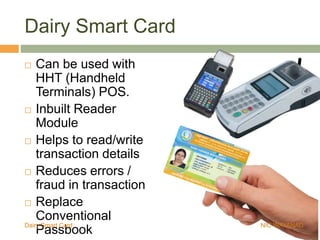
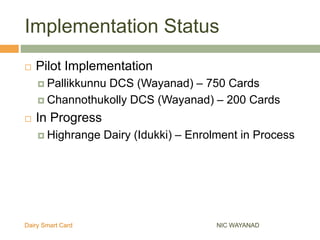
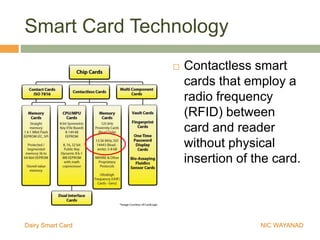
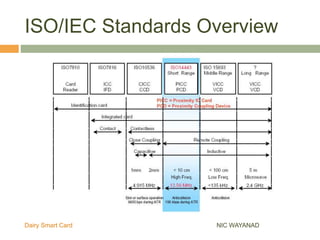
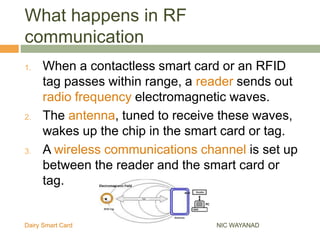
The Wayanad Dairy Smart Card is an RFID-enabled identity card for dairy farmers that securely stores personal information, milk procurement details, and transaction records. It facilitates transactions at the doorstep and reduces errors and fraud by replacing conventional passbooks with digital records. The implementation of the card is underway, with pilot programs and ongoing enrollments in progress in various districts.