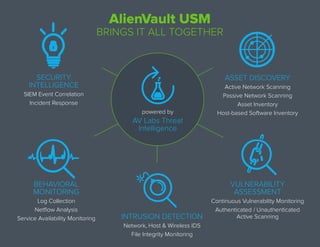
The document outlines five essential security controls for an effective Security Operations Center (SOC) to enhance breach detection and response capabilities. These controls emphasize understanding assets, assessing vulnerabilities, detecting threats, monitoring behavior for breaches, and prioritizing responses based on the impact on security posture. By establishing these controls, organizations can reduce response times and effectively manage their security operations.