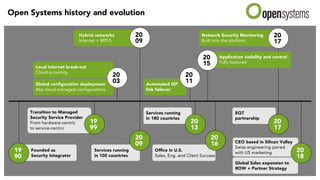
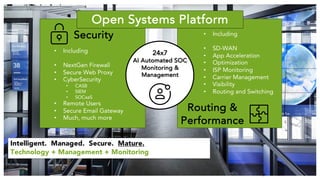
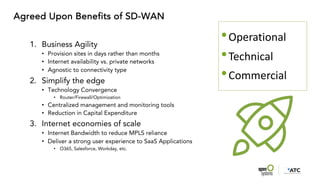
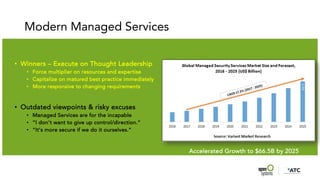
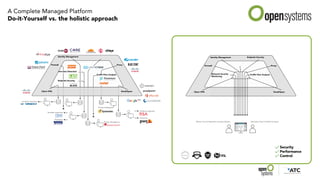
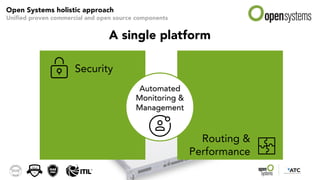
The document outlines the evolution and advantages of managed SD-WAN services offered by Open Systems. It debunks common SD-WAN myths, discusses its adoption drivers, and highlights the importance of a holistic approach to network security and management. Additionally, it emphasizes the need for unified technology strategies in response to emerging networking and security challenges.