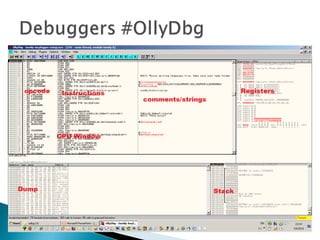
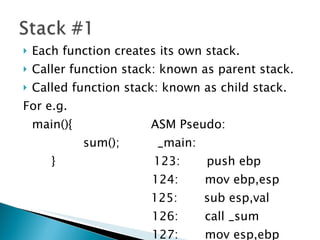
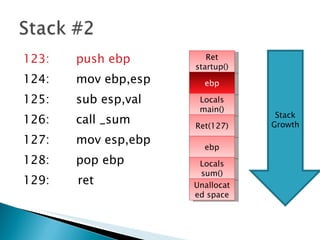
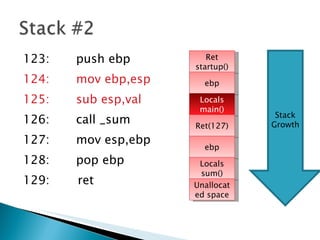
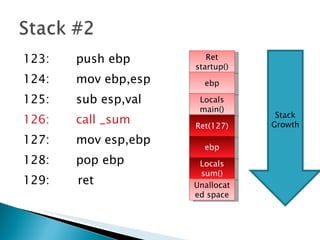
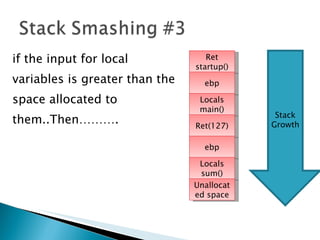
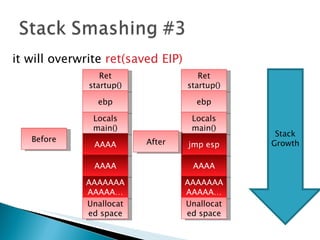
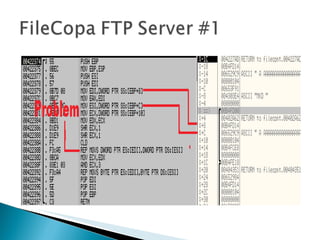
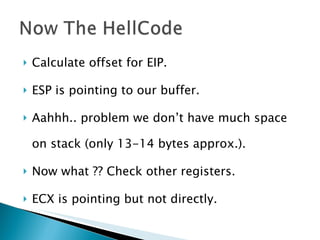
The document discusses stack-based buffer overflow vulnerabilities. It begins with an overview of buffer overflows and demonstrates one using the Filecopa FTP server. It explains the stack structure when functions call each other and how a buffer overflow can overwrite the return address on the stack. The document then discusses three methods for finding security bugs: fuzzing, reverse engineering, and source code auditing. It walks through fuzzing the FTP server, determining the vulnerable function through reverse engineering, calculating the offset needed for the instruction pointer, addressing issues of limited space on the stack, and constructing an exploit to gain remote code execution by manipulating the ECX register and jumping to it.
![Presented By: Amit Malik a.k.a DouBle_Zer0 [email_address]](https://image.slidesharecdn.com/softwareexploitationtechniques2-100719125618-phpapp02/75/Software-Exploitation-Techniques-by-Amit-Malik-1-2048.jpg)