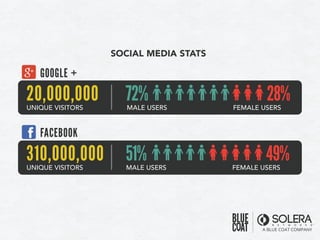
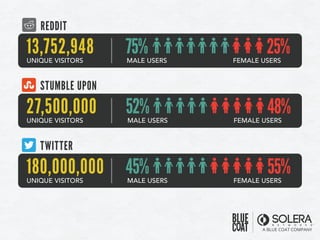
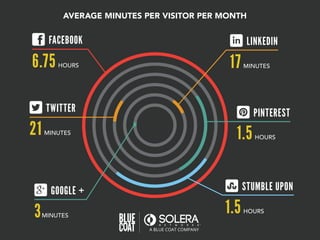
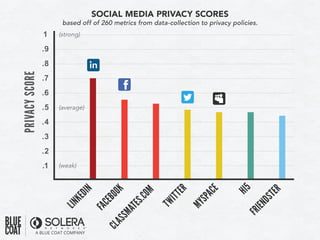
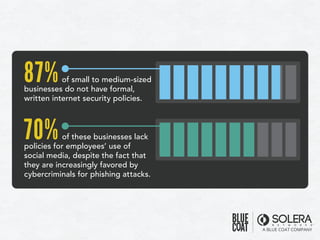
The document discusses various aspects of social media security, highlighting statistics and privacy issues across popular platforms like Facebook, Twitter, and LinkedIn. It outlines the risks of cyber threats such as phishing, impersonation, and botnets, emphasizing the lack of security policies among small to medium-sized businesses. Additionally, it notes alarming trends in user behavior regarding data sharing and protection, raising concerns about overall privacy and security in social networks.