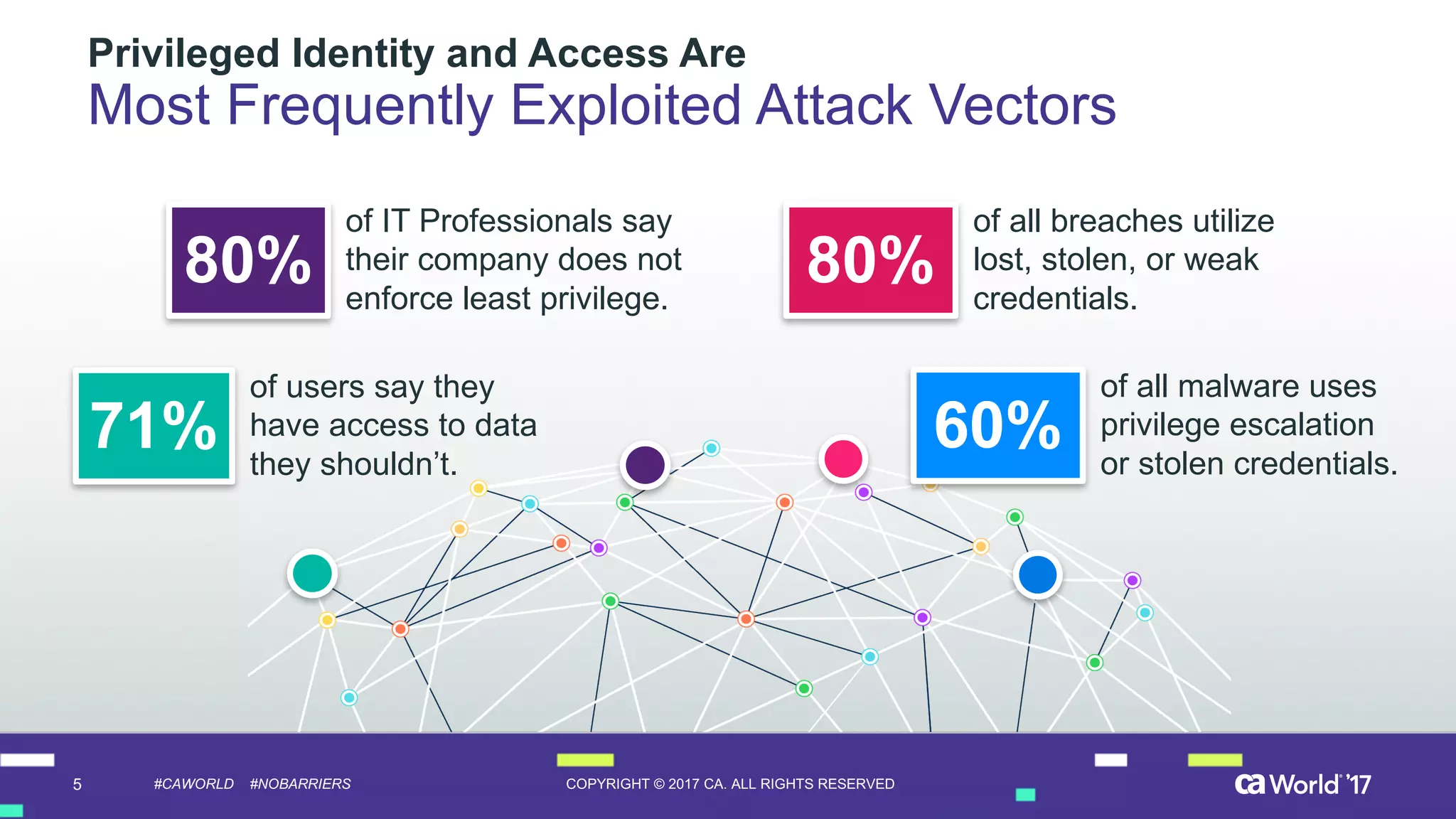
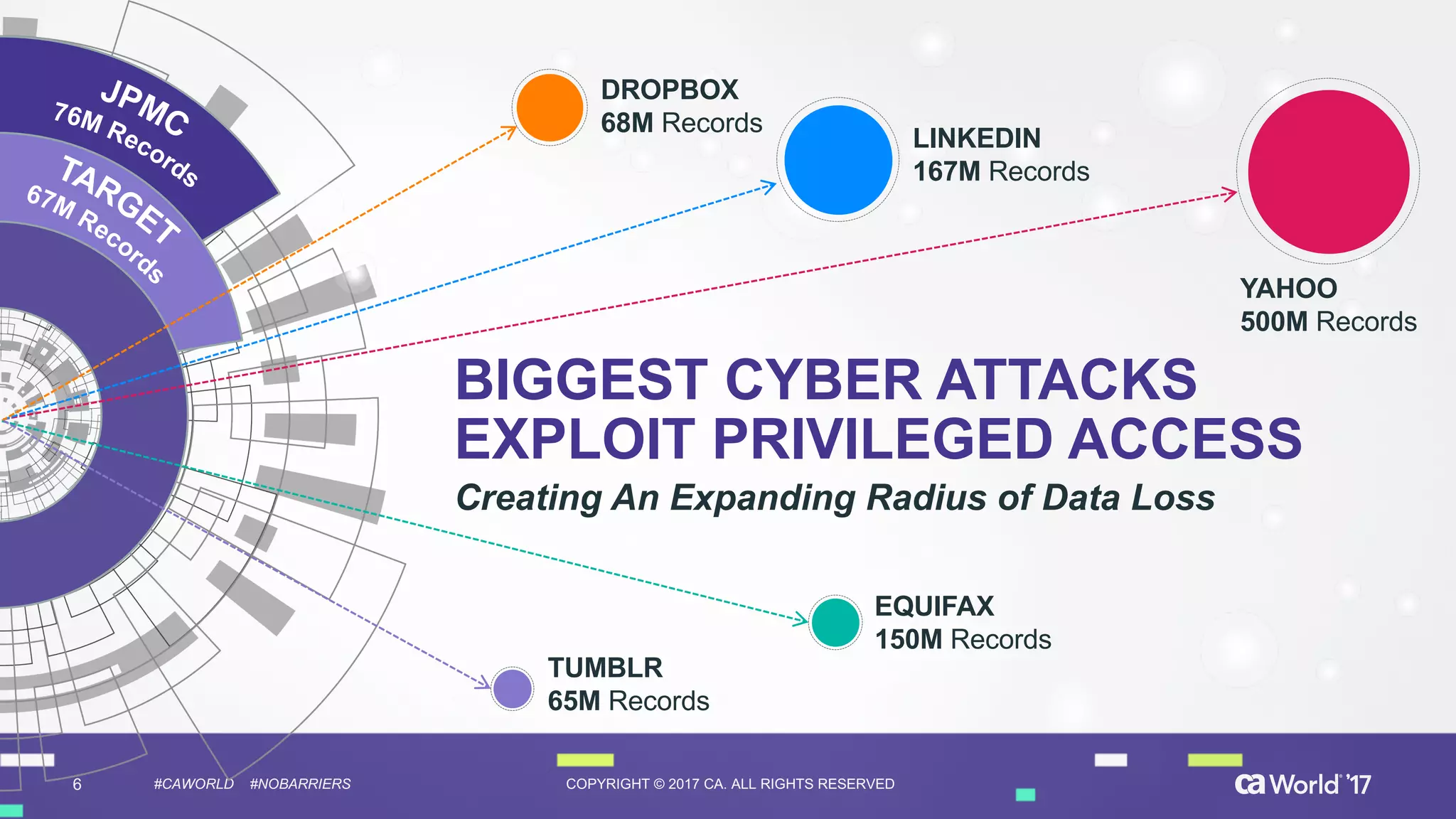
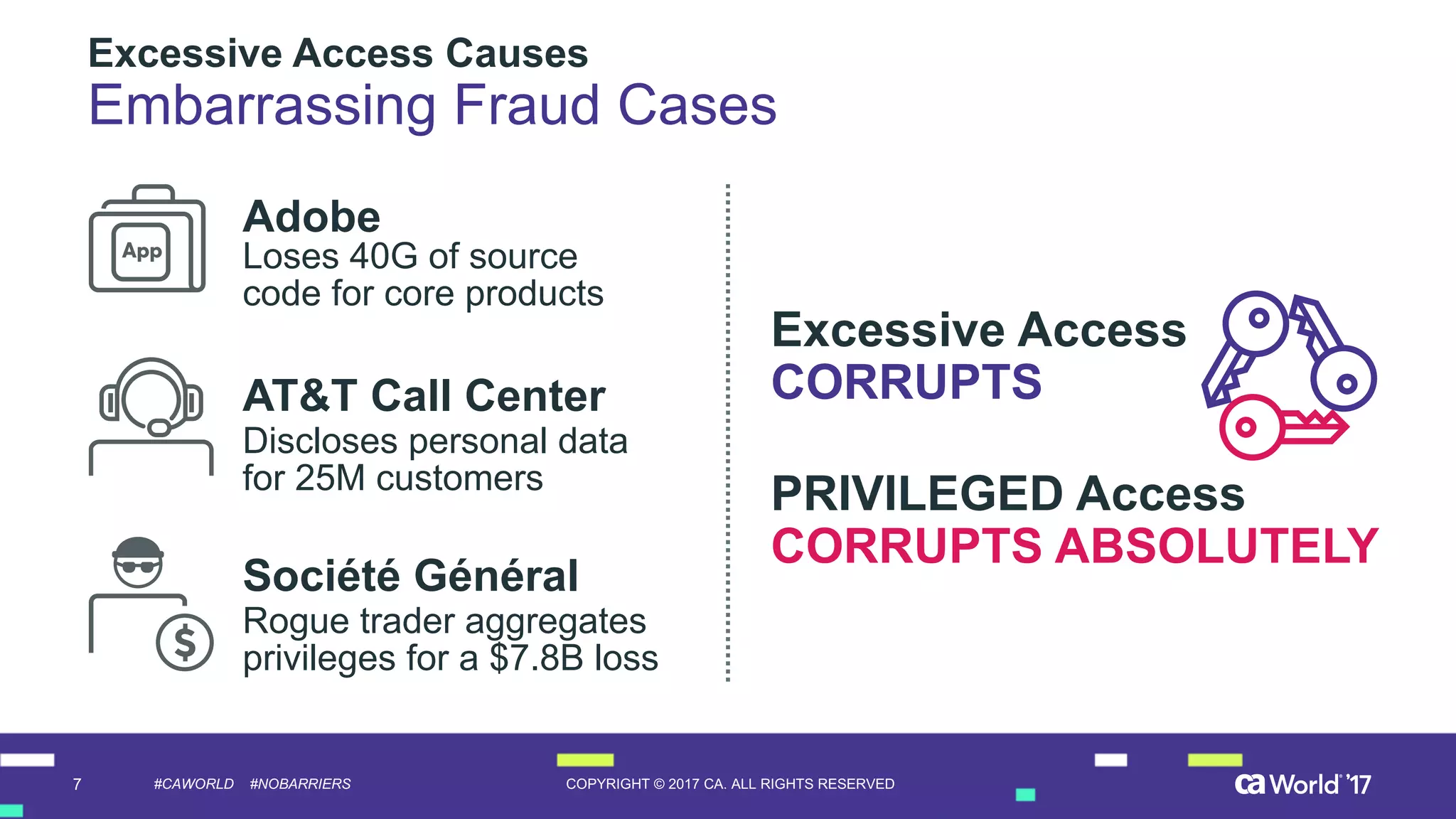
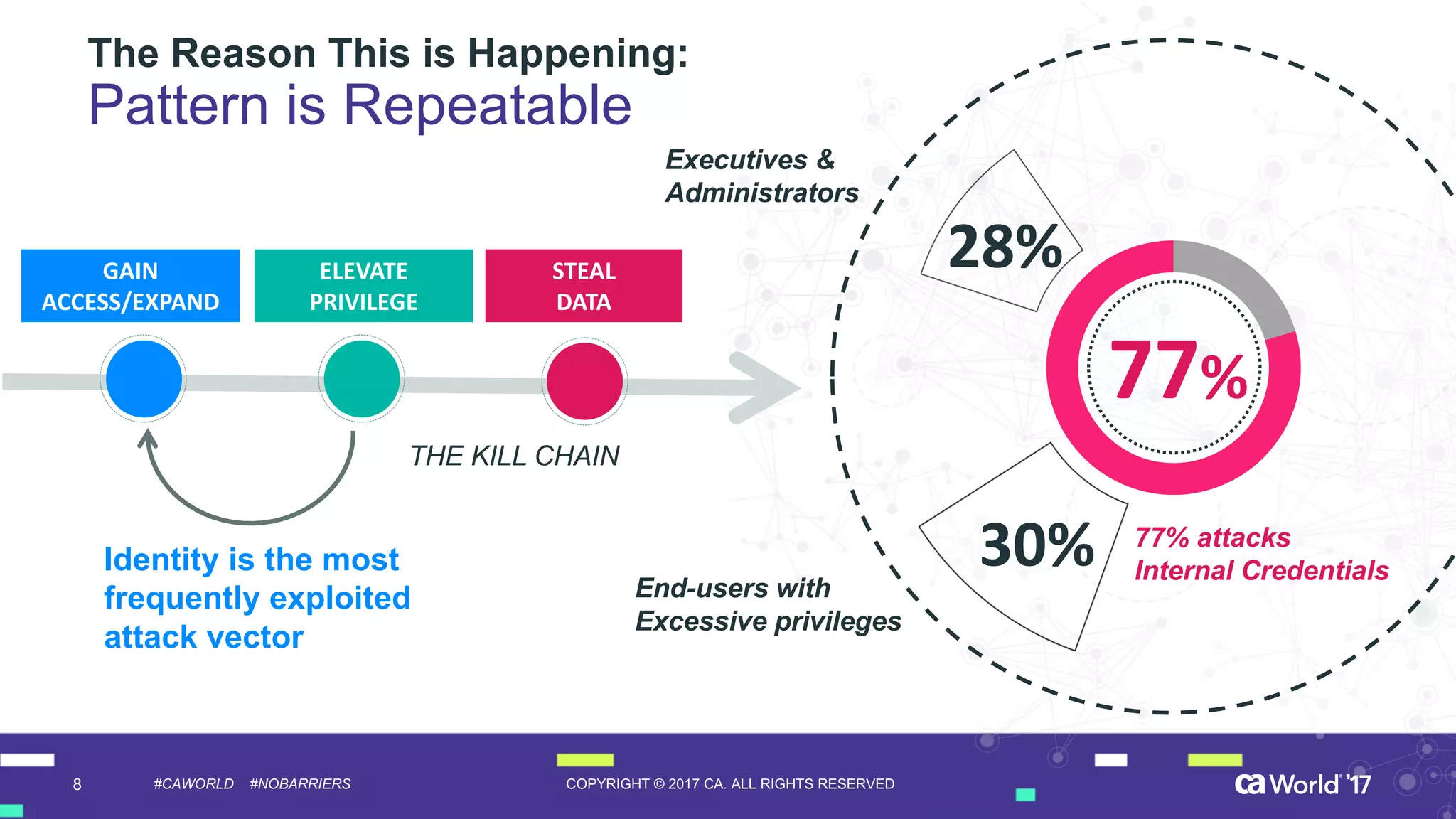
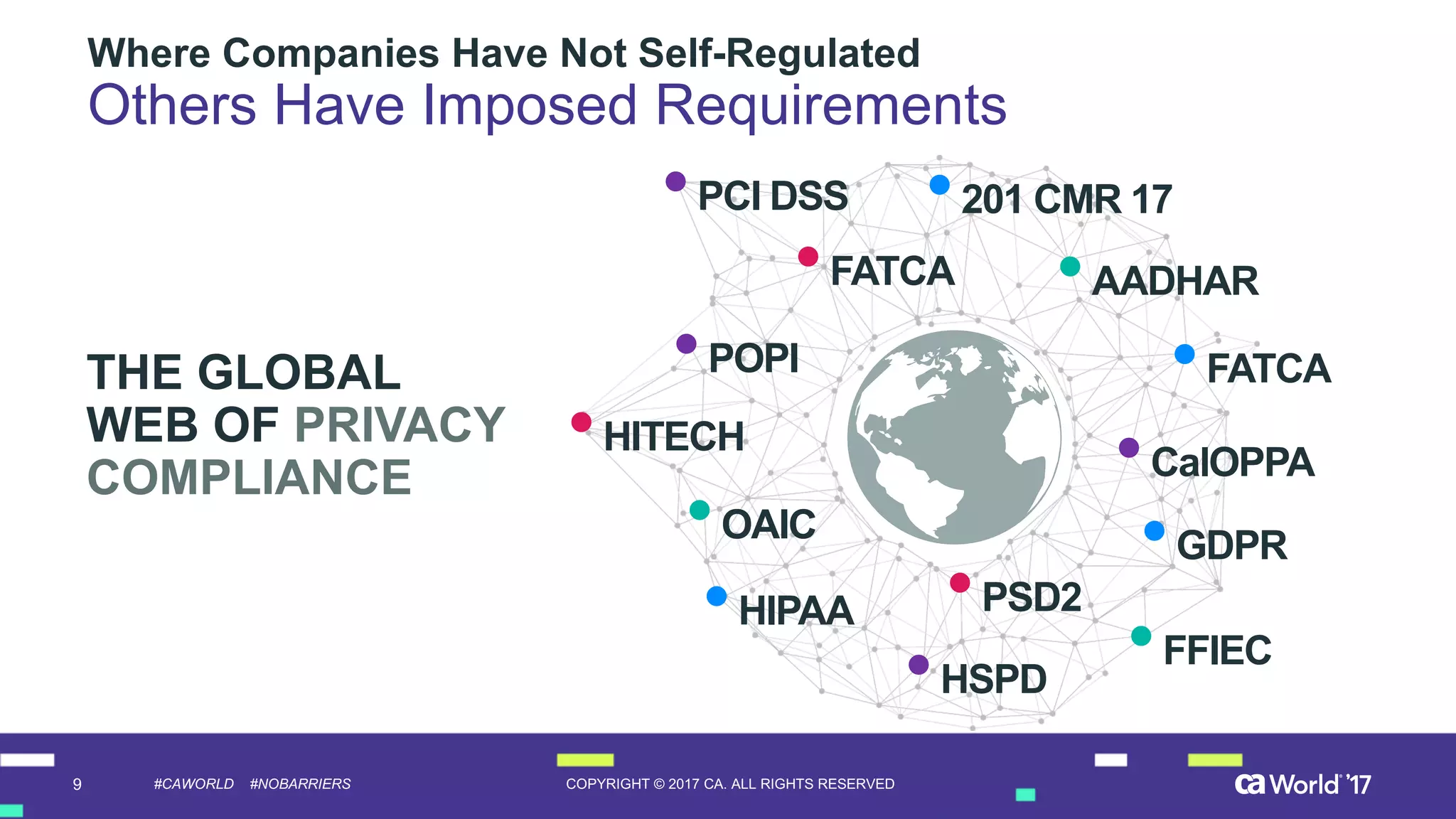
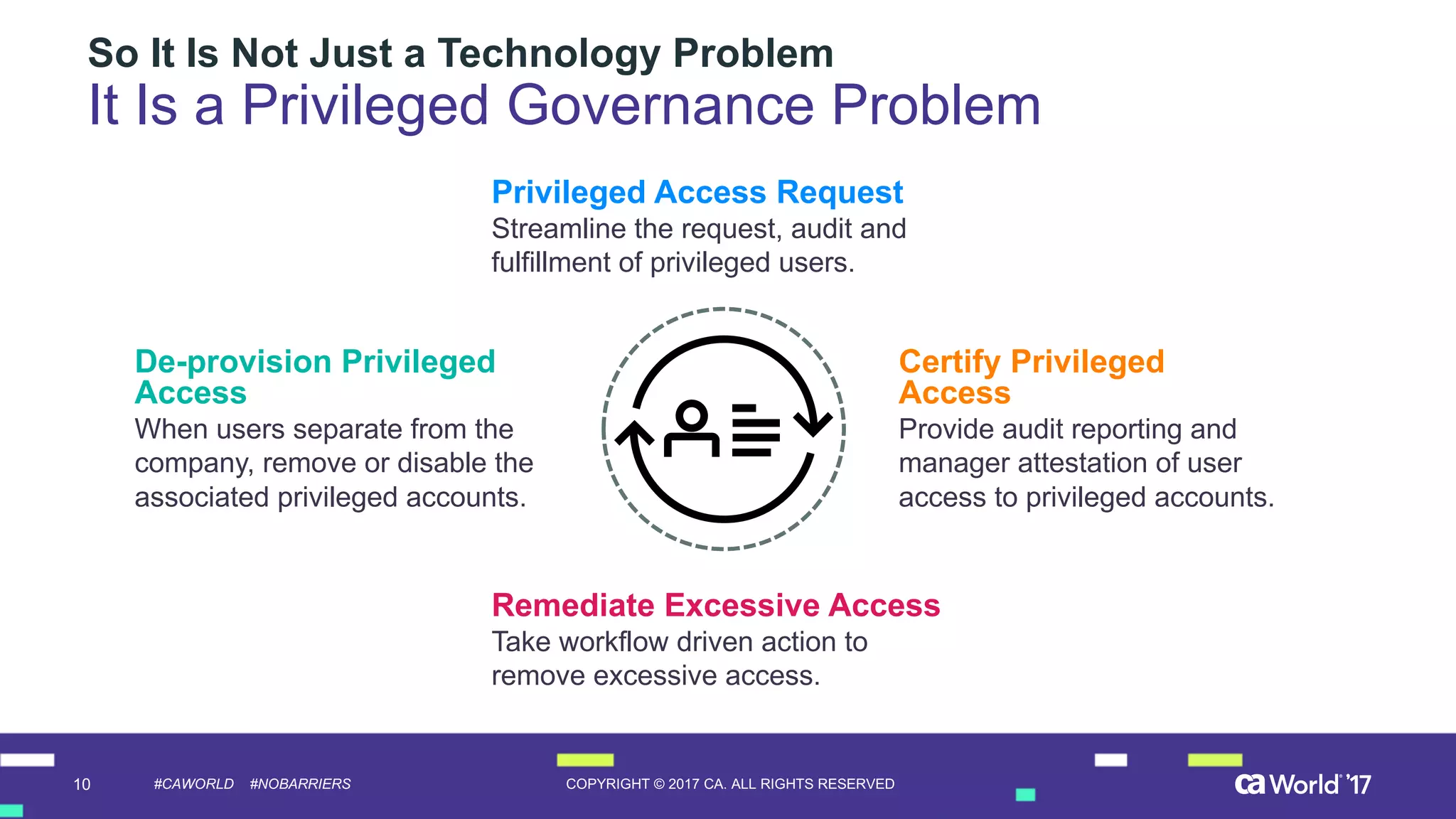
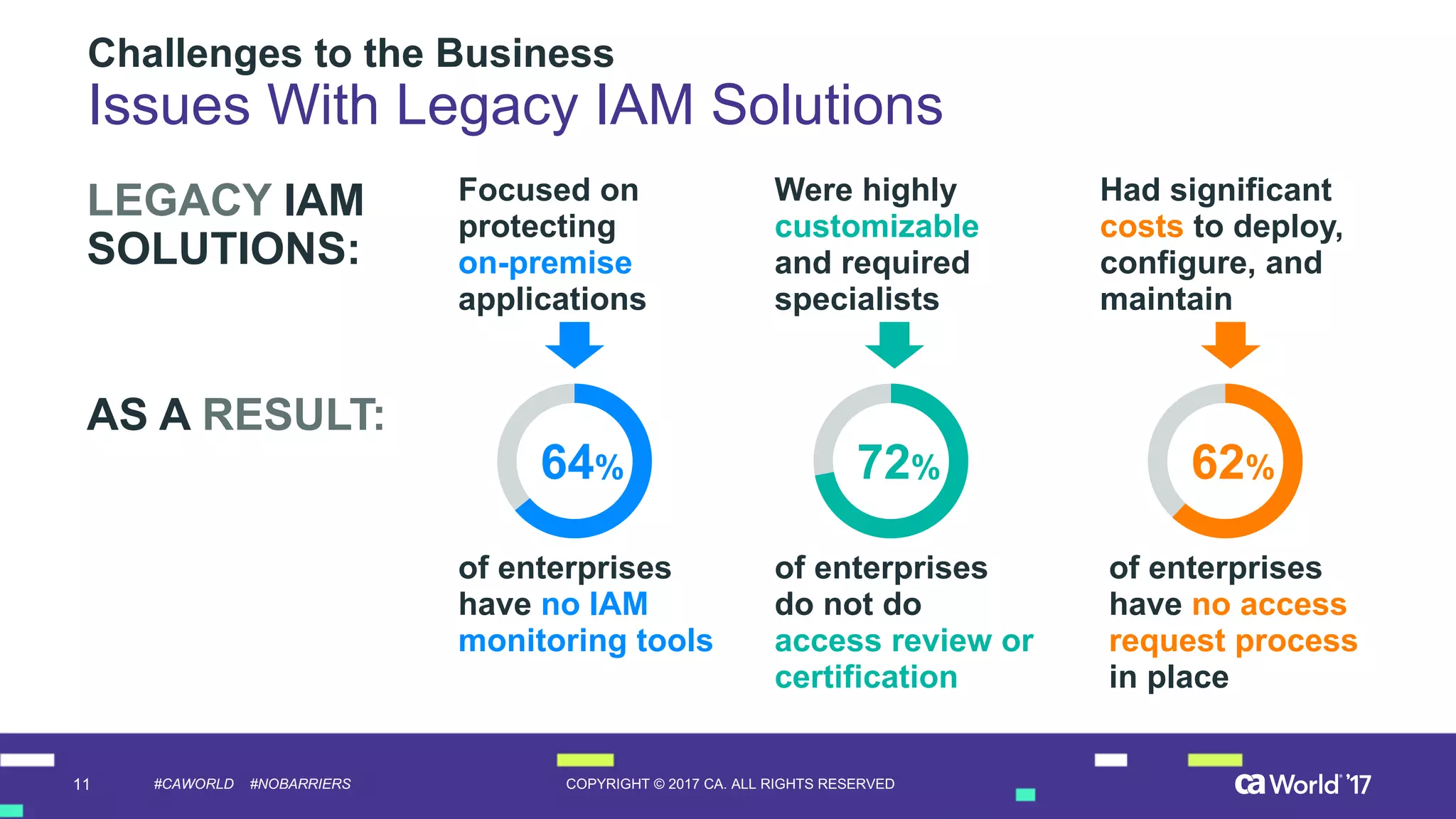
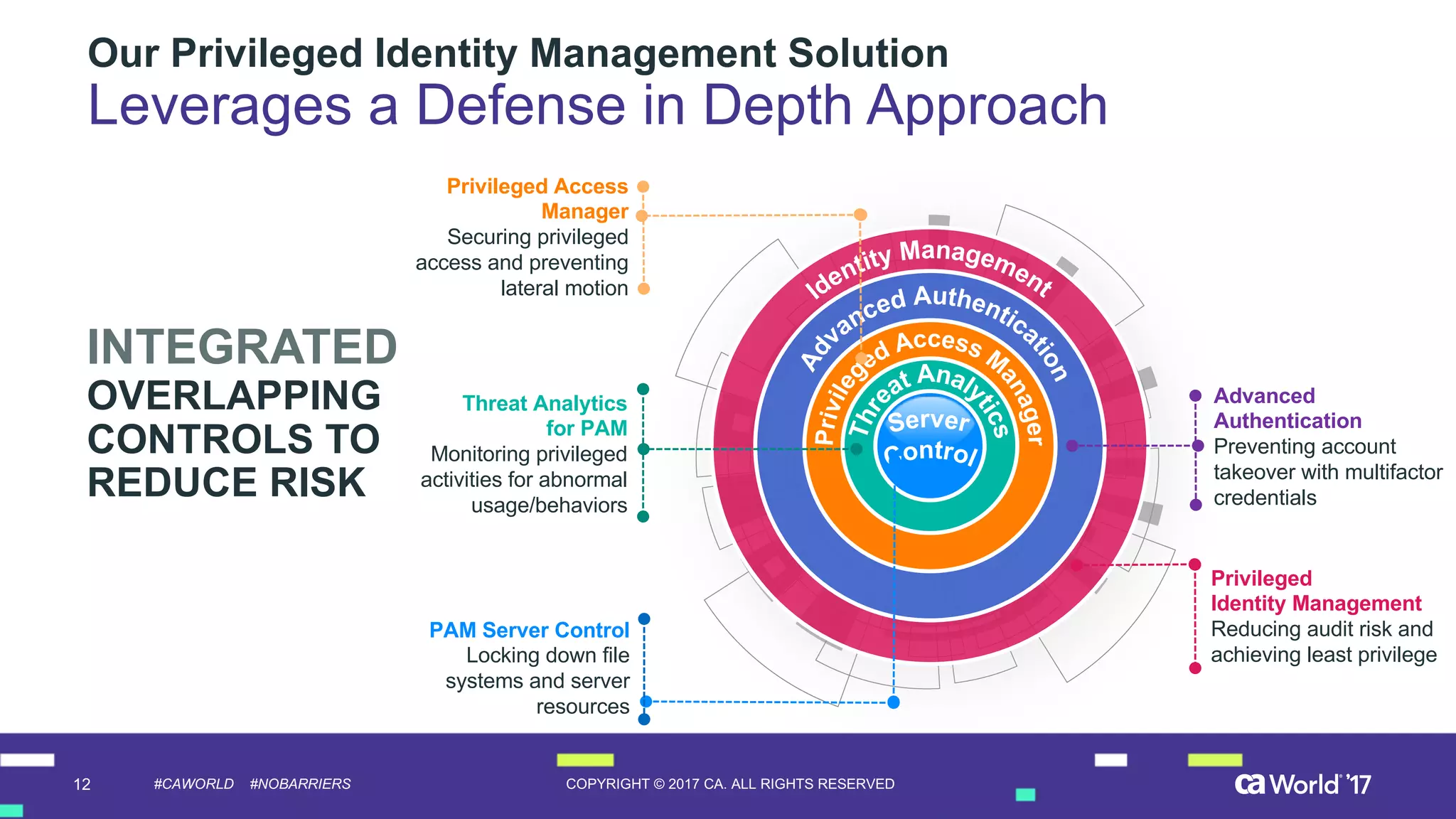
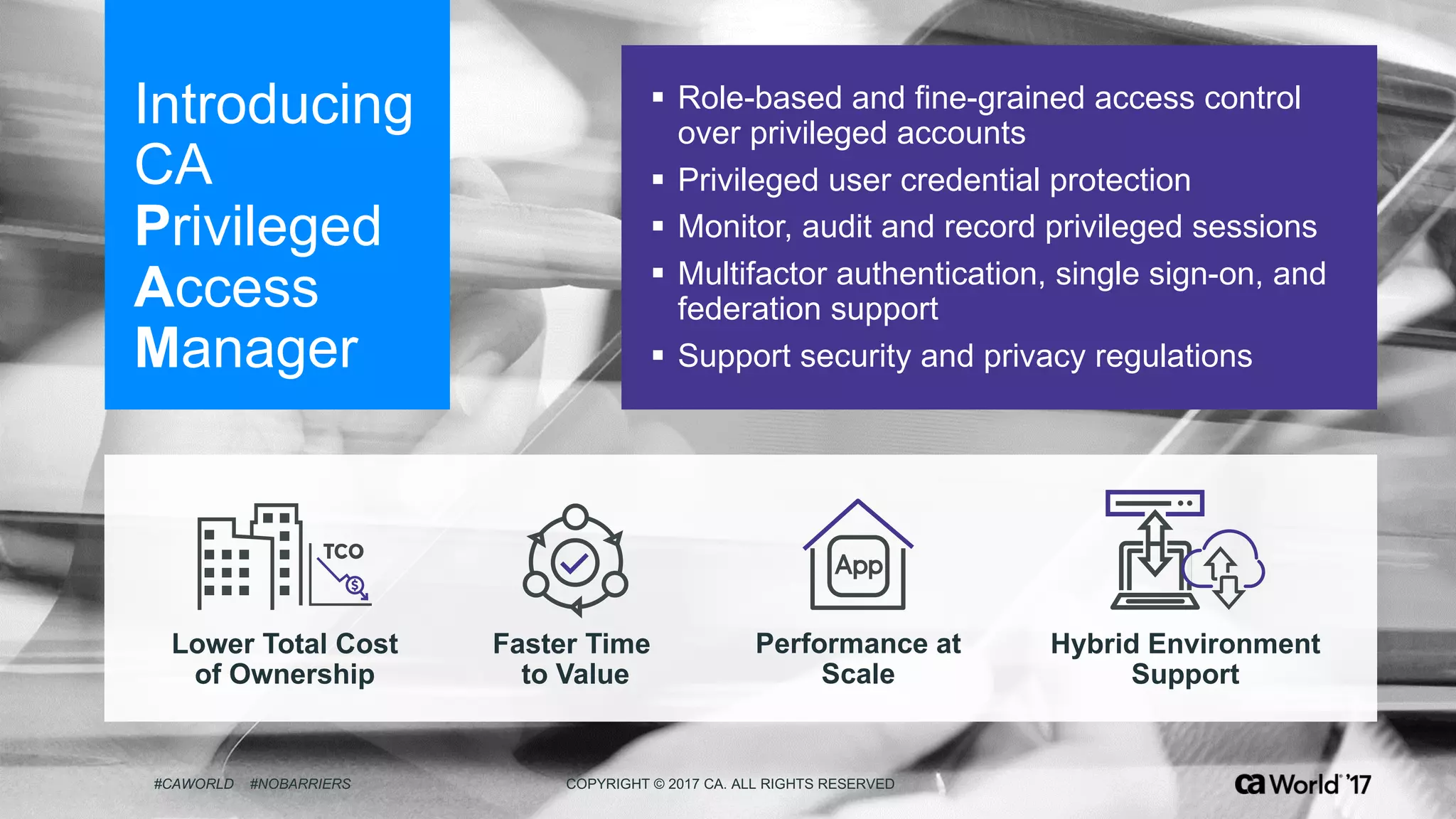
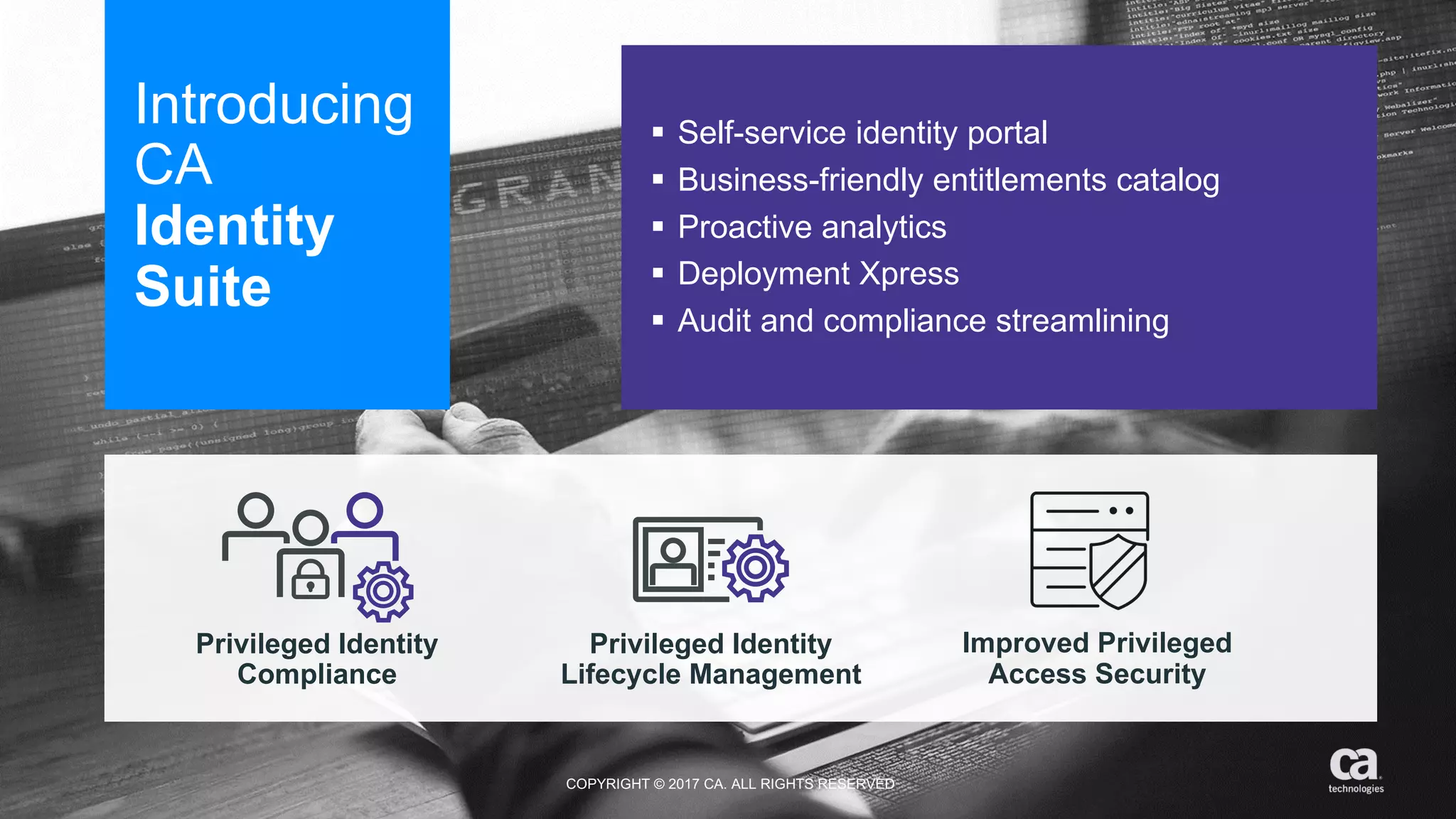
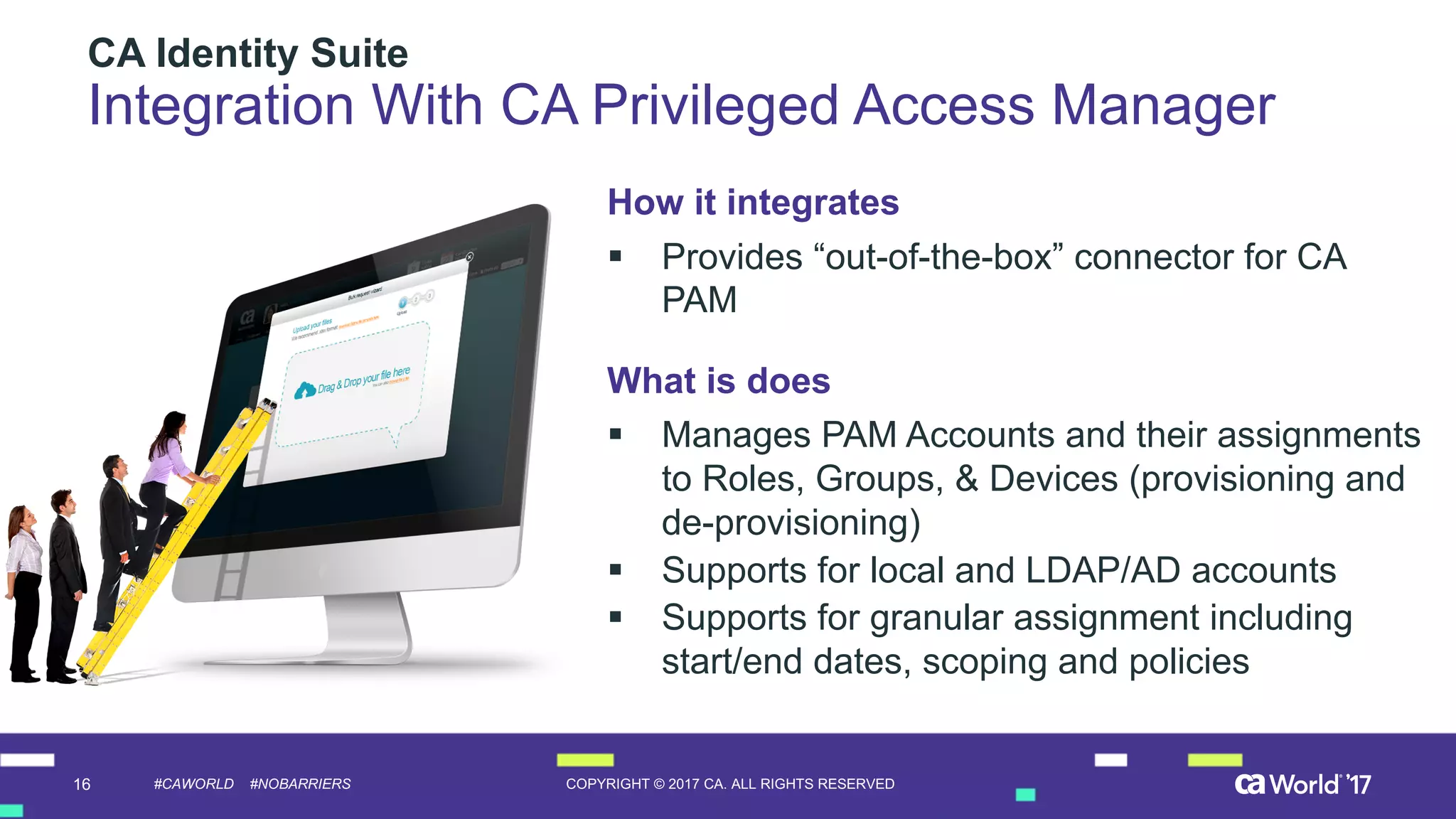
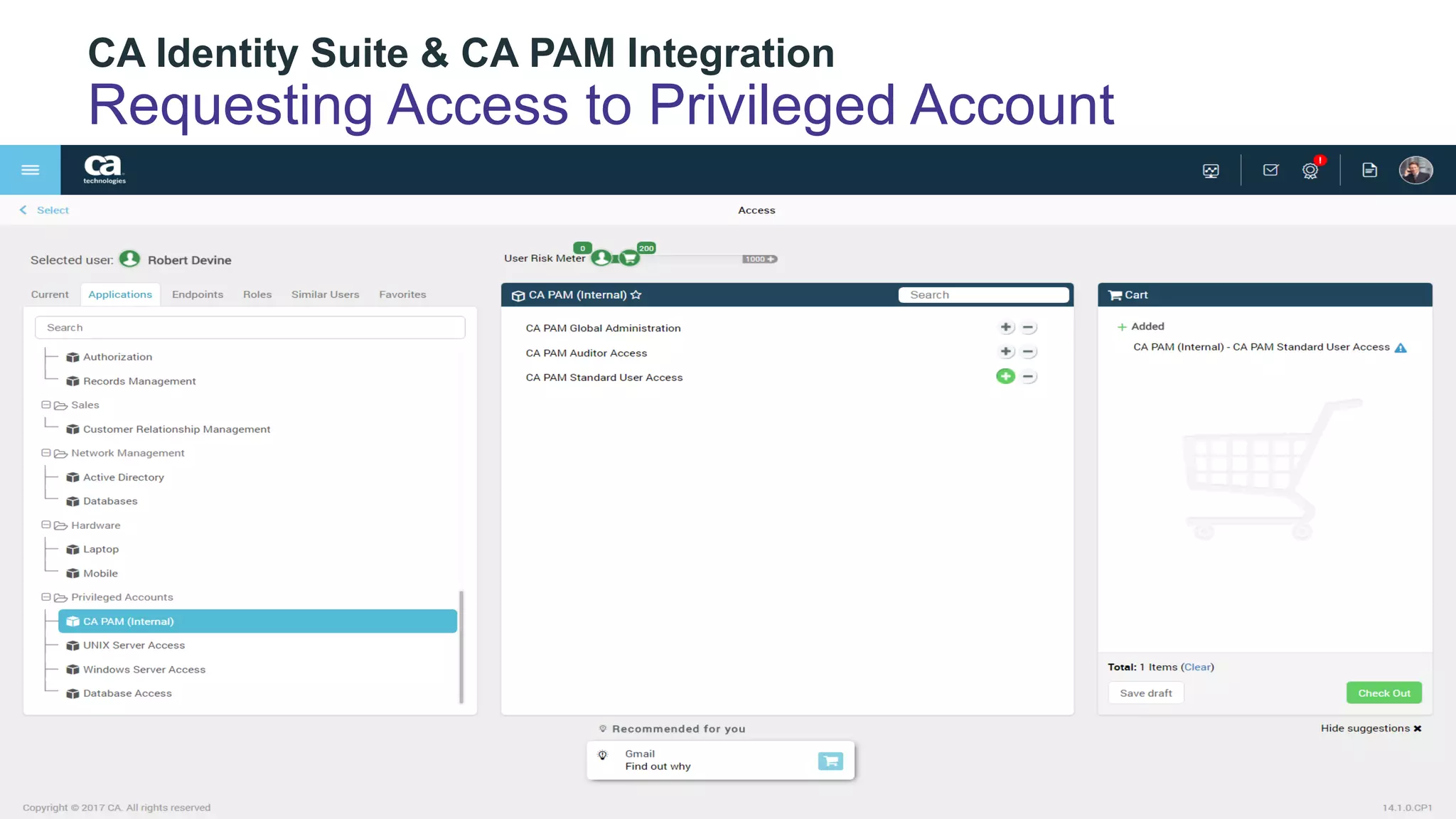
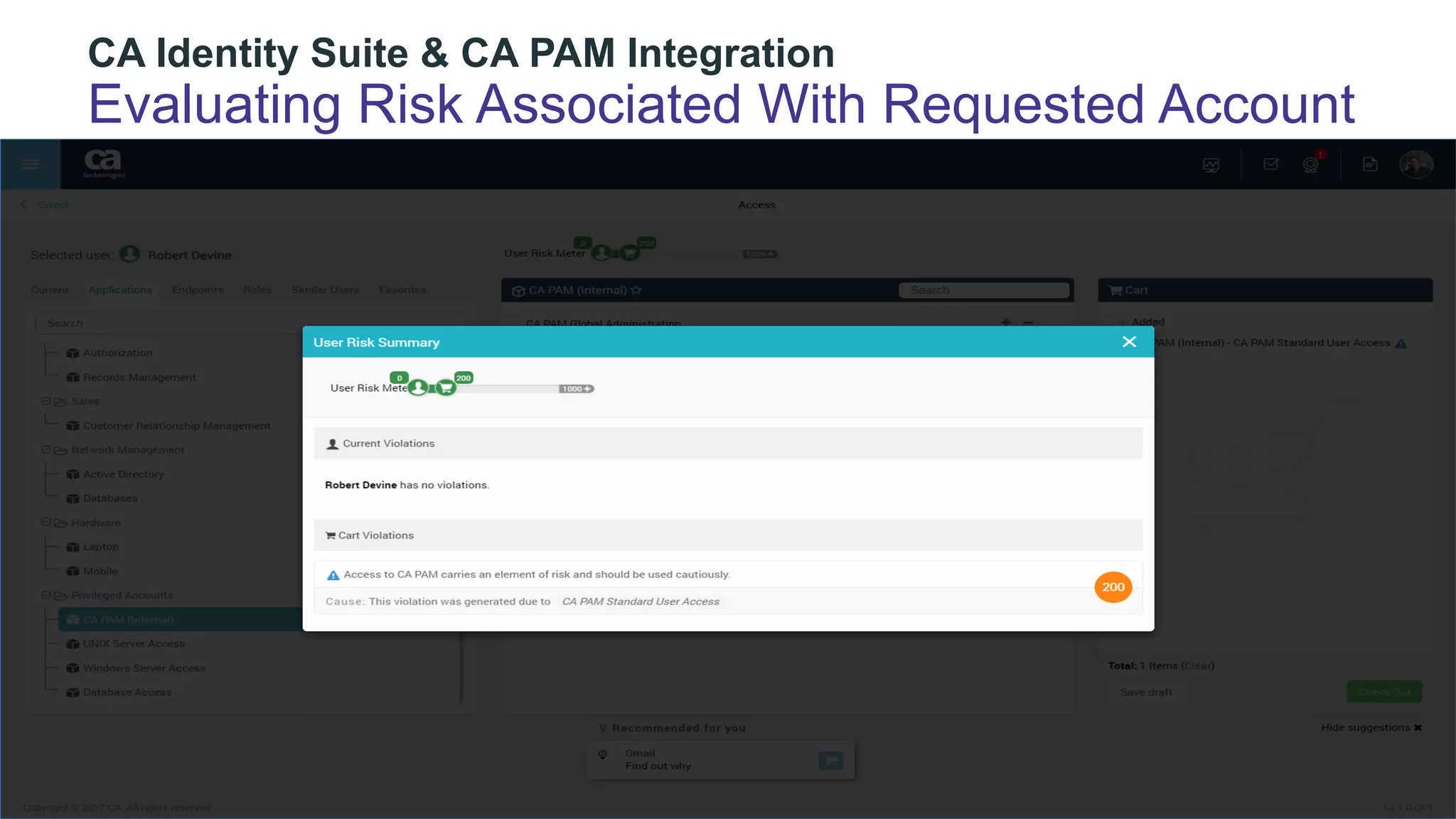
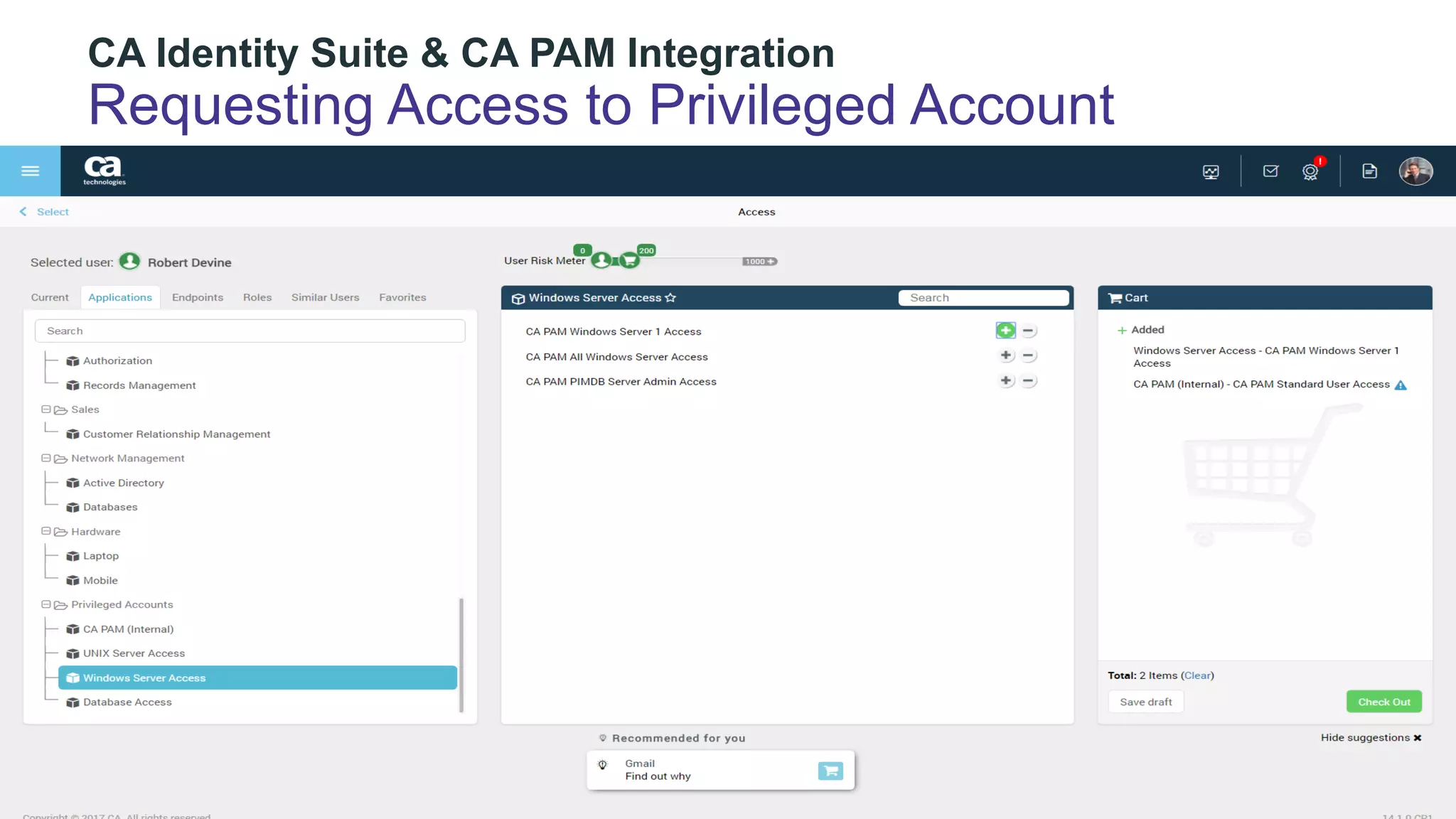
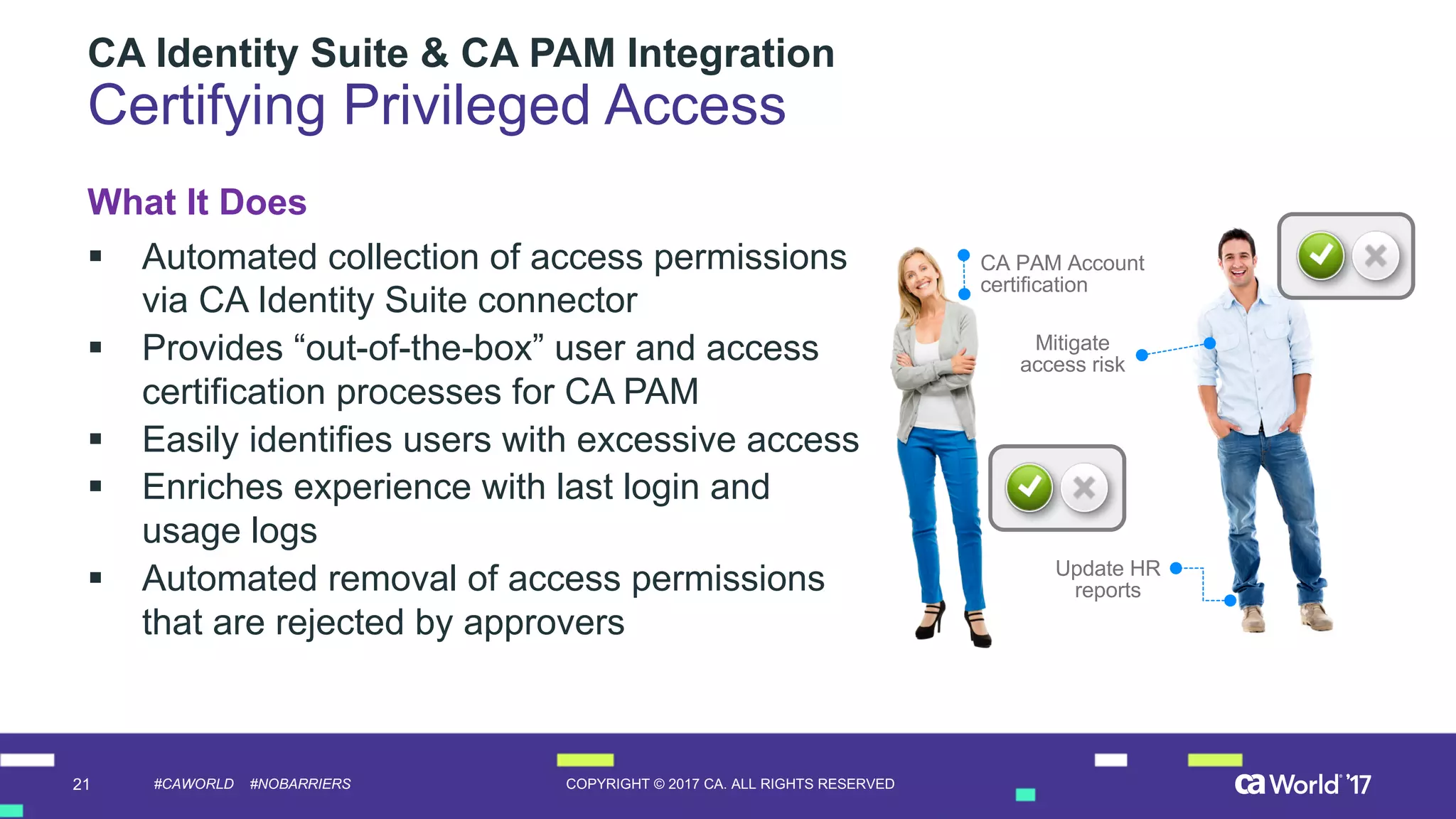
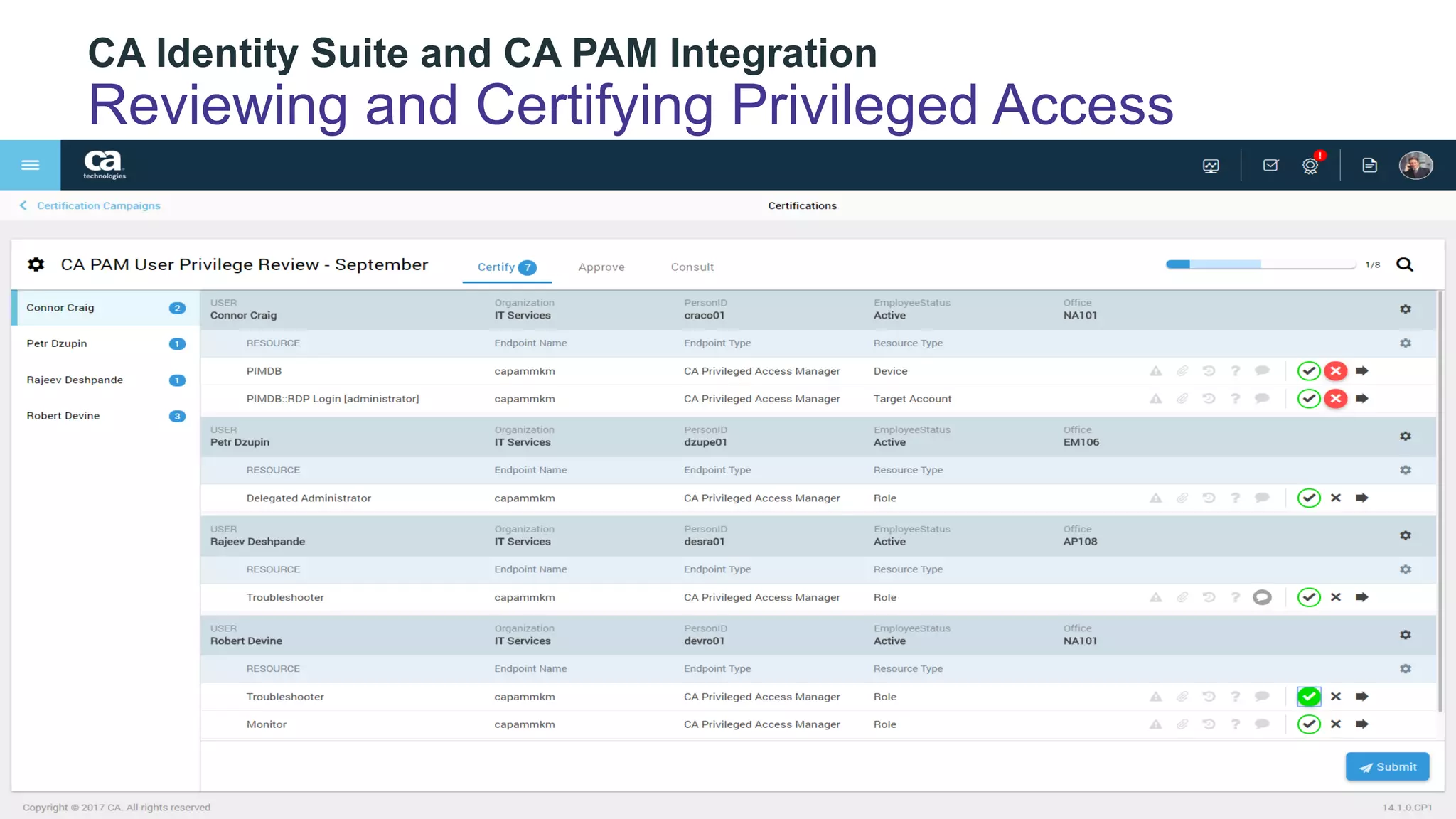
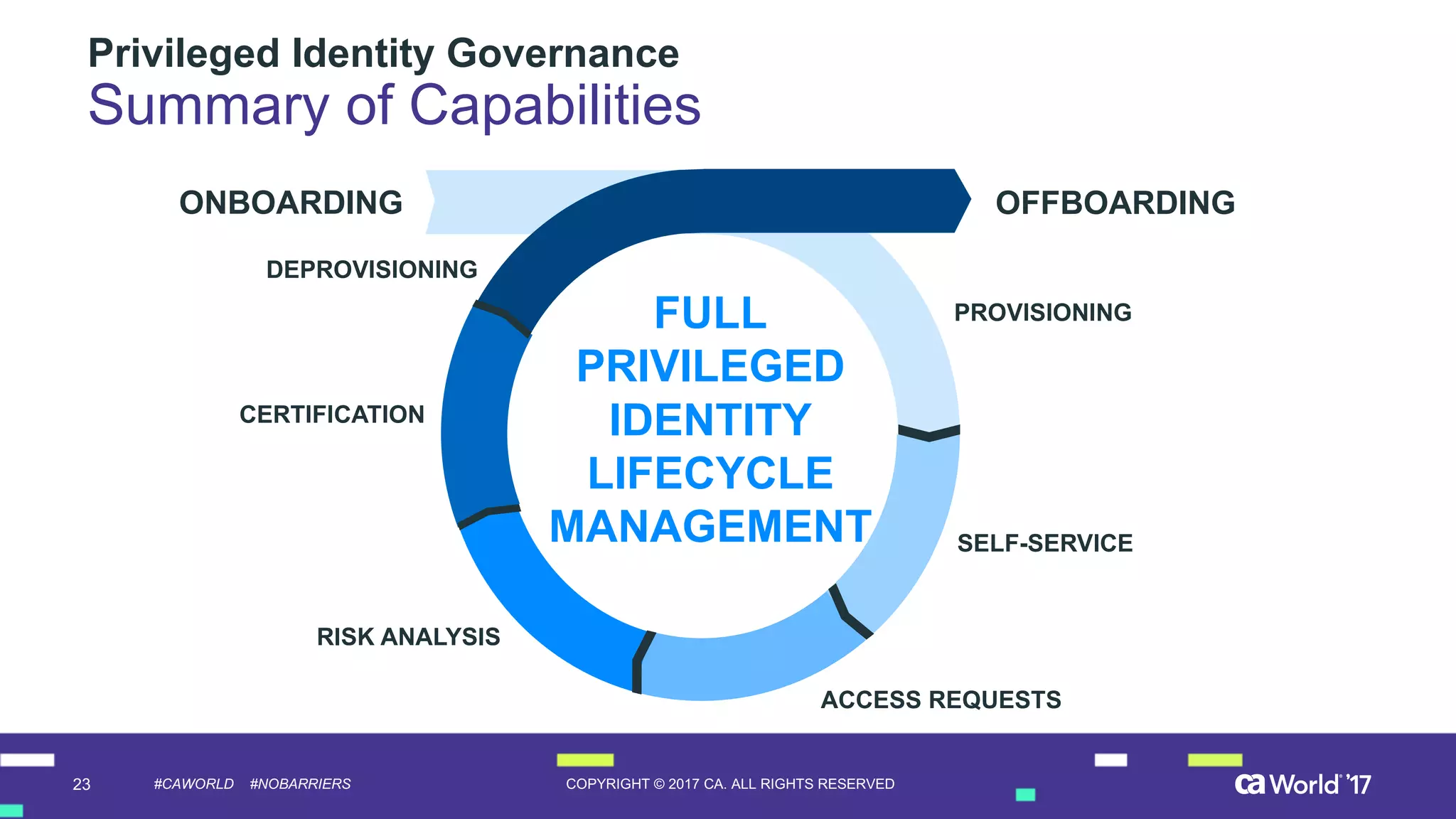
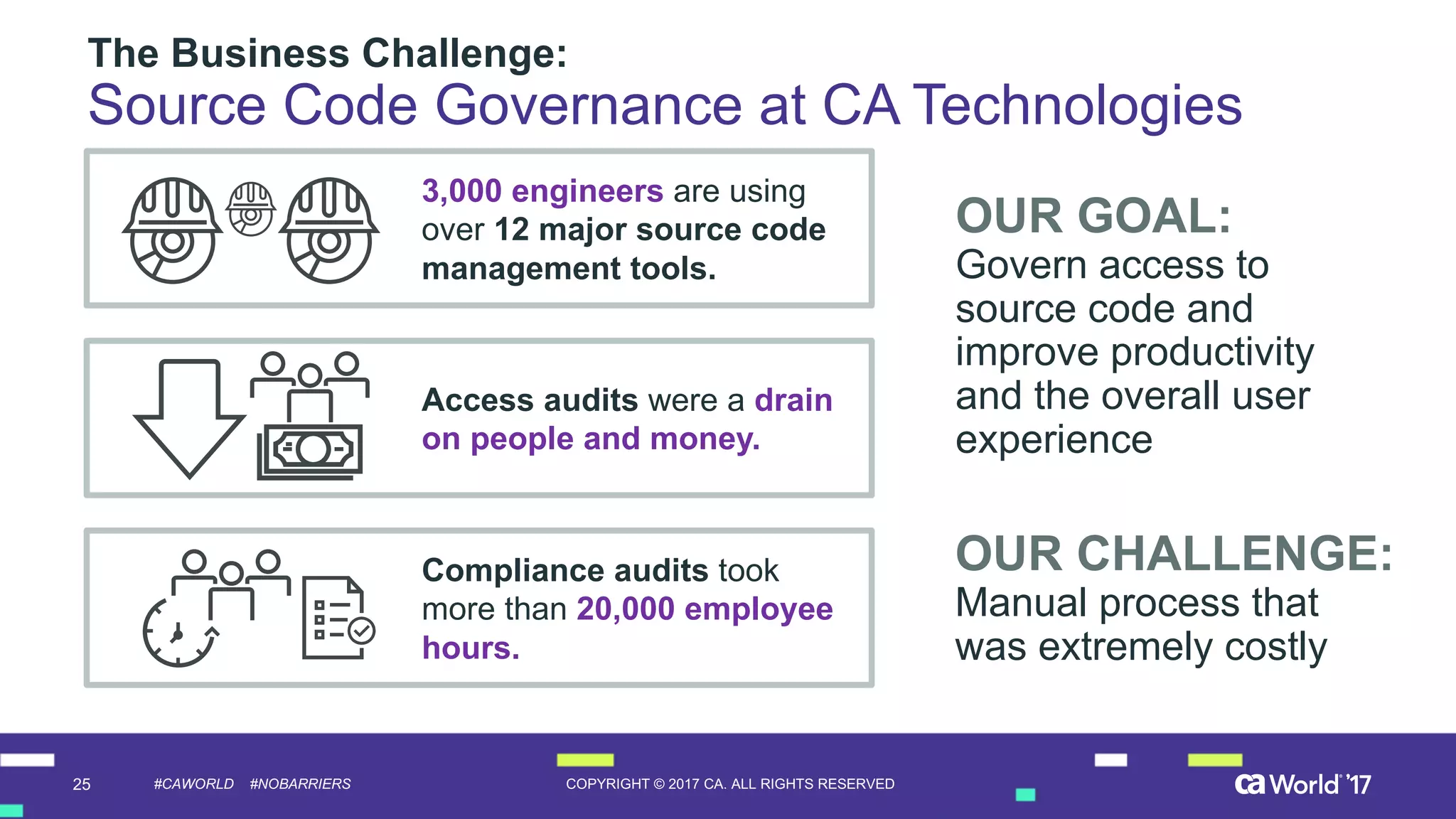
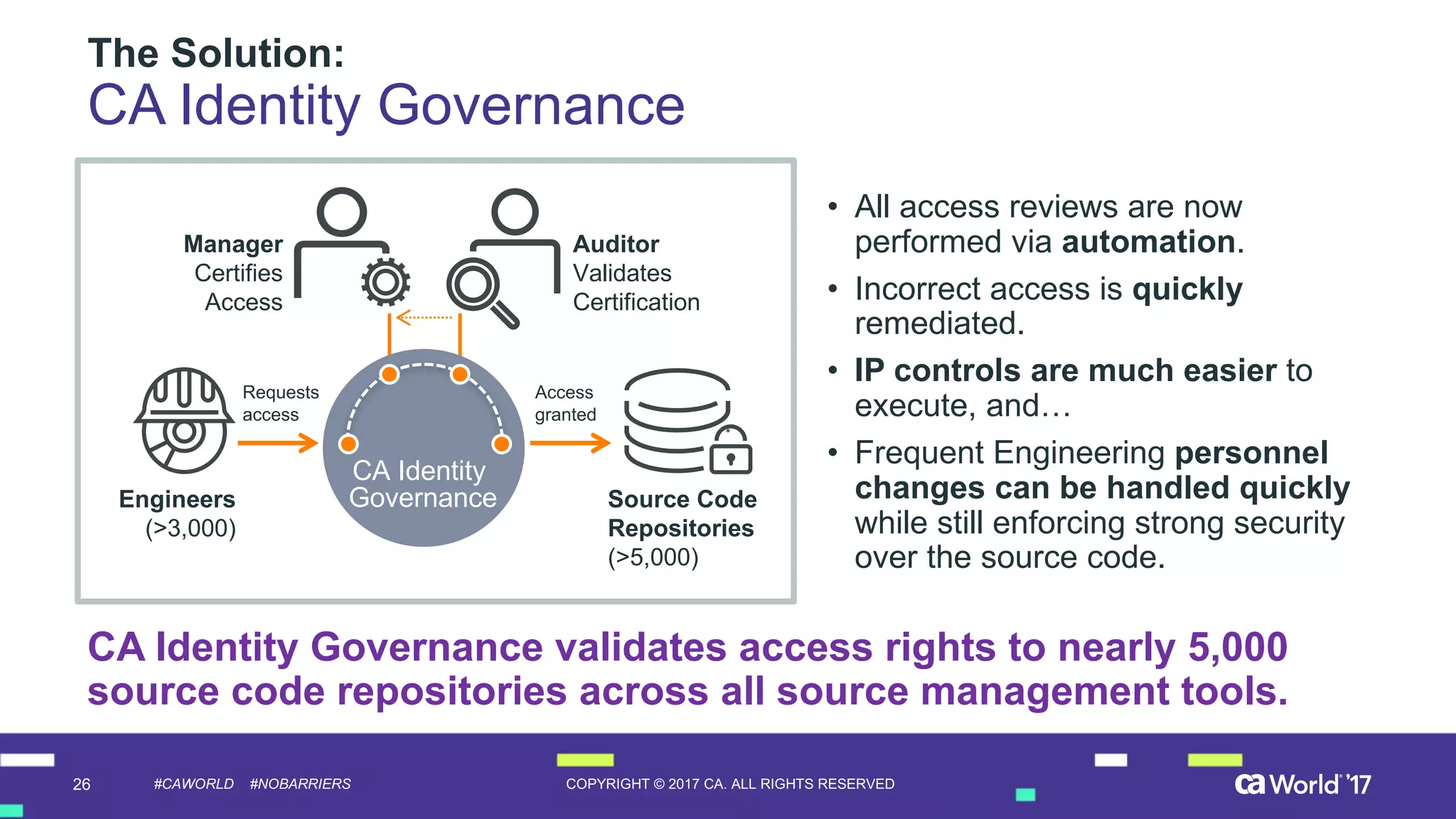
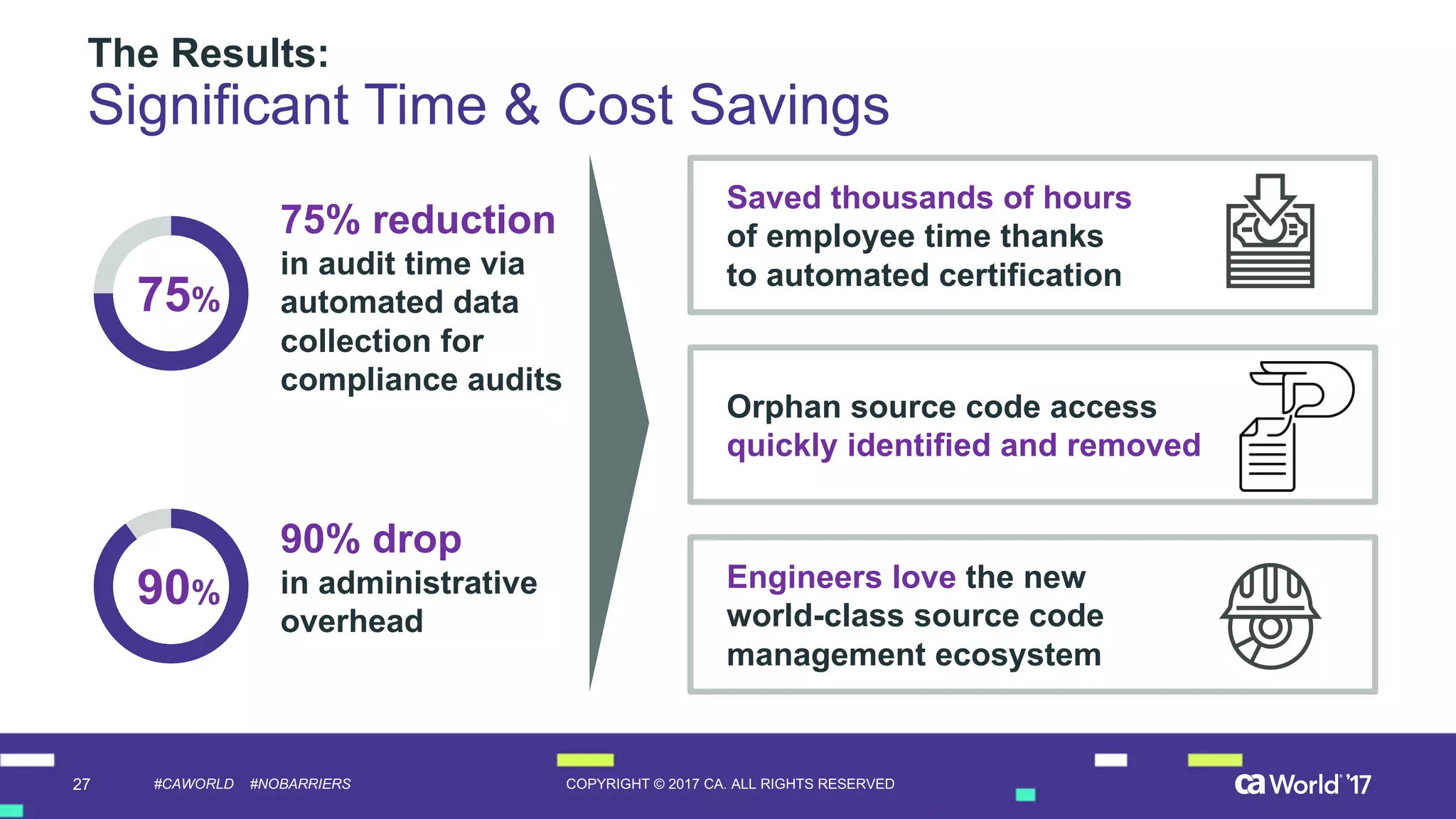
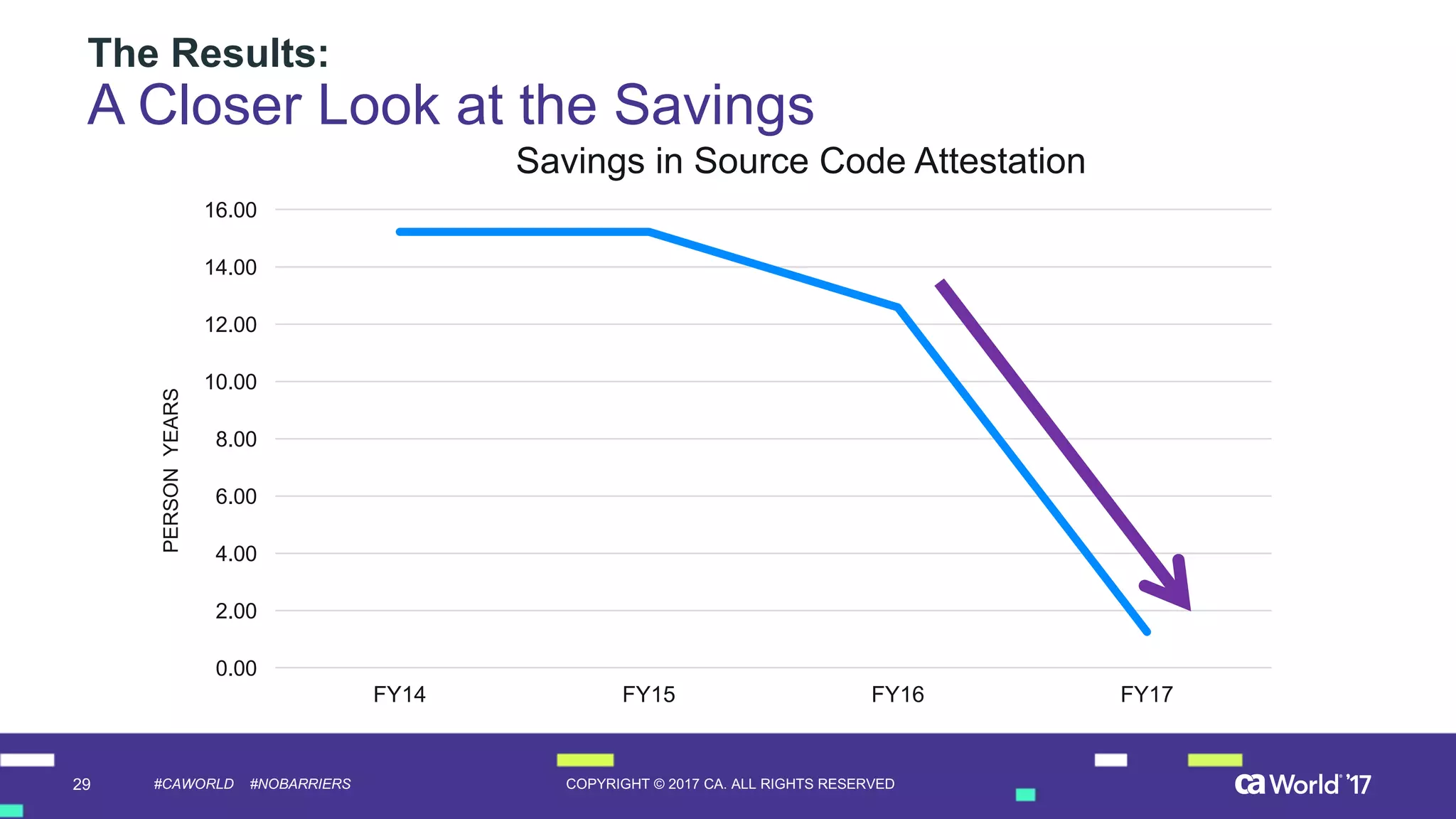
The document discusses the importance of privileged identity governance in managing and certifying privileged user access to minimize security risks. It highlights the significant challenges organizations face with legacy identity access management solutions and presents CA Technologies' Privileged Access Manager as a comprehensive approach to mitigate these issues. A case study is provided showing how automation in access governance led to substantial time and cost savings for CA Technologies.