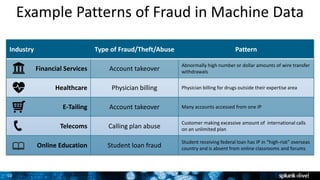
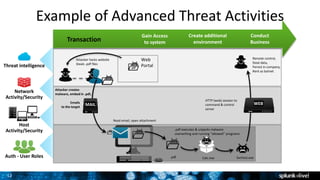
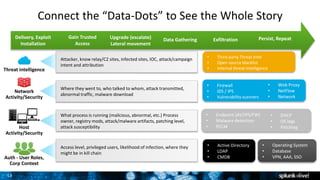
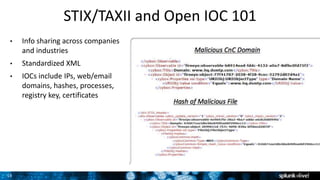
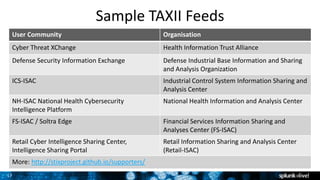
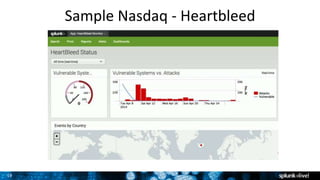
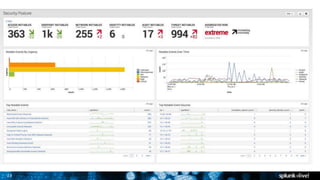
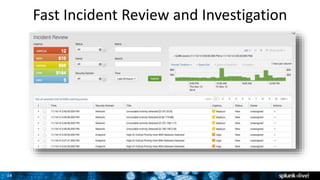
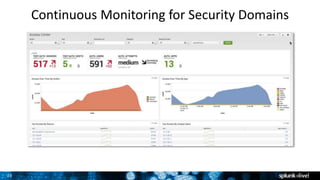
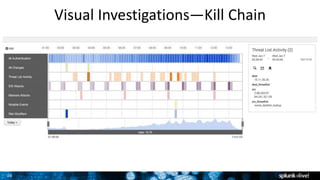
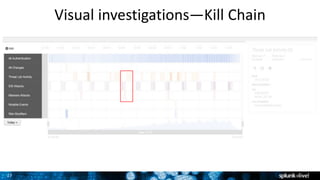
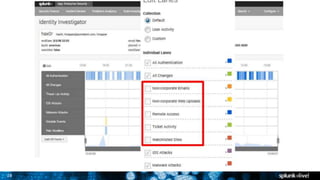
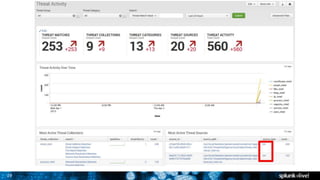
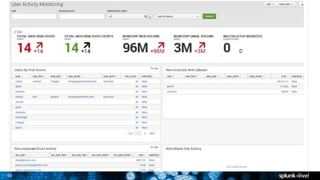
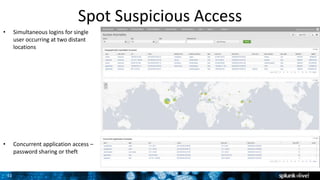
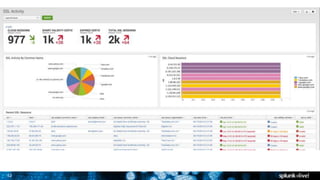
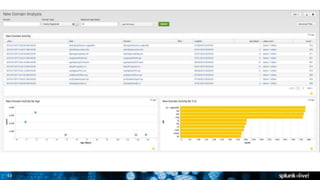
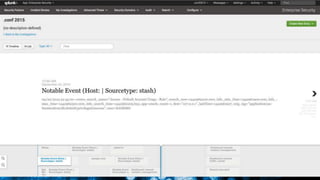
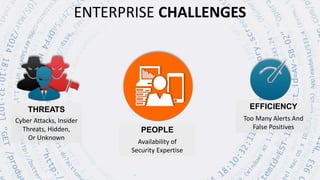
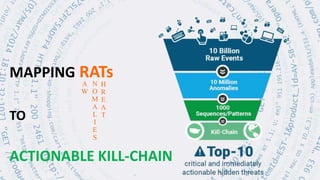
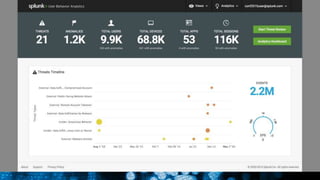
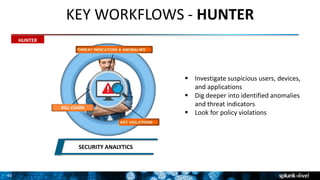
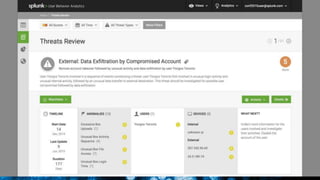
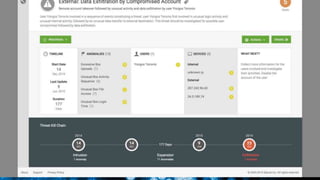
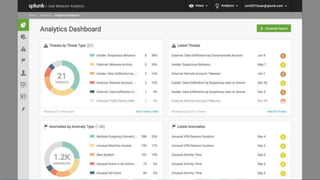
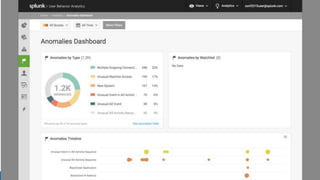
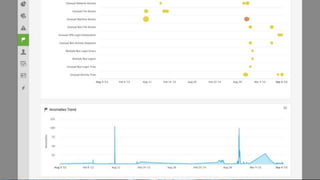
The document discusses security session presented by Philipp Drieger. It begins with a safe harbor statement noting any forward-looking statements are based on current expectations and could differ from actual results. The agenda includes discussing Splunk for security, enterprise security, and Splunk user behavior analytics. It provides examples of how Splunk can be used to detect threats like fraud and advanced persistent threats by analyzing machine data from various sources. It also discusses how threat intelligence can be incorporated using STIX/TAXII standards and open IOCs. Customer examples show how Nasdaq and Cisco have replaced their SIEMs with Splunk to gain better scalability and flexibility.