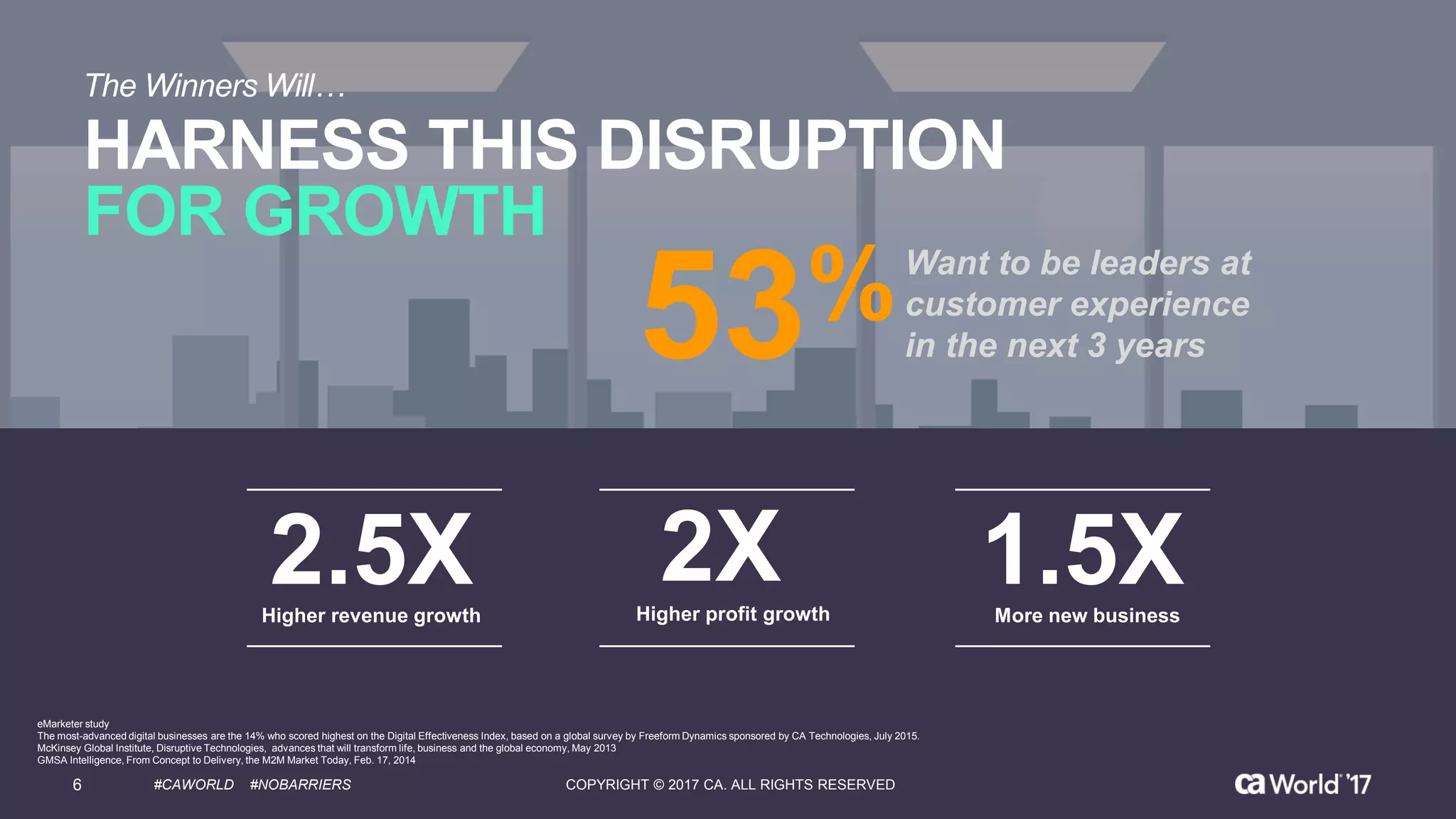
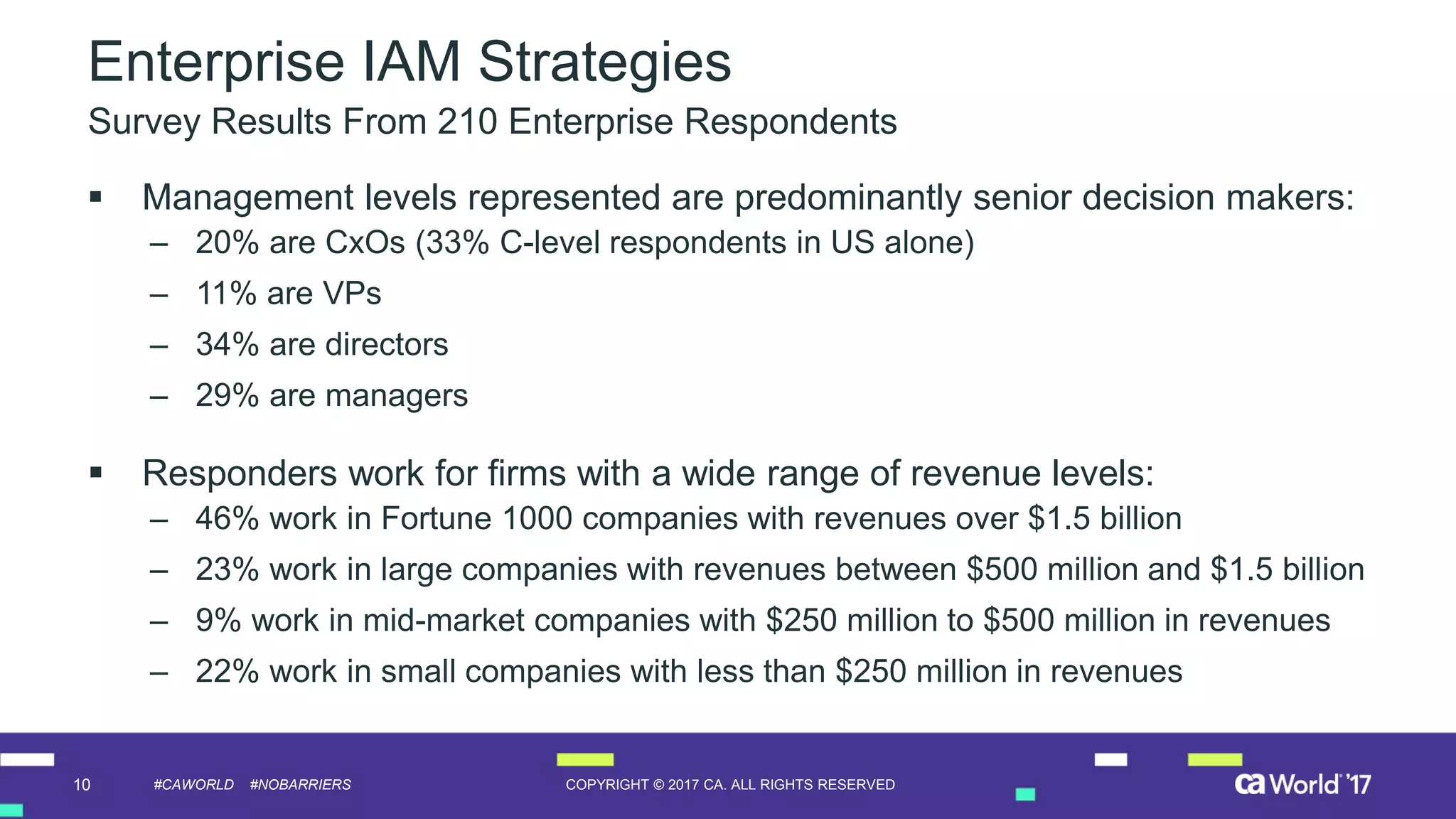
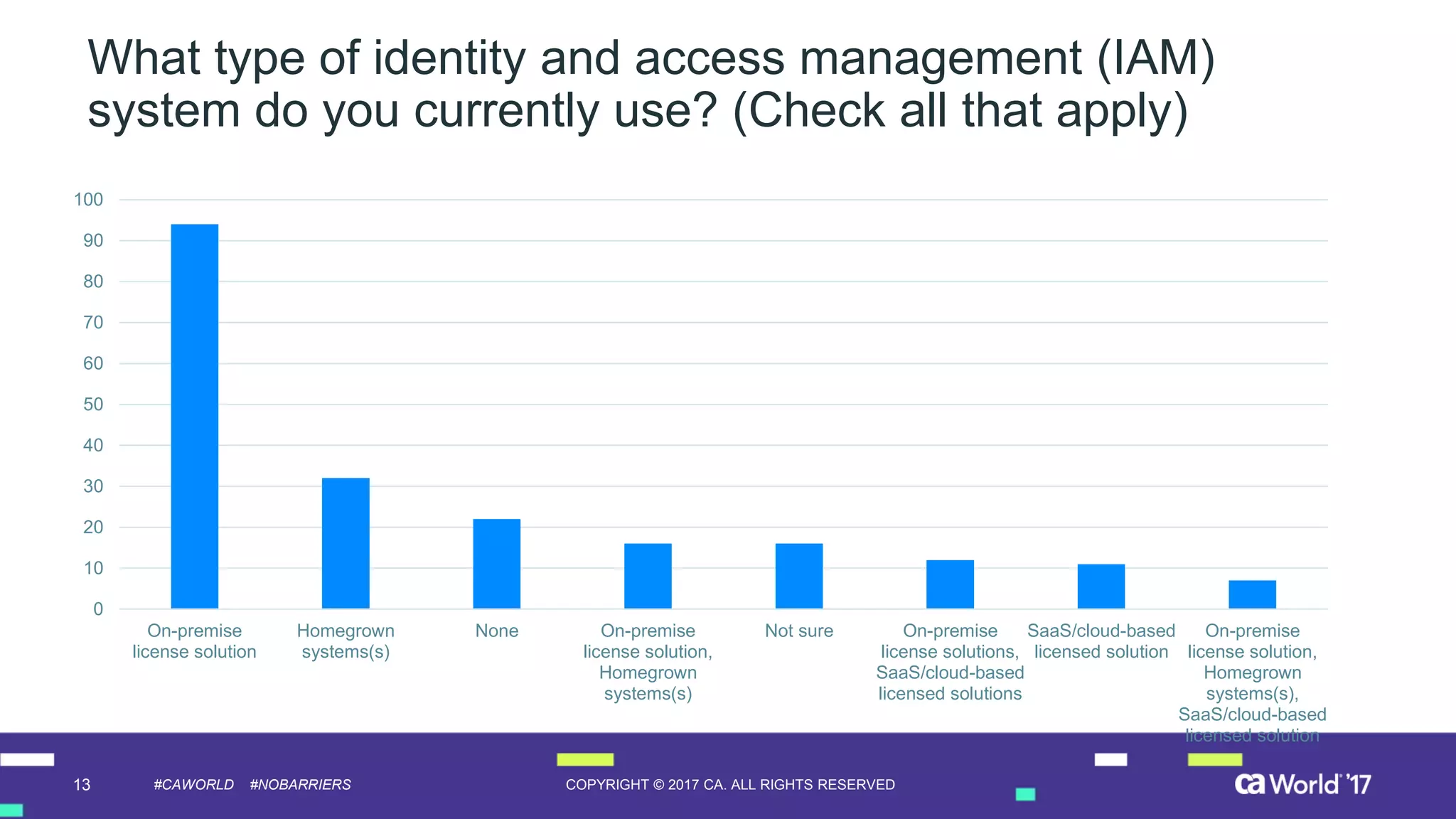
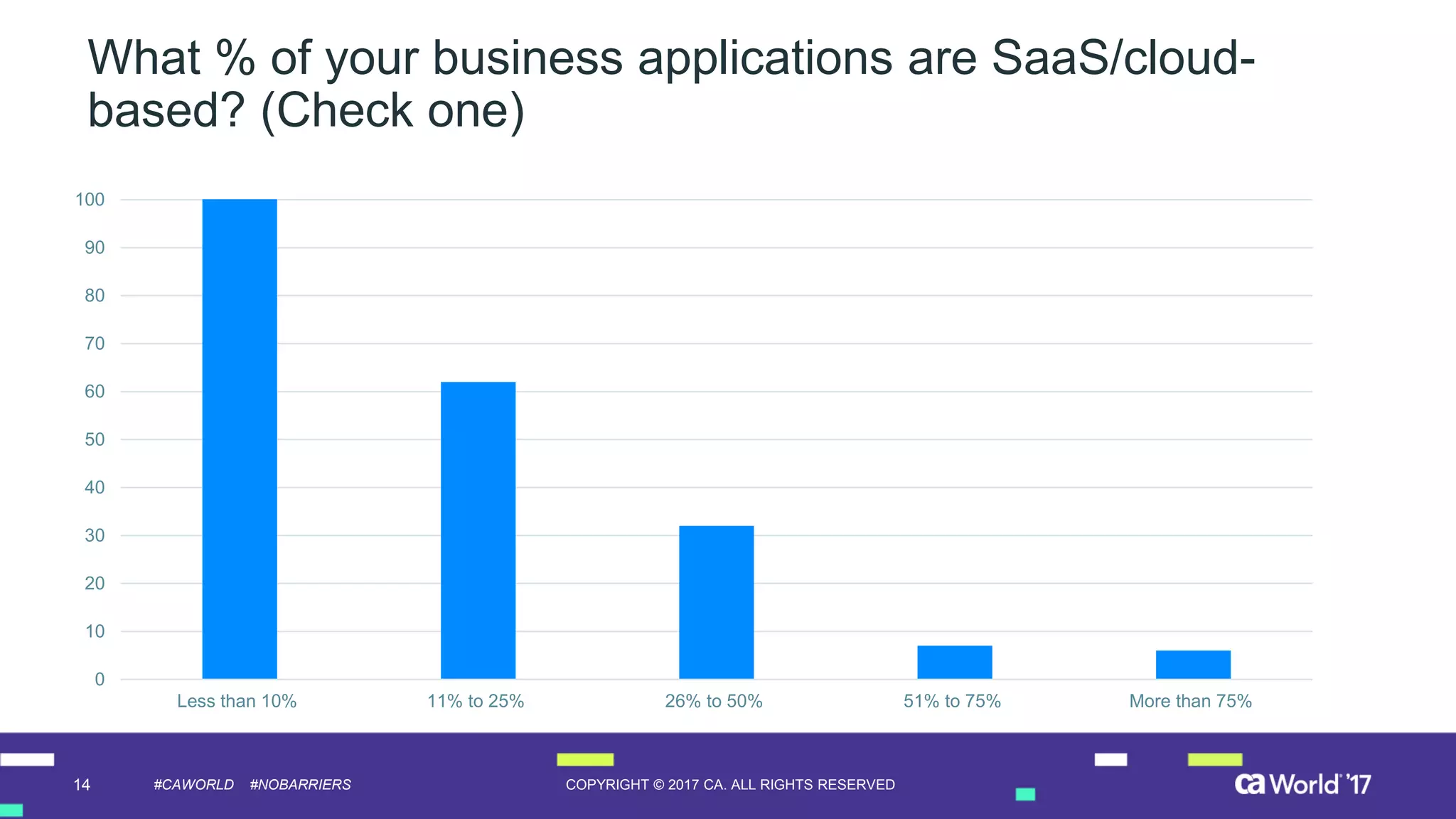
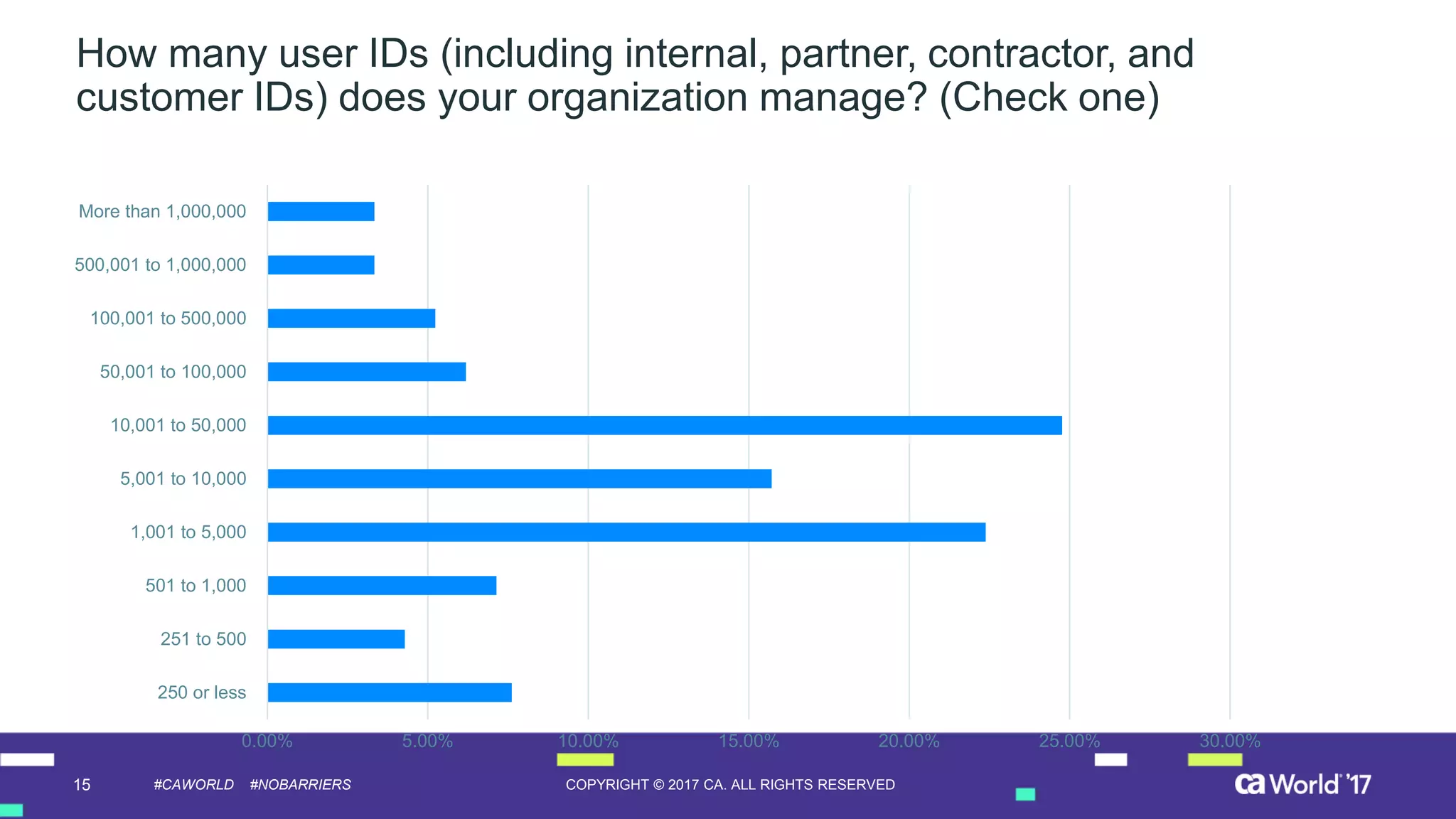
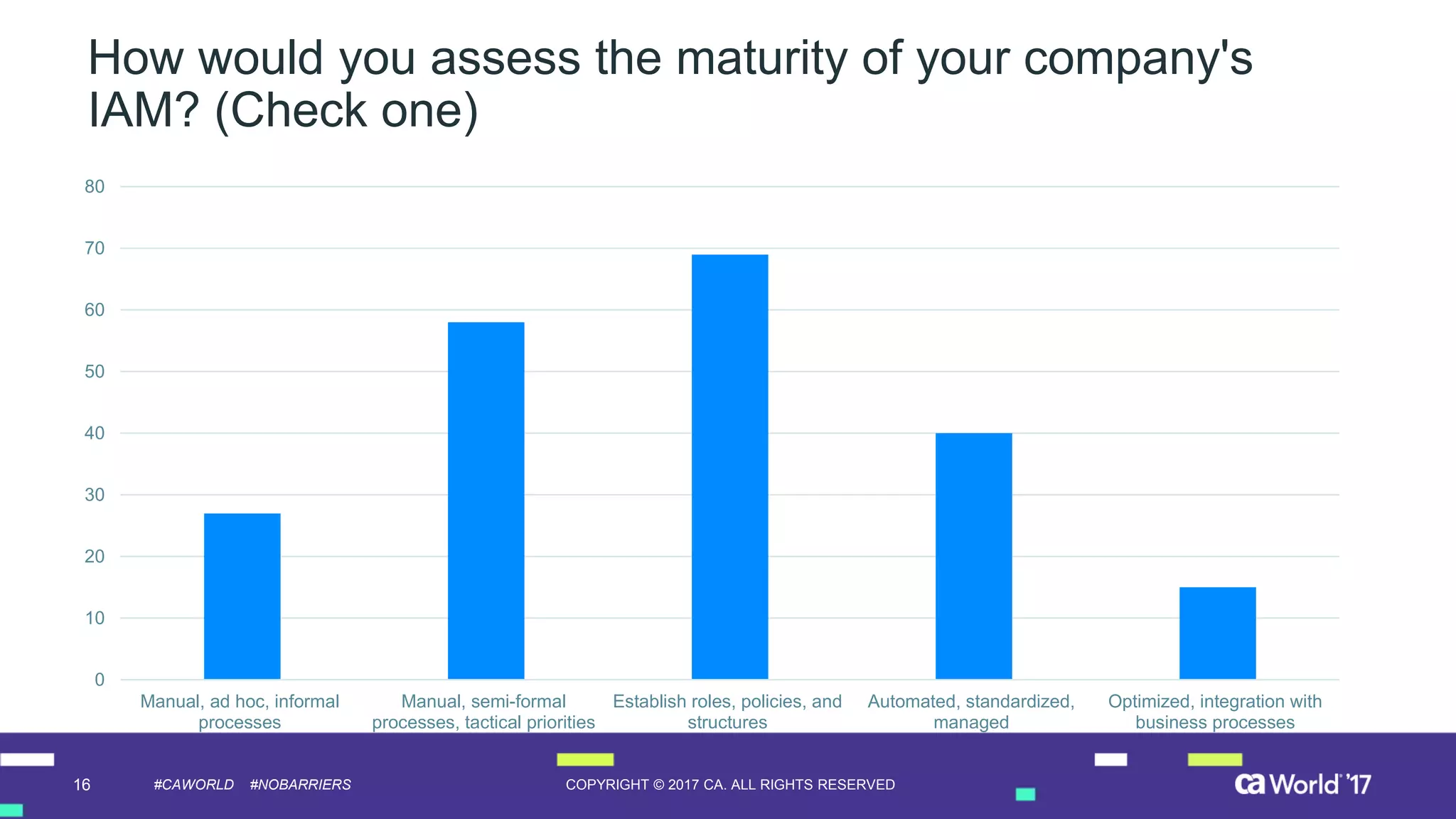
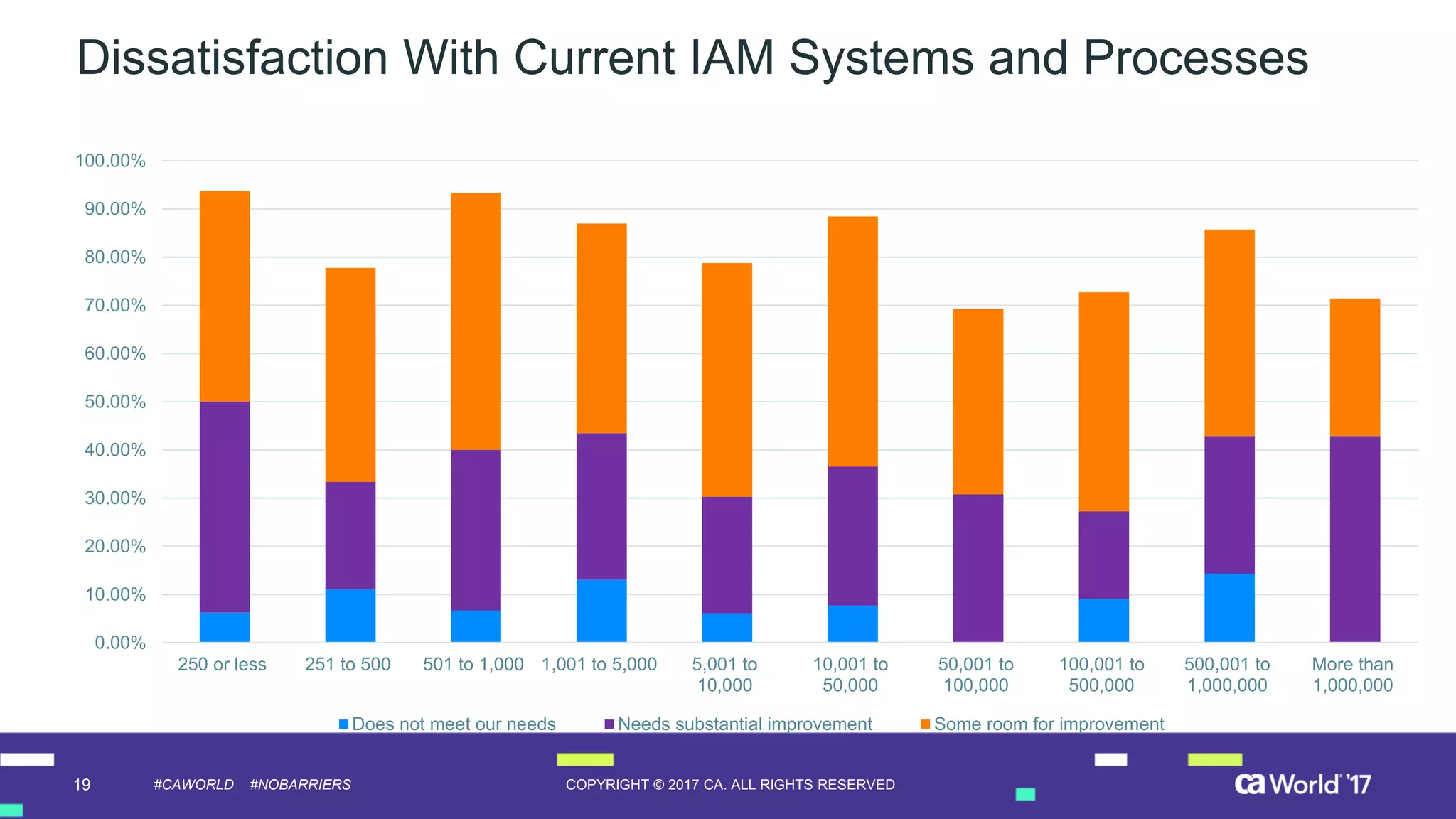
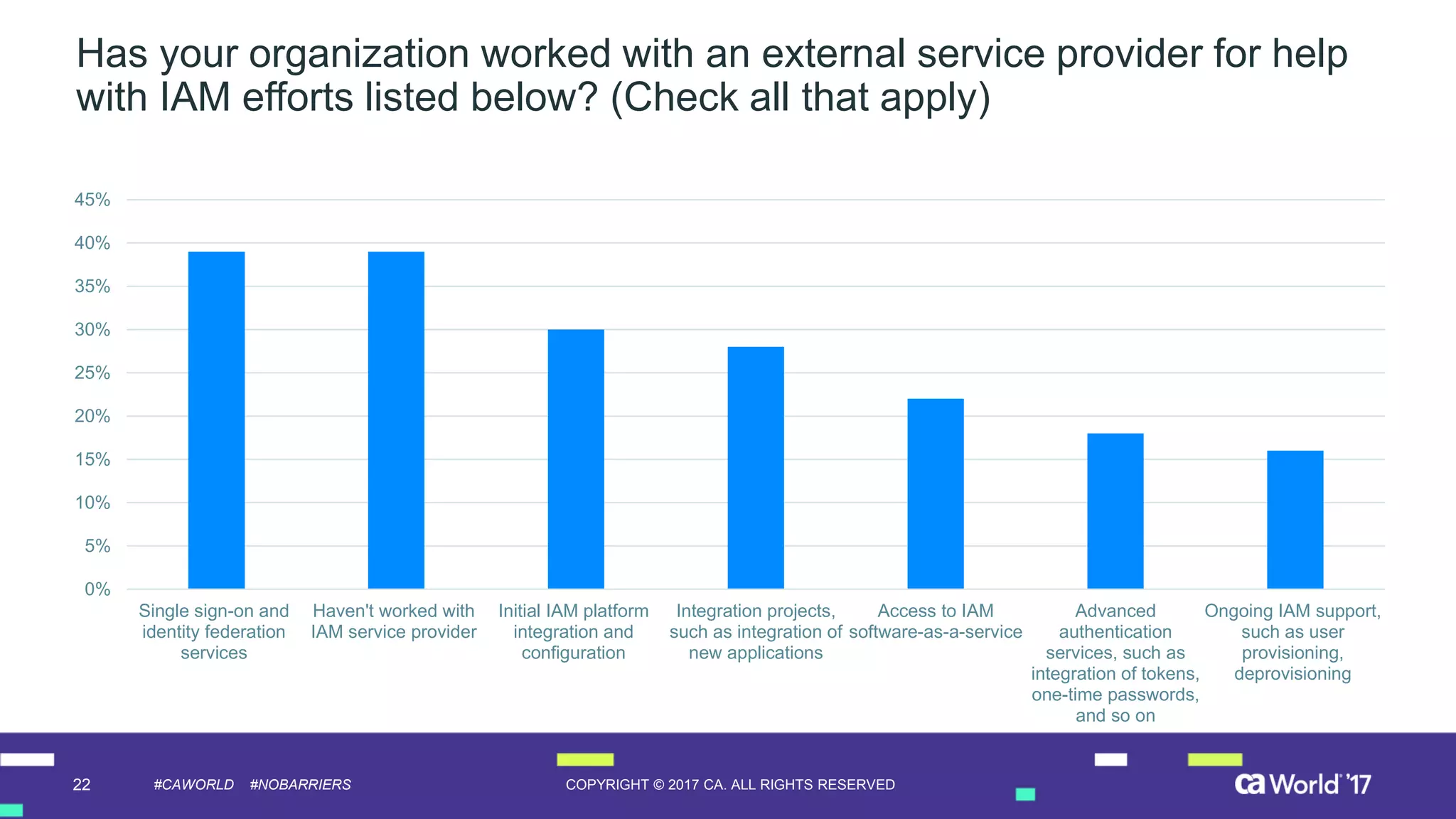
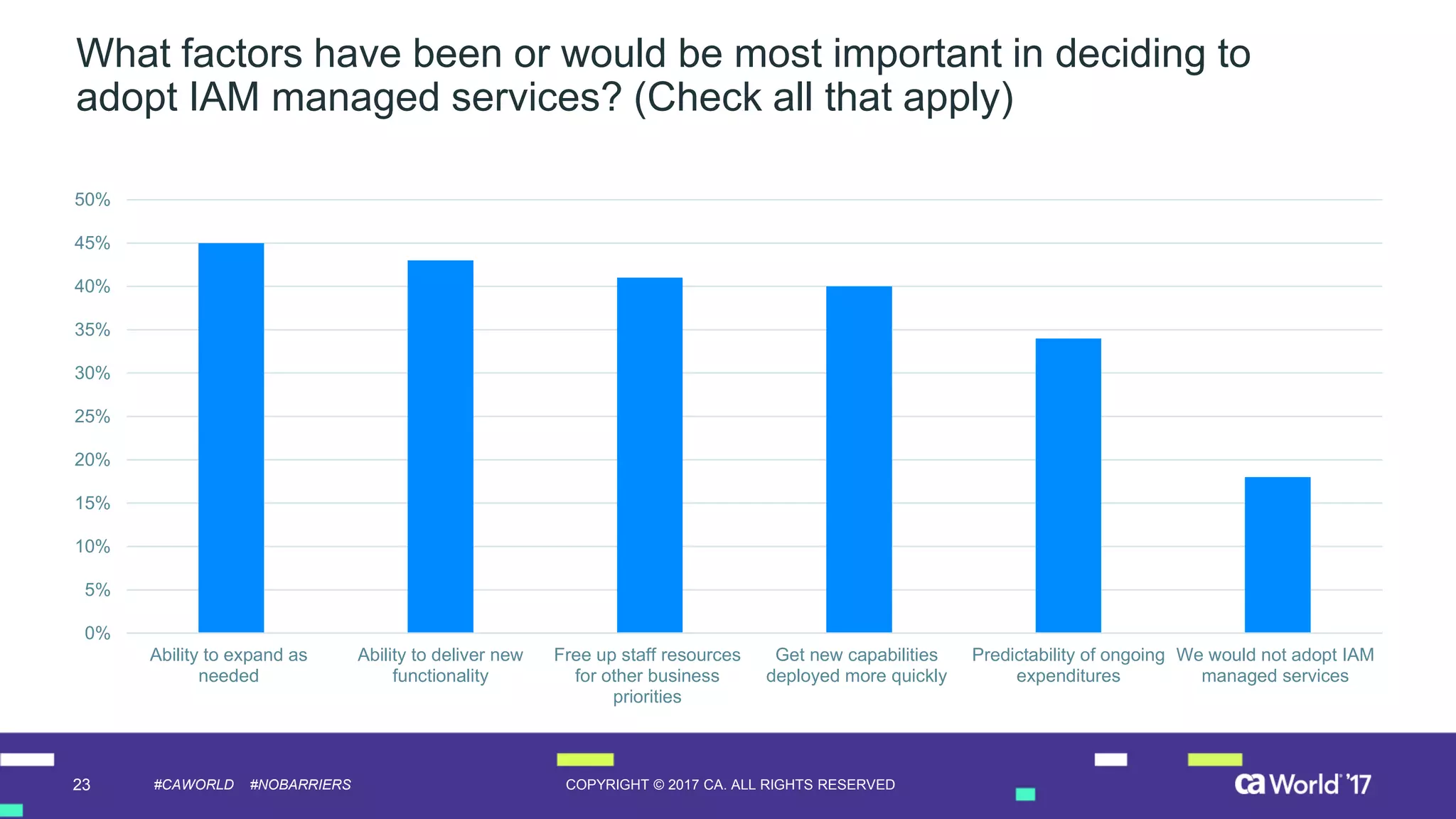
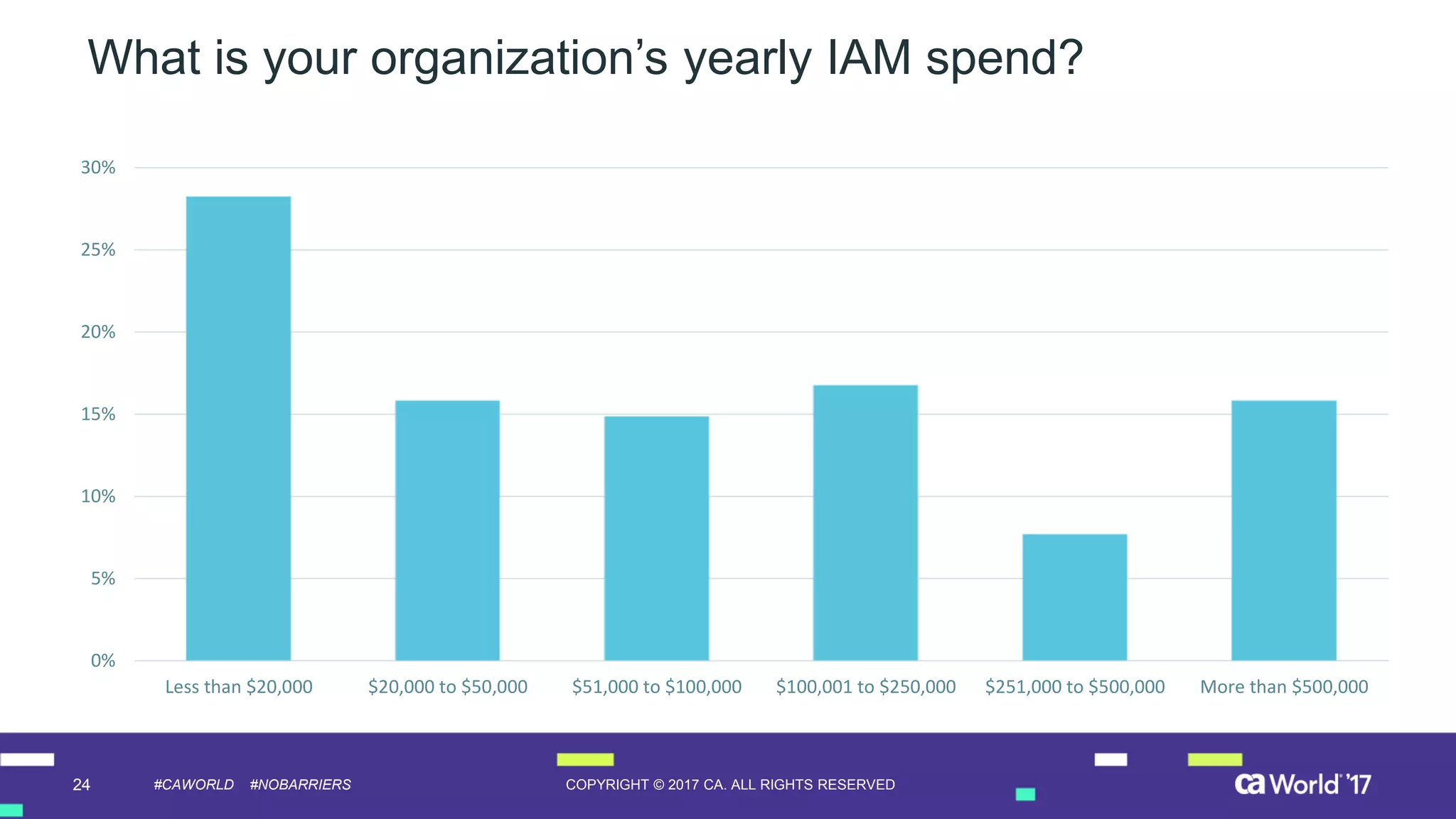
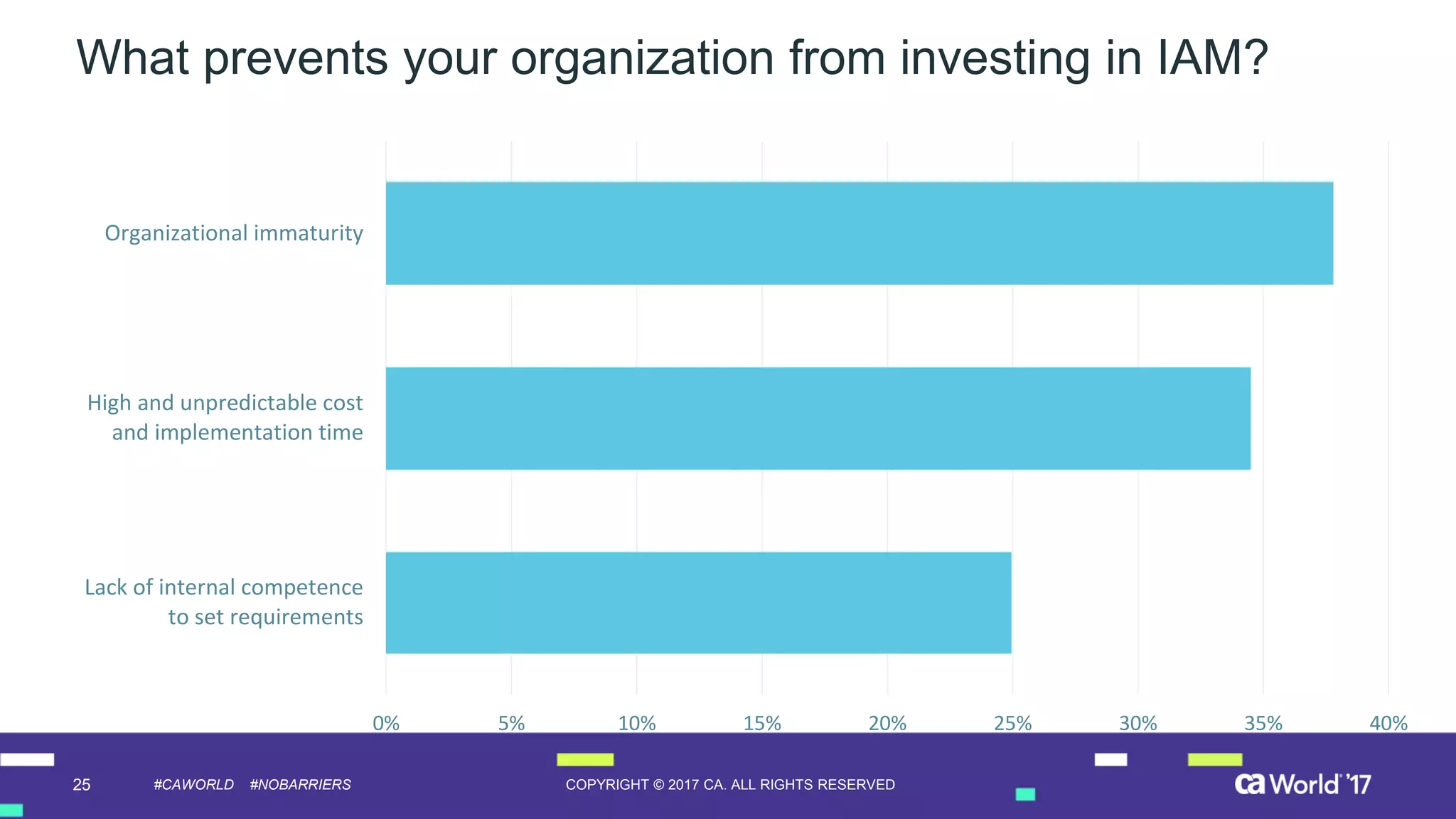
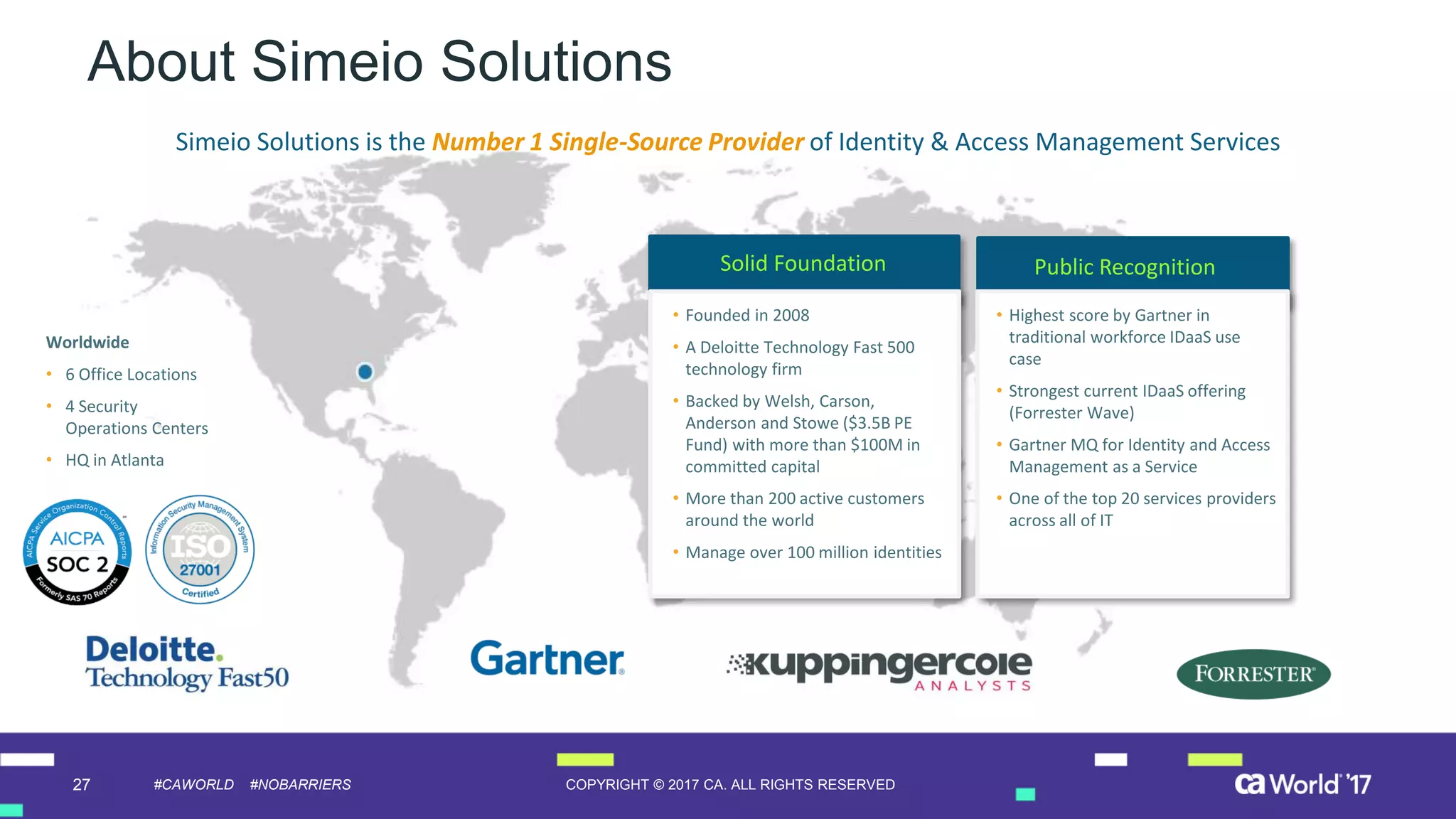
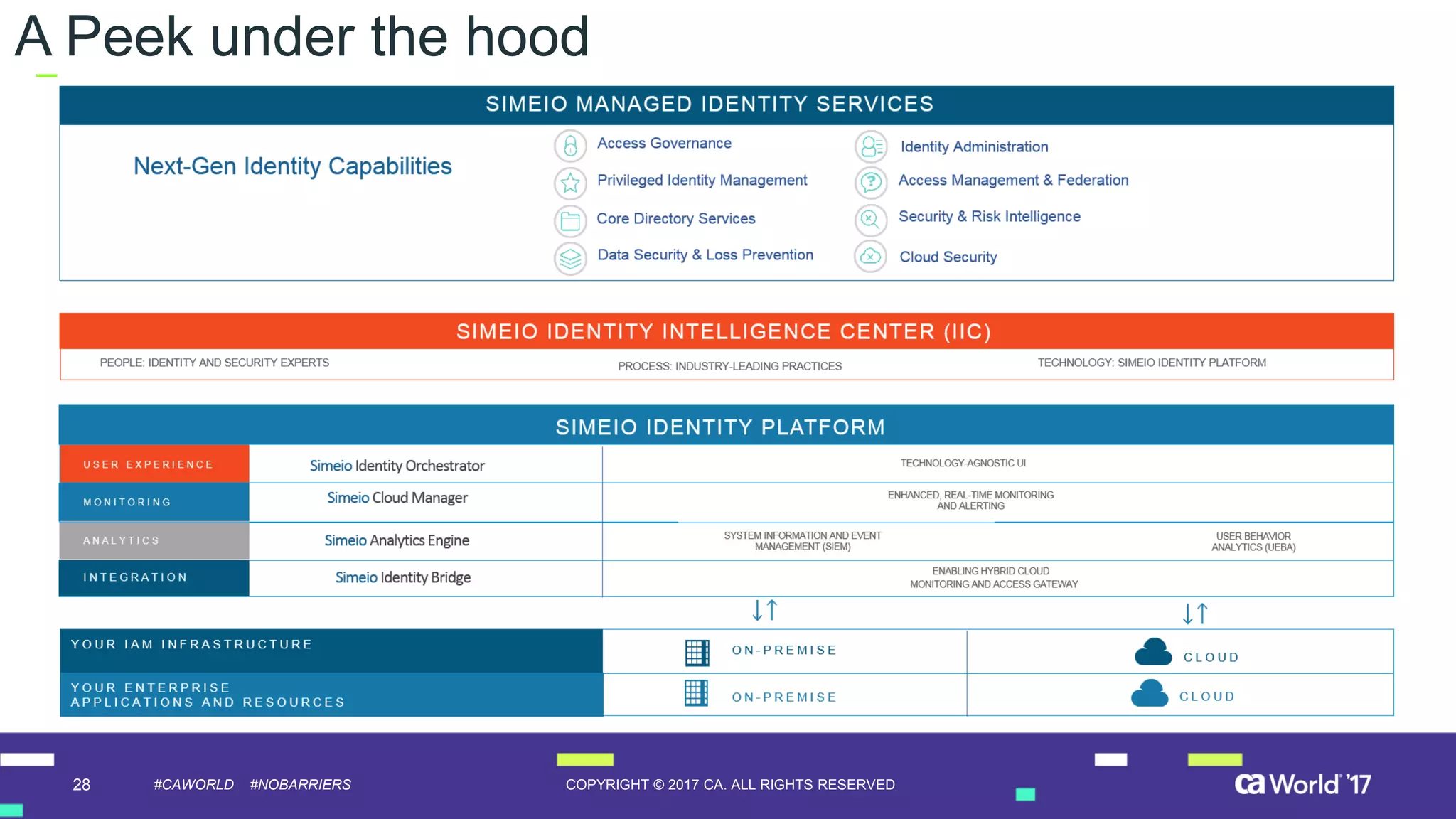
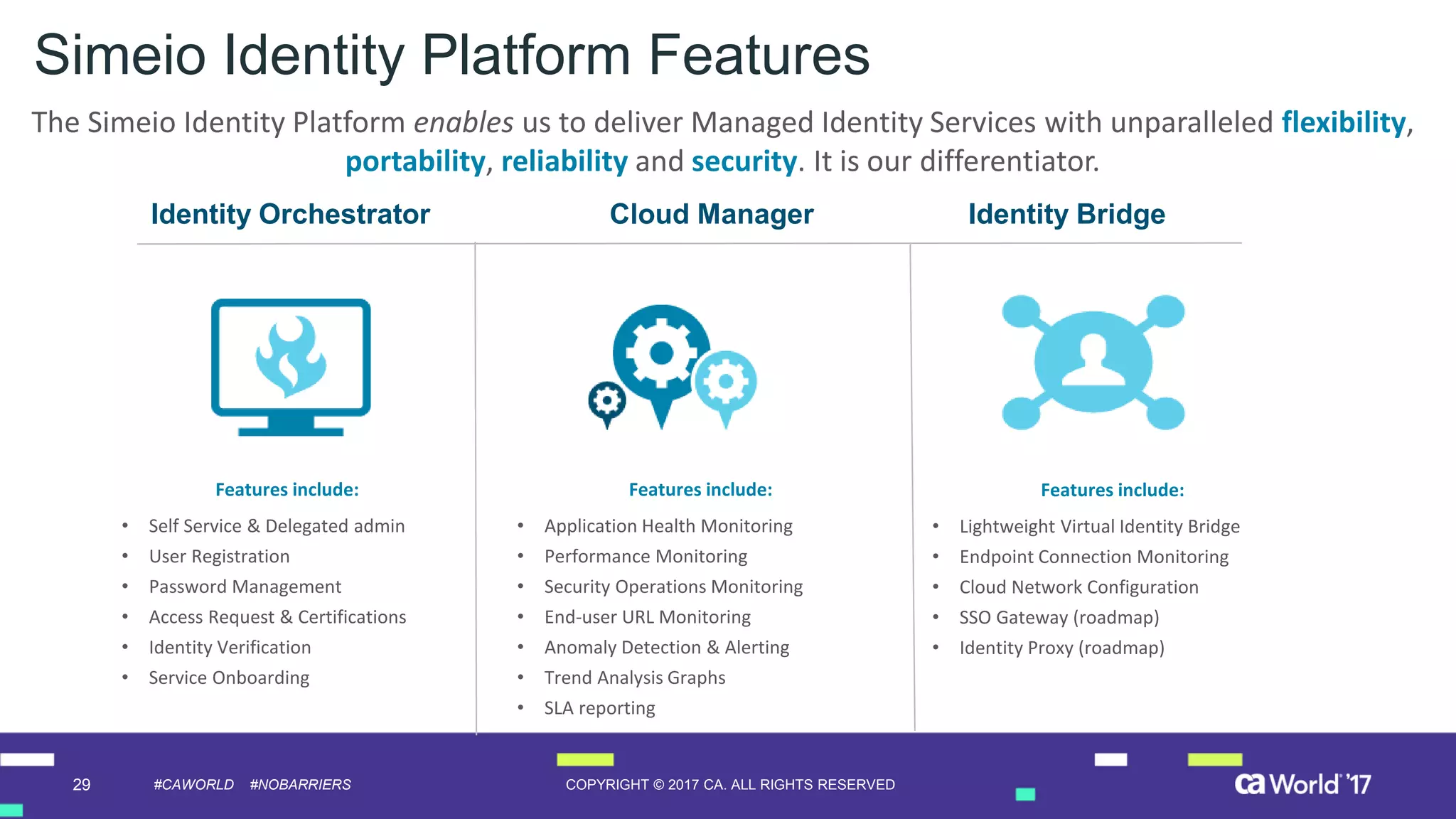
The document discusses the growing demand for identity and access management (IAM) services, highlighting a survey revealing that less than 20% of enterprises have automated IAM processes, indicating significant challenges in meeting organizational needs. It emphasizes the role of external partners in assisting enterprises to overcome IAM obstacles and improve security measures. Additionally, the presentation outlines the importance of identity in delivering personalized experiences in the evolving application economy.