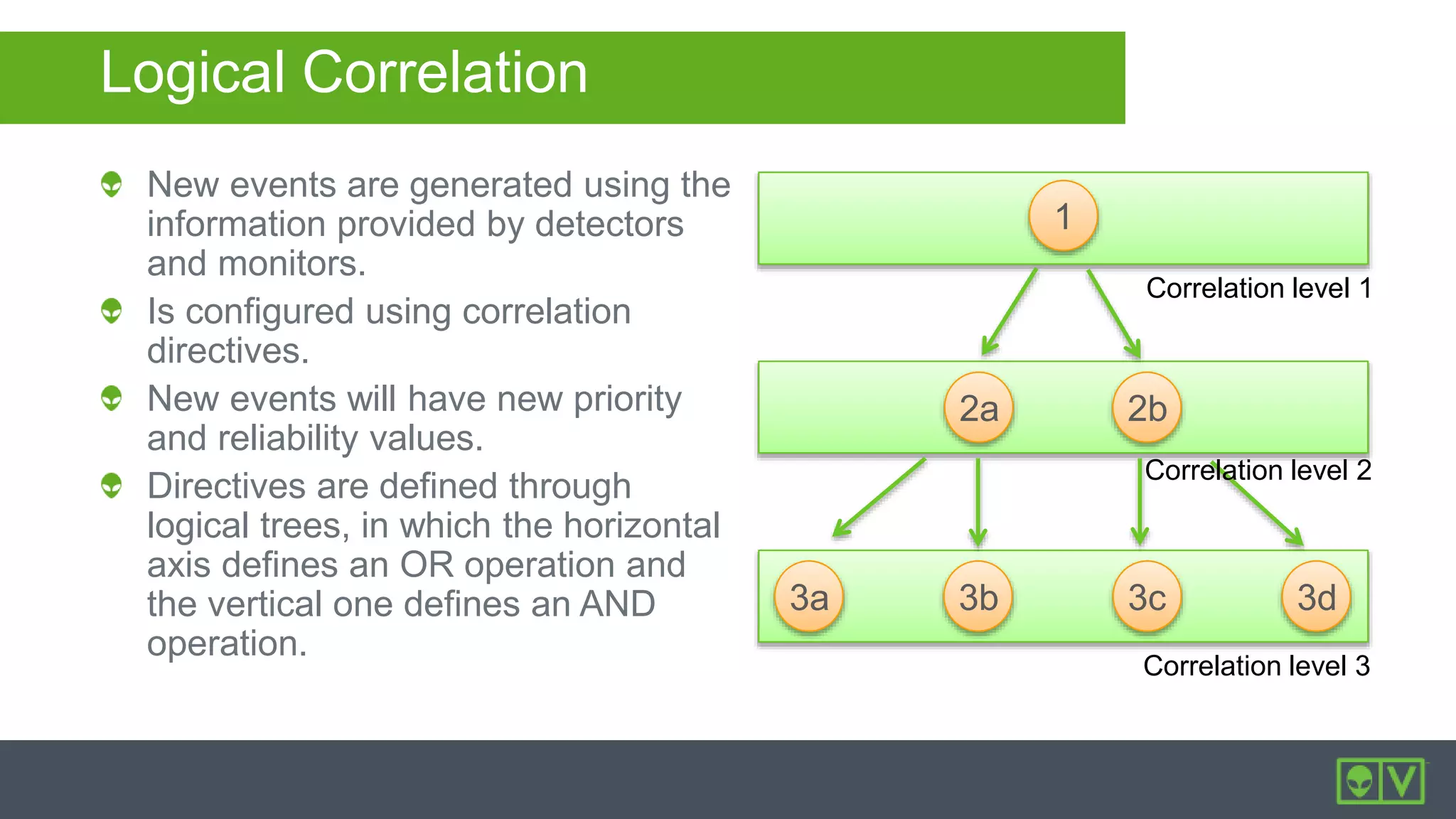
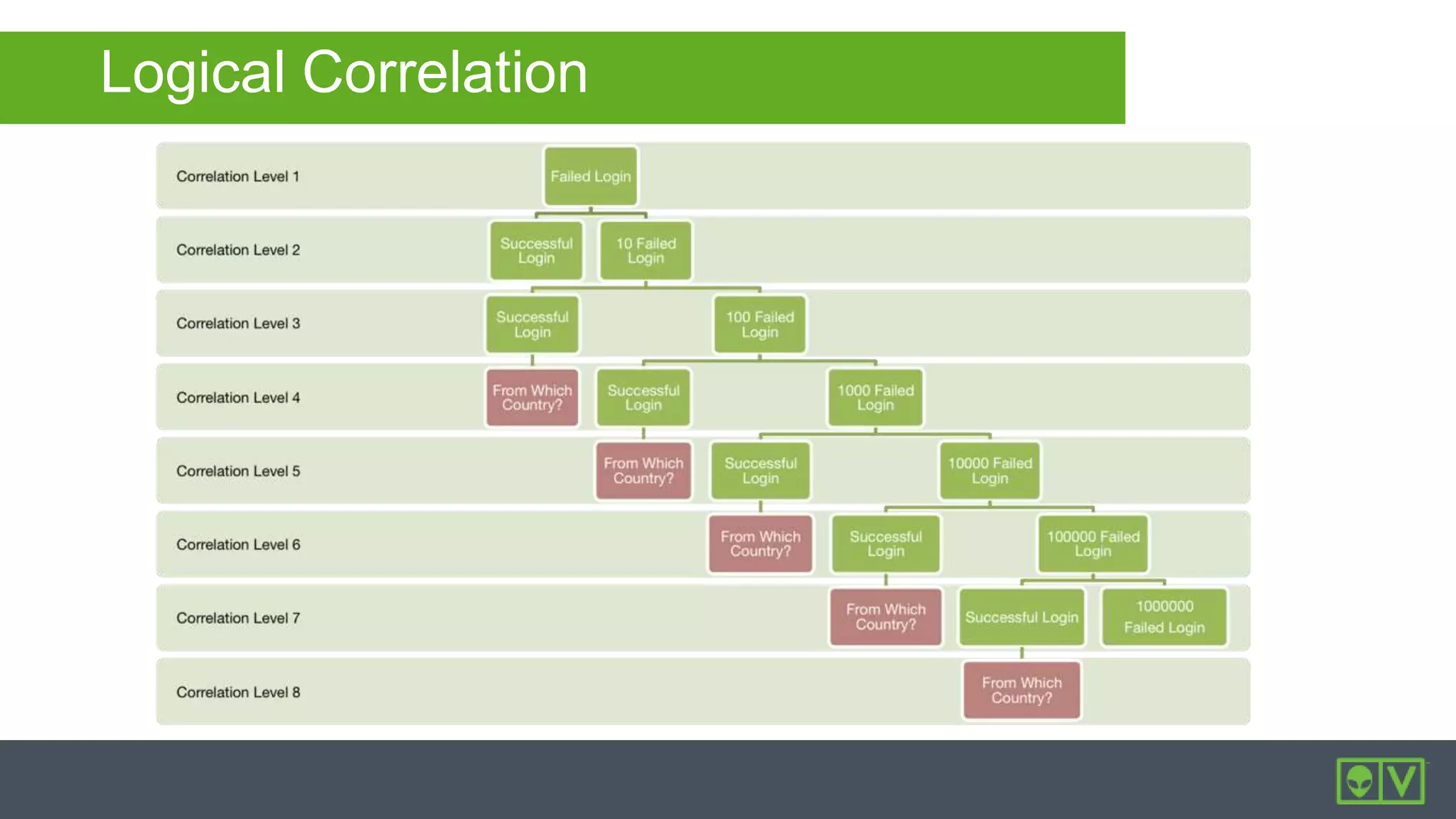
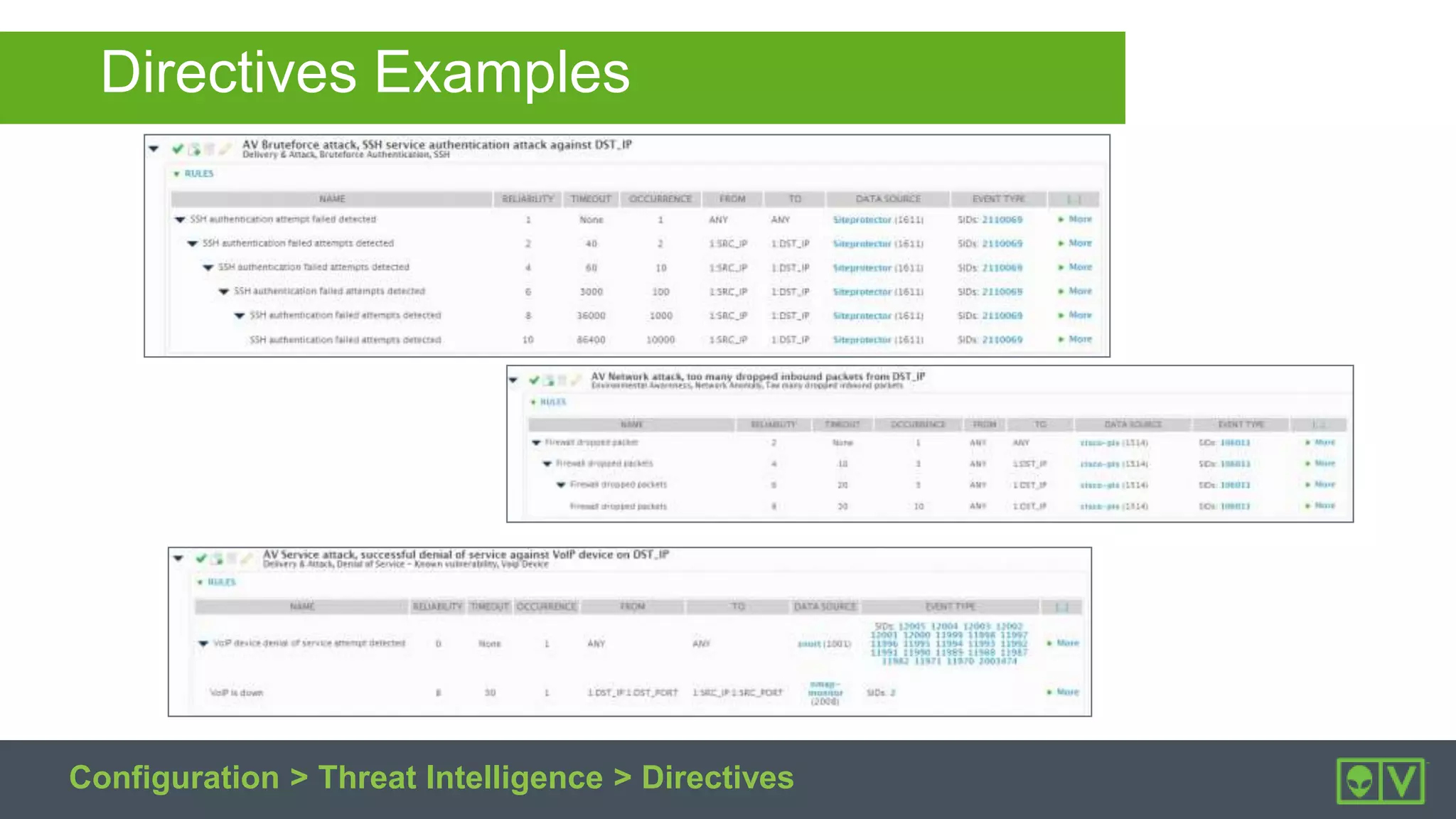
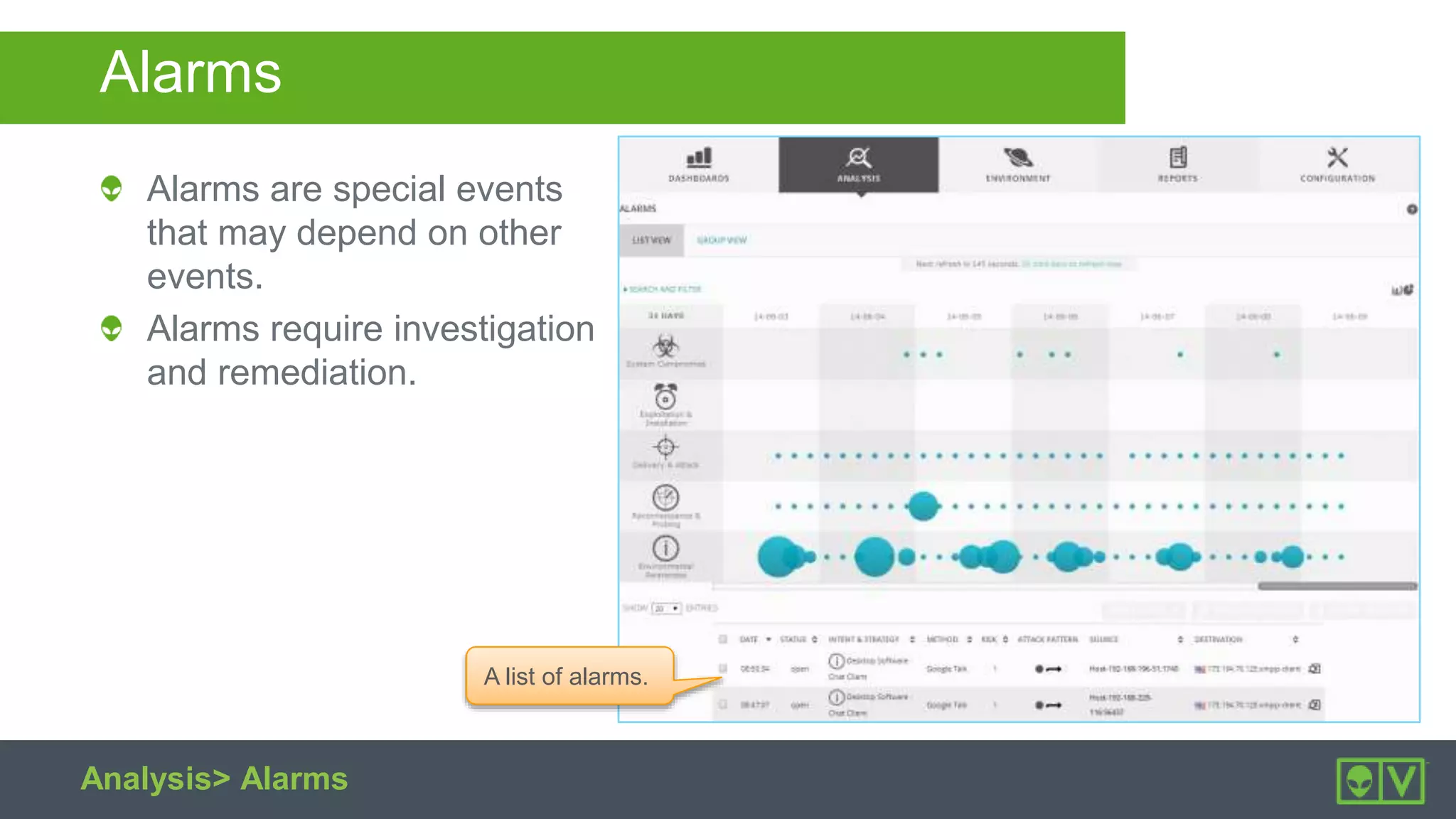
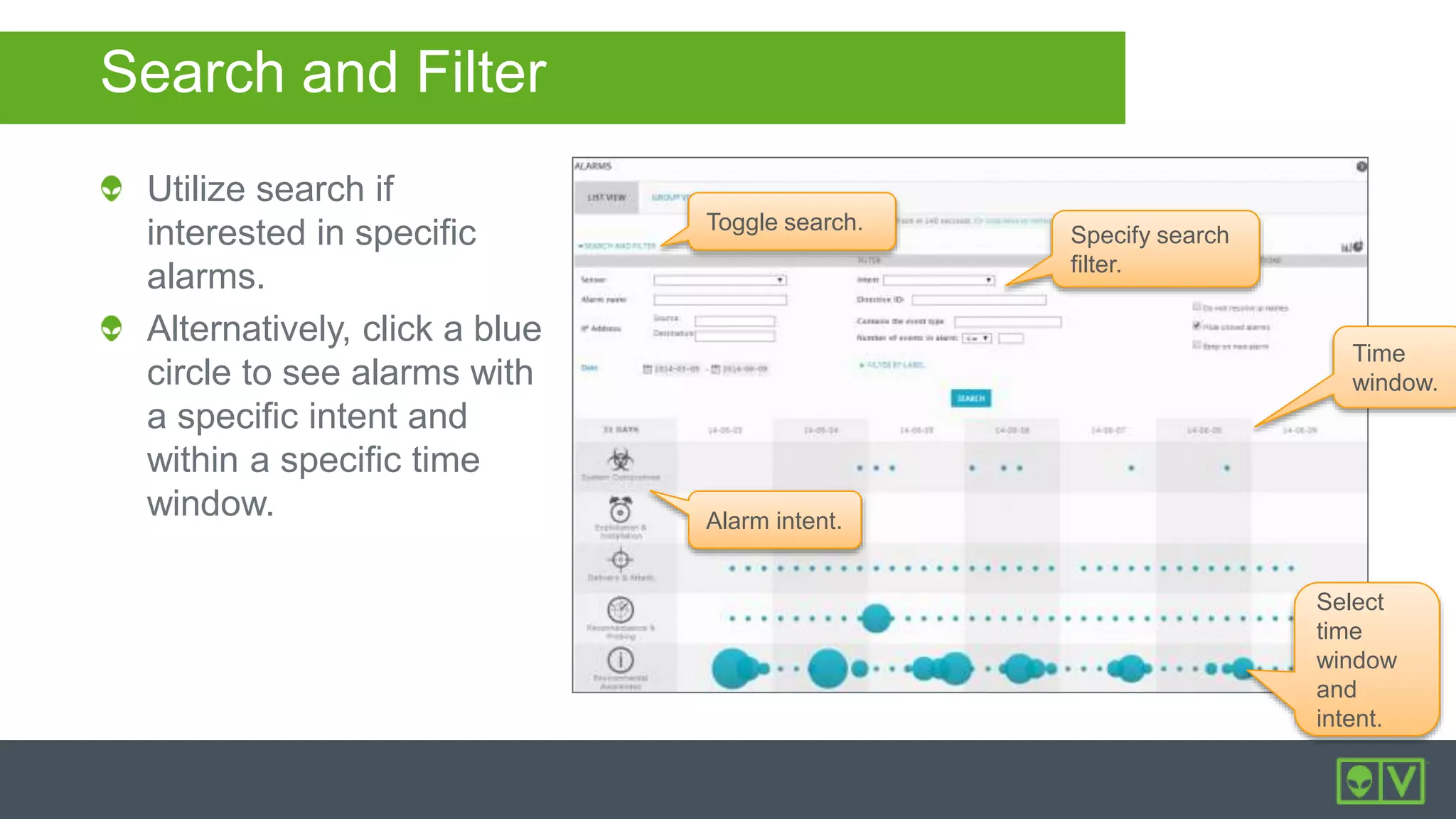
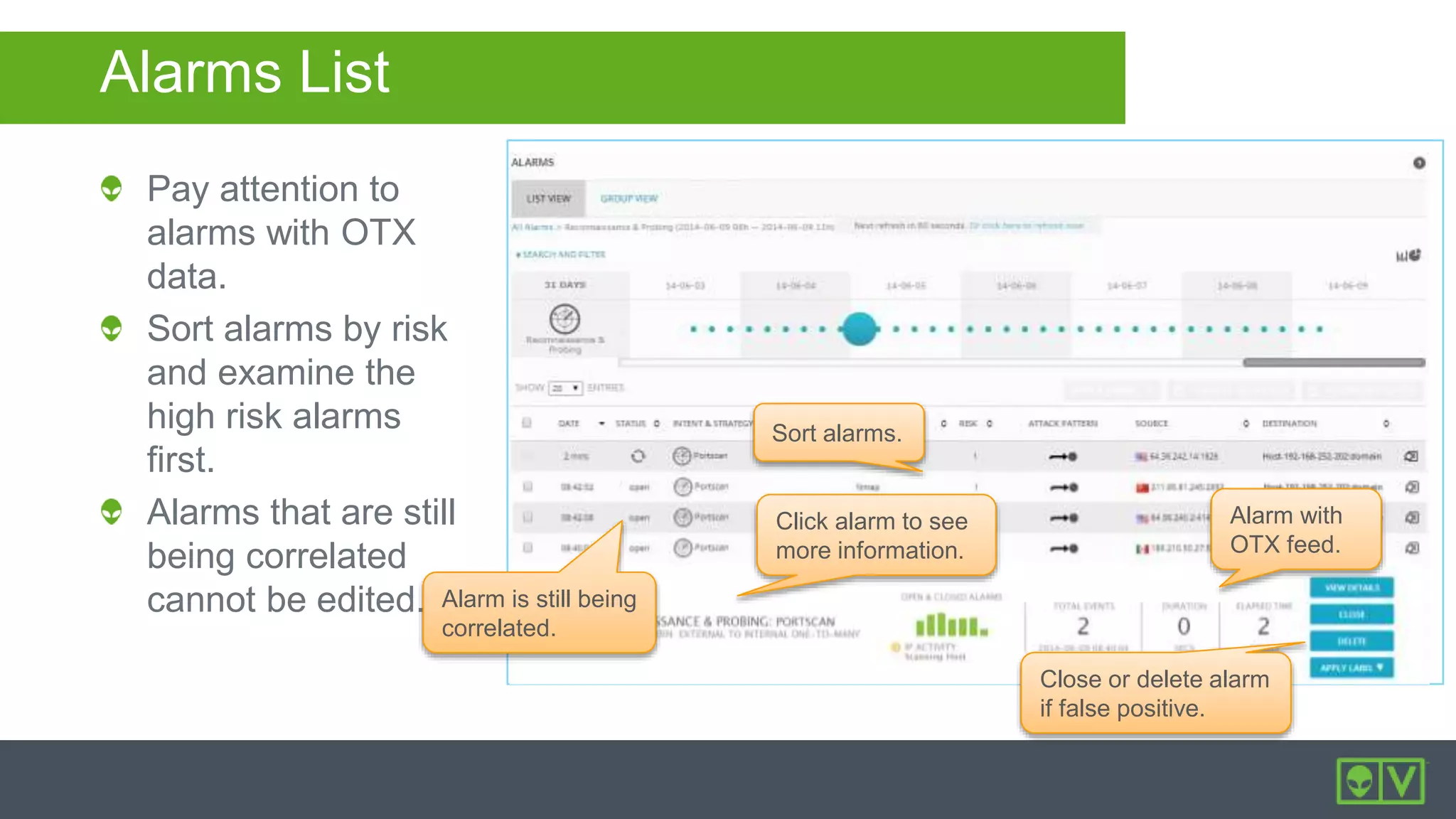
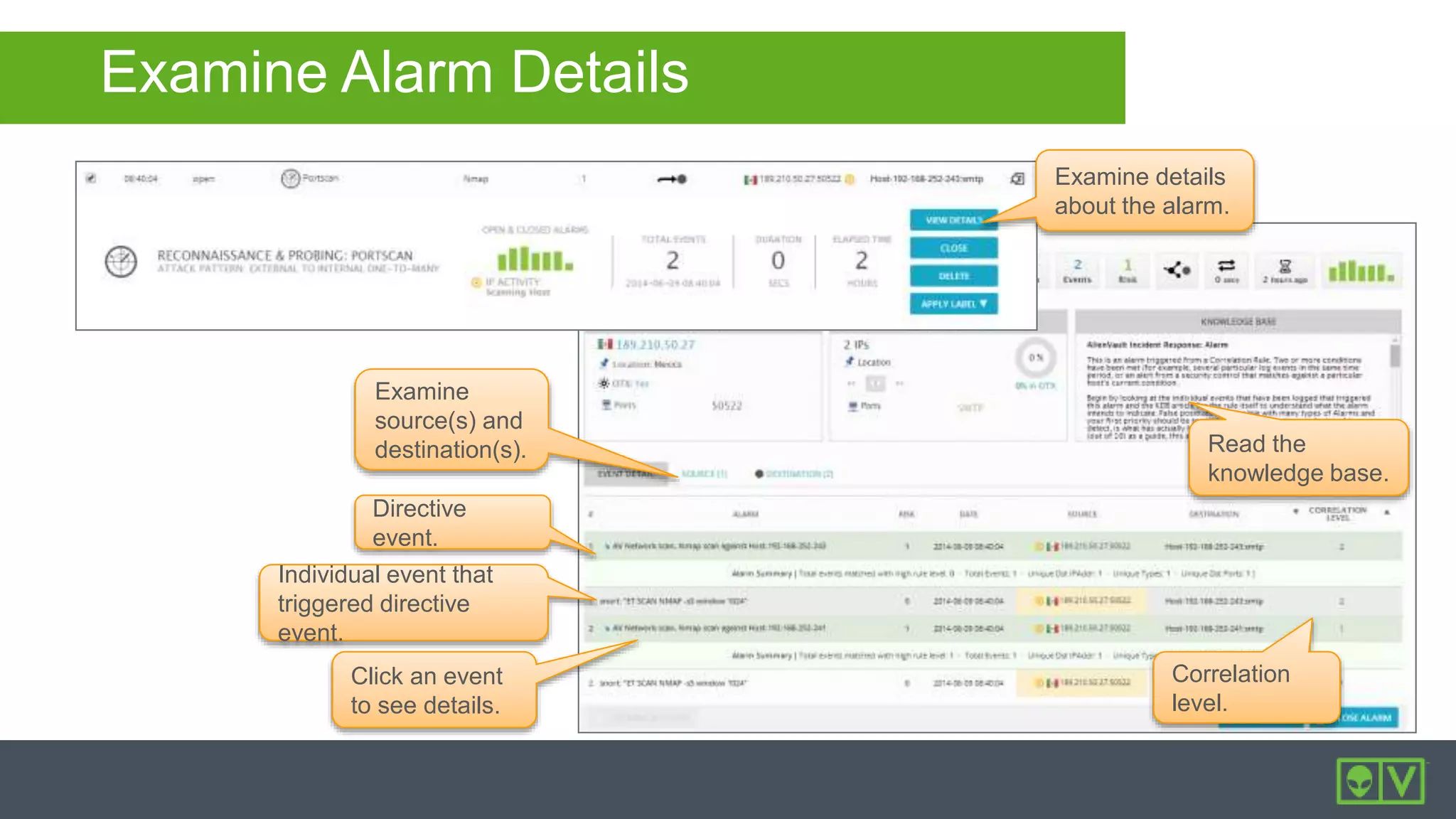
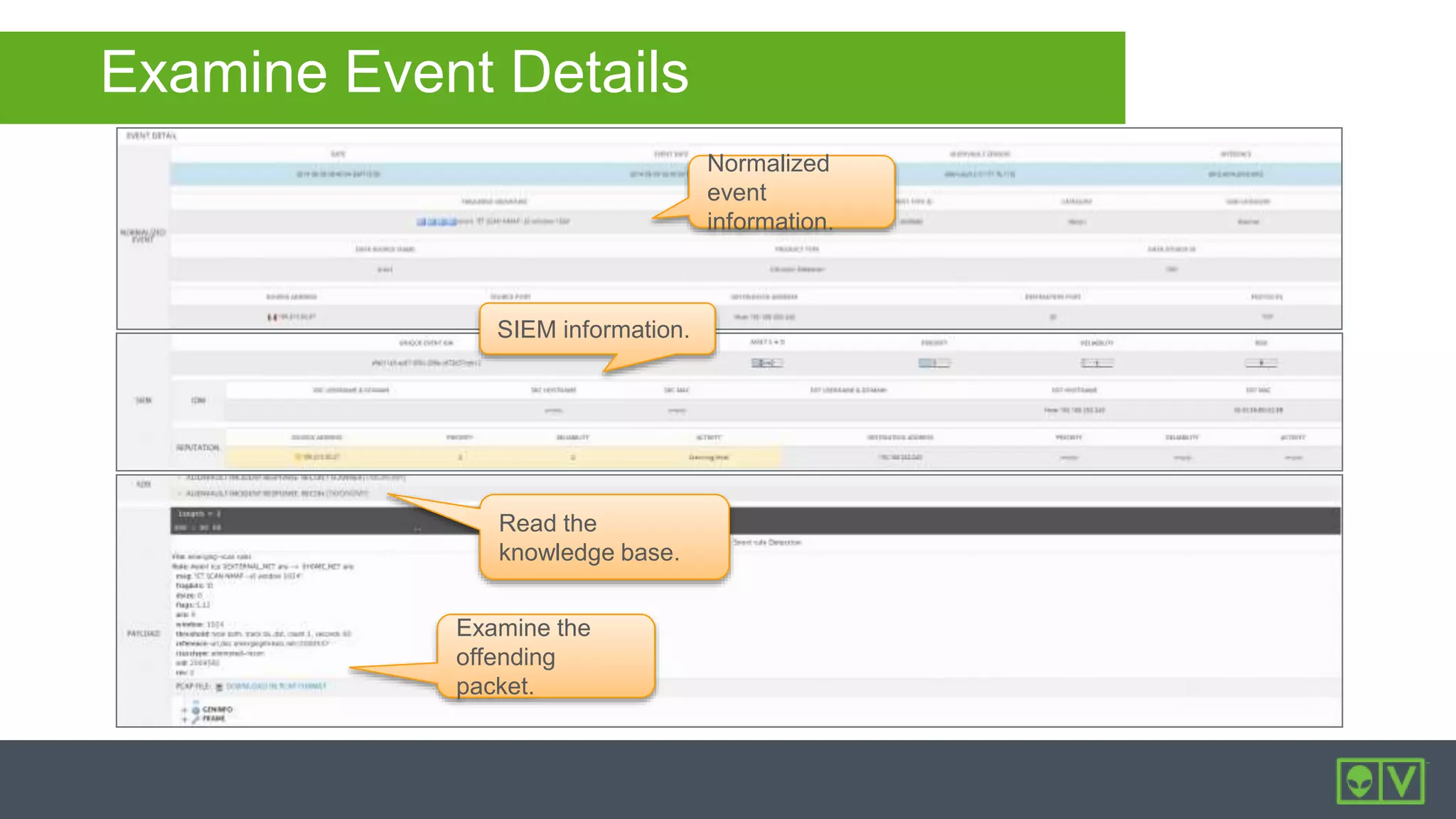
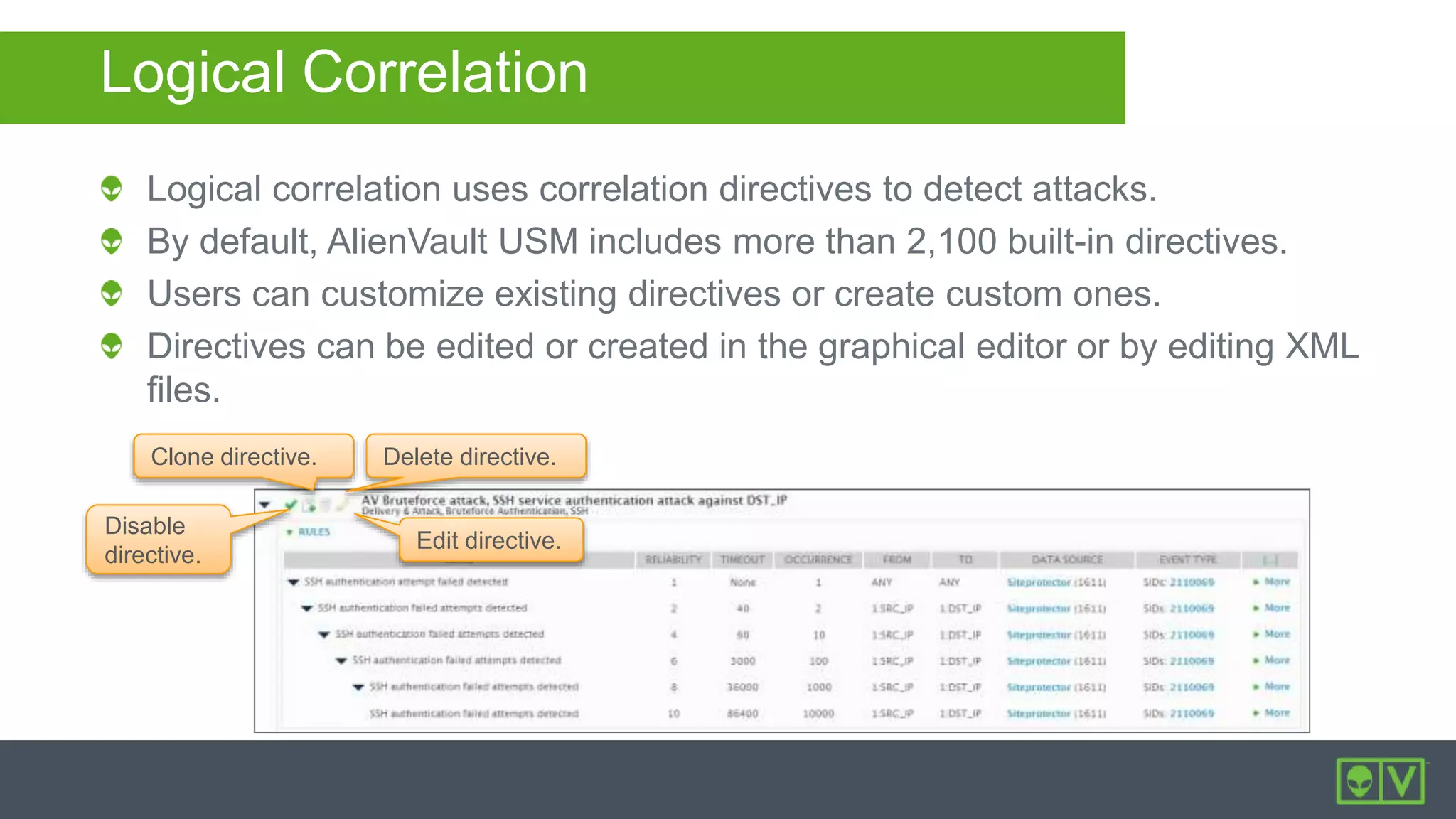
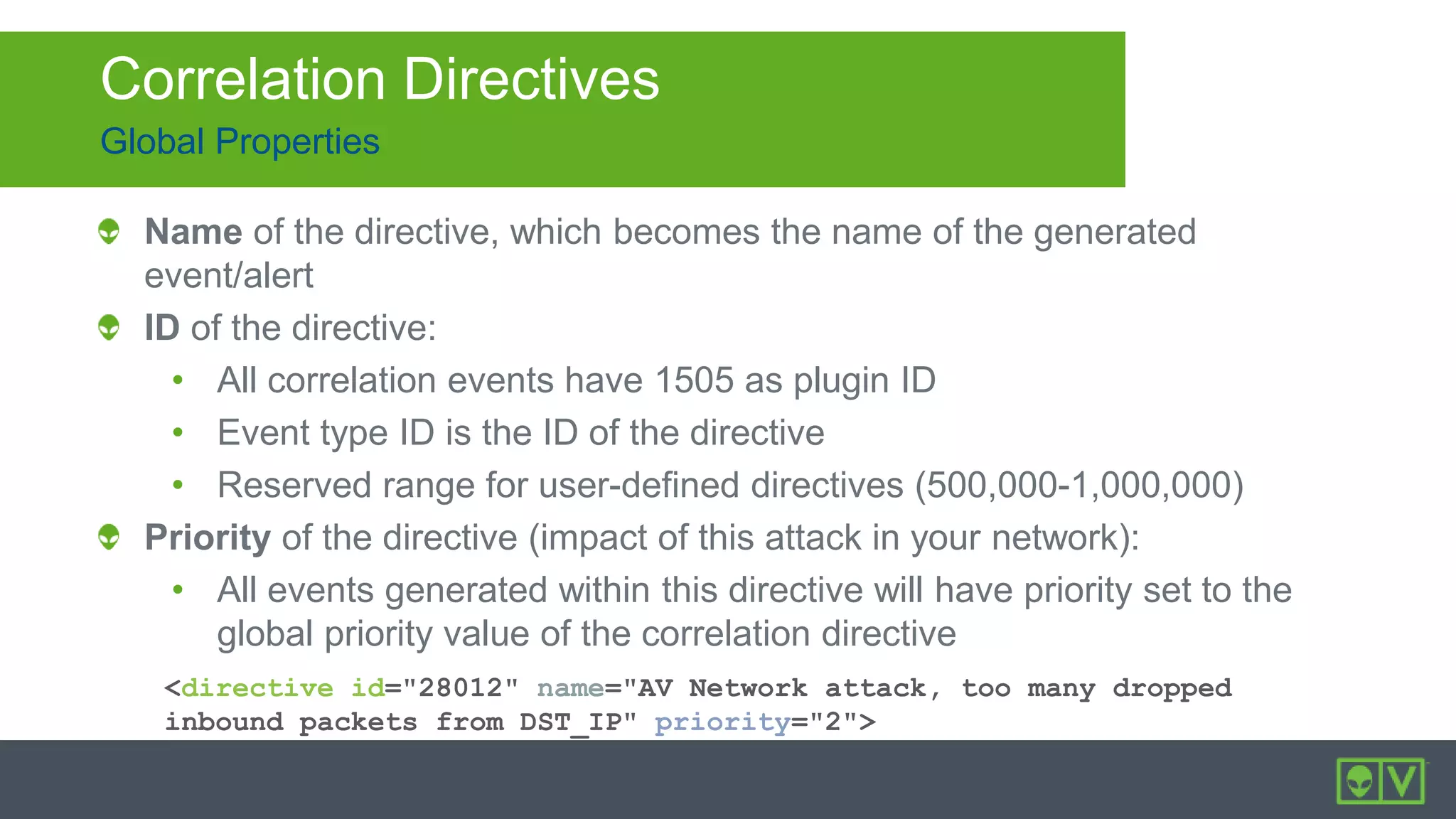
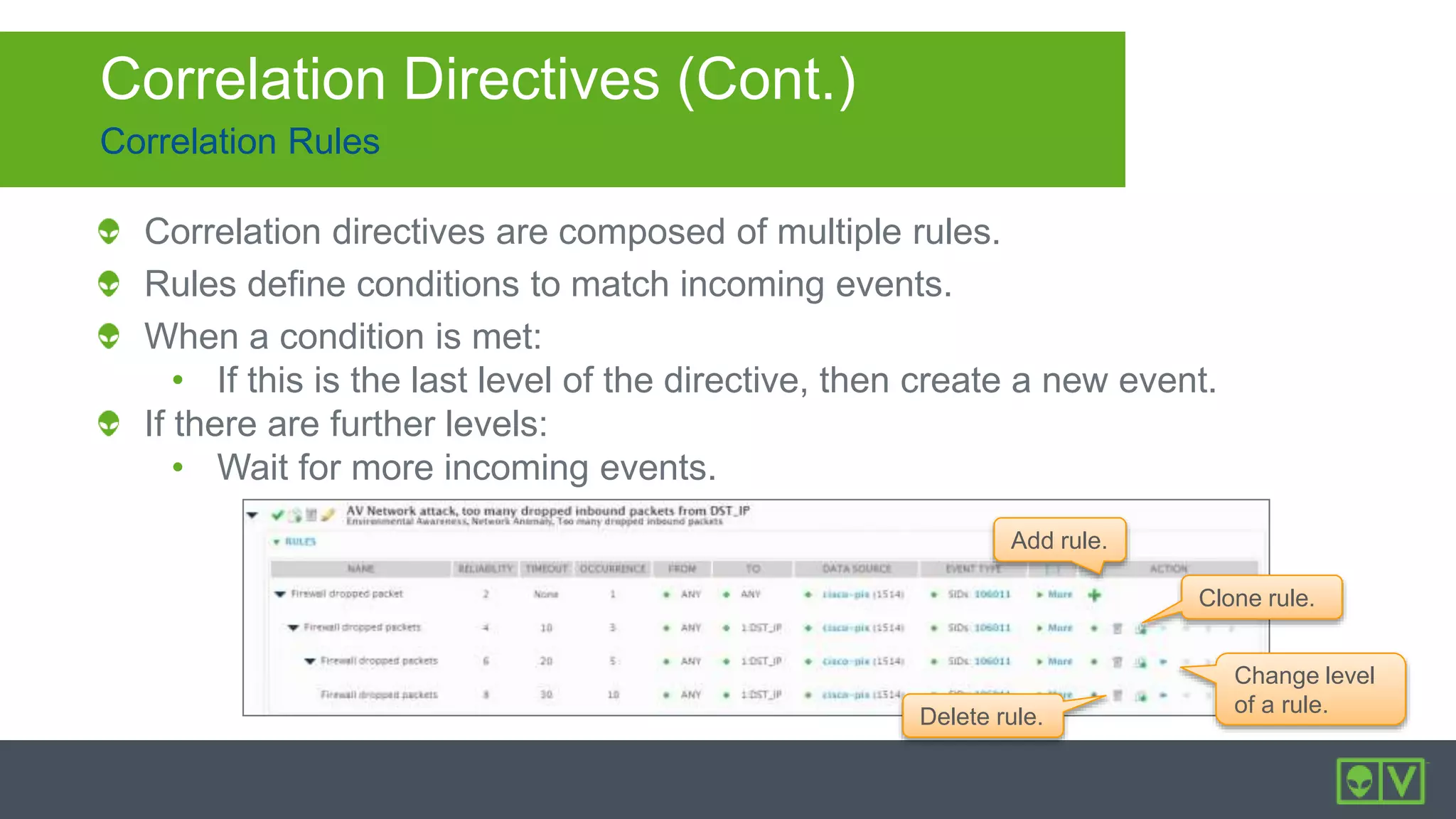
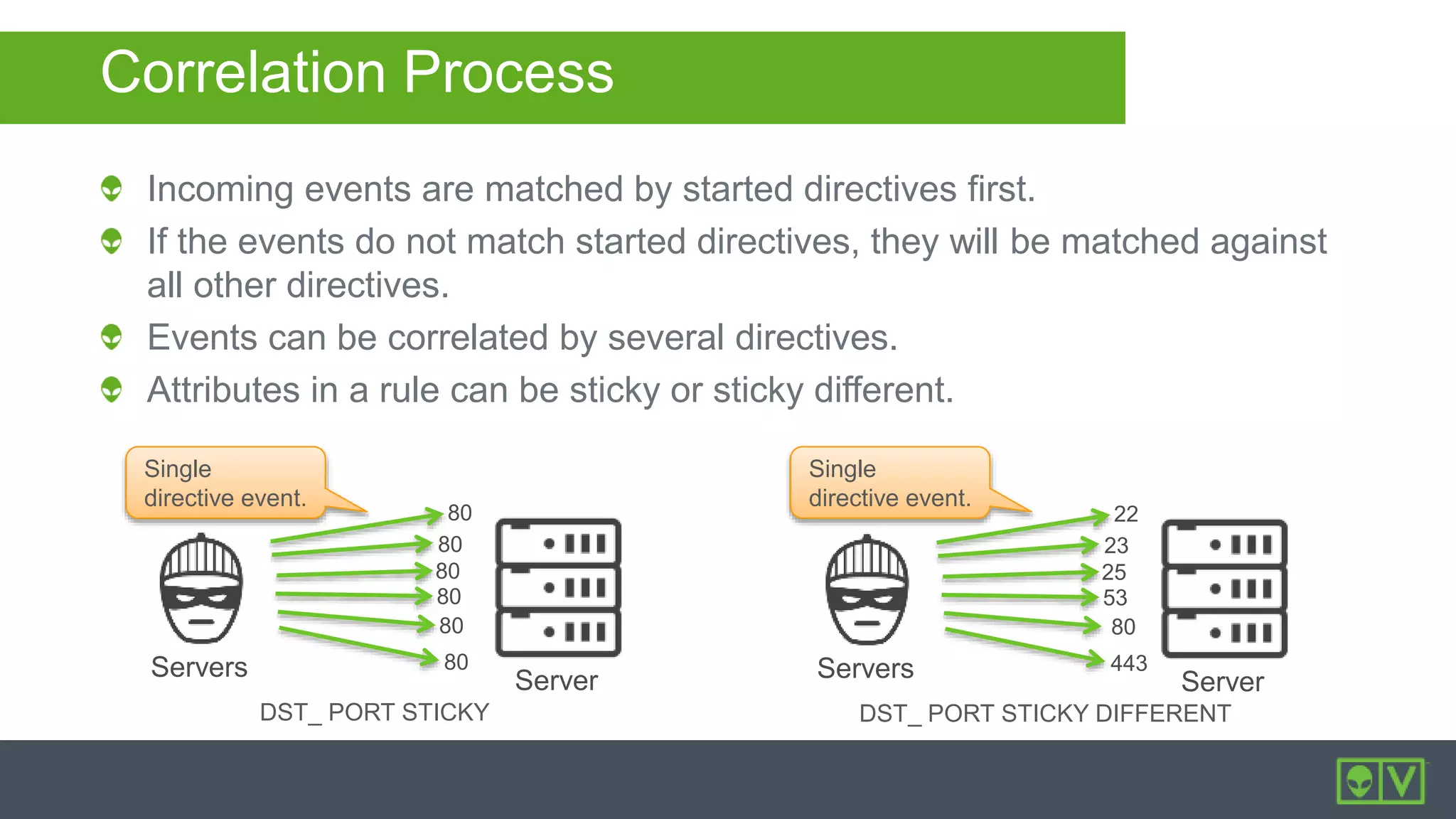
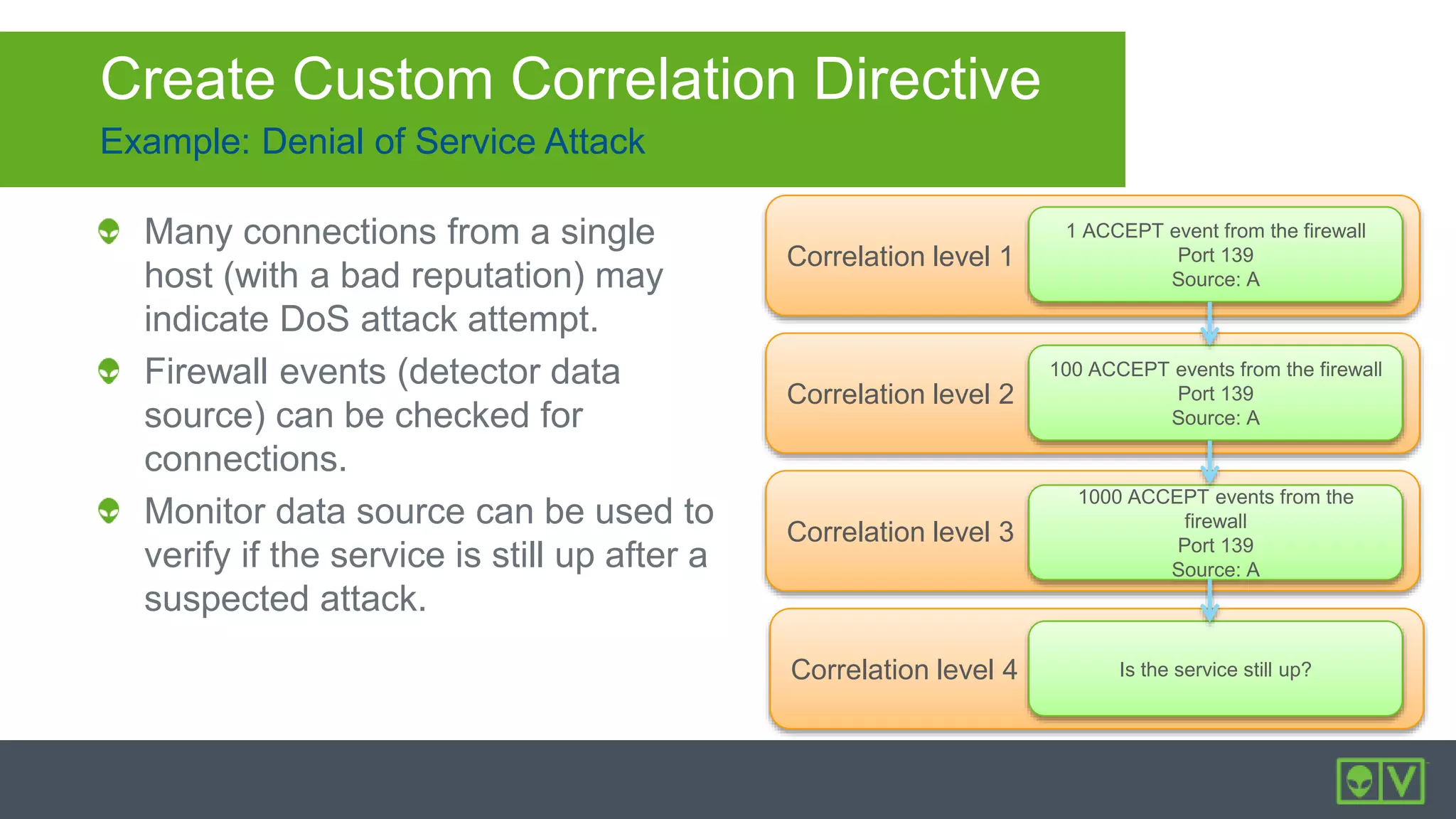
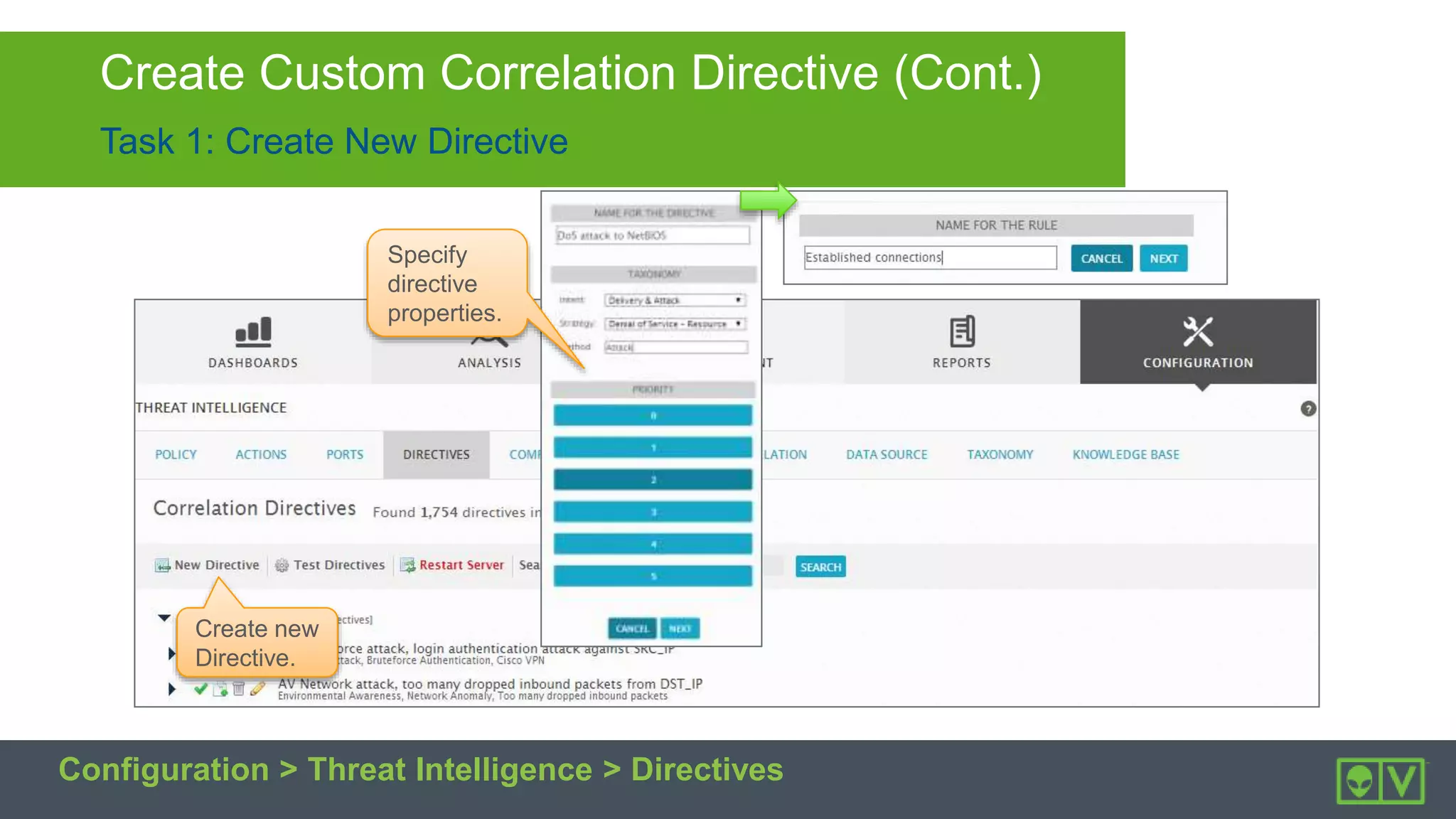
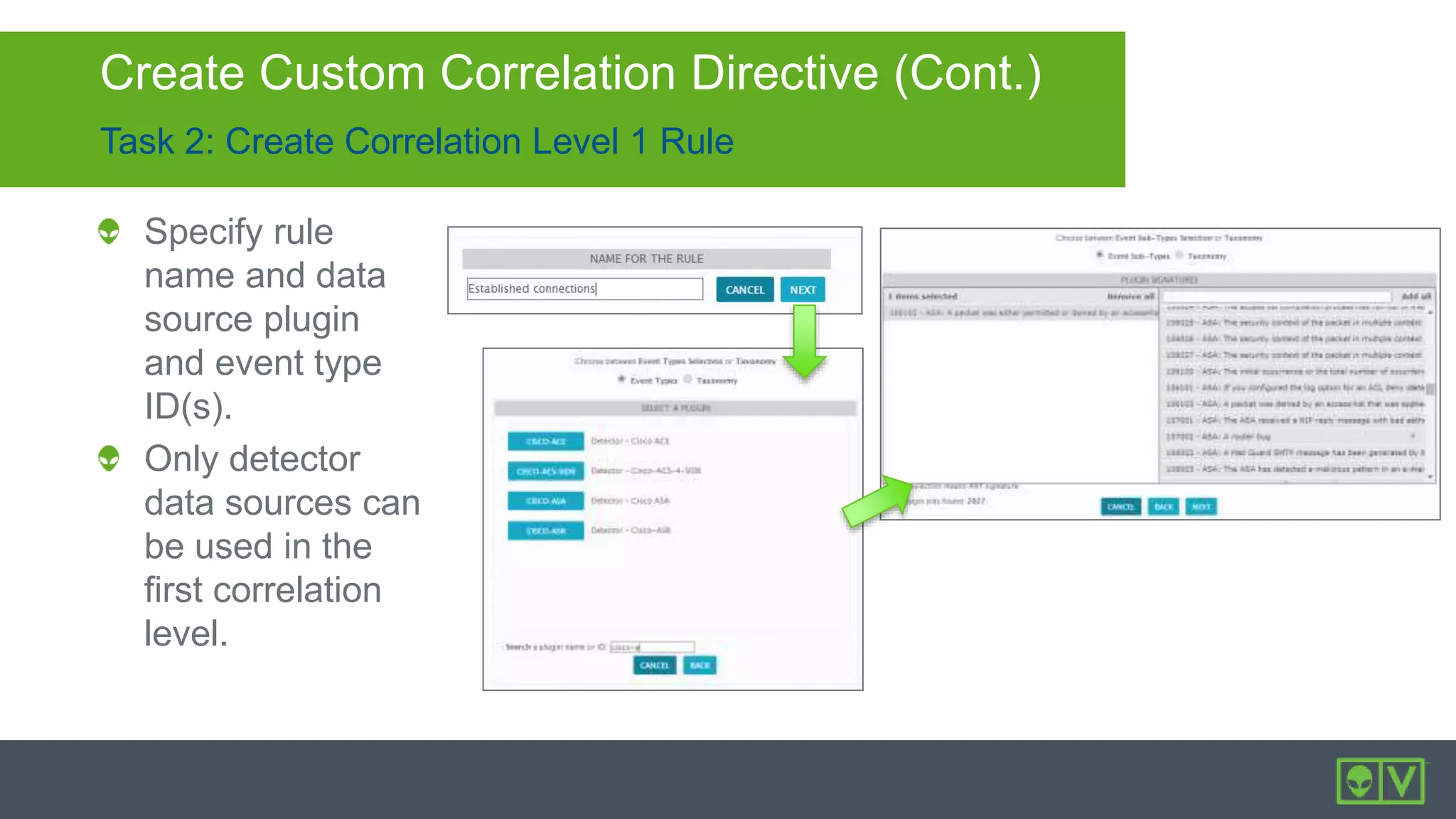
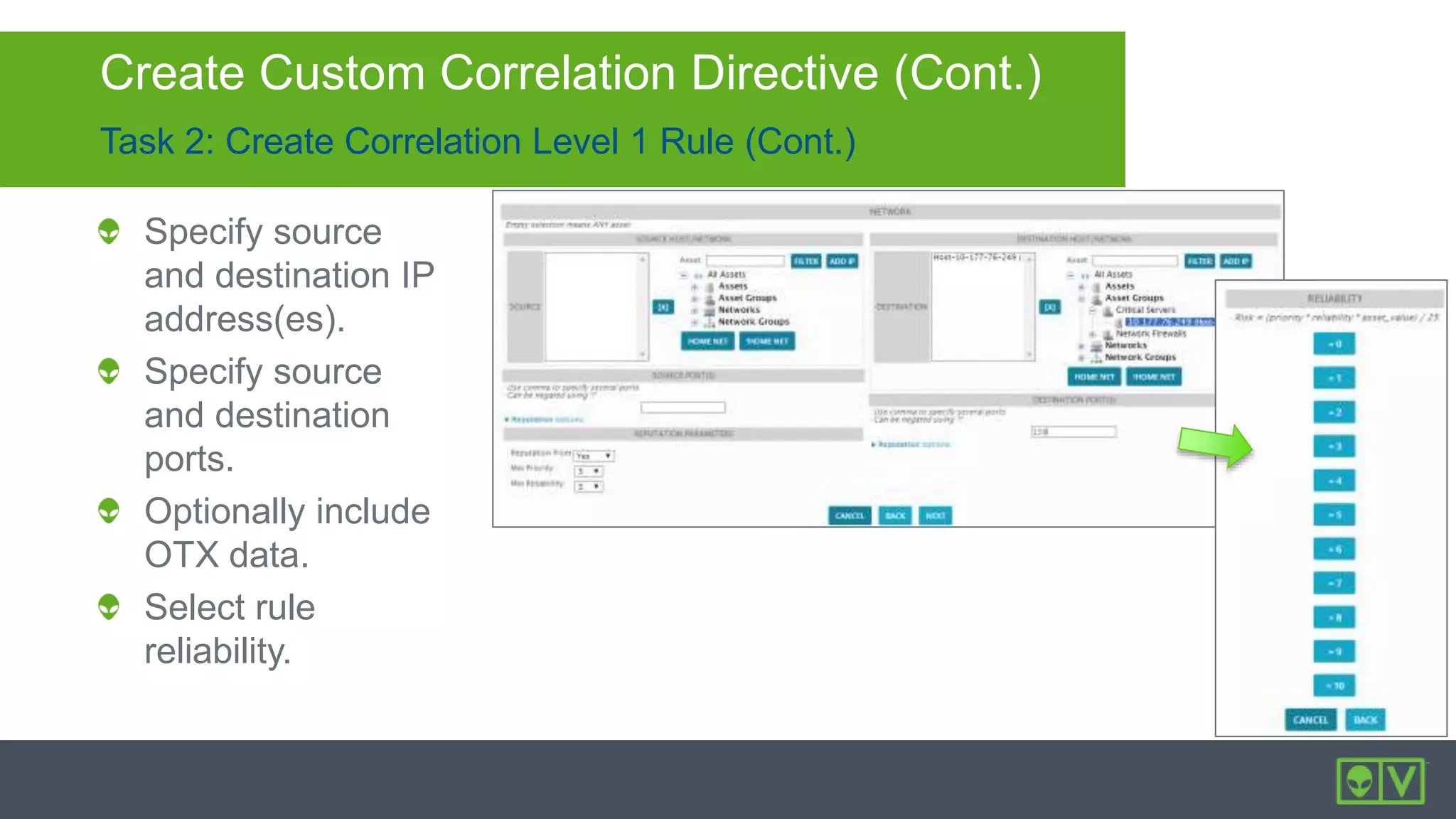
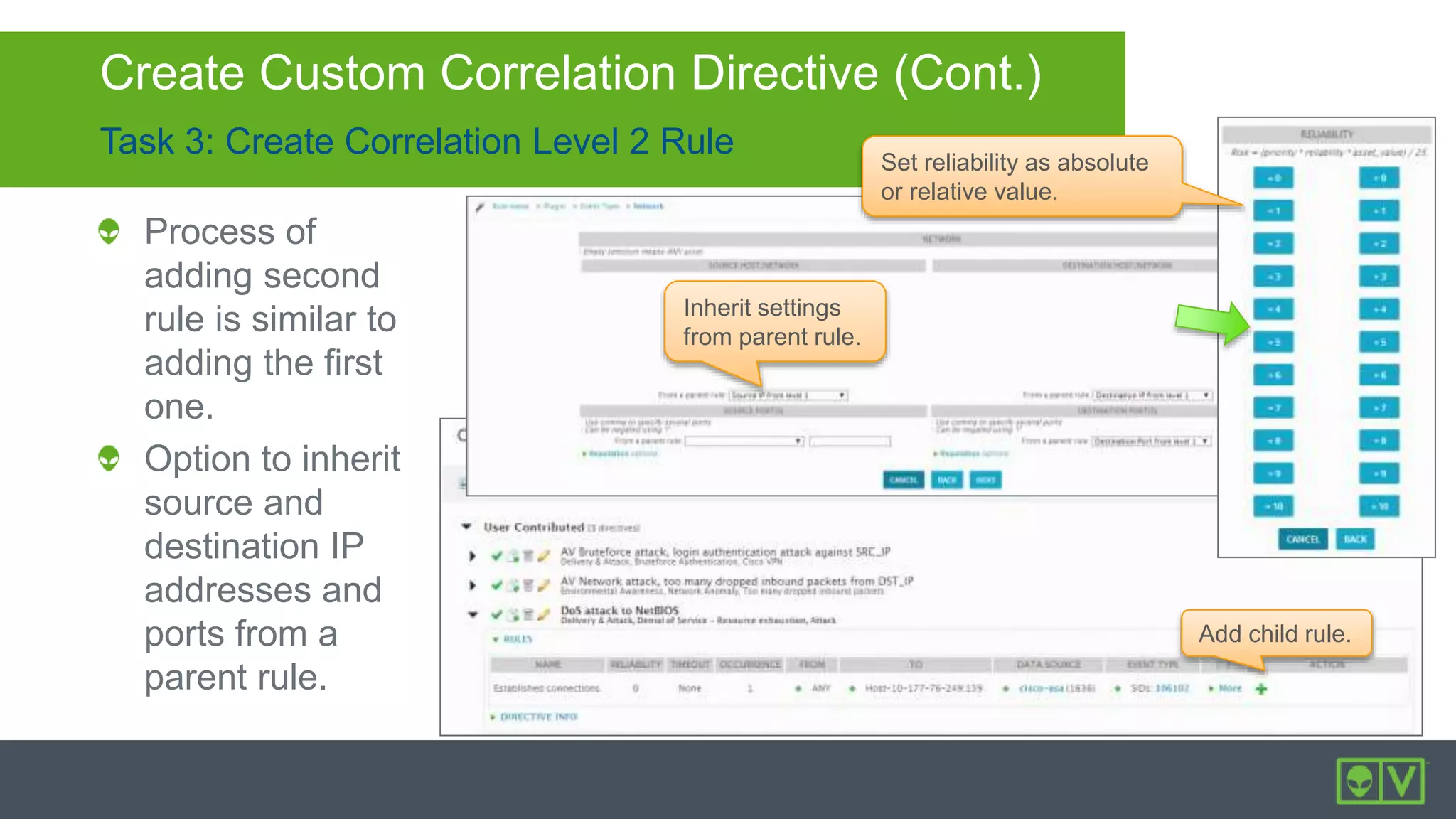
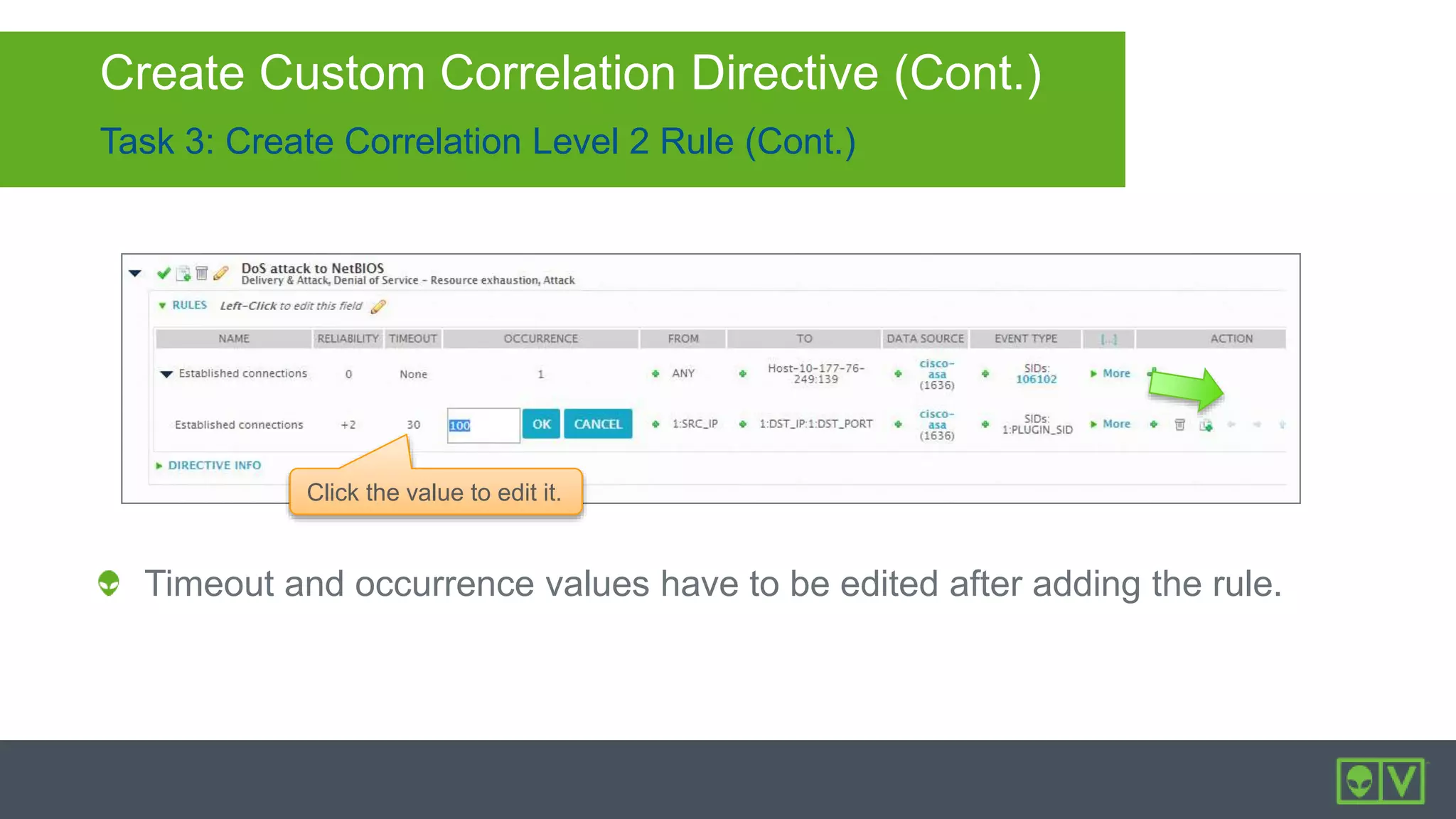
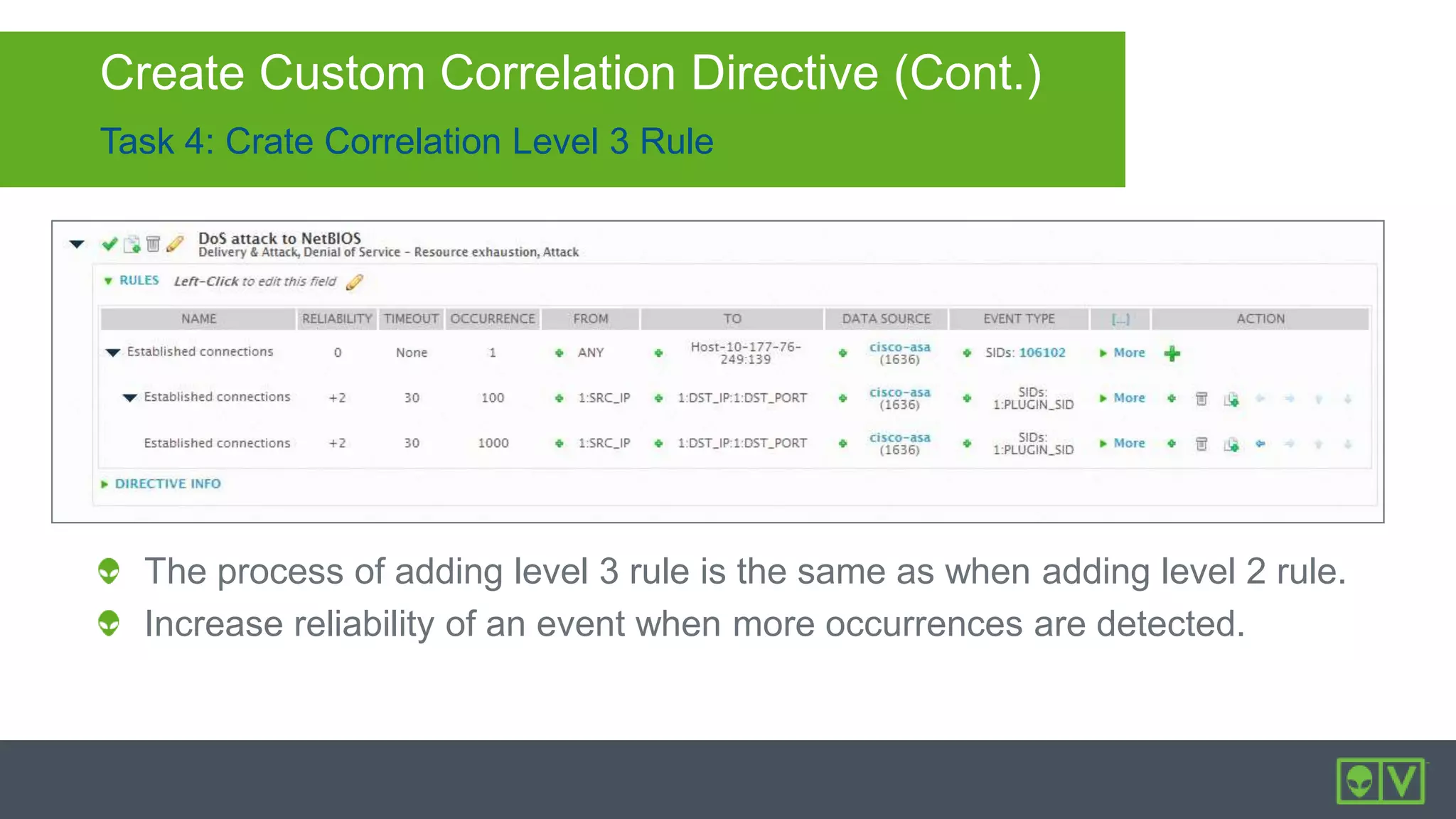
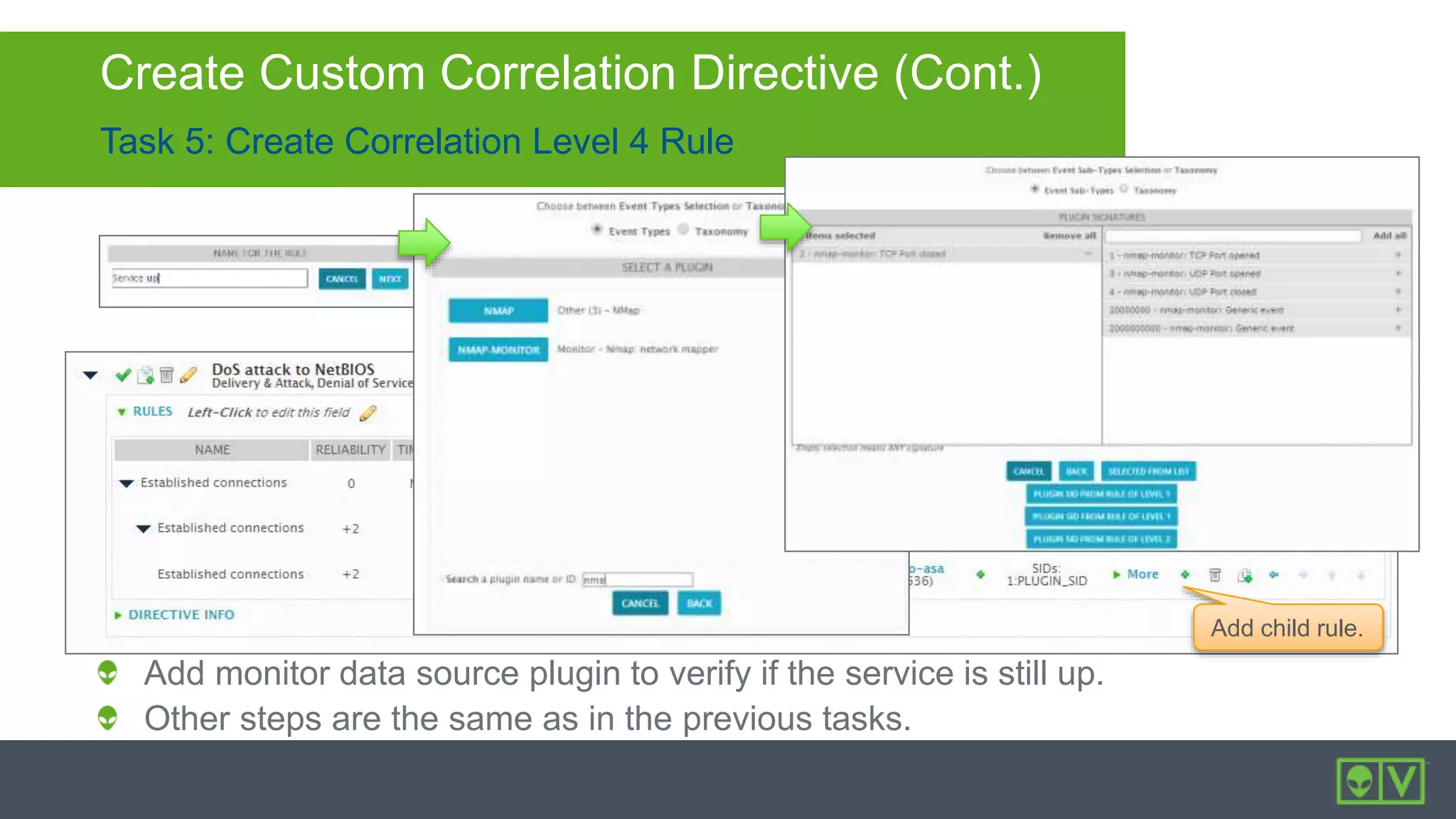
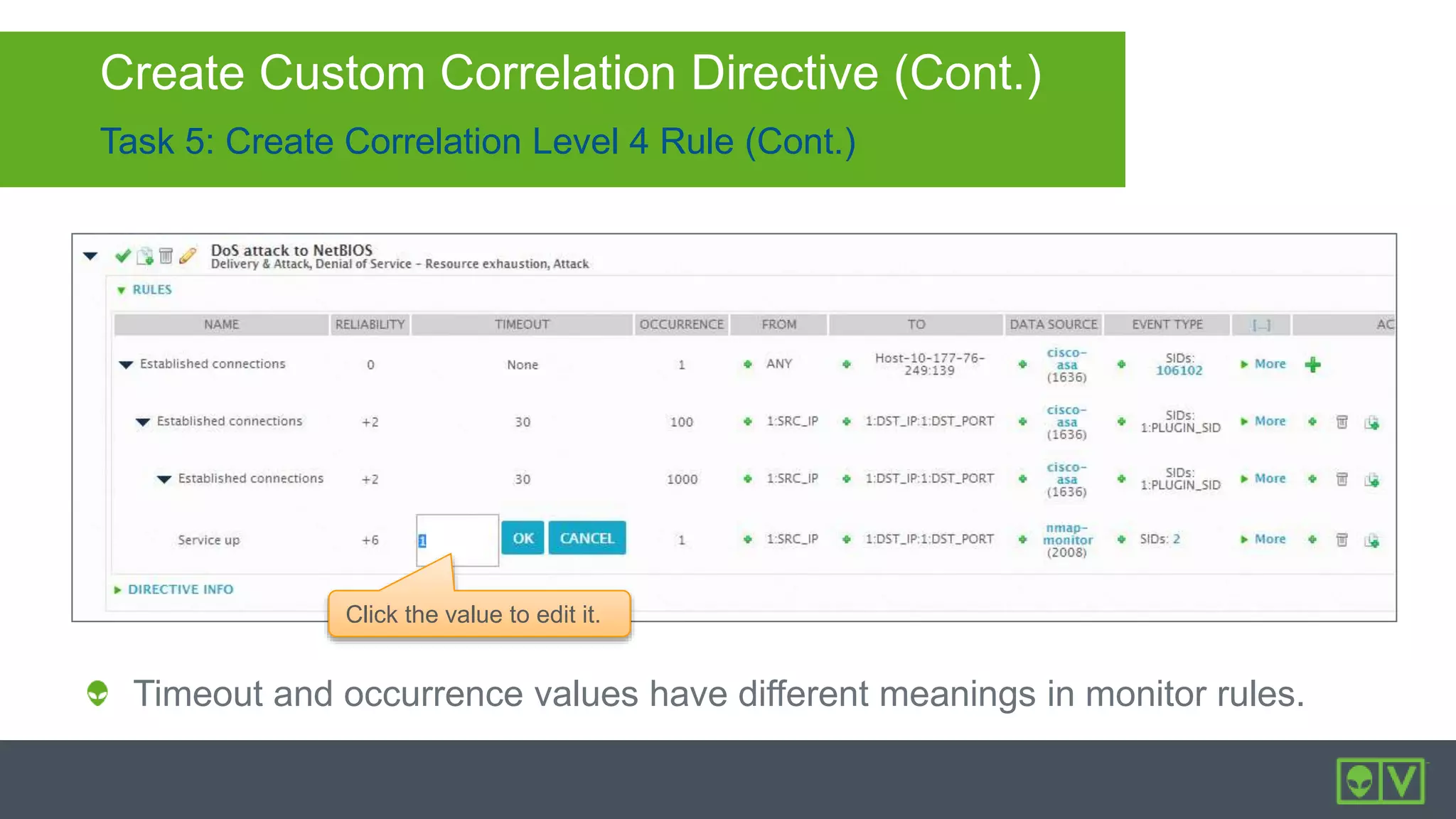
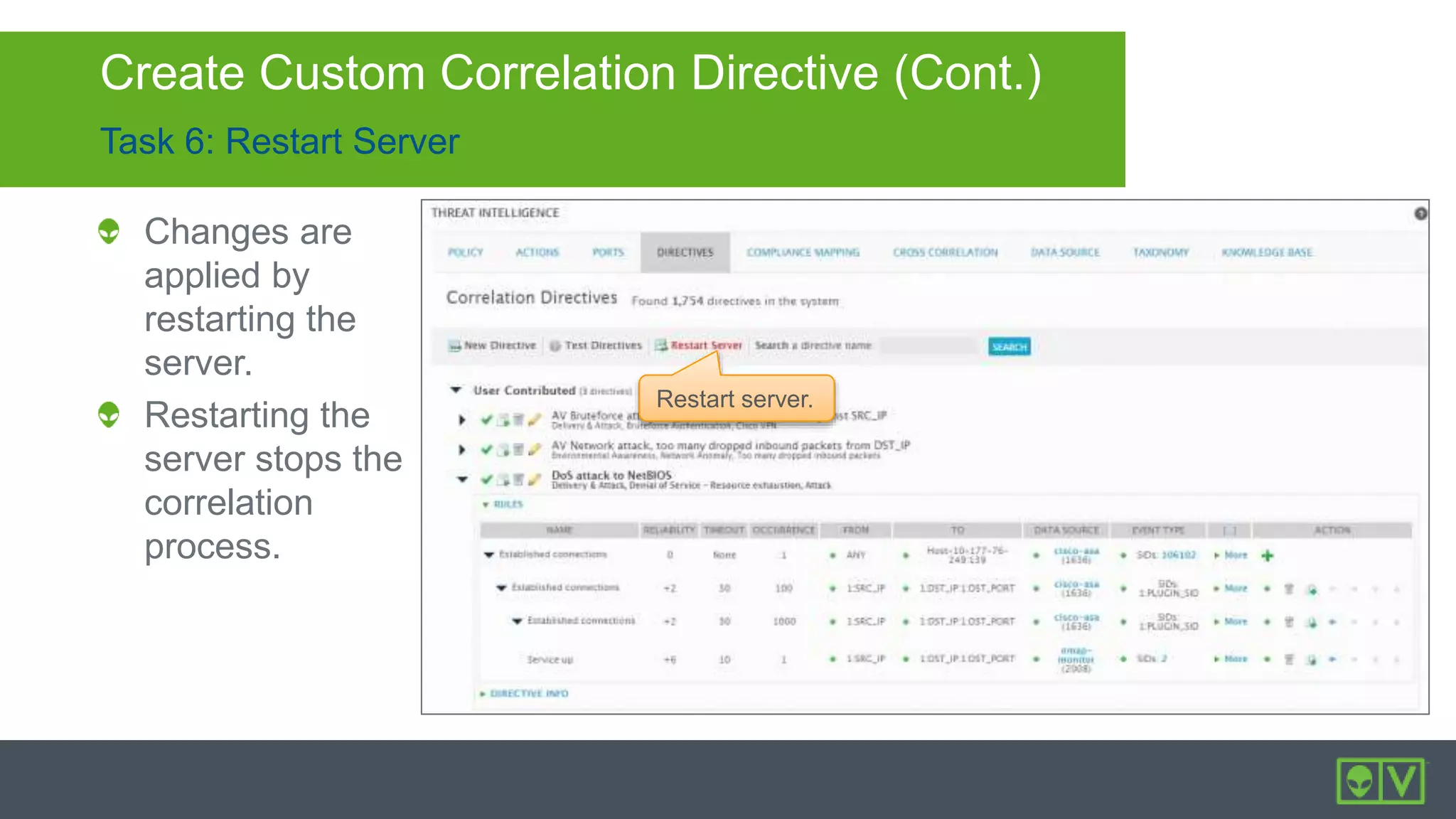
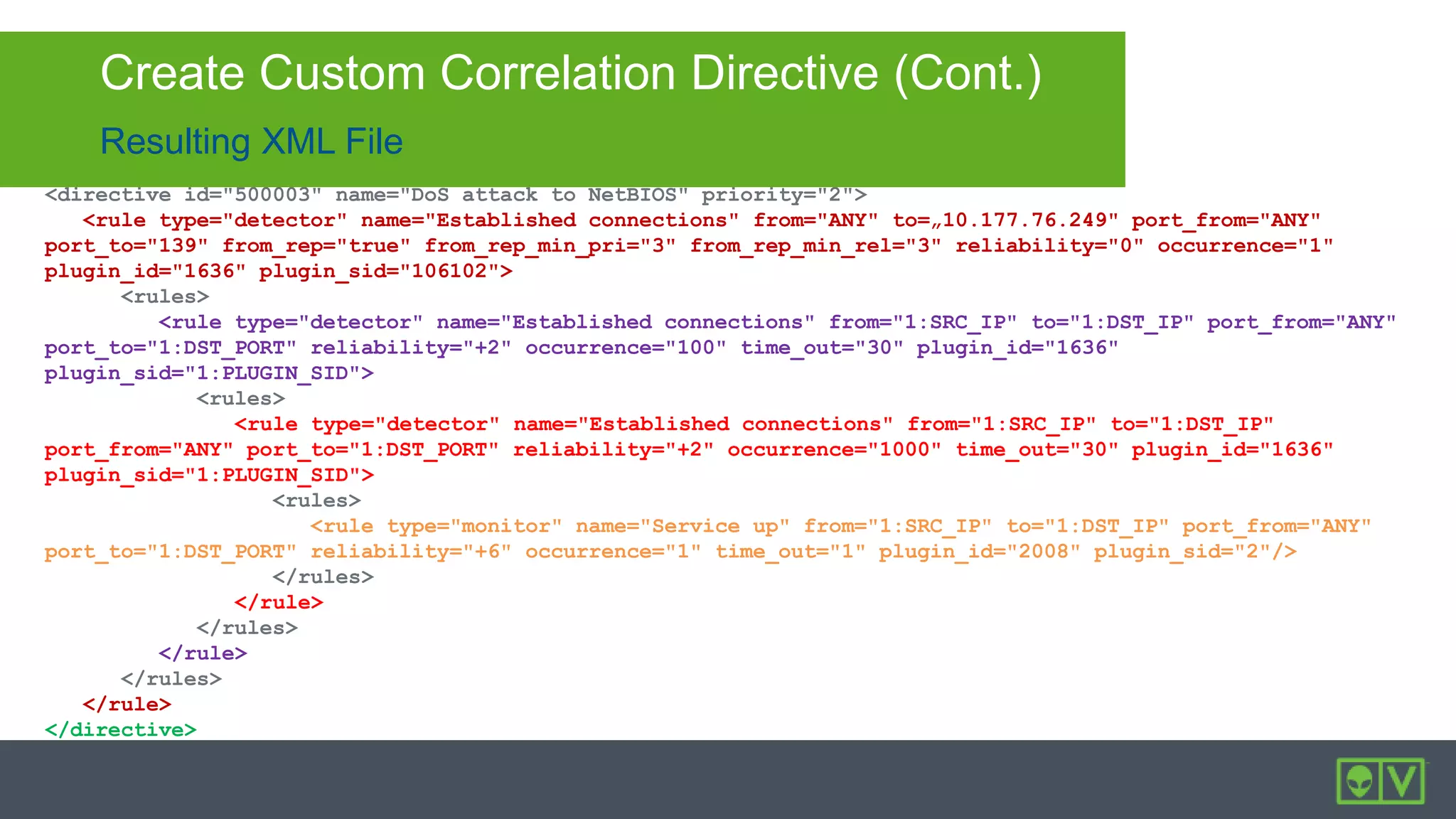
The document discusses how to utilize and customize correlation directives in AlienVault for enhancing security by turning event data into actionable alarms. It provides guidance on creating custom directives, setting correlation rules based on specific events, and managing alarms effectively. Best practices emphasize configuring directives with appropriate priority and reliability values while leveraging built-in directives for learning and adaptation.