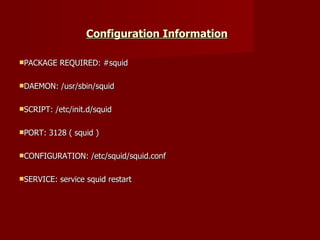
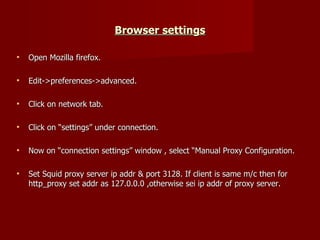
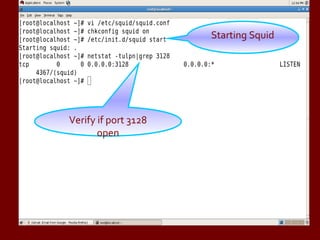
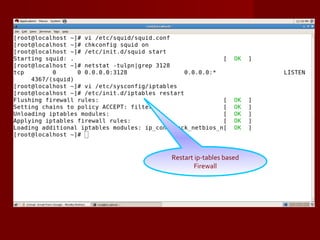
Squid Proxy Server on RHEL introduces Squid, a free and open-source proxy server software that provides caching, authentication, bandwidth management, and web filtering capabilities. It discusses configuring Squid on Red Hat Linux including installing packages, editing configuration files, starting services, and testing the proxy functionality. Browser and client settings are also covered to allow systems to route traffic through the Squid proxy server.