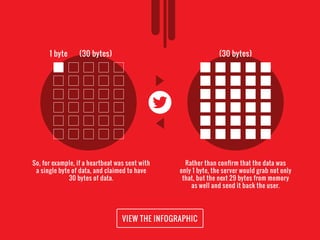
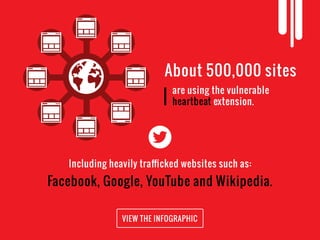
The document discusses the Heartbleed vulnerability (CVE-2014-0160) in OpenSSL software, which allowed attackers to access sensitive data from servers without detection. Discovered by Neel Mehta and his team in 2014, this bug was present for two years and exploited the heartbeat protocol error that caused servers to expose more data than intended. Major websites like Facebook and Google were affected, leading to significant security concerns.