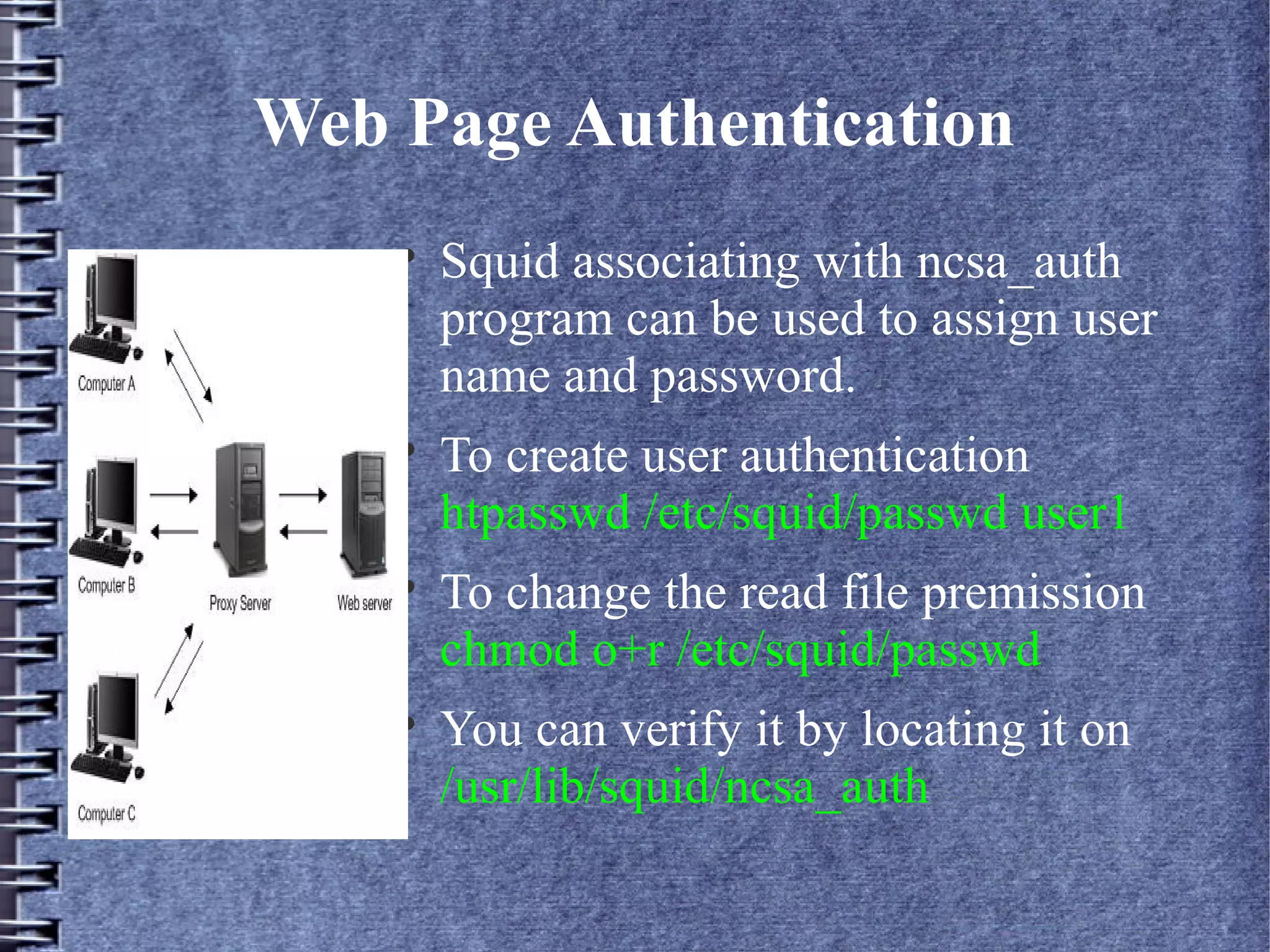
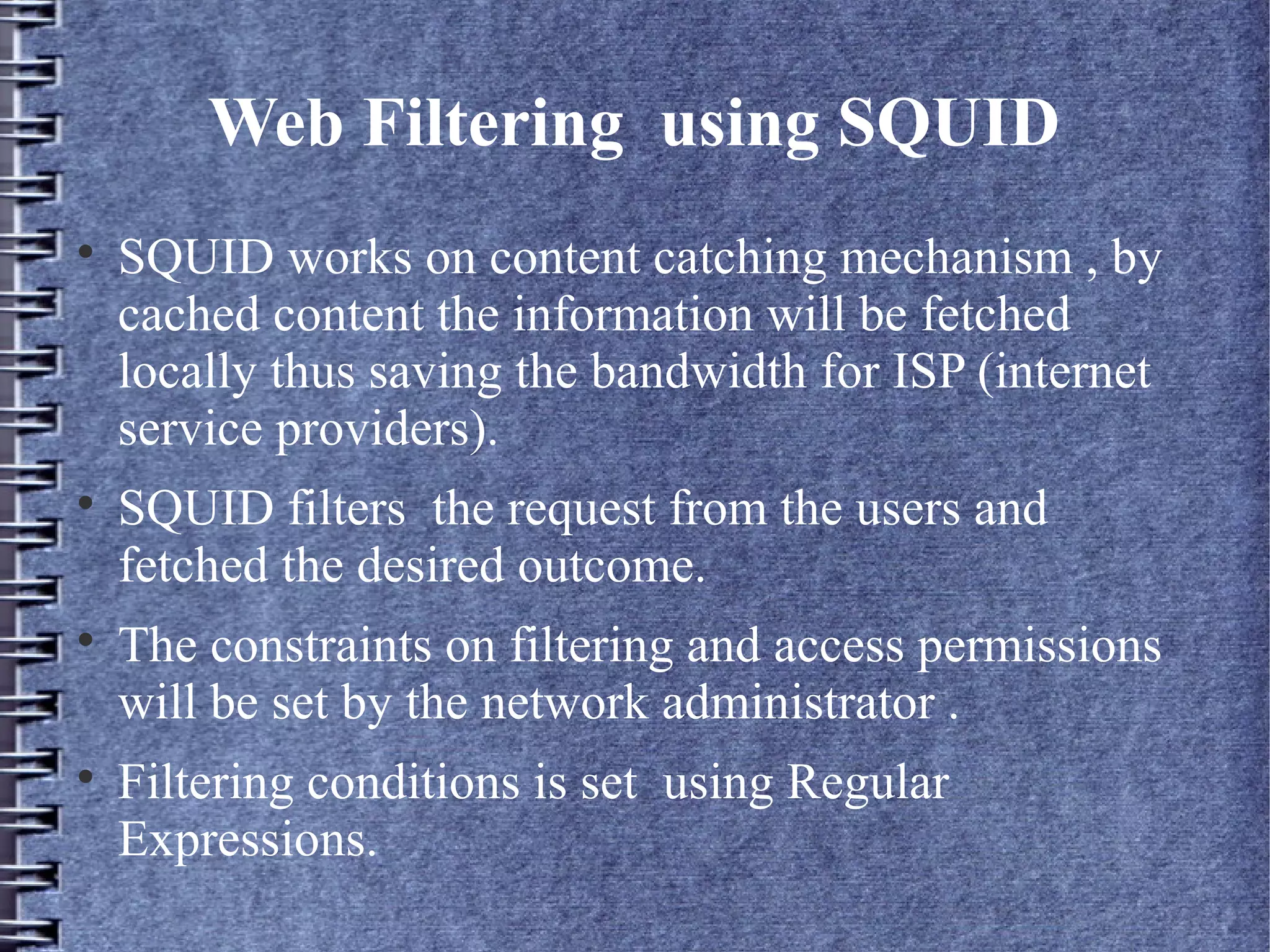
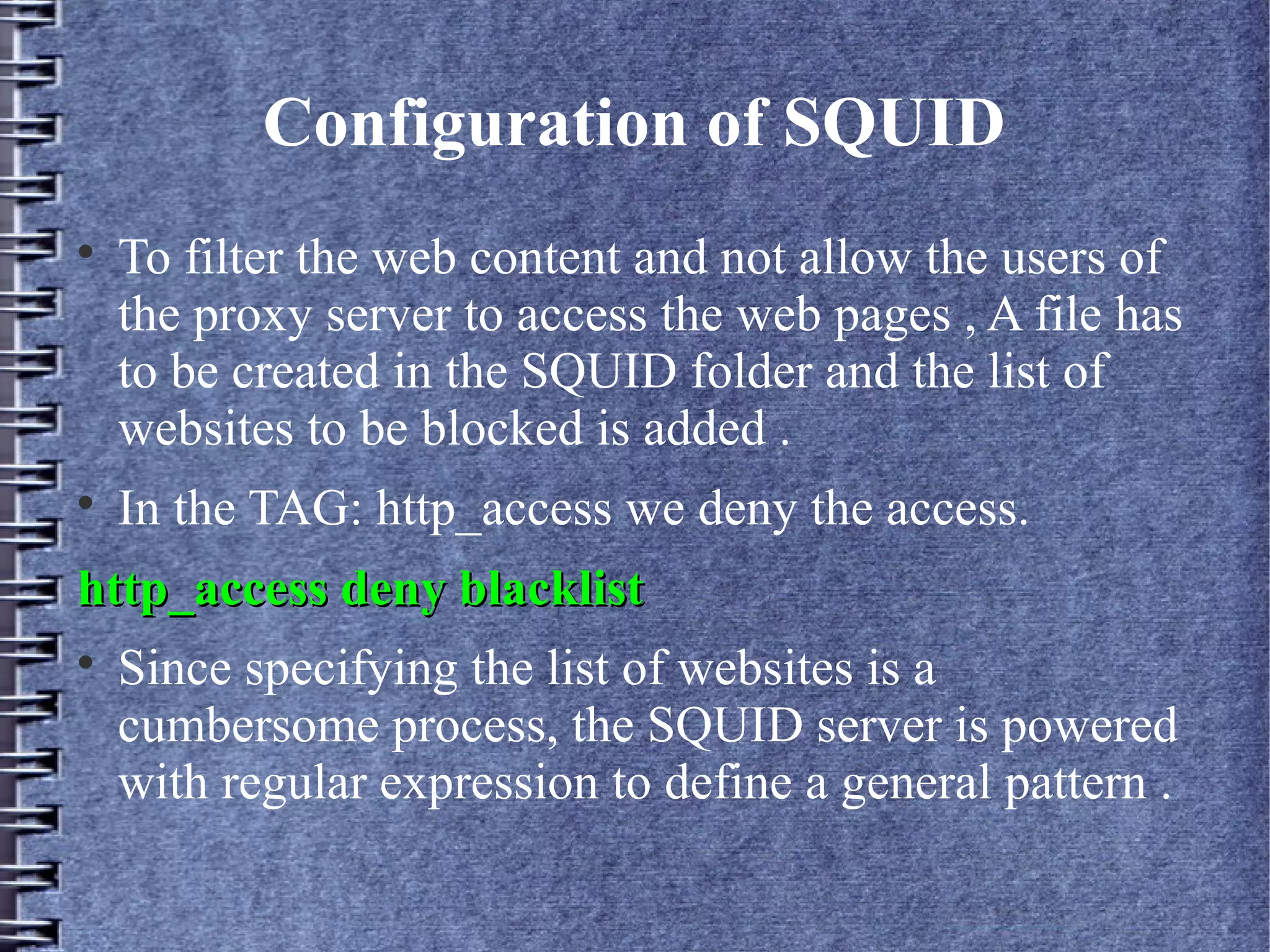
Squid is an open source web proxy and cache server that provides content filtering, access control, and caching capabilities to improve network performance; it sits between clients and external servers to filter web traffic based on configured rules and restrictions set by the network administrator using regular expressions and access control lists. Squid can also integrate with authentication servers like ncsa_auth to require passwords for user access through the proxy.





![Configuration of SQUID
The Regular Expression are specified in the file
named blocks.file.acl .
.[Ee][Xx][Ee]$
.[Aa][Vv][Ii]$
.[Mm][Pp][Gg]$
.[Mm][Pp][Ee][Gg]$
.[Mm][Pp]3$
In the TAG: http_access we deny the access.
http_access deny blocks.file.acl](https://image.slidesharecdn.com/squidnew-121021115747-phpapp02/75/Squid-Caching-for-Web-Content-Accerlation-10-2048.jpg)