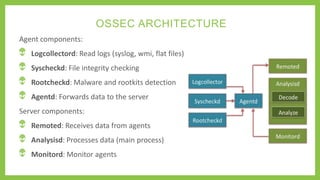
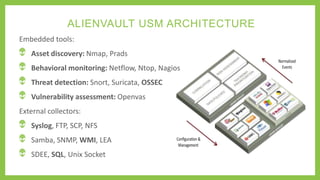
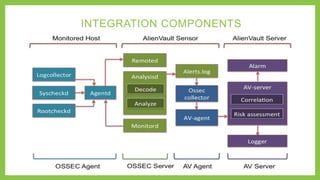
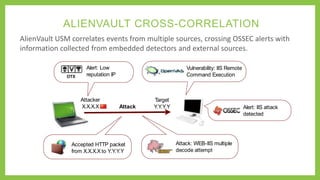
This document summarizes an advanced training on integrating OSSEC and AlienVault for open source security. The presentation covers the capabilities and architecture of OSSEC and AlienVault, how they integrate, and a demo of deploying OSSEC agents, managing alerts, and correlating events across sources. OSSEC provides log analysis, file integrity checking, and signature-based malware detection while AlienVault adds threat detection capabilities, centralized management, risk assessment, and cross-source event correlation to strengthen security monitoring.