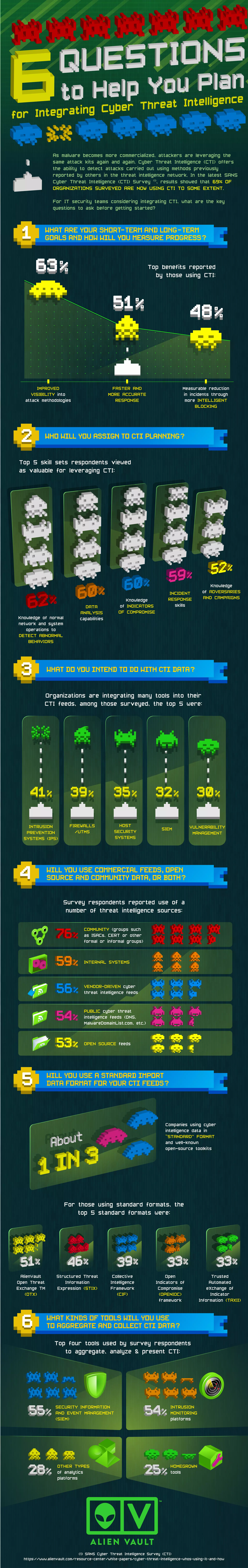
The document discusses the commercialization of malware and the increasing use of cyber threat intelligence (CTI) among organizations, with 69% of those surveyed integrating it into their security practices. It highlights the key questions organizations should consider before adopting CTI, such as goals, tools for data aggregation, and data formats. Additionally, it lists the top benefits and skills needed for effective CTI usage, along with popular sources and tools for threat intelligence.