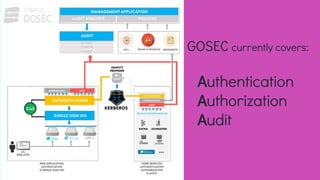
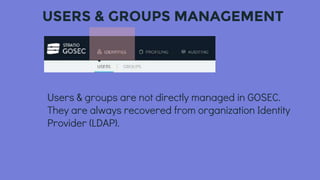
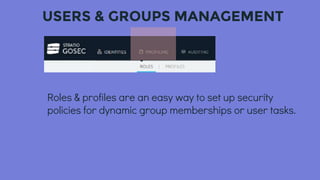
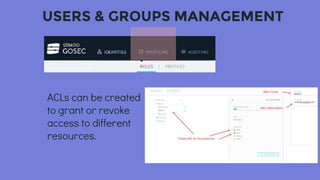
This document discusses security and governance considerations for big data. It notes that while many businesses use big data, they may not have sufficient access controls or security practices in place. Big data breaches can be large, making security critical. It then outlines some risks like insufficiently hardened systems, uncontrolled access, and unfulfilled regulatory requirements. The document introduces GOSEC as a centralized security component that manages access control across big data services like HDFS and applications. GOSEC allows setting access policies for users and groups for resources like files and topics. It covers authentication, authorization, and auditing. The document stresses the need to integrate GOSEC with the organization's identity provider and security strategies to prevent leakage of internal and external data. It