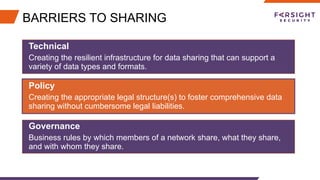
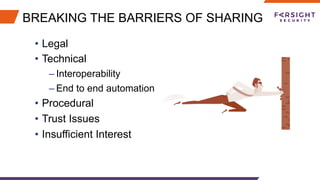
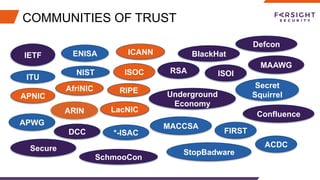
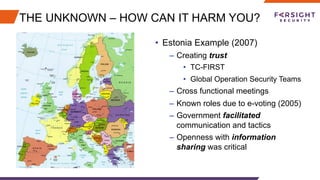
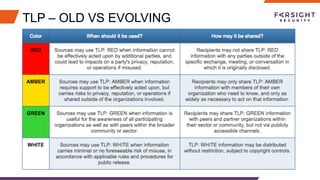
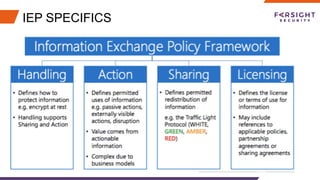
The document discusses the challenges and barriers to information sharing in cybersecurity, emphasizing the need for resilience in data exchange and the establishment of legal and governance frameworks. It highlights the role of various communities and initiatives aimed at promoting trust and collaboration, as well as the importance of evolving standards to facilitate effective information sharing. Additionally, it underscores the need for organizations to build trust and define clear roles in incident response, while addressing complexities related to privacy laws and data protection.