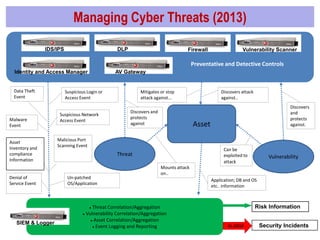
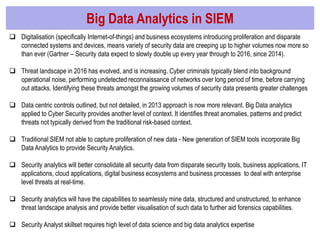
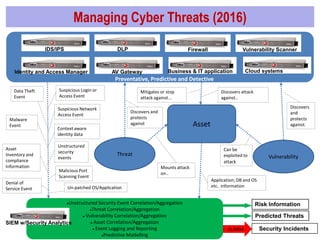
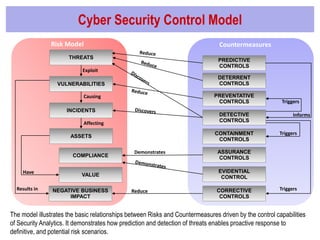
The document discusses the evolution of cyber security in relation to big data analytics, emphasizing the need for advanced analytical tools to address increased and evolving cyber threats. It highlights the limitations of traditional SIEM systems and advocates for integrating big data analytics to enhance threat detection and response capabilities. The conclusions stress the importance of adopting a more data-centric and agile approach to security intelligence, while also suggesting future investments in security analytics capabilities.