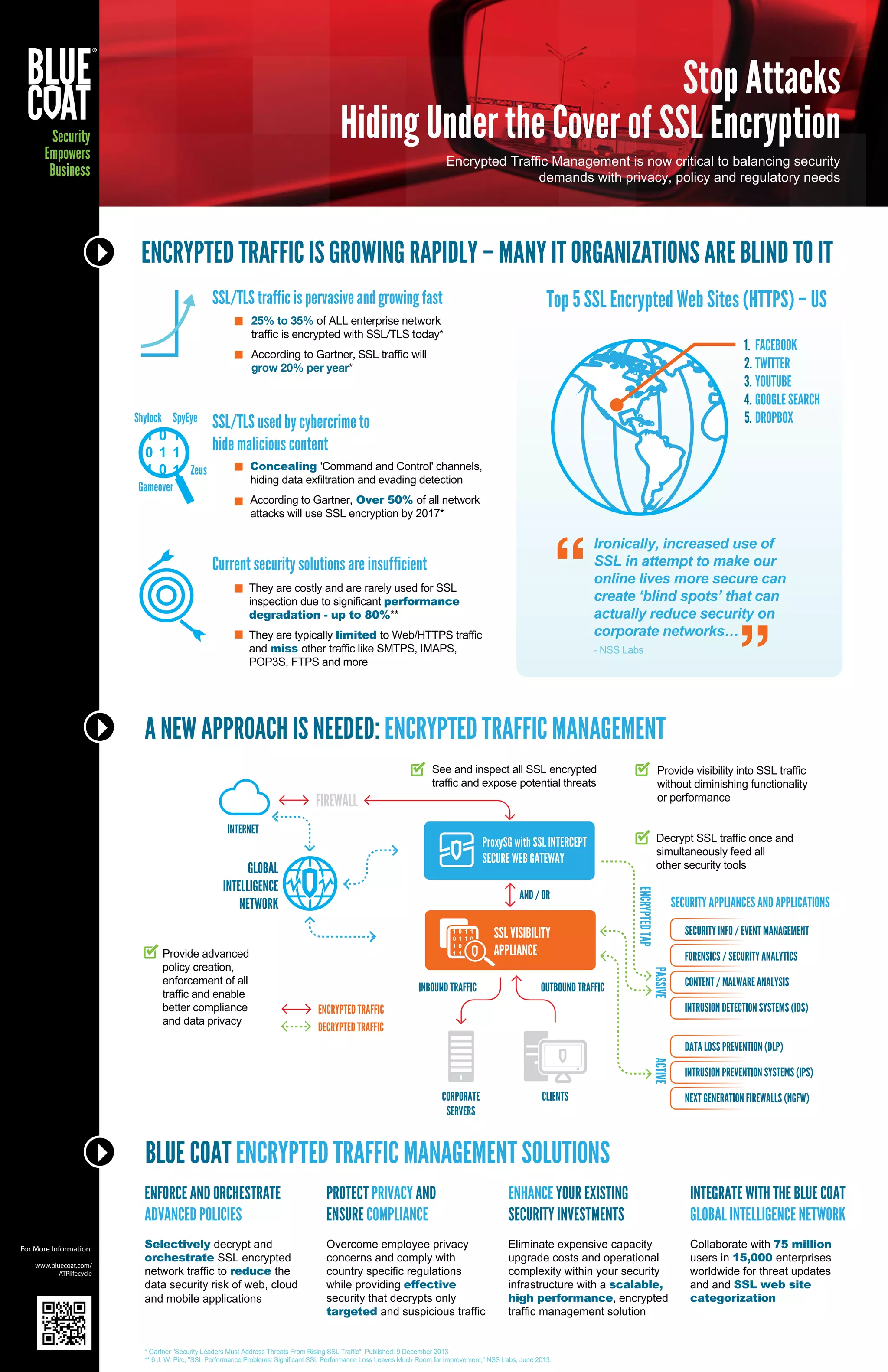
The document discusses the growing threat of encrypted network traffic and the need for encrypted traffic management solutions. It notes that over 50% of attacks will use encryption by 2017, and current security solutions are insufficient and costly. A new approach called encrypted traffic management is needed to provide visibility into encrypted traffic without impacting performance or functionality. This allows security tools to inspect encrypted traffic and identify potential threats.