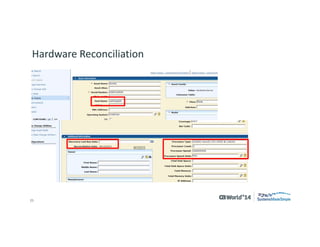
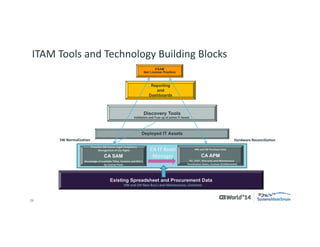
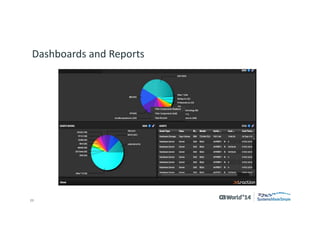
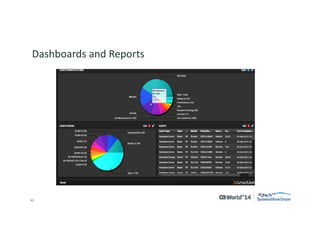
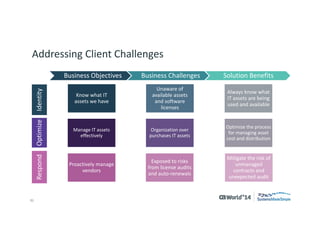
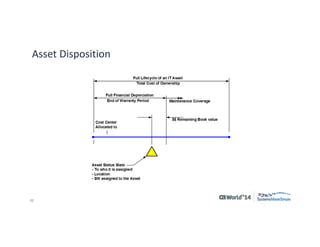
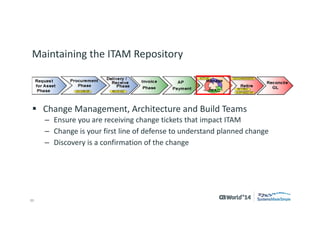
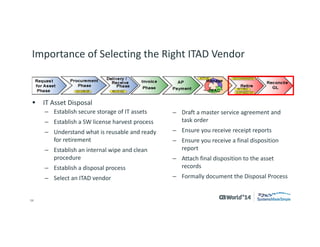
The document outlines strategies for effective hardware and software asset management in complex IT environments, emphasizing a proactive approach to managing IT assets and planning for future needs. It details a comprehensive lifecycle approach and tactical execution that includes stakeholder collaboration, data management, integration of various organizational functions, and asset tracking techniques. Key objectives include optimizing asset management processes, ensuring compliance, and adapting to changes through a well-maintained IT asset management repository.