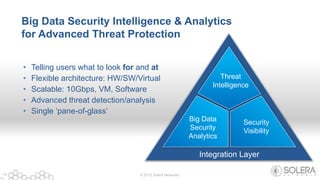
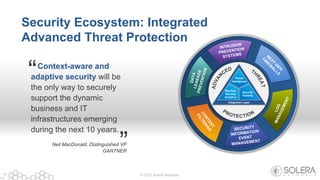
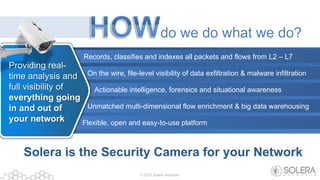
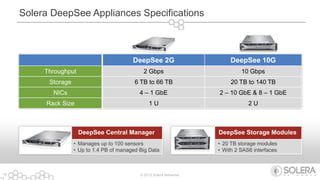
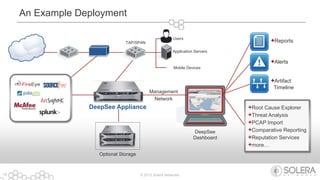
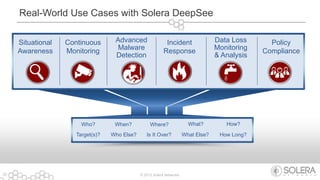
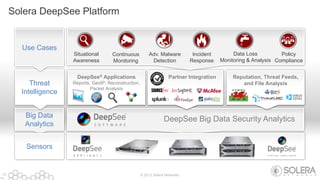
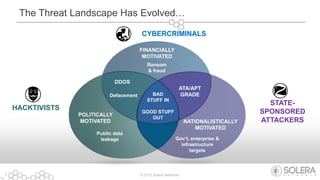
The document discusses Solera Networks' advanced threat protection and big data security analytics solutions aimed at safeguarding organizations from various cyber threats, including state-sponsored attacks and cybercriminal activities. It highlights the importance of real-time visibility and comprehensive analysis to identify and respond to security breaches effectively. Solera's DeepSee platform offers flexible and scalable solutions for monitoring, incident response, and compliance, emphasizing the necessity of context-aware security in today's evolving threat landscape.

![© 2013 Solera Networks5
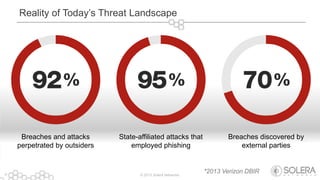
Initial Attack to
Initial Compromise [ 11% 13% 60%] 13% 2% 1% 0%
74%
Window of Opportunity for Advanced Threats*
Seconds Minutes Hours Days Weeks Months Years
Initial Compromise
to Discovery 0% 1% 9% 11% [ 12% 62% 4% ]
78%
*2013 Verizon DBIR](https://image.slidesharecdn.com/soleranetworks-bigdatasecurityintelligenceandanalyticsforadvancedthreatprotection-130508103414-phpapp02/85/Big-Data-Security-Intelligence-and-Analytics-for-Advanced-Threat-Protection-5-320.jpg)