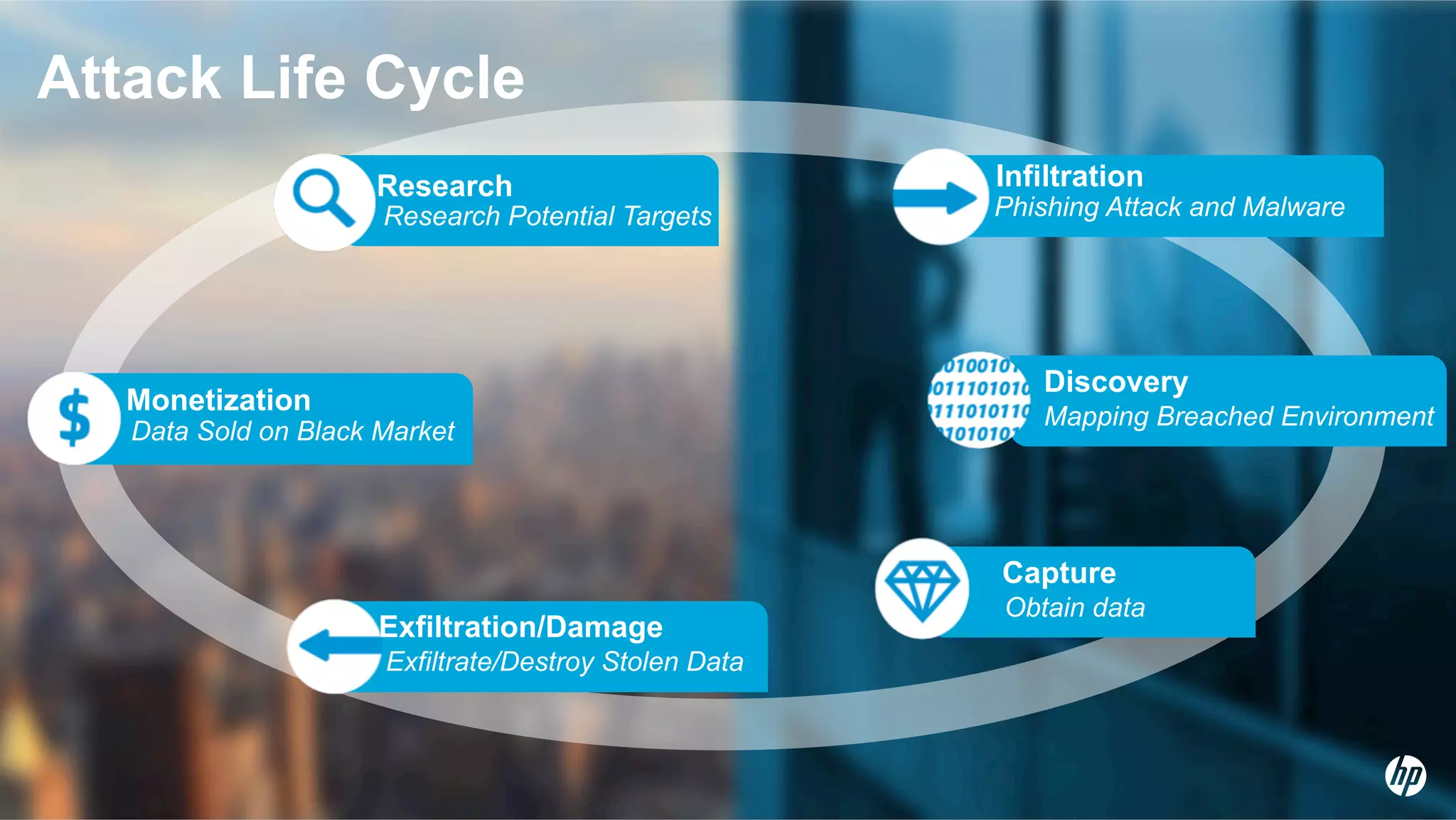
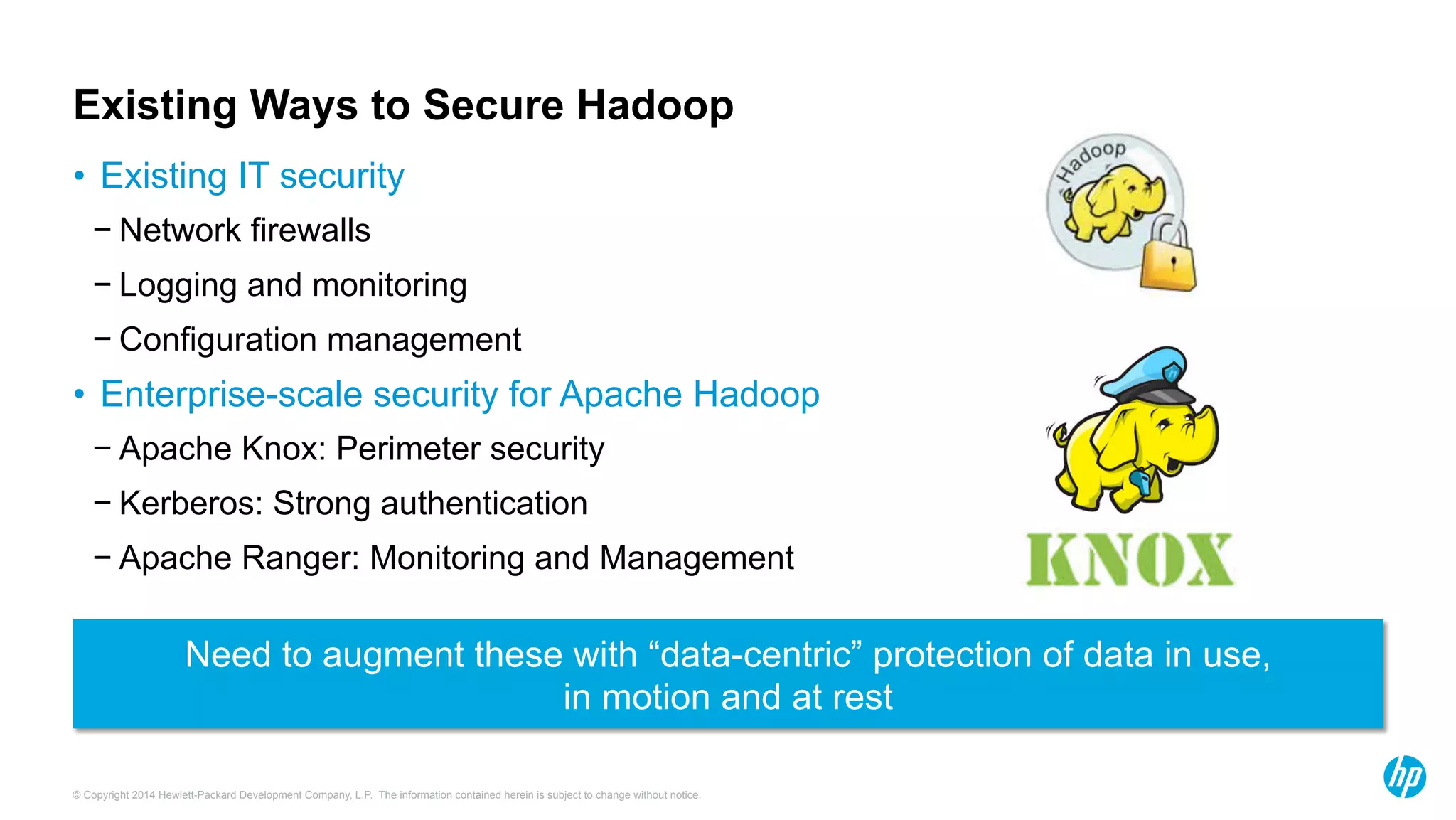
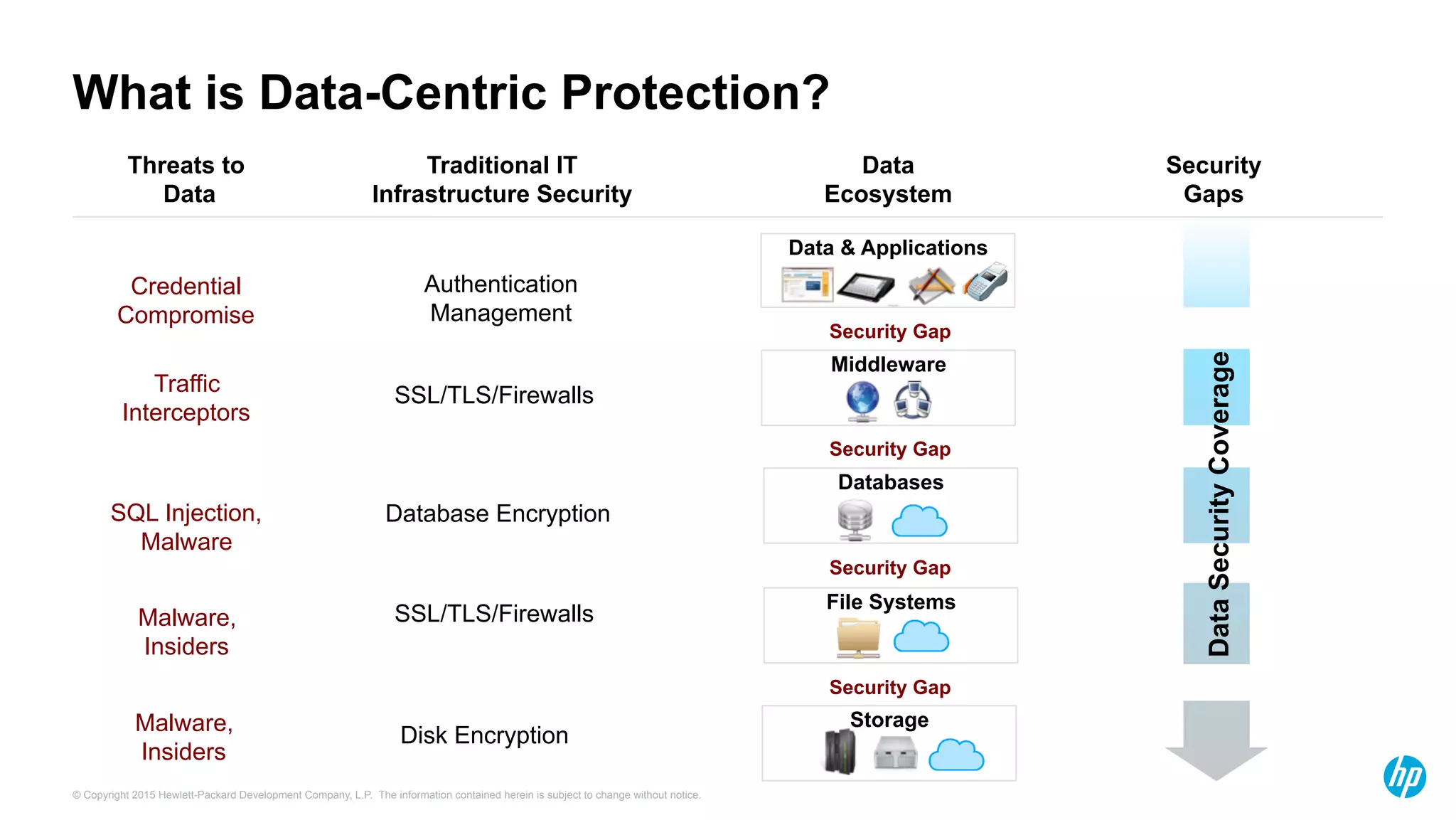
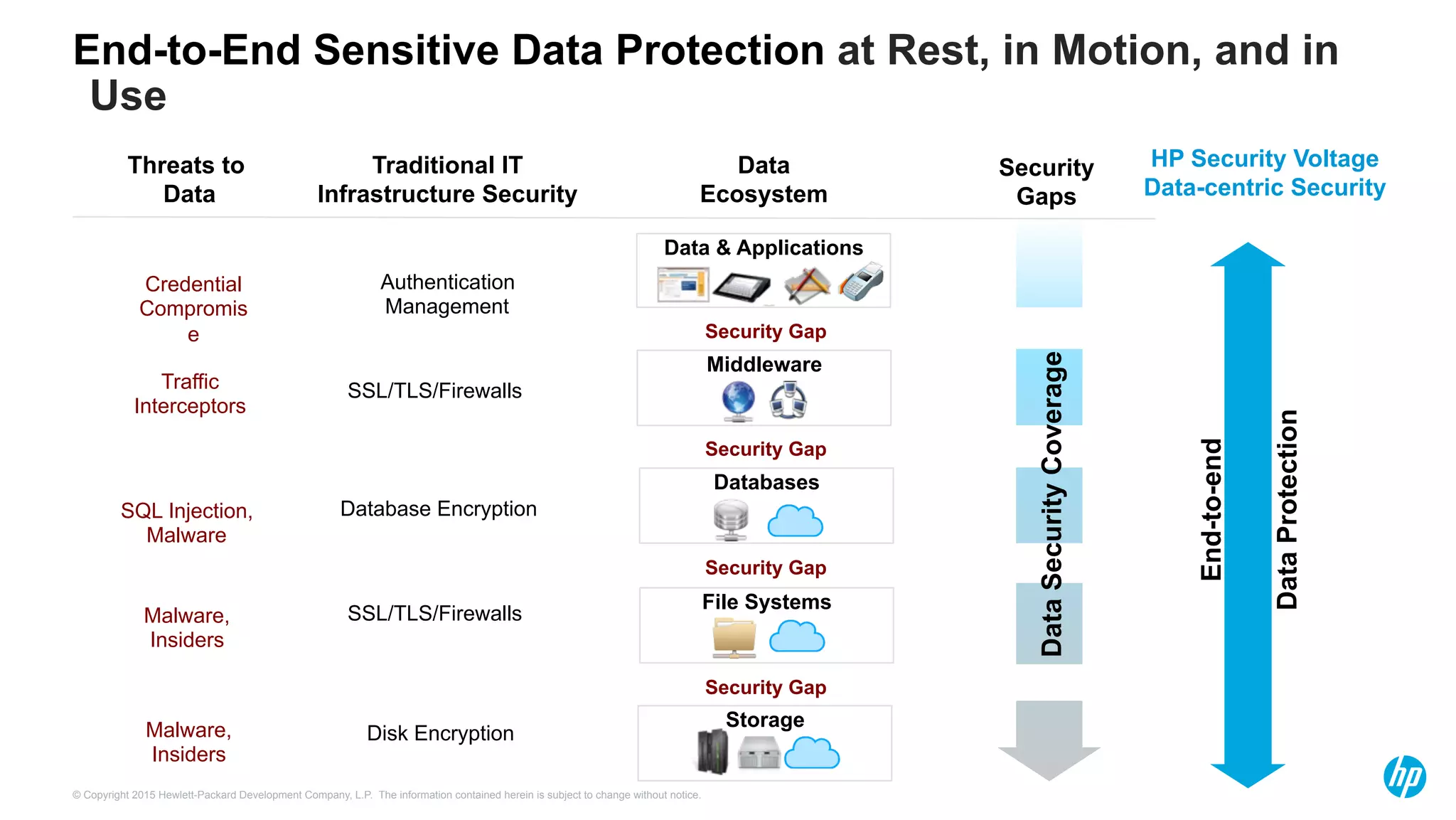
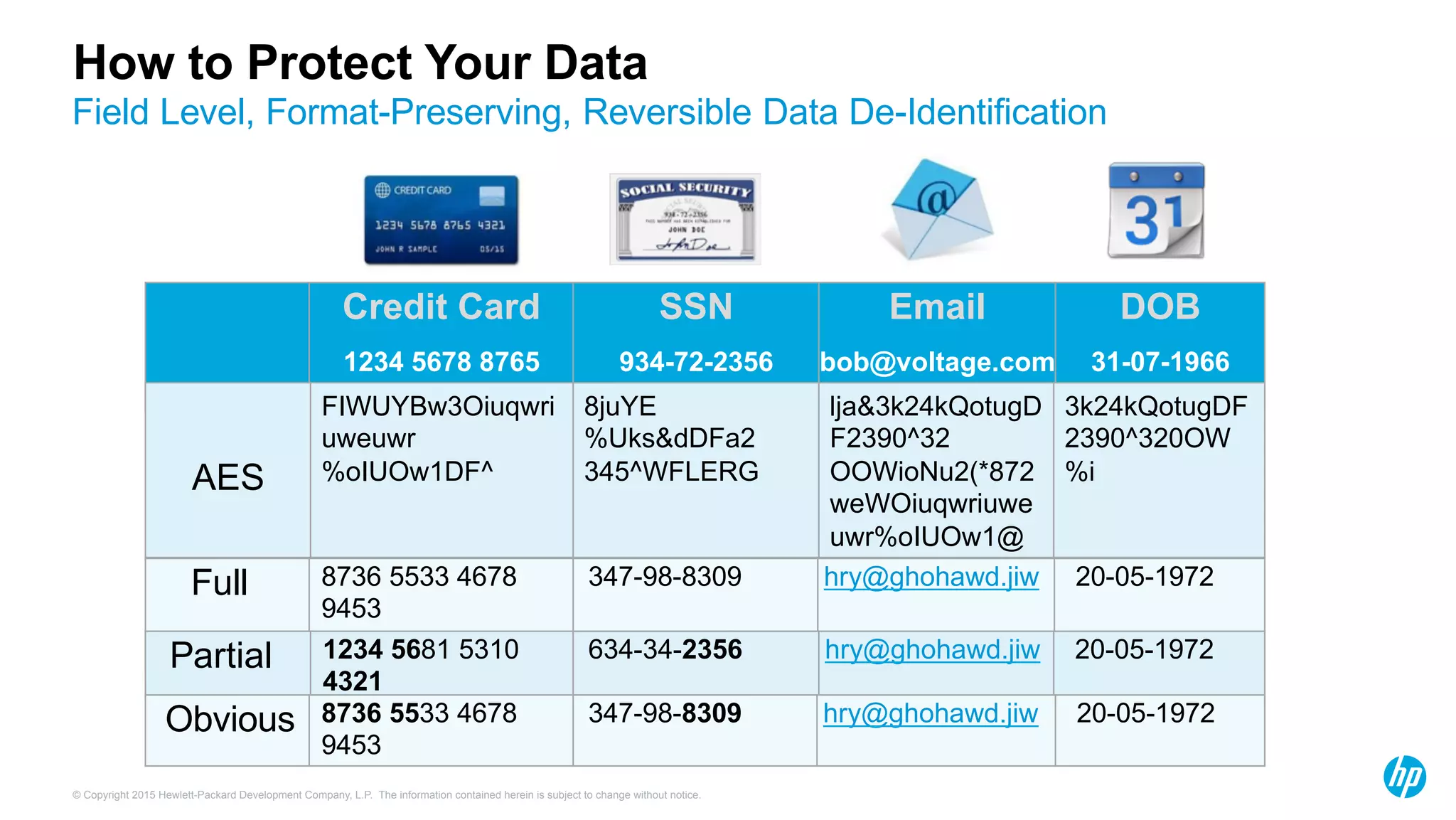
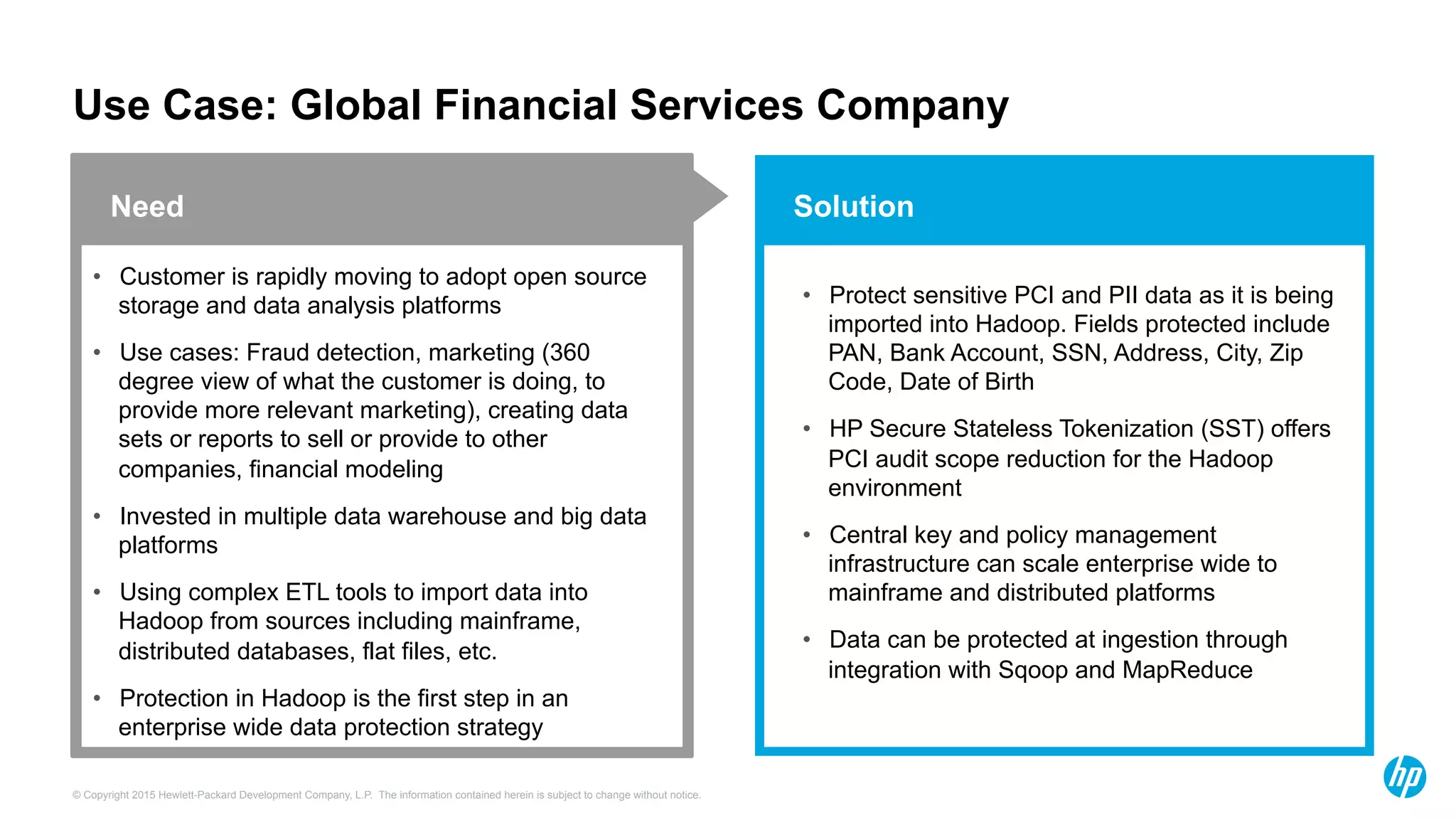
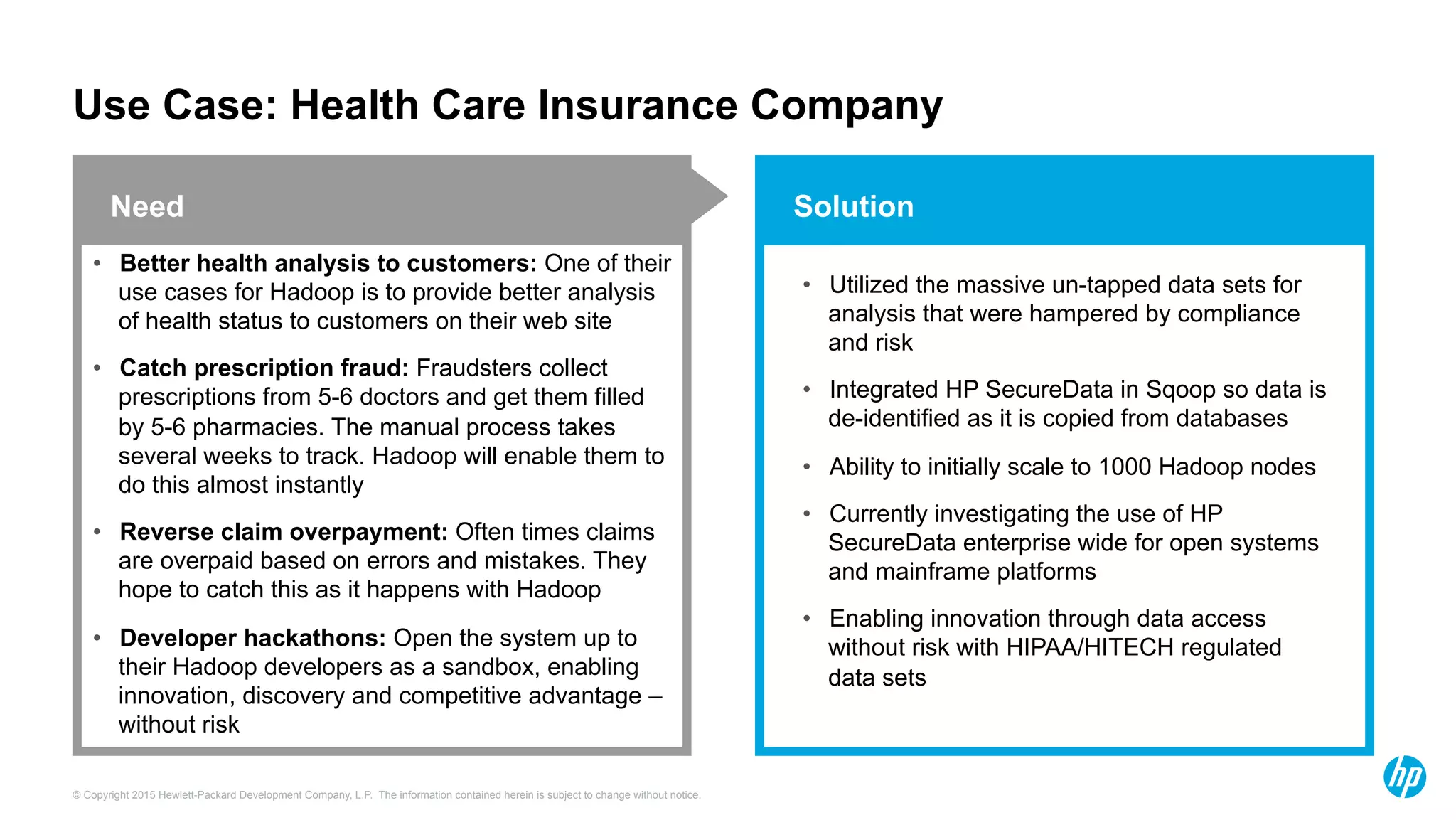
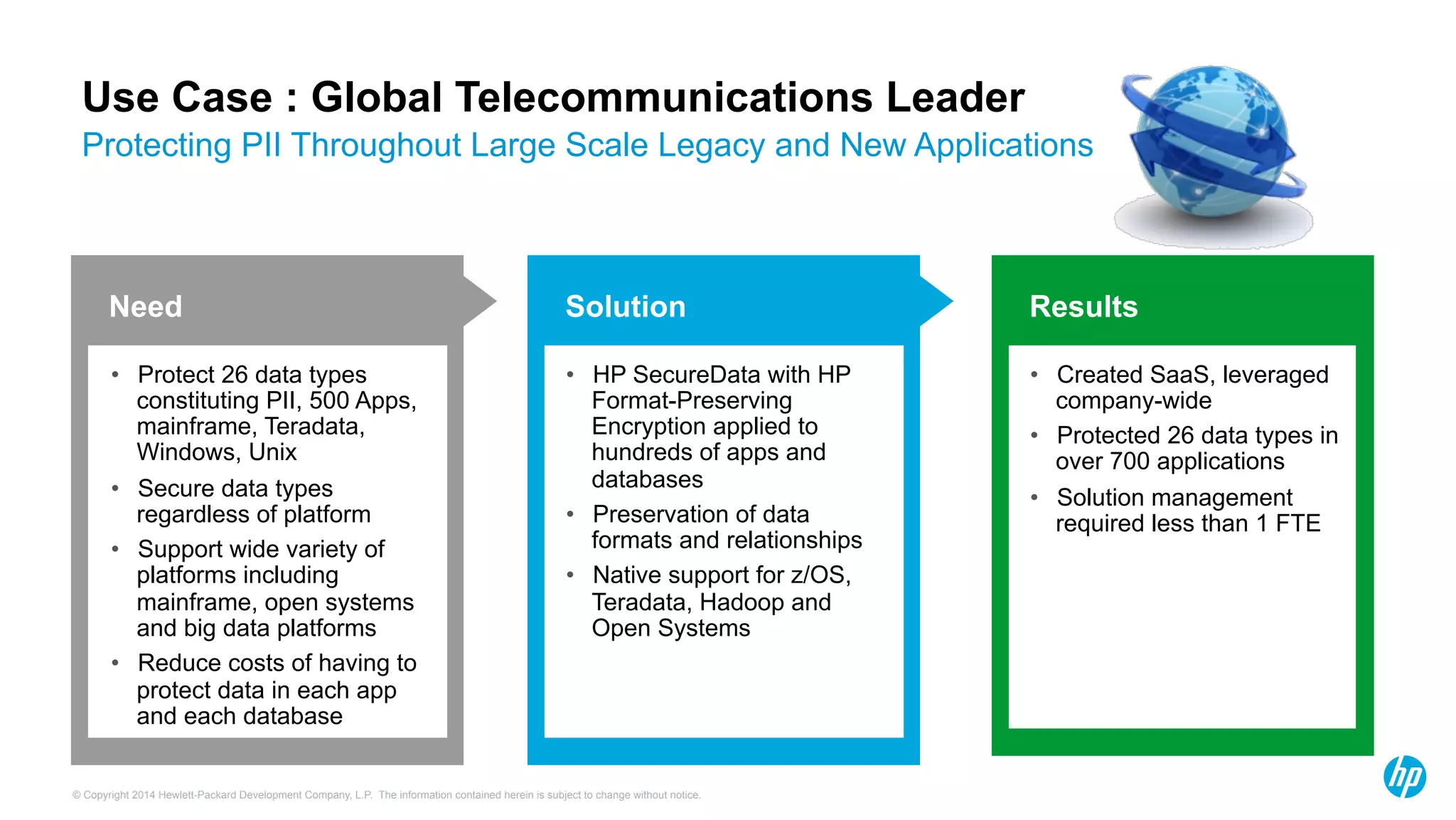
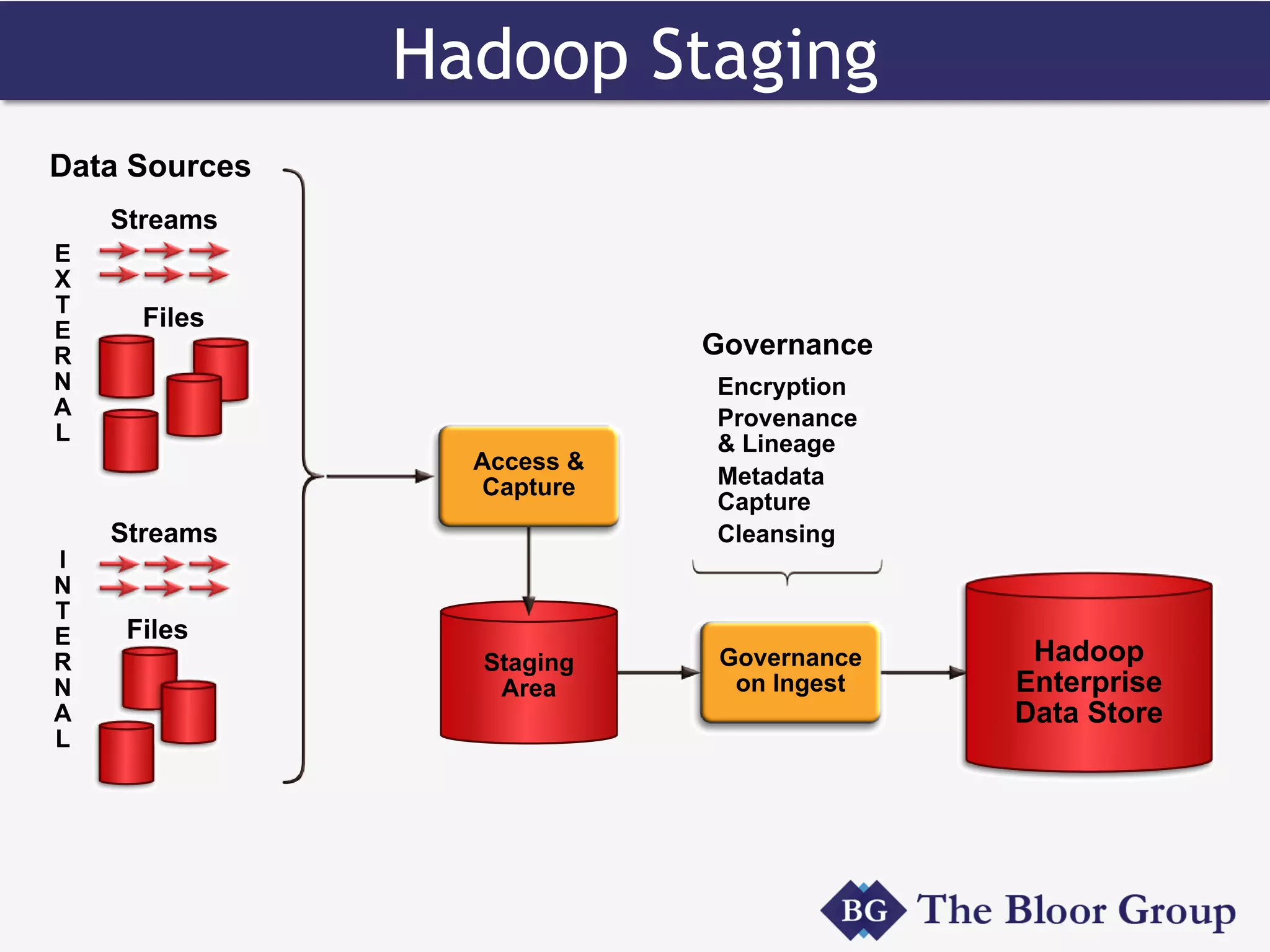
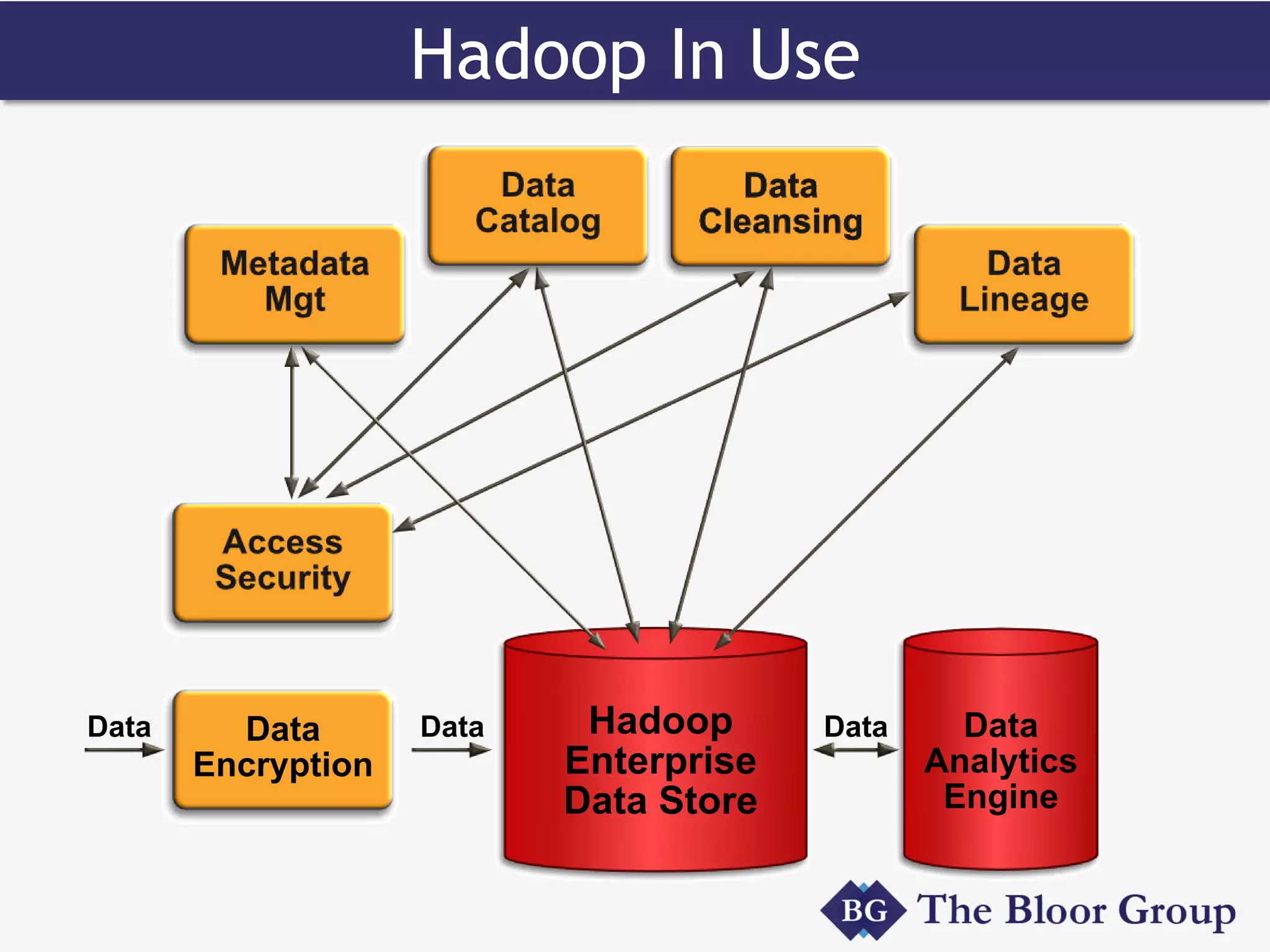
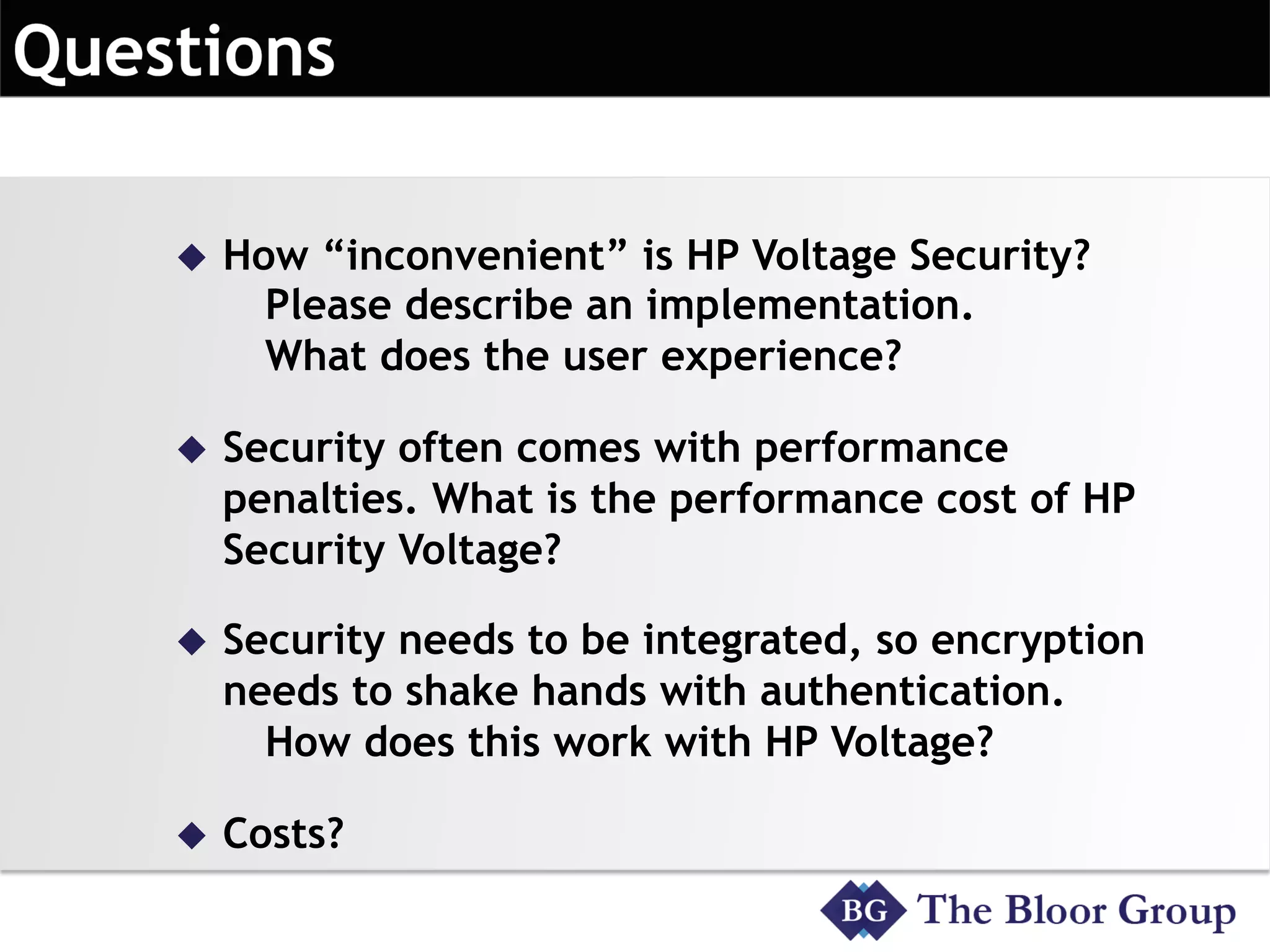
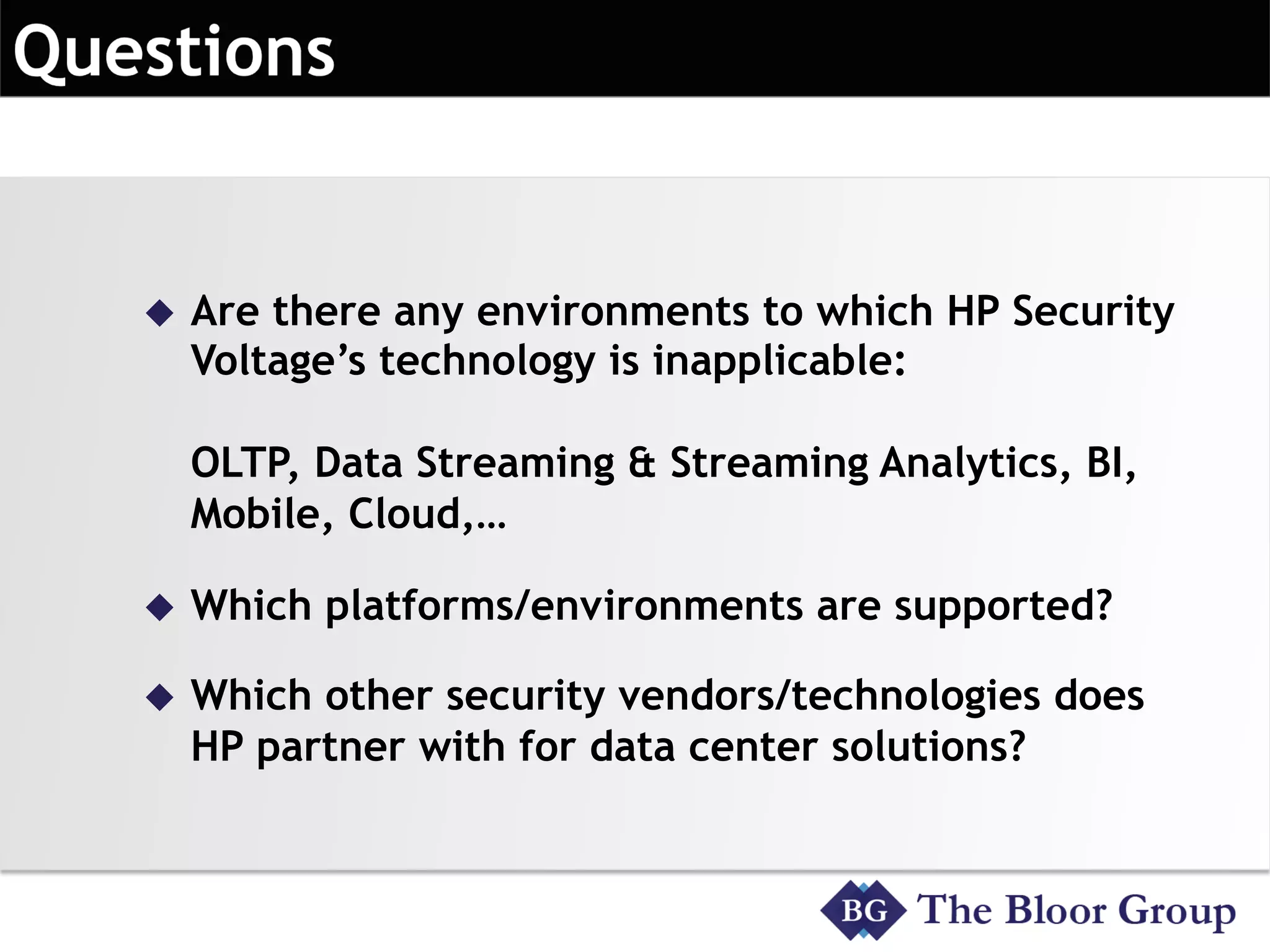
HP Security Voltage provides data-centric security solutions to protect sensitive data in Hadoop environments. Their solutions leverage tokenization and encryption to safeguard data at rest, in motion, and in use across the data lifecycle. They presented use cases where their technology helped secure financial, healthcare, and telecommunications customer data in Hadoop and other platforms. Questions from analysts focused on implementation experience, performance impacts, integration with authentication, costs, and supported environments and partnerships.