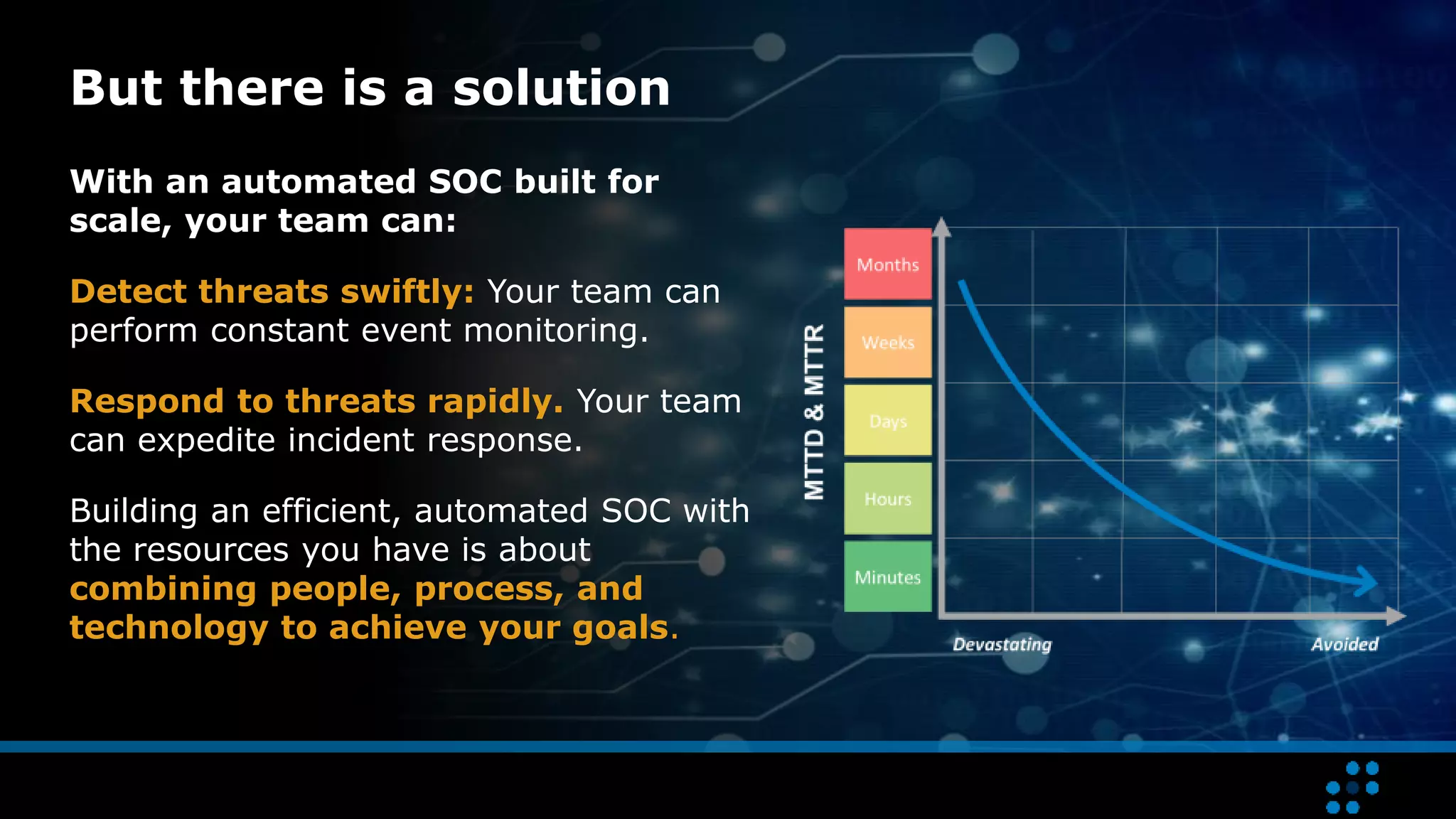
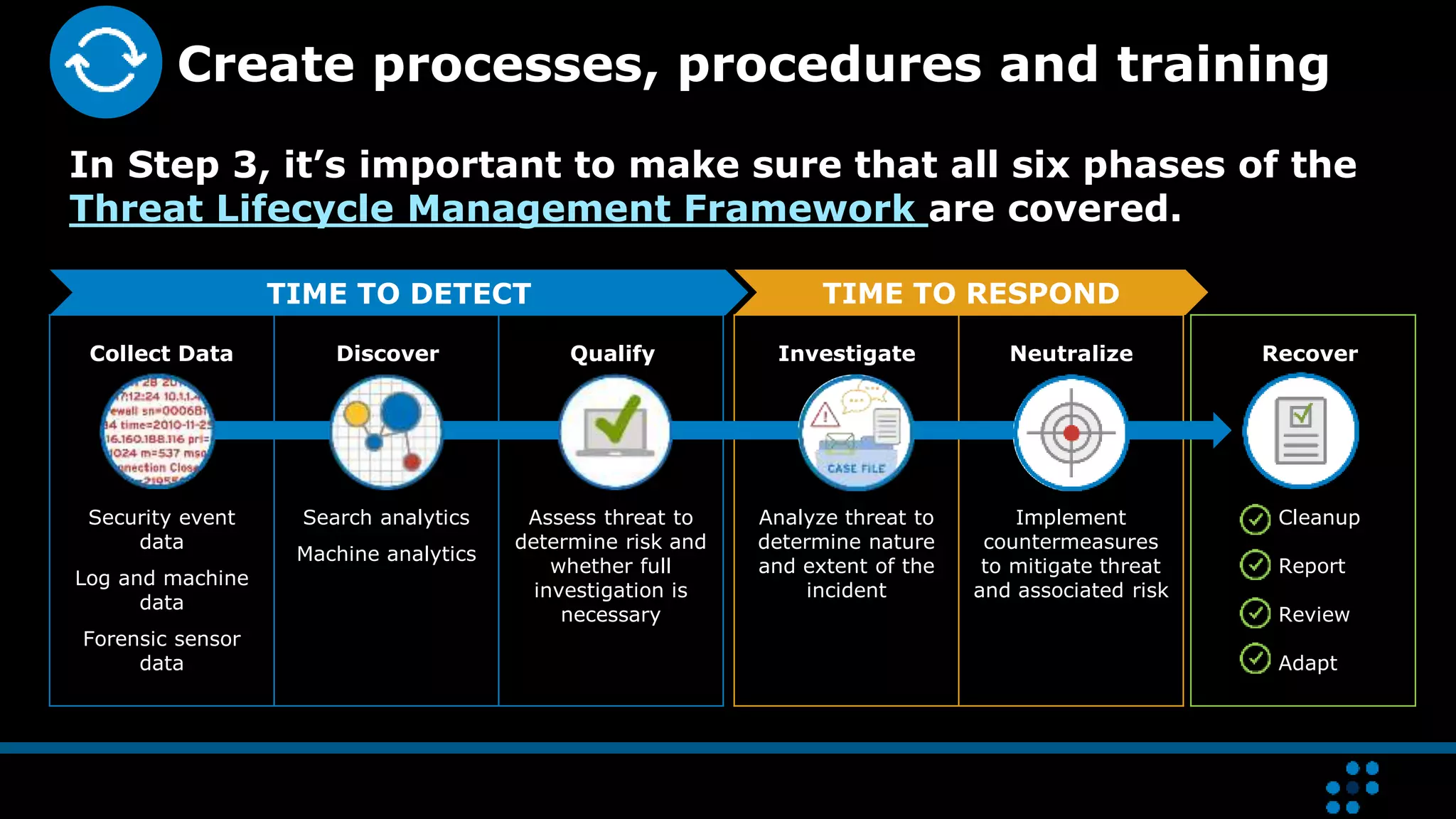
Building a Security Operations Center (SOC) with limited resources requires a structured 7-step approach focused on strategy development, solution design, preparation, implementation, and maintenance. Organizations can enhance threat detection and response by integrating technology effectively while starting with core functions, defining use cases, and ensuring system interoperability. Continuous evolution of the SOC is necessary to improve performance and adapt to changing needs.