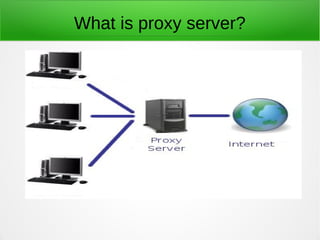
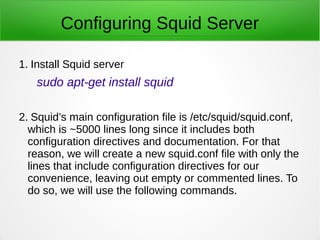
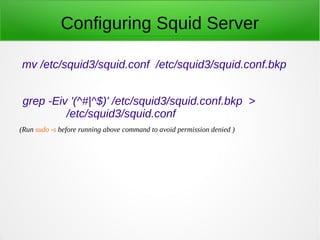
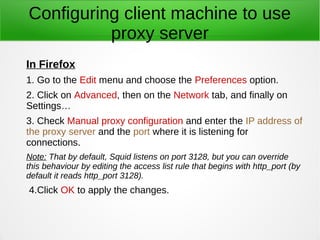
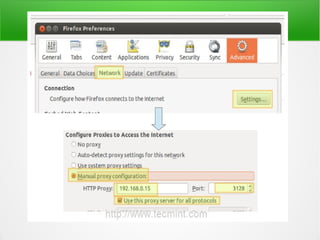
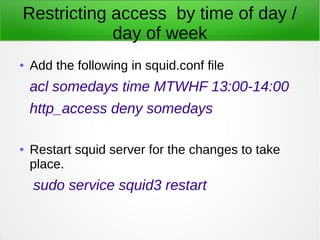
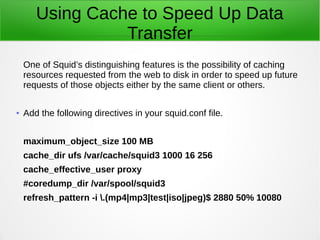
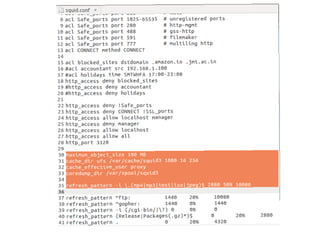
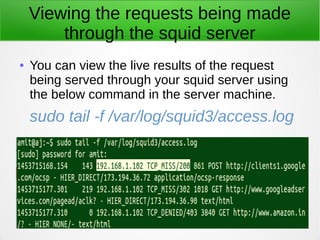
A proxy server acts as an intermediary between clients and the internet or other network resources. Squid is a caching and forwarding proxy server that can improve performance by caching frequently requested files. It can restrict access based on client IP, domain, or time of day. Configuring Squid involves installing it, editing the squid.conf file to define access controls and caching, and configuring clients to use the proxy. The access log can be tailed to view current proxy requests.