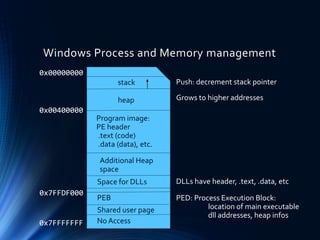
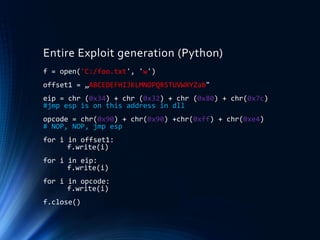
This document discusses software vulnerabilities and exploits. It begins with an introduction to remote code execution and provides legal aspects of data interception for Germany and Switzerland. It then discusses the goals of preventing teaching how to write malware or hack systems illegally. The document covers basics of function calls, stack smashing vulnerabilities, and how to redirect program flow to injected shellcode through buffer overflows. It provides examples of finding vulnerabilities using debuggers and generating exploits in Python to execute shellcode by overwriting return addresses. Methods discussed include placing shellcode in registers or on the stack and dealing with gaps between the stack pointer and shellcode.








![Basic: Function Calls
Main
stackframe
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
1. after program initialization
Stack
ESP
EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-10-320.jpg)
![Basic: Function Calls
Main
stackframe
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
2. push function parameter
Stack
ptr to argv[1]
ESP
EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-11-320.jpg)
![Basic: Function Calls
Main
stackframe
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
3. Push instruction pointer
Stack
ptr to argv[1]
EIP
ESP
EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-12-320.jpg)
![Basic: Function Calls
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
4. push base pointer
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
ESP
EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-13-320.jpg)
![Basic: Function Calls
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
5. new stack frame:
MOV EBP, ESP
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
ESPEBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-14-320.jpg)
![Basic: Stack space allocation
• Local variables of a function are stored on the current stack frame
• decrement stack pointer to store a new variable on top of the stack
• How to allocate arrays?
• SUB ESP, <arraysize>
• decrement stack pointer with array size
• How to store data in a array?
• Array begin + position
• Find “array begin” with fixed offset or LEA (load effective address) instruction
• Remember: a[4] == *(a+4)](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-15-320.jpg)
![Basic: Allocate Stack Array
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
6. Allocate array:
SUB ESP, 0x80
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-16-320.jpg)
![Basic: Write to Stack Array
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
7. Allocate array:
MOV ESP, ECX
INC ECX
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-17-320.jpg)
![Basic: Return from a function: LEAVE
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
8. Return: LEAVE
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP ESP
Array
Leave Step 1: MOV ESP, EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-18-320.jpg)
![Basic: Return from a function: LEAVE
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
9. Return: LEAVE
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
Array
Leave Step 2: POP EBP
ESP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-19-320.jpg)
![Basic: Return from a function: RET
void do_sth(char *buf){
char var[128];
…
}
int main(int argc, char** argv){
do_sth(argv[1])
}
10. Return: RETN
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
Array
Restore the instruction pointer
ESP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-20-320.jpg)
![Stack smashing
• What can possibly go wrong?
void do_sth(char *buf){
char var[128];
strcpy(var, buffer);
}
int main(int argc, char** argv){
do_sth(argv[1])
}](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-21-320.jpg)
![Stack smashing
• What can possible go wrong?
• strcpy terminates when
a ‘0’ character is reached
• What happens if argv[1]
is larger than 128 characters?
void do_sth(char *buf){
char var[128];
strcpy(var, buffer);
}
int main(int argc, char** argv){
do_sth(argv[1])
}](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-22-320.jpg)
![Stack smashing
• What can possible go wrong?
• strcpy terminates when
a ‘0’ character is reached!
• What happens if argv[1]
is larger than 128 characters?
• EBP and EIP are overwritten,
and possible other stack frames
program will crash
void do_sth(char *buf){
char var[128];
strcpy(var, buffer);
}
int main(int argc, char** argv){
do_sth(argv[1])
}
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-23-320.jpg)

![Shell code
• How to inject shell code in the
programs memory?
• Use program IO similar as for
overwriting EIP
• write OP_CODES into
input array behind EIP
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array
Shellcode](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-25-320.jpg)
![Shell code
• How to start the shell code?
• Jump to address where shell code is stored
• BUT:
when executing on different machines the
address may be different!
• Additional:
0x00 in the address breaks the exploit
• you cannot overwrite EIP with hardcoded
address
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array
Shellcode](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-26-320.jpg)
![Shell code
• How to start the shell code?
• Idea:
After executing “ret” ESP points below
the stored EIP
• search an address which contains jmp esp
• In a application dll (address is constant there)
• In a system dll (may differ in differentOS versions)
• Overwrite EIP with this address
• When ret is executed the program will jmp to
address
jmp esp is executed
shellcode is executed
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array
Shellcode](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-27-320.jpg)



![Example
void readfile(char *filename){
char file[10]; memset(file, 0, sizeof(file));
FILE *f = fopen(filename,"r");
if (!f) {
printf("FILE NOT FOUNDn");
return;
}
fseek(f, 0L, SEEK_END);
int size = ftell(f);
rewind(f);
printf("Size: %dn", size);
fread(file, size, 1, f);
printf("%s", file);
}](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-31-320.jpg)

![Example
• Start application with large file will crash it!
(char file[10]) overflow)
• e.g. use a file with many ‘A‘
• Debugger shows an Access violation](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-33-320.jpg)


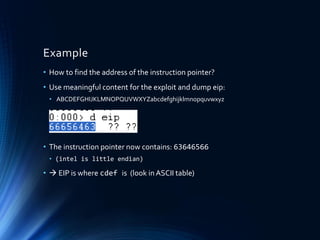
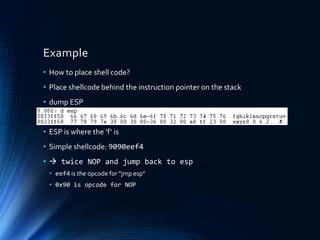


![Gap between ESP and shellcode
• Sometimes it is not possible to write
the shellcode directly to ESP
• May overwritten by other data or
• OS counter mechanism.
• Assume you have 8 byte gap
overwrite EIP with an address that
contains “pop pop ret”
first bytes of the shellcode are address
of “jmp esp”
• Pop takes 4 byte from stack (32bit)
• ret loads the first stack value in EIP
• goto “jmp esp” address and execute
shellcode
• popad removes 32bytes from stack if pop
is not enough
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array
Shellcode
gap](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-41-320.jpg)
![Search the address of the shellcode on the
stack
• Sometimes the shellcode address is not in
any register
• but it can be found on the stack
• POP until you reached shellcode address
• execute ret to load the address to EIP
• if the gap is 8 bytes again overwrite EIP
with an address that points on a
“pop pop ret”
Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array
Shellcode
address
gap
Shellcode](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-42-320.jpg)
![What if only a few bytes are usable for the
shellcode
• Sometimes only a few bytes are usable
for shellcode behind EIP
• but you can place more shellcode above
• use the few bytes to jmp the the shellcode
above:
• Small shellcode can be:
sub esp, 80
jmp esp
• Start shellcode with NOPs
• no exact jmp required Main
stackframe
Stack
ptr to argv[1]
EIP
EBP
EBP
ESP
Array Shellcode
Shellcode](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-43-320.jpg)

![SEH (Structured Exception Handler) exploits
• a try-catch block runs in its own stack frame
• Information about the EH are pushed on the stack
• 8bytes:
• pointer to the next exception handler
(for the case the current exception handler
cannot handle the exception)
• pointer to the actual exception handler
• Chain of exception handlers
• FFFFFFFF marks the end of the chain
OS exception handler kicks in
Main
stackframe
Stack
EH
ptr to argv[1]
EIP
Array
EBP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-45-320.jpg)

![Stack Cookies
• Compiler flag (only for string buffer)
• Random value is computed when application
starts (stack cookie)
• Stored in .data section on the program
• After saving EBP and EIP push stack cookie
on the stack
• To overwrite EIP you have to overwrite the
Stack Cookie
• Before ret the stack cookie will be checked.
• So do not return, overwrite SEH to exploit
• Sometimes you can compute the value or
it is constant
• Overwrite stack cookie in .data
Main
stackframe
Stack
EH
EIP
Stack Cookie
Array
ptr to argv[1]
ESP](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-47-320.jpg)

![Preventing Buffer Overflows
• ALWAY check array boundaries
• Do NOT forget to check for index overflows:
0 1 2 3 4 5 6 7 8 9 10 11 12
base bound
int array[4]:
ptr: array
• Iterate through the array:
++array;
• Boundary check:
array > base && array+elementsize < bound](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-49-320.jpg)
![Preventing Buffer Overflows
• ALWAY check array boundaries
• Do NOT forget to check for index overflows:
0 1 2 3 4 5 6 7 8 9 10 11 12
boundbase
int array[4]:
ptr: array
• Boundary check:
array > base && array+elementsize < bound
• Point with long long *ptr2 on element 12:
• ptr2 > base: 12 > 9
• ptr2 + 1 < bound: 1 < 12
Access to element 0!
ptr2](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-50-320.jpg)
![Preventing Buffer Overflows
• ALWAY check array boundaries
• Do NOT forget to check for index overflows:
0 1 2 3 4 5 6 7 8 9 10 11 12
boundbase
int array[4]:
ptr: array ptr2
• Boundary check correct:
array > base && array+elementsize < bound
&& base < array+elementsize
• ptr2 > base: 12 > 9
• ptr2 + 1 < bound: 0 < 12
• ptr2 + 1 > base: 0 > 9 X](https://image.slidesharecdn.com/softwarevulnerabilityworkshop-140529151634-phpapp01/85/fg-workshop-Software-vulnerability-51-320.jpg)
