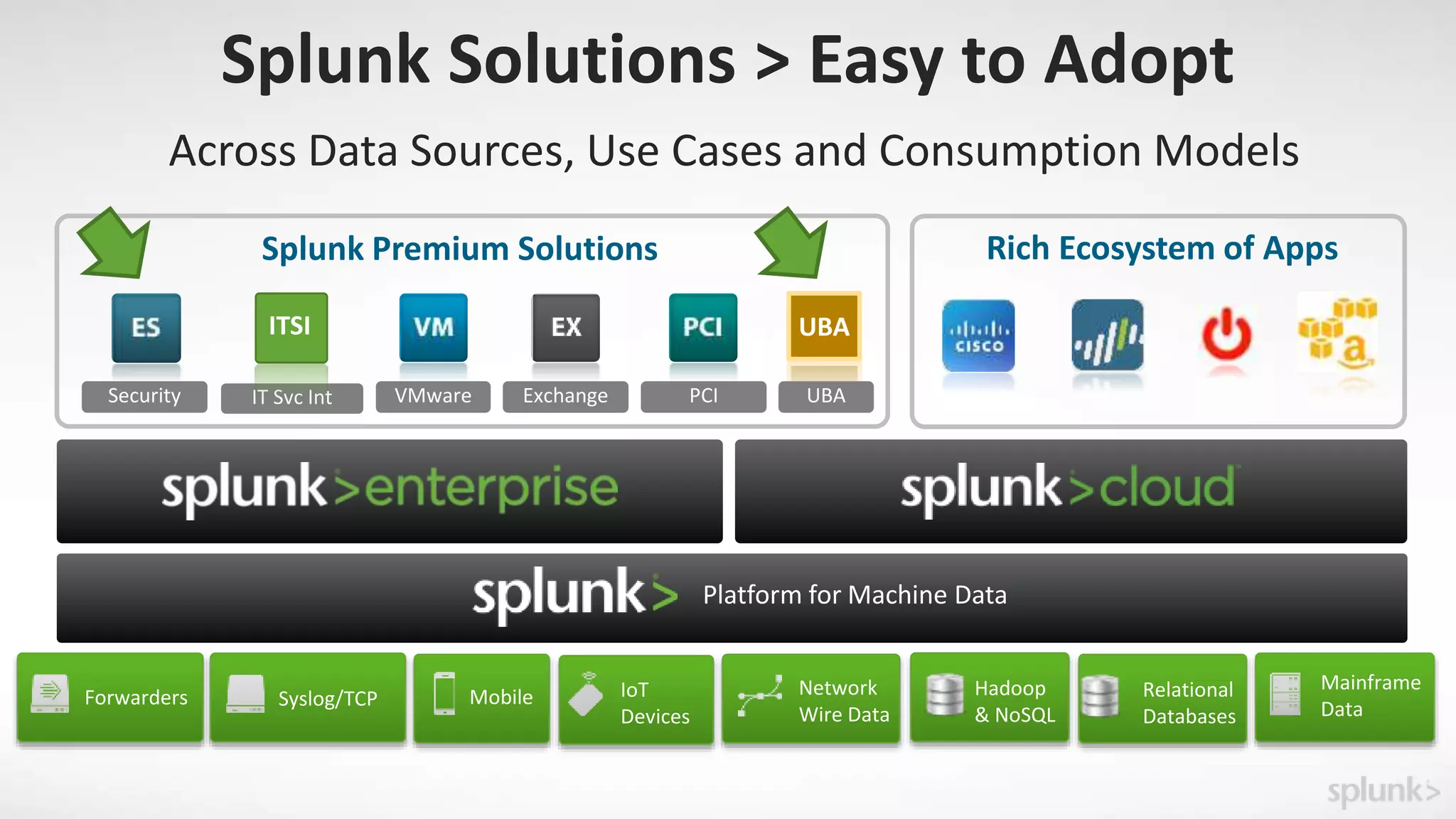
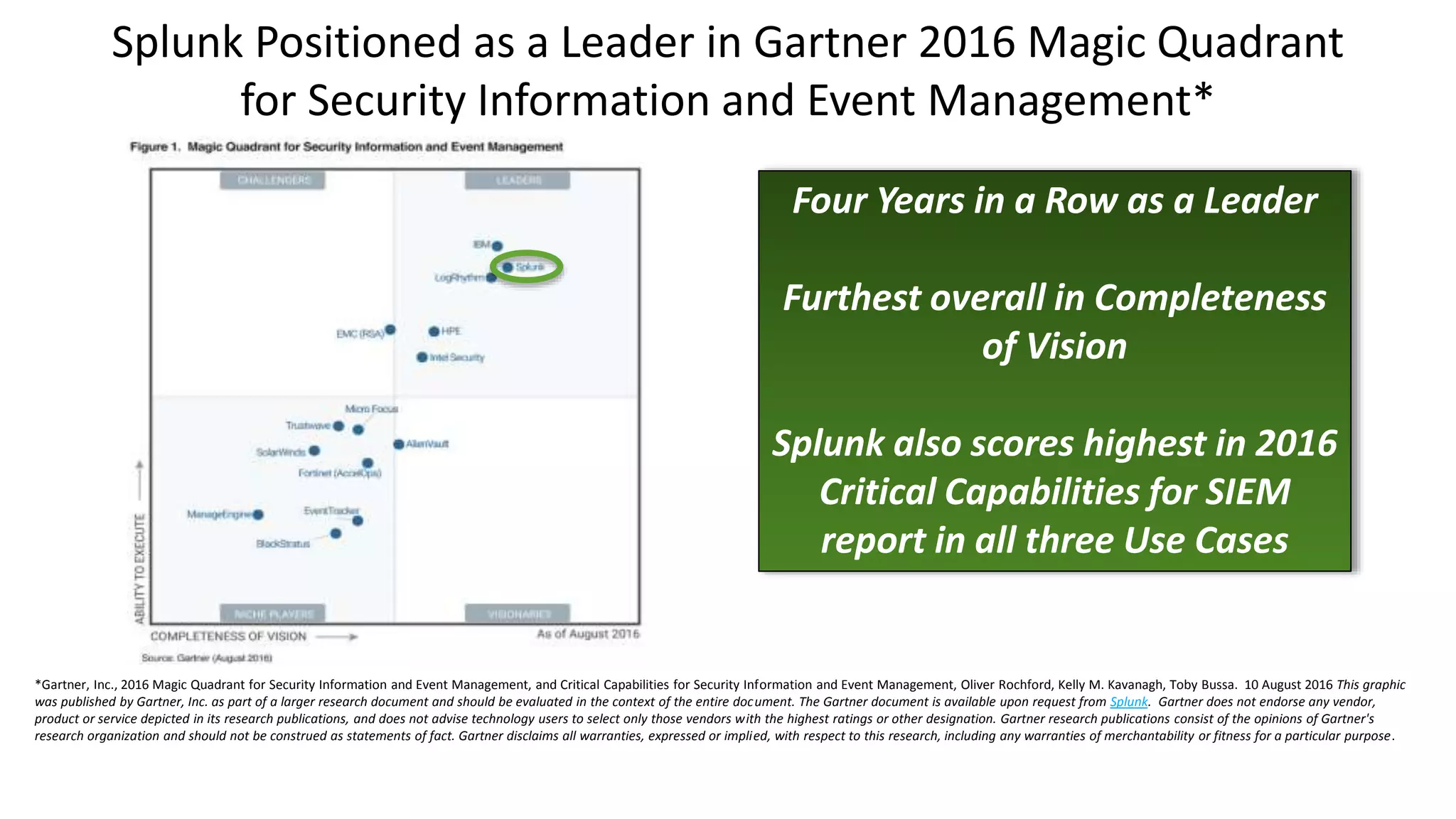
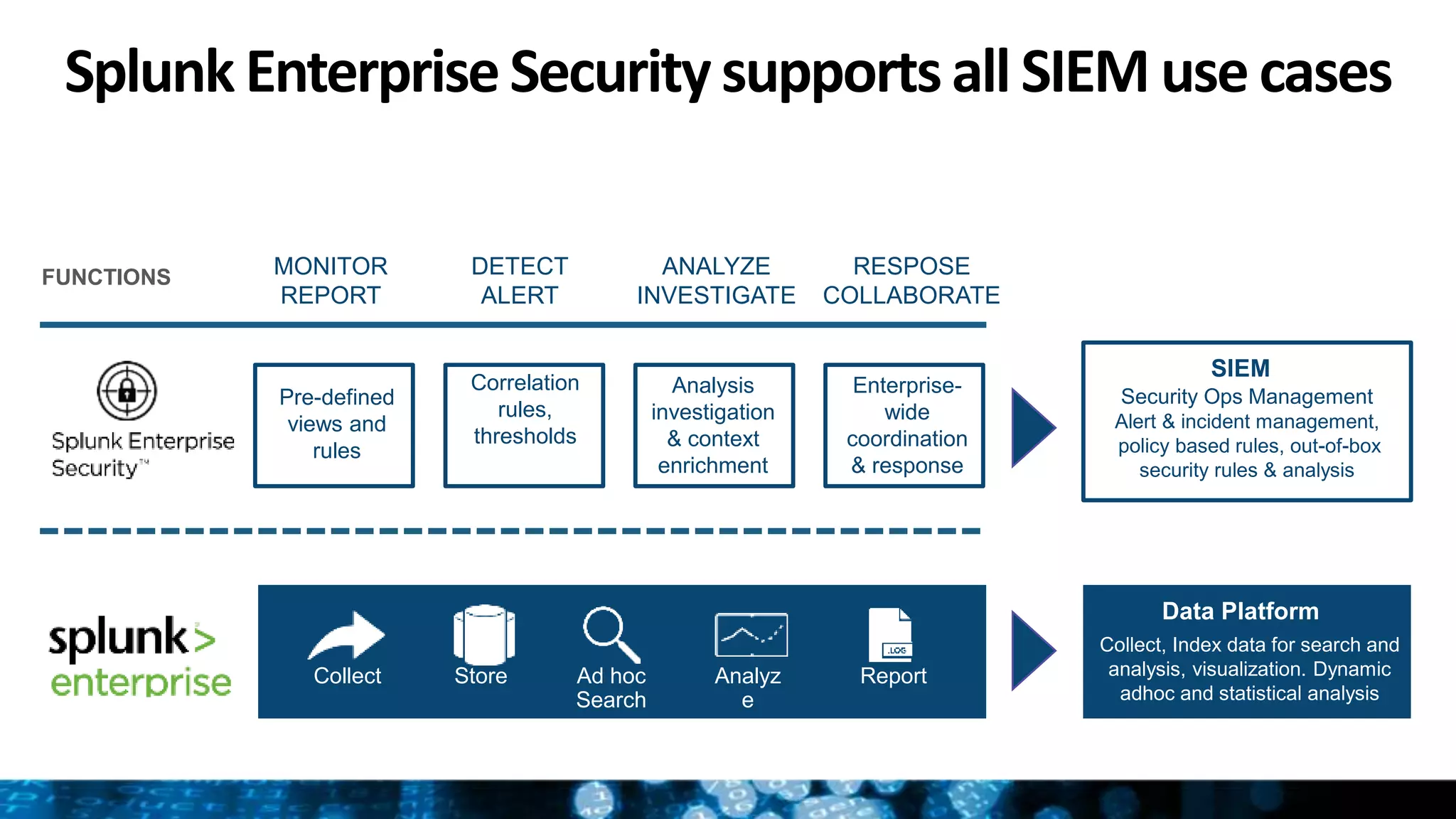
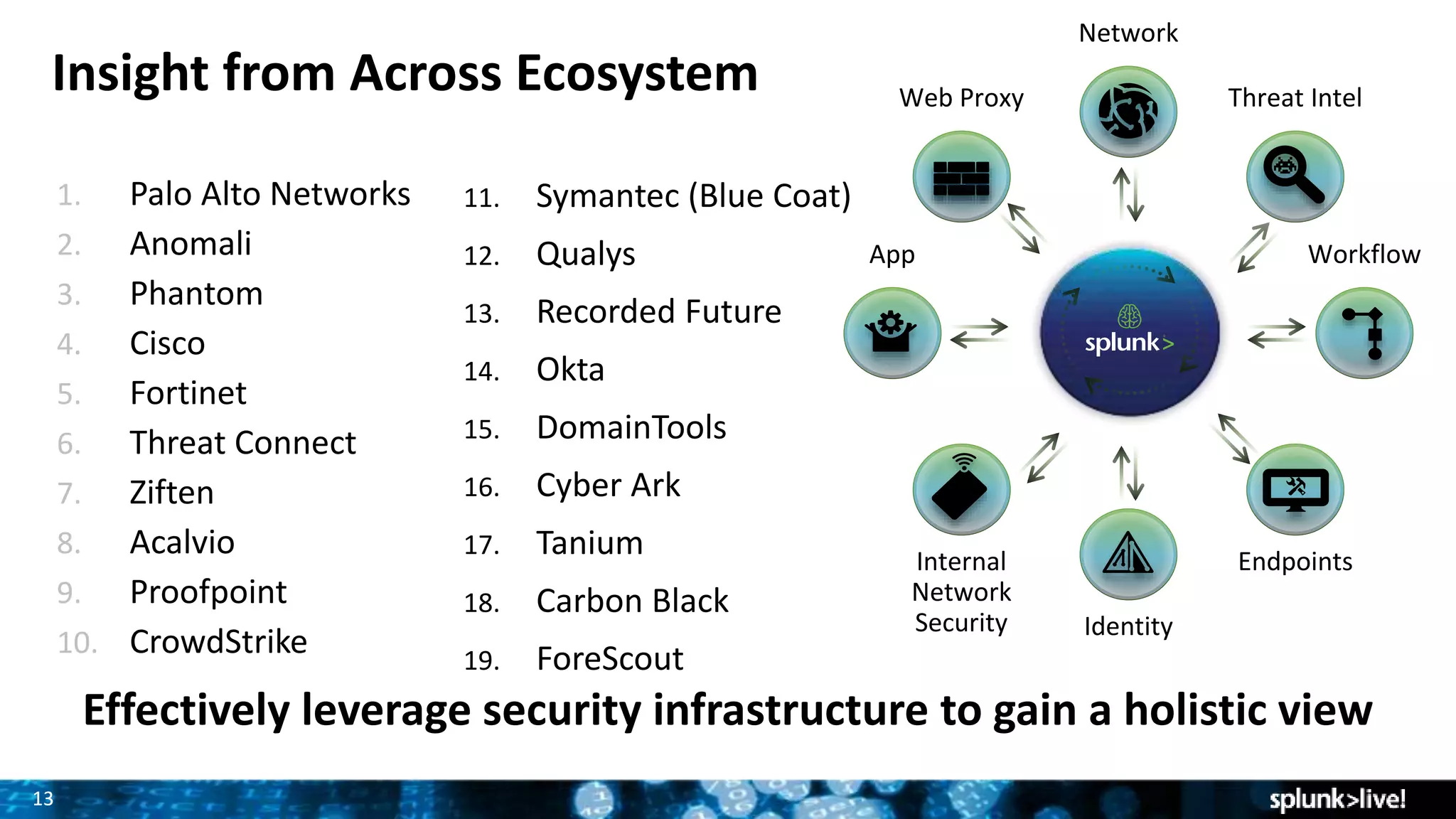
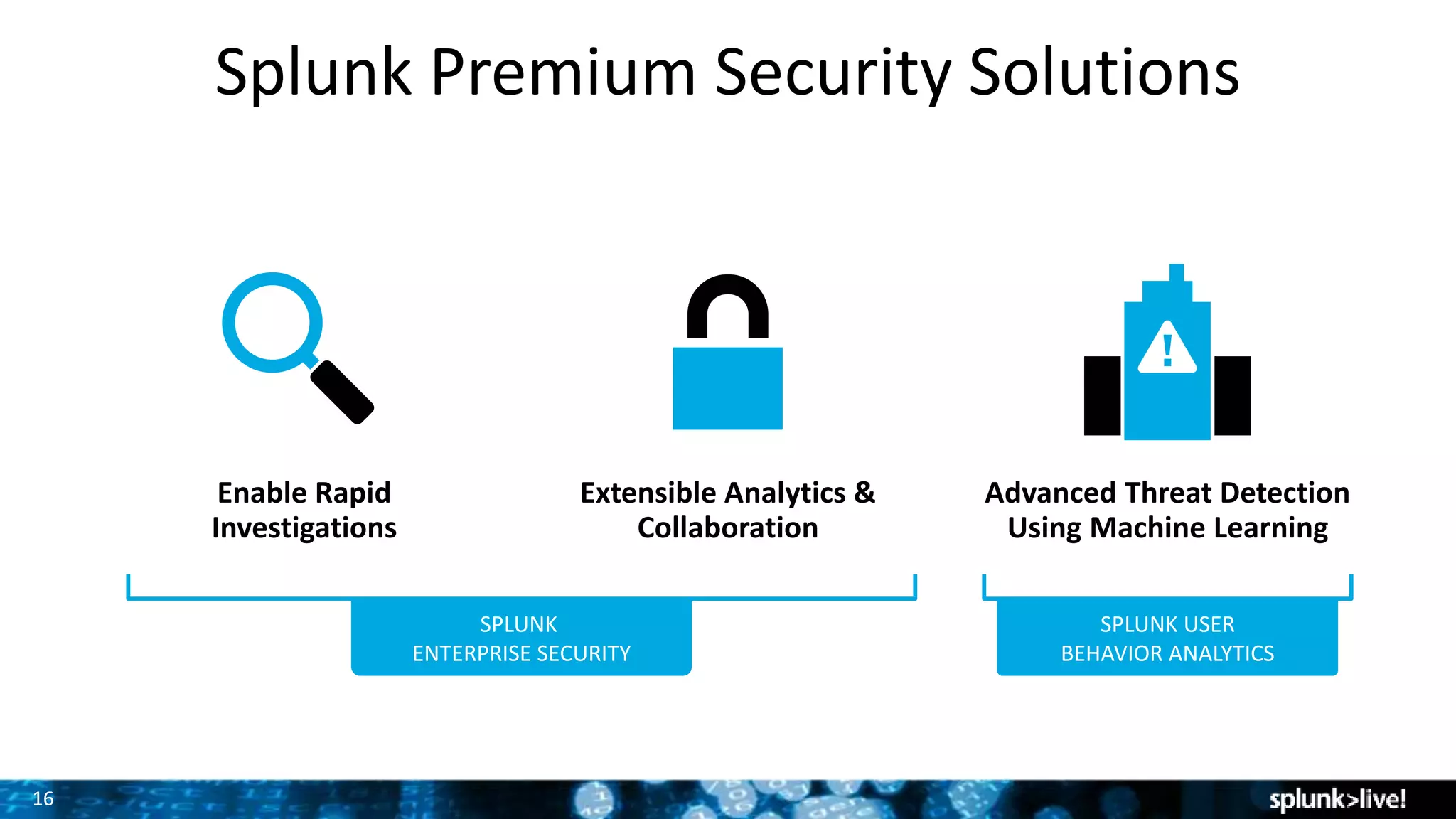
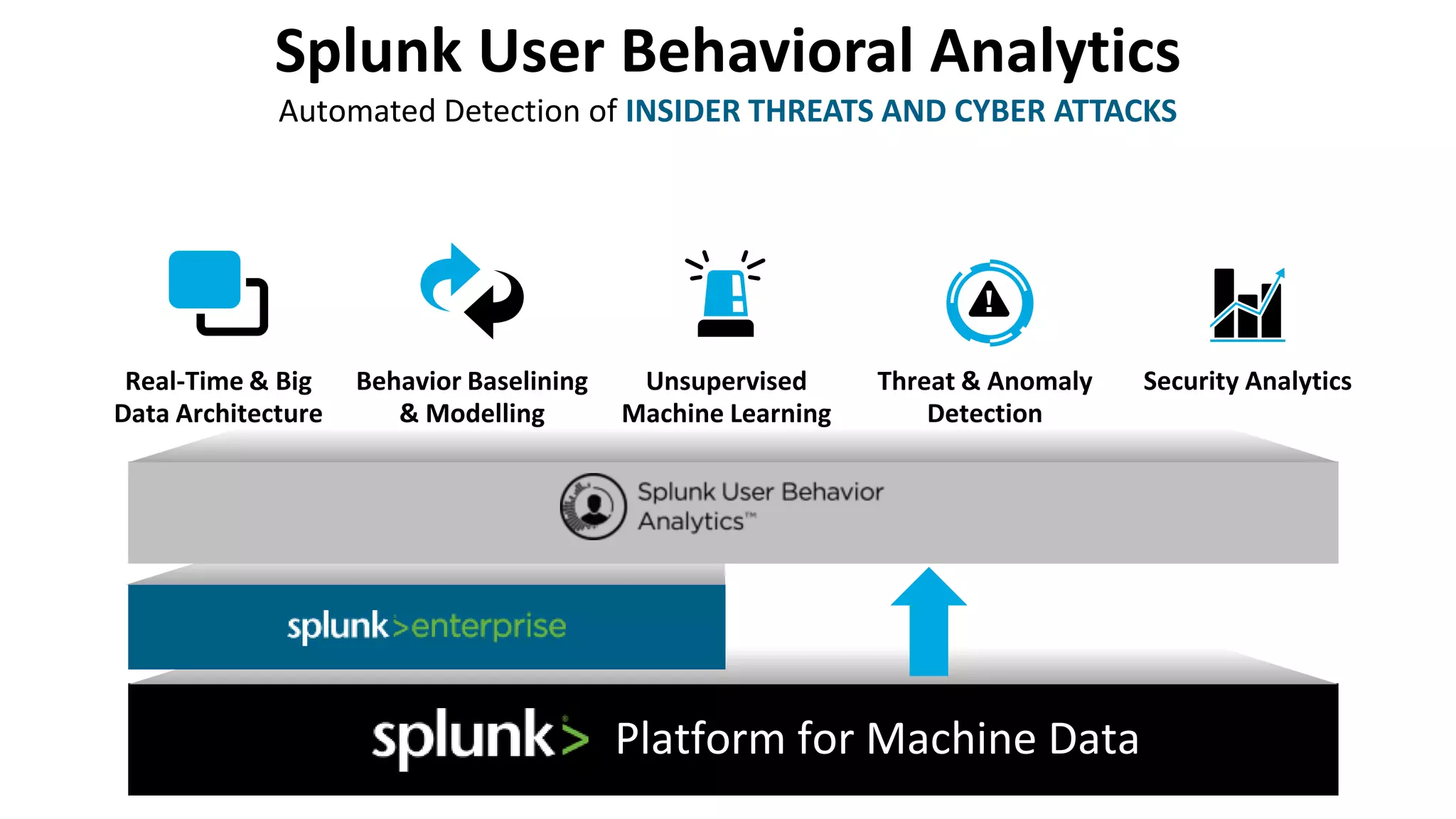
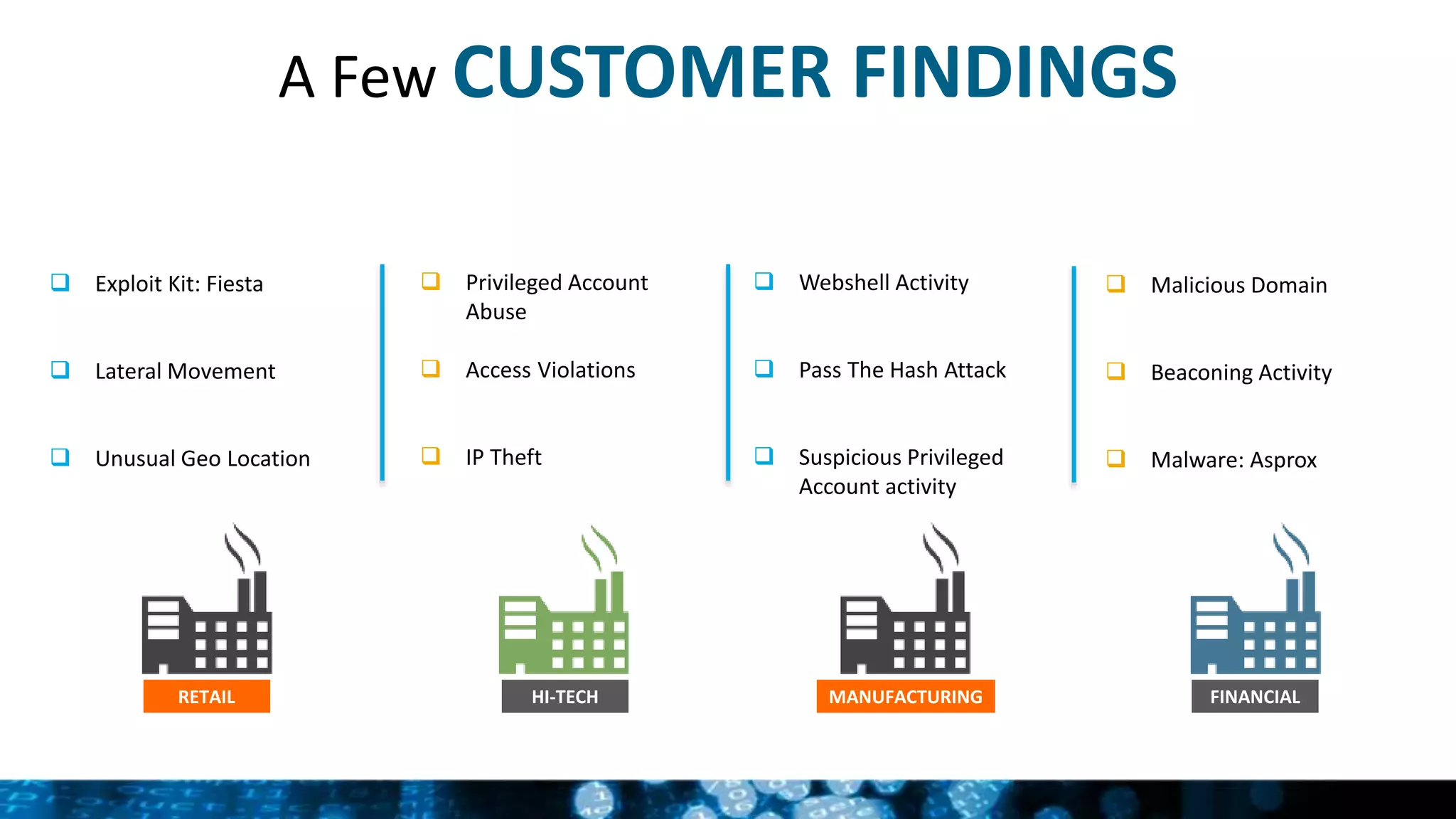
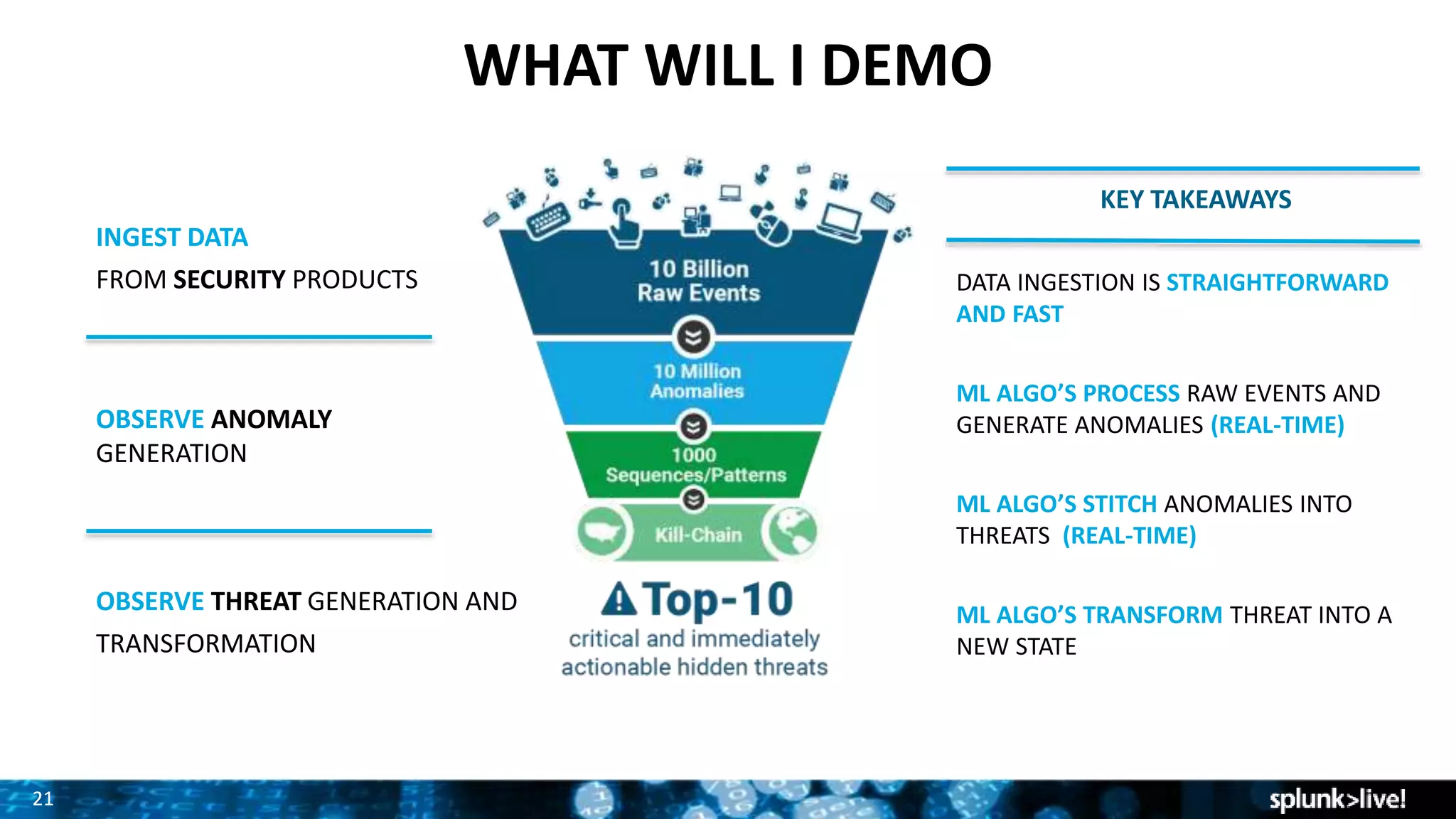
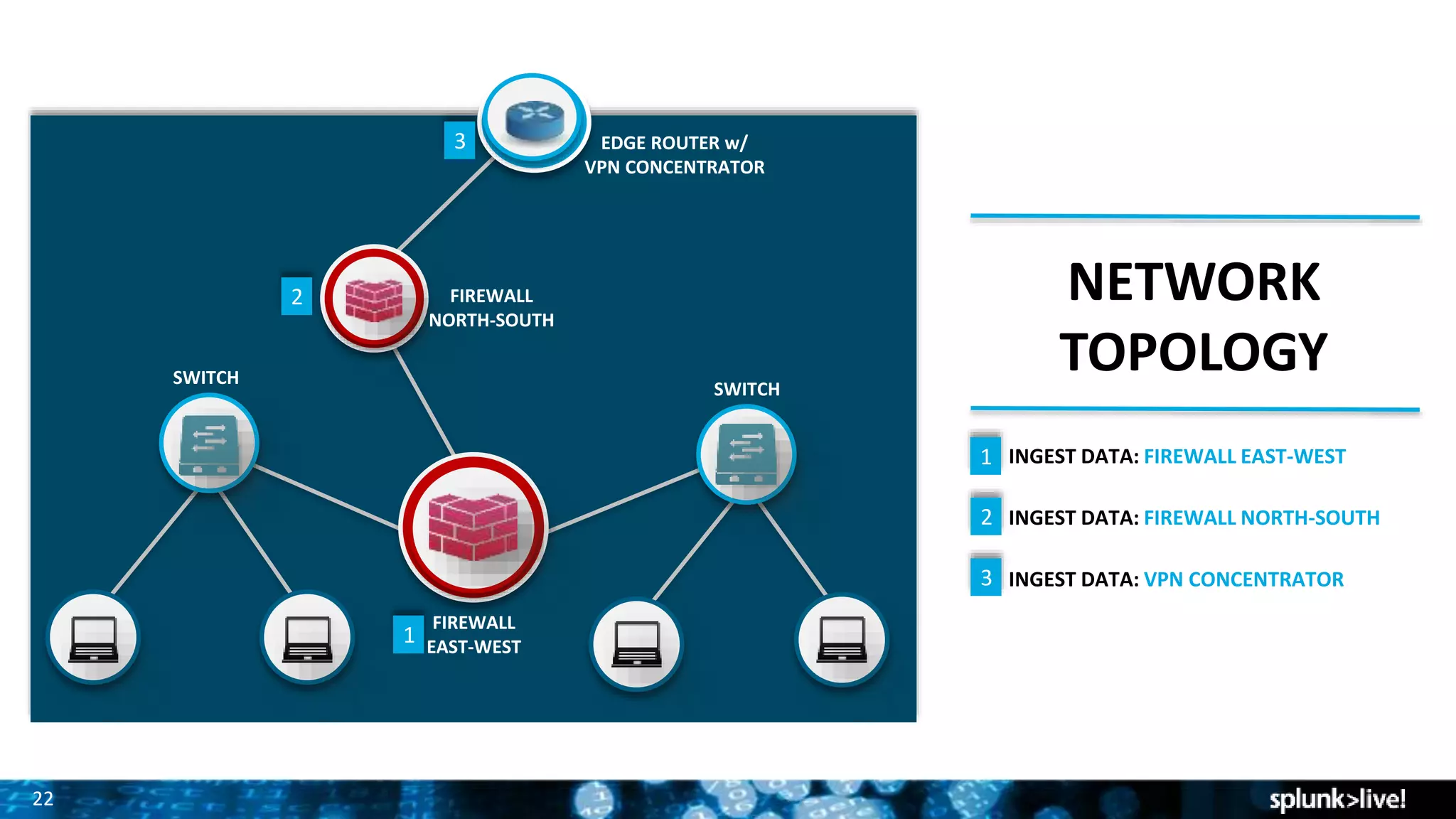
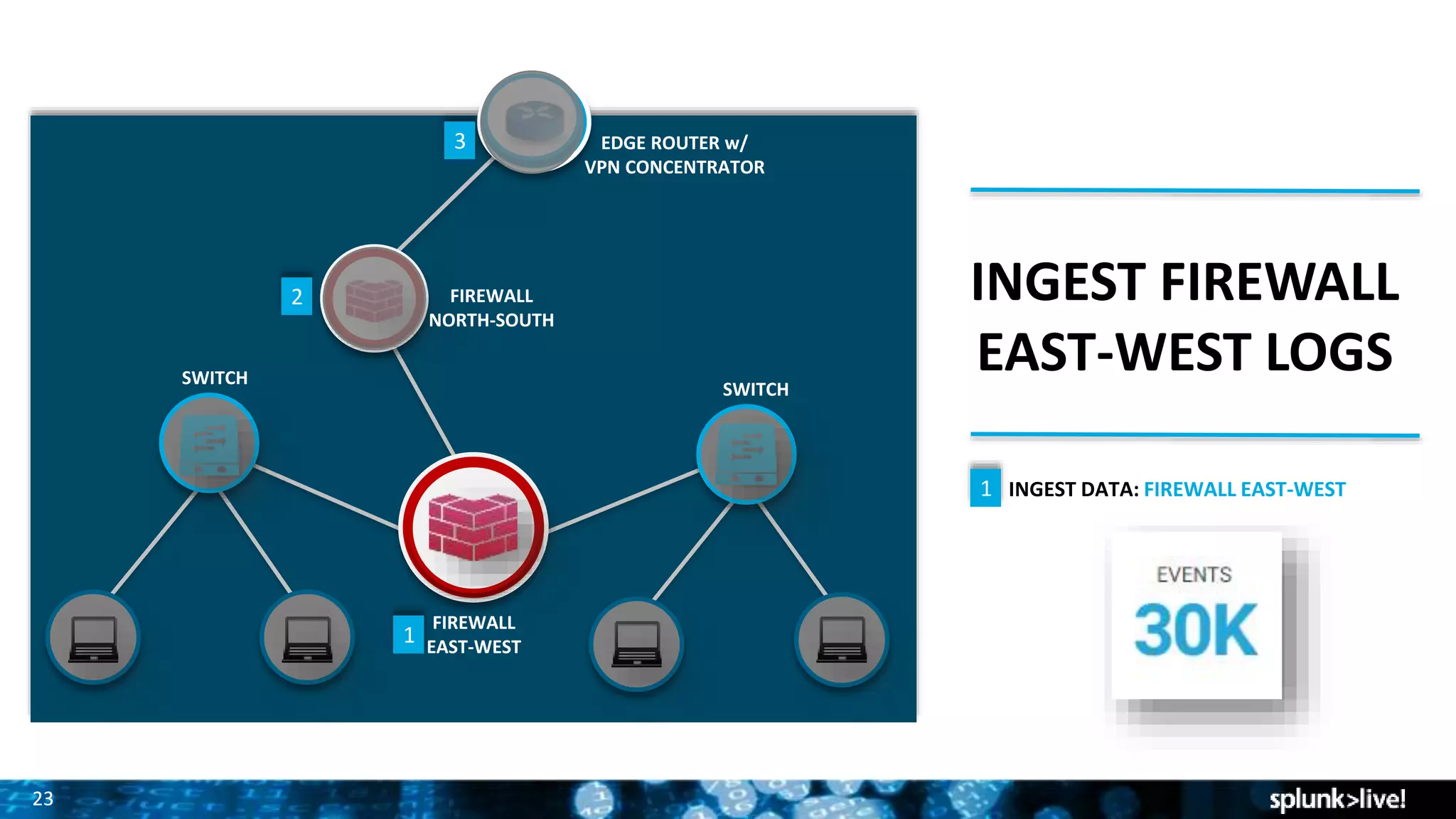
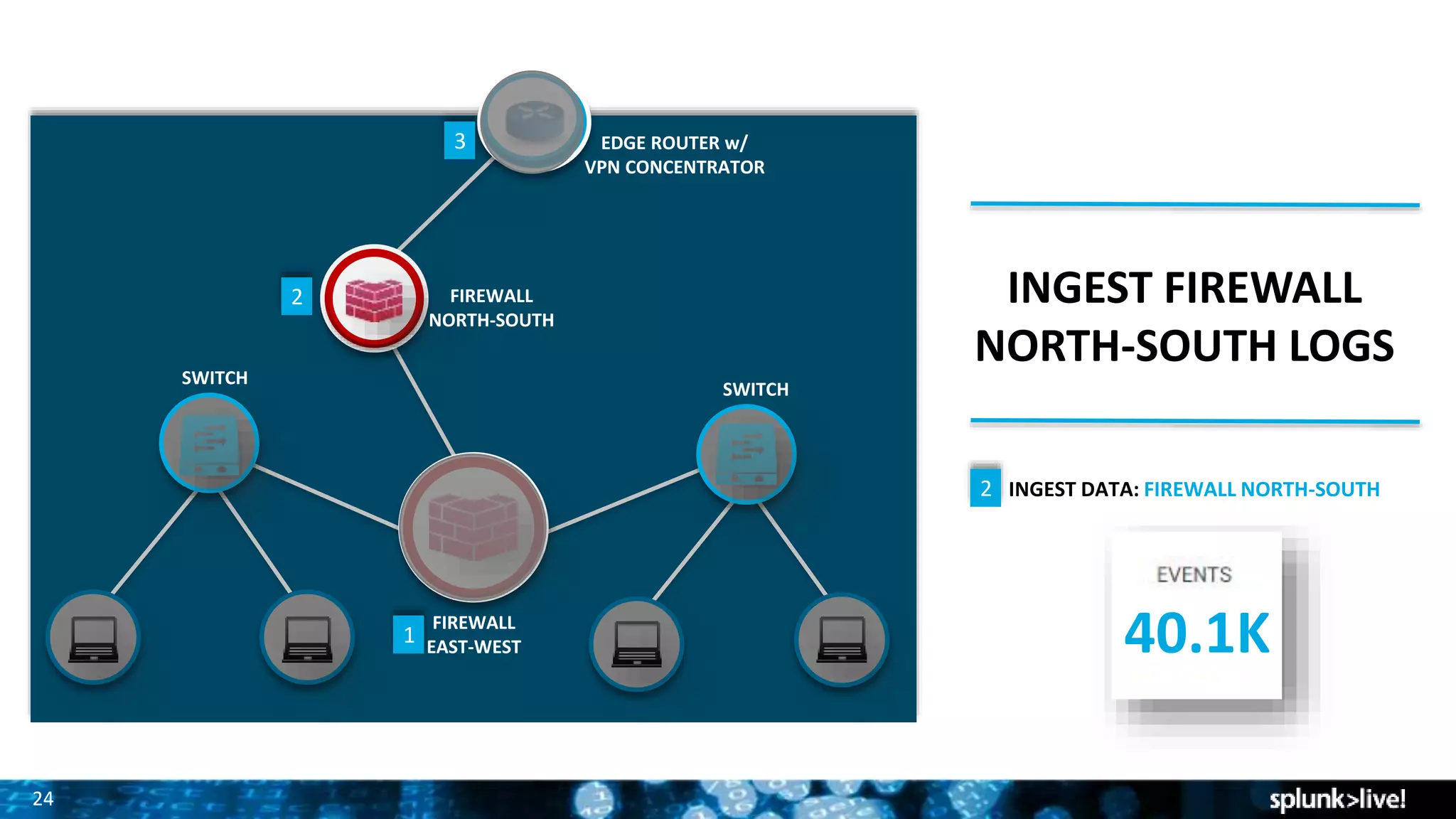
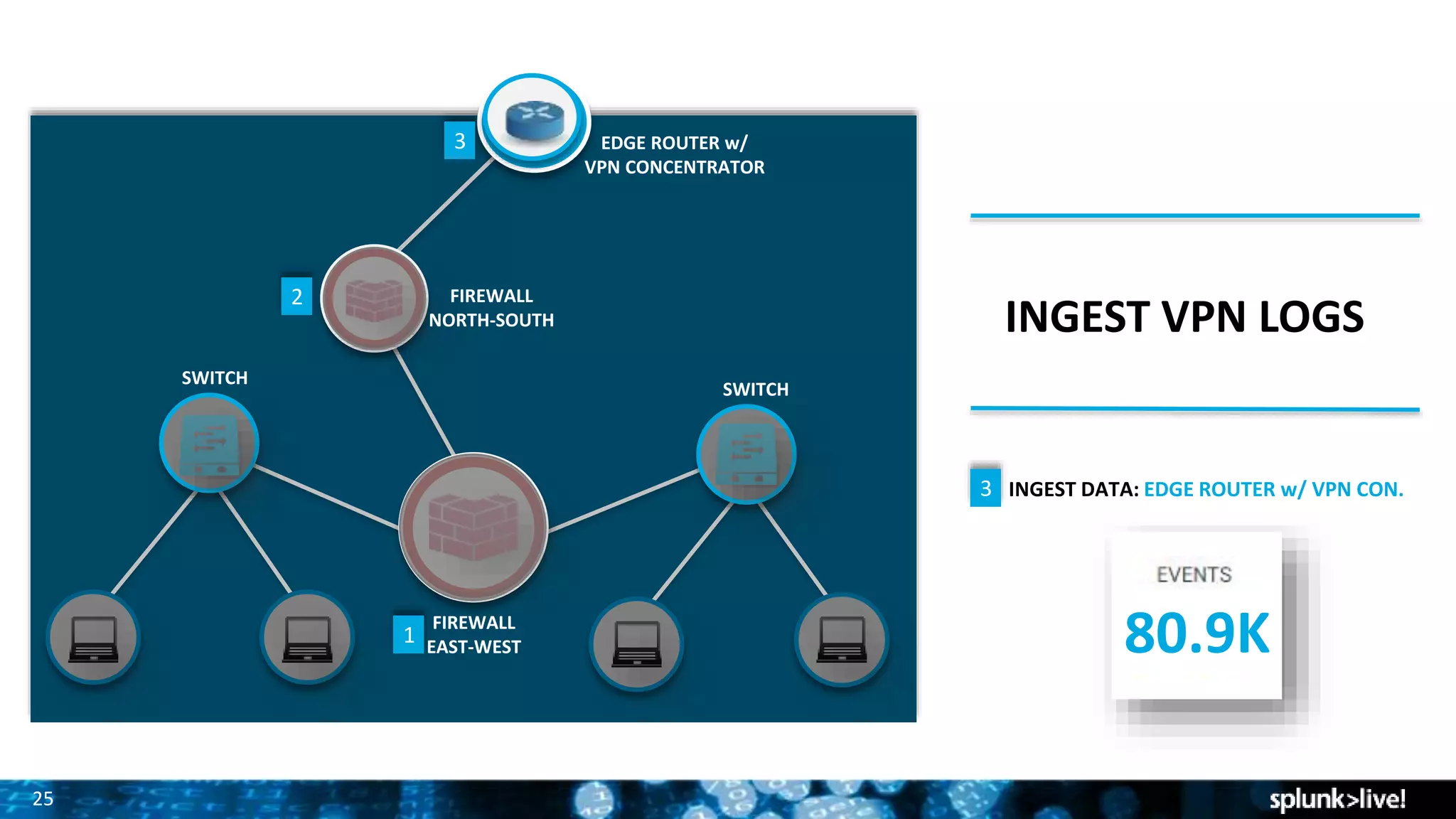
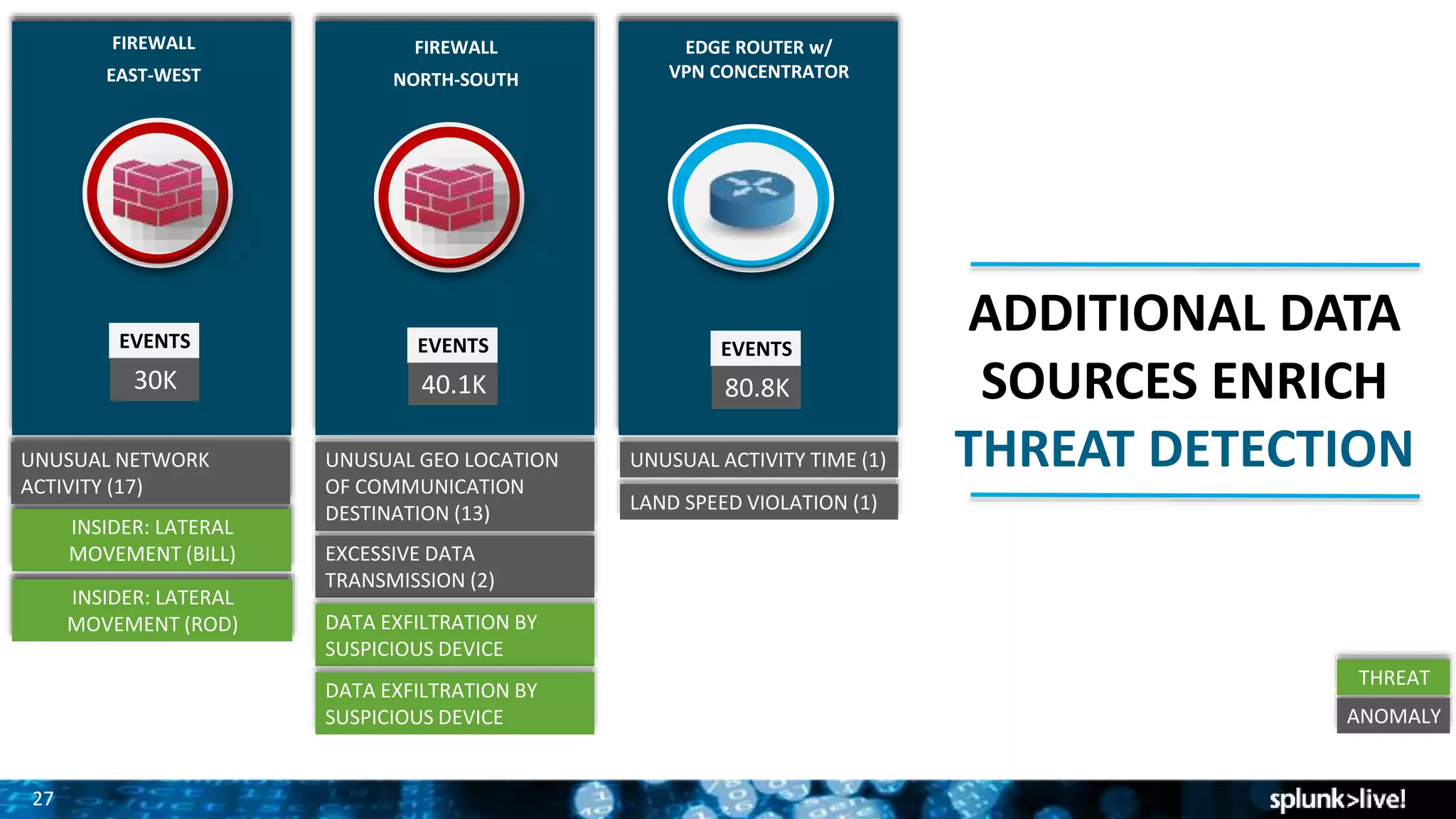
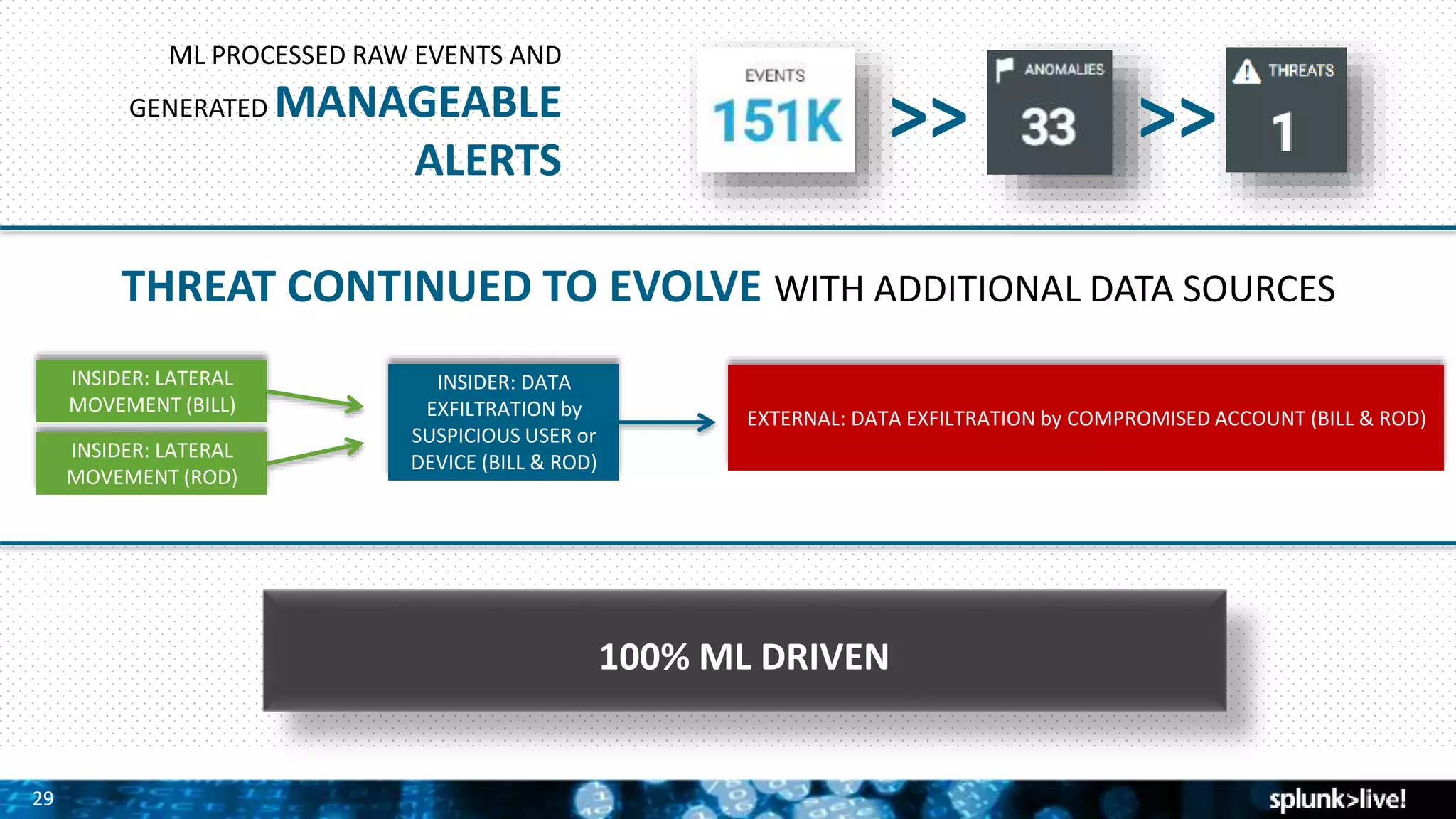
Splunk provides enterprise security solutions that leverage machine data for threat detection and user behavior analytics. The platform enhances operational efficiency through automated response actions and enables organizations to detect various security threats using advanced analytics and machine learning. Splunk's enterprise security has been recognized as a leader in the SIEM space, continuously evolving with new features to improve monitoring and analysis capabilities.