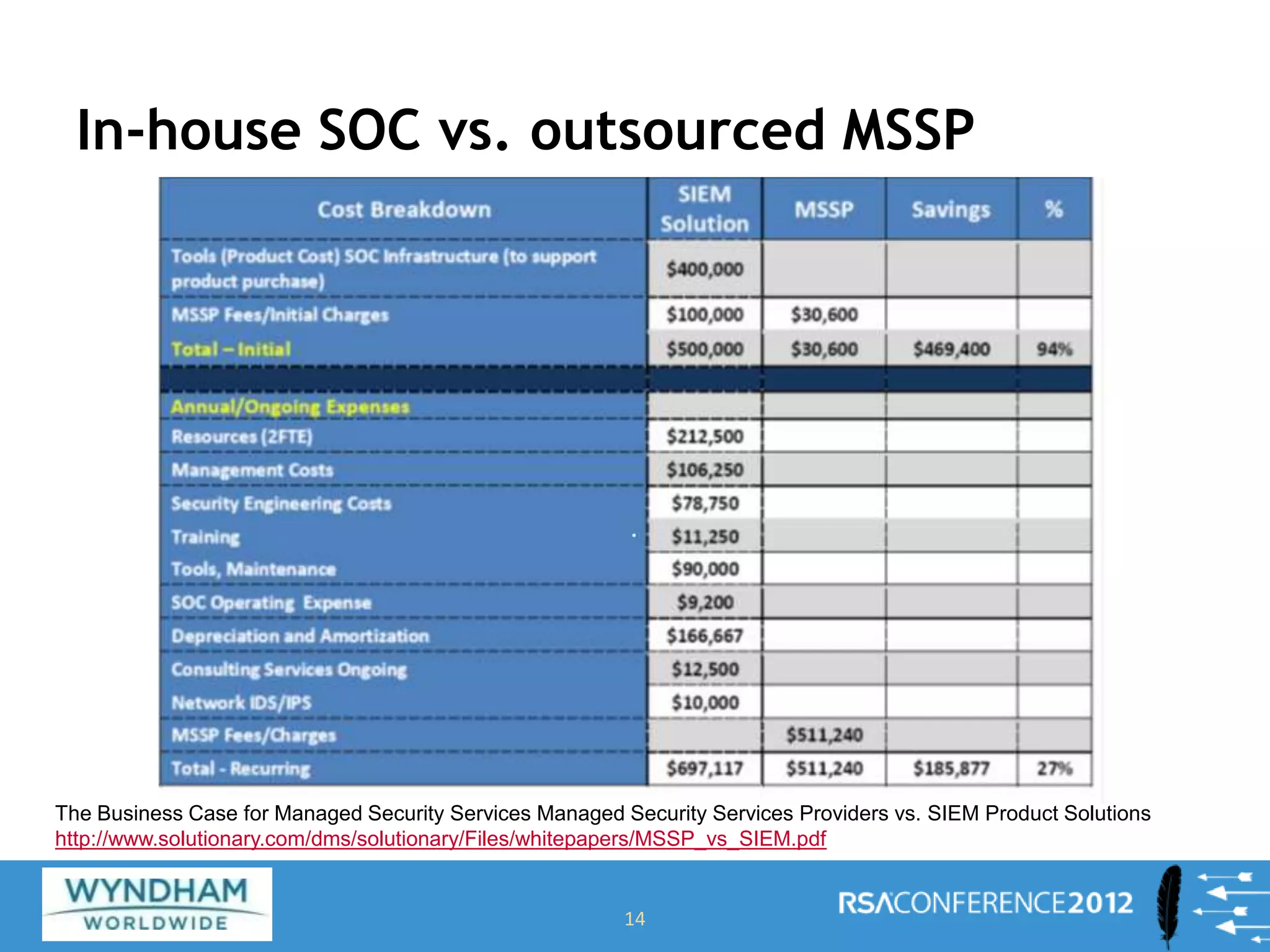
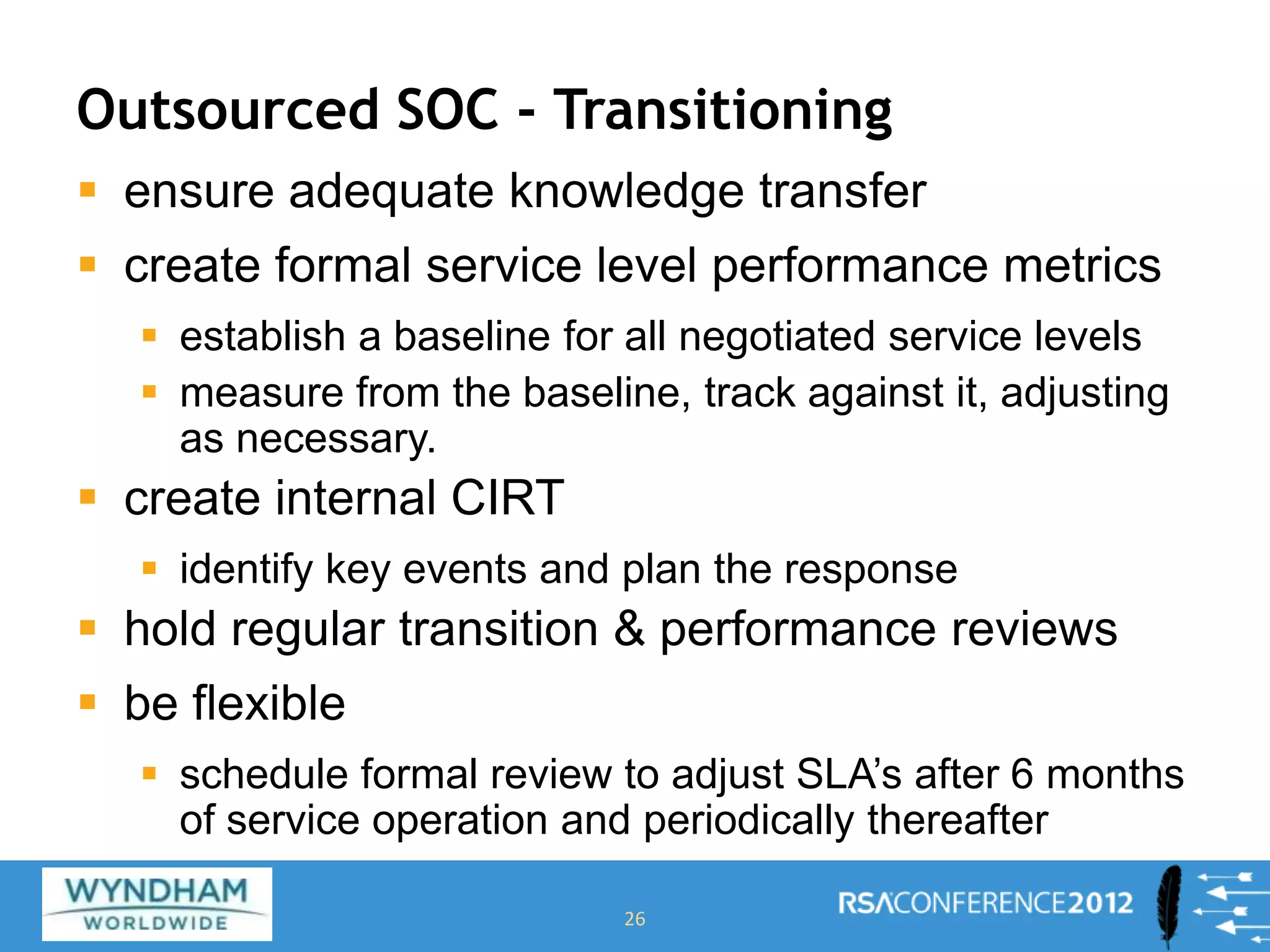
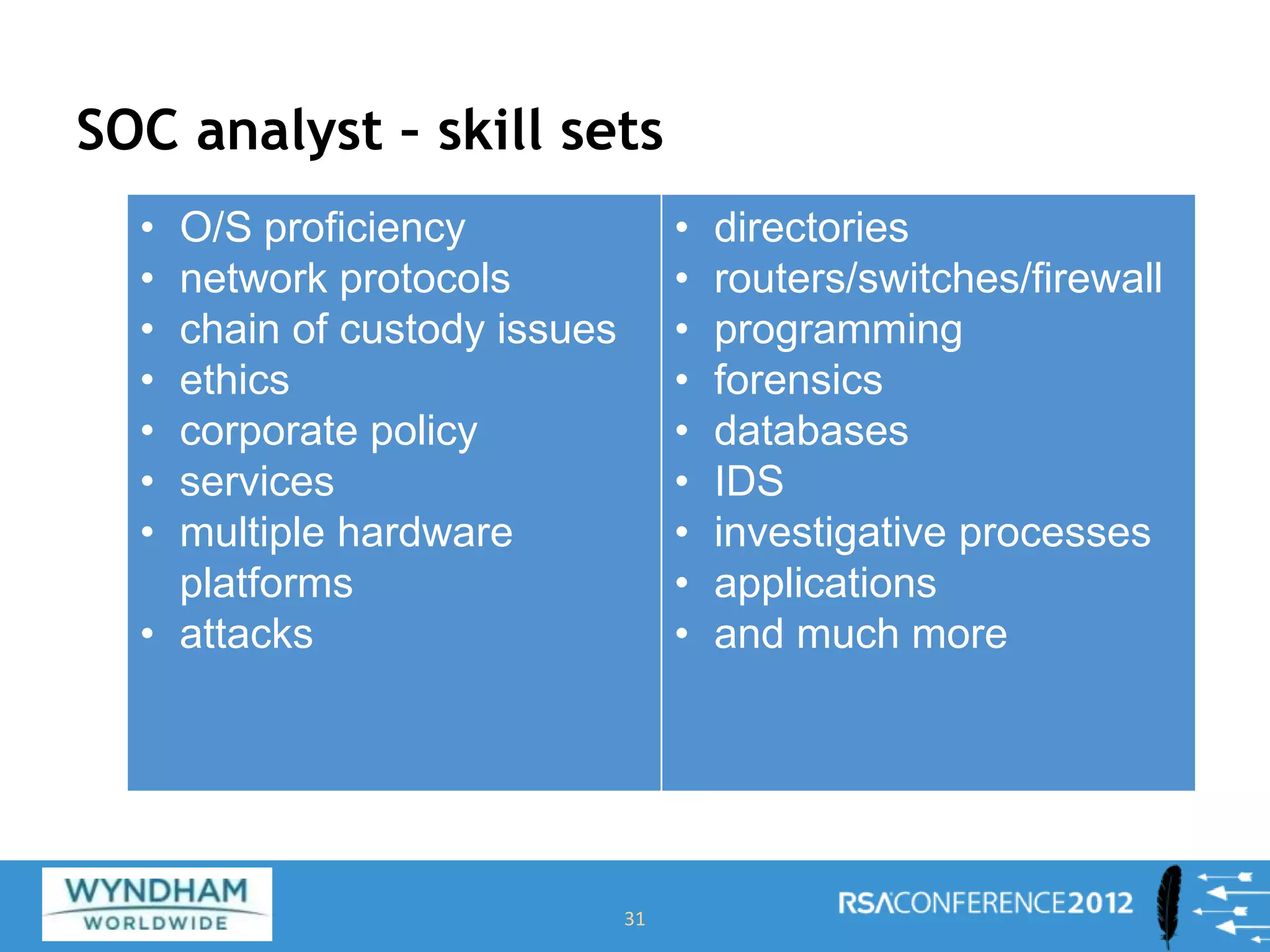
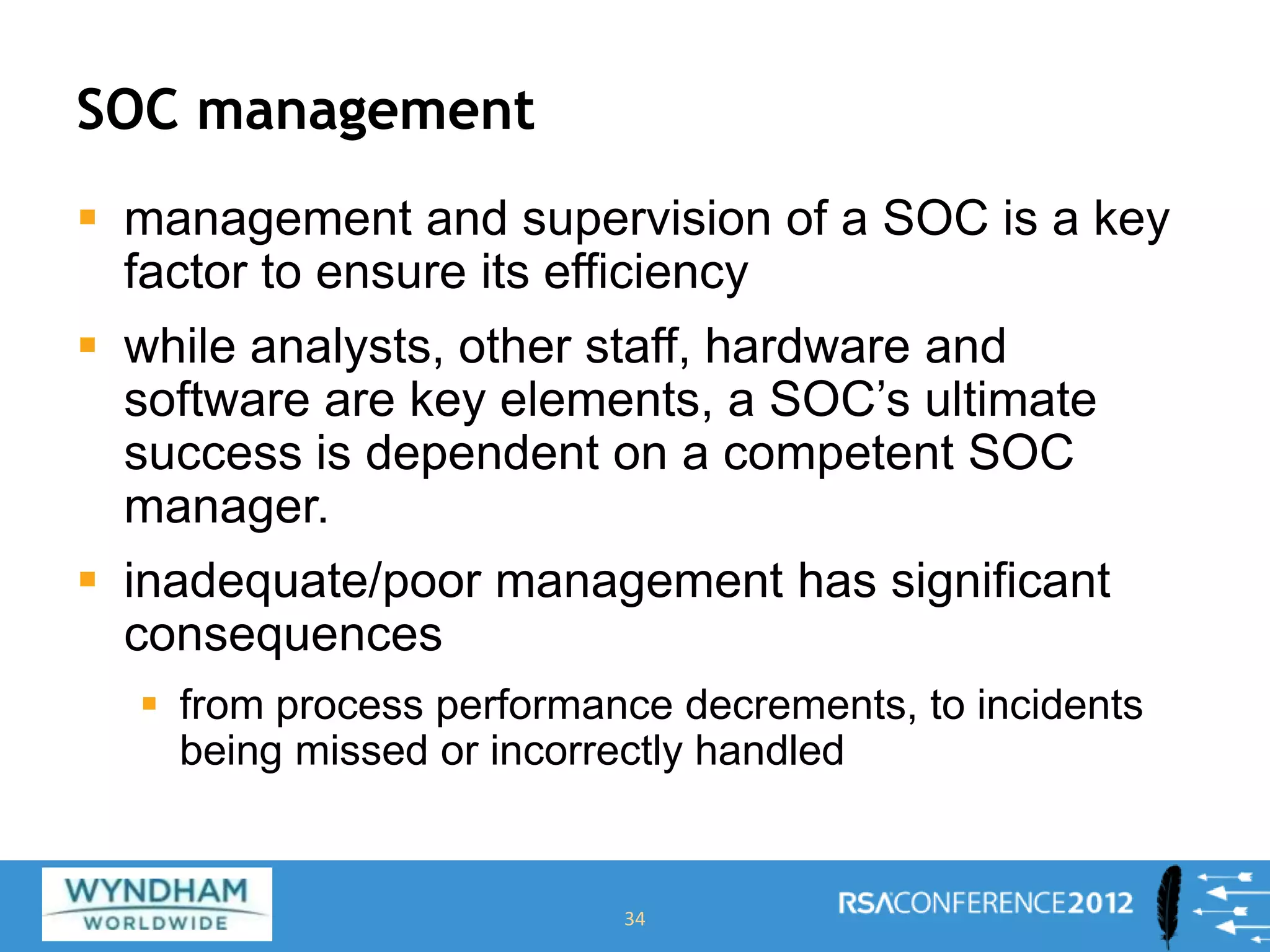
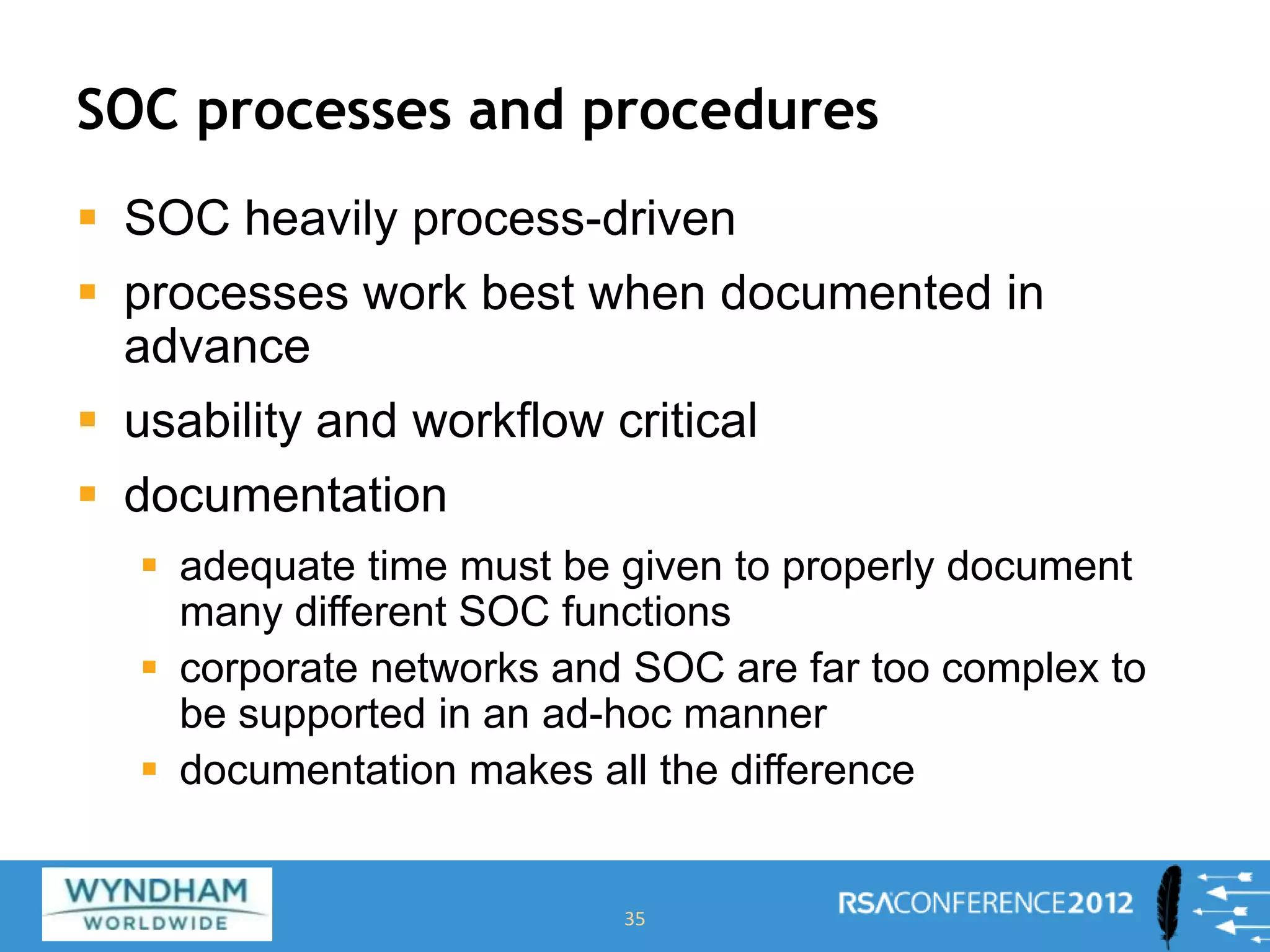
This document discusses building a Security Operations Center (SOC). It outlines the need for a SOC to provide continuous security monitoring, protection, detection and response against threats. It then discusses the key components of an effective SOC, including real-time monitoring, reporting, post-incident analysis and security information and event management tools. Finally, it examines the considerations around choosing to build an internal SOC versus outsourcing to a managed security service provider.