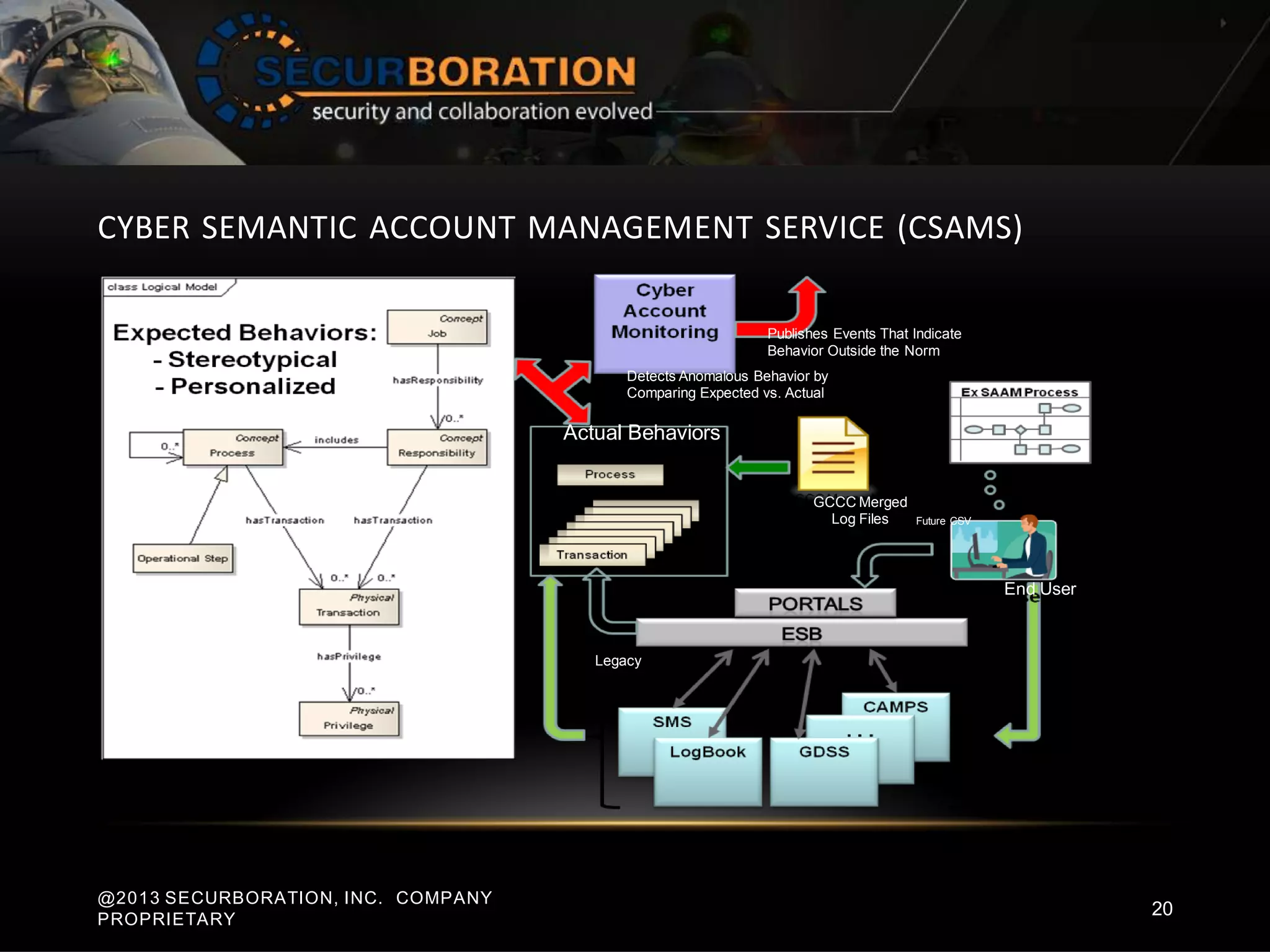
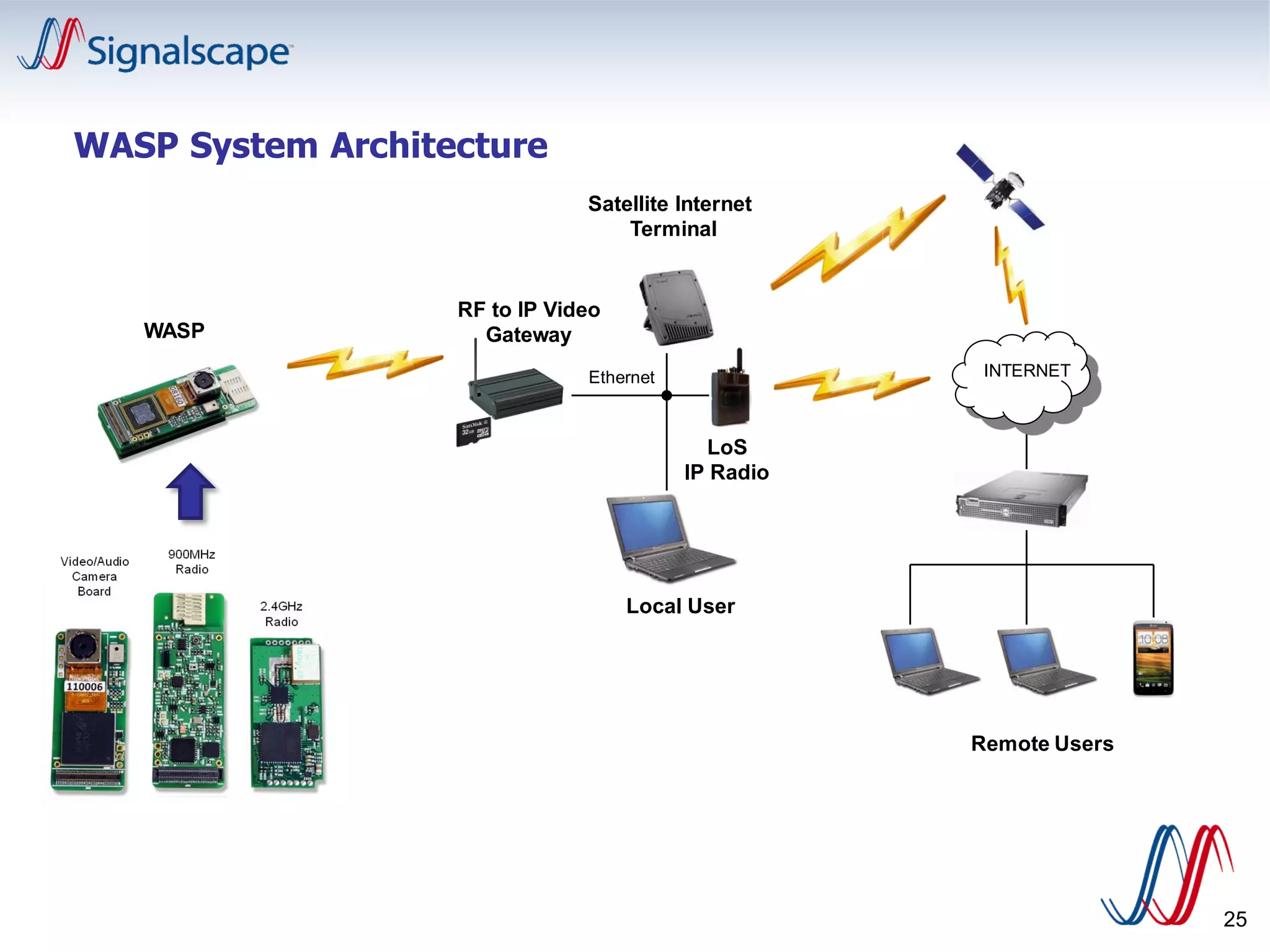
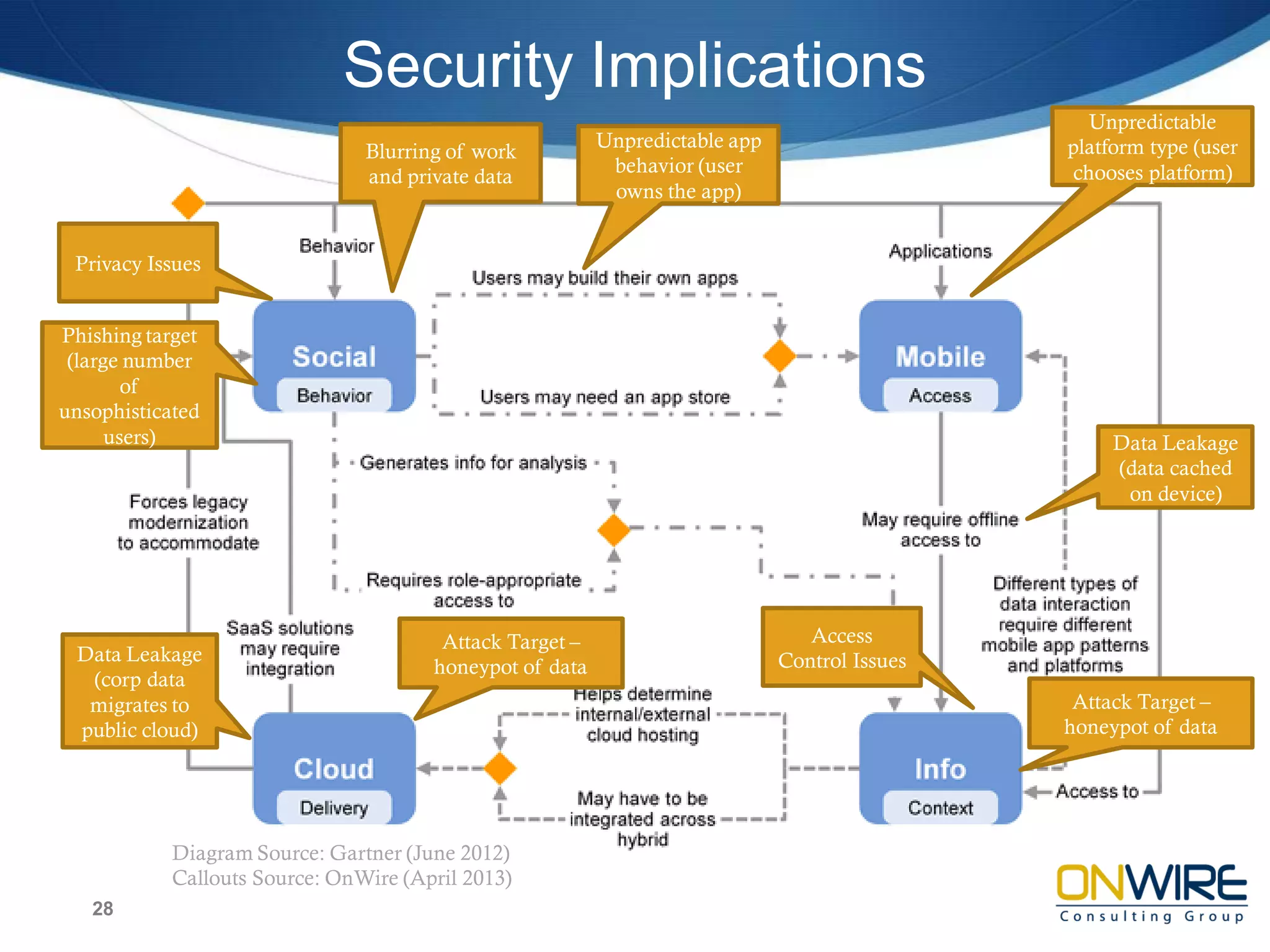
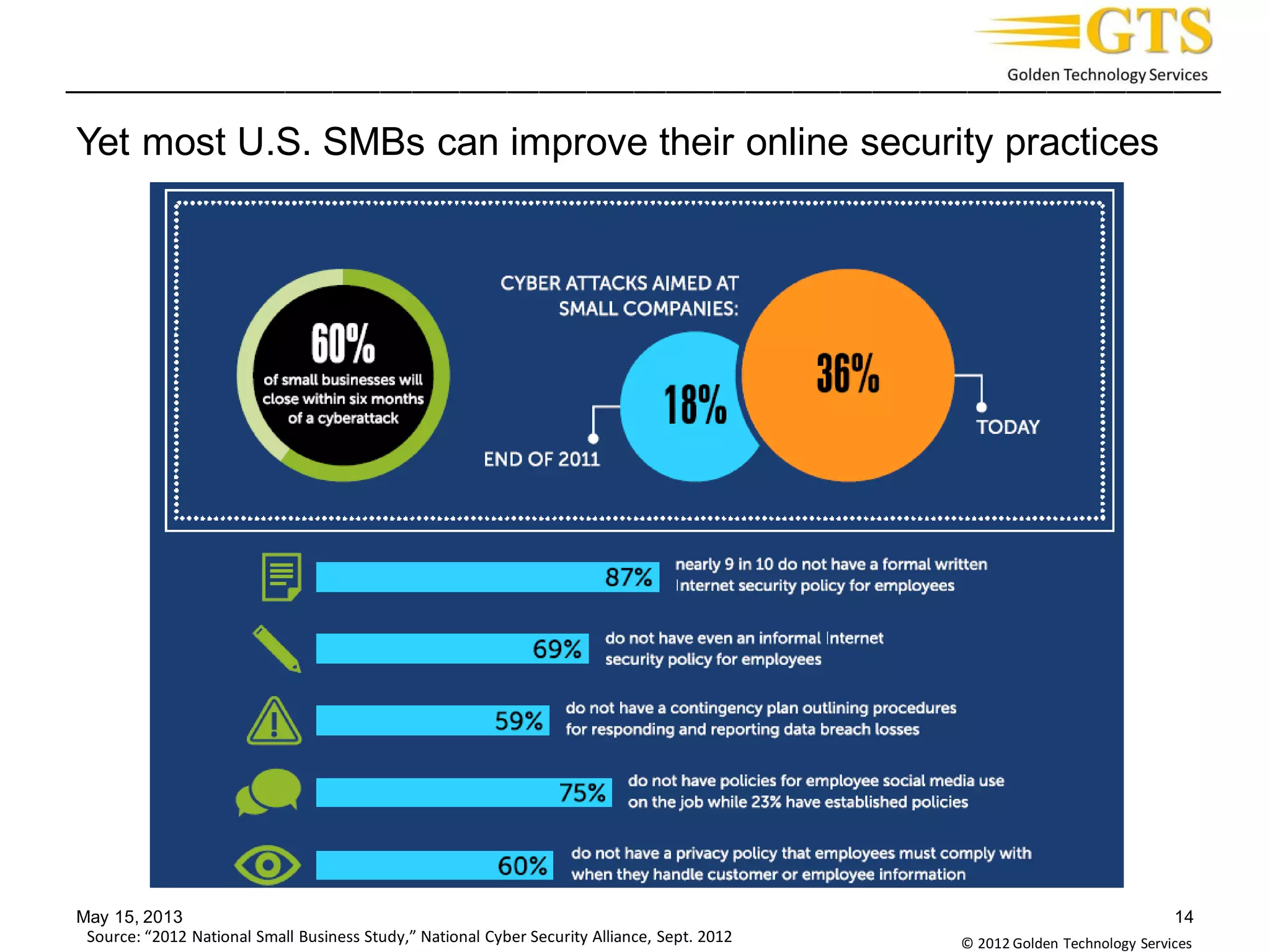
The document summarizes a cyber security panel discussion held on May 9, 2013 in North Carolina. It provides background on the event sponsors and introduces Professor Ehab Al-Shaer, the director of the Cyber Defense Network Assurability Center at UNC Charlotte, who presented on security configuration analytics. It also briefly describes Al-Shaer's research at UNC Charlotte focusing on security configuration verification and risk estimation.

![About CyberDNA Research
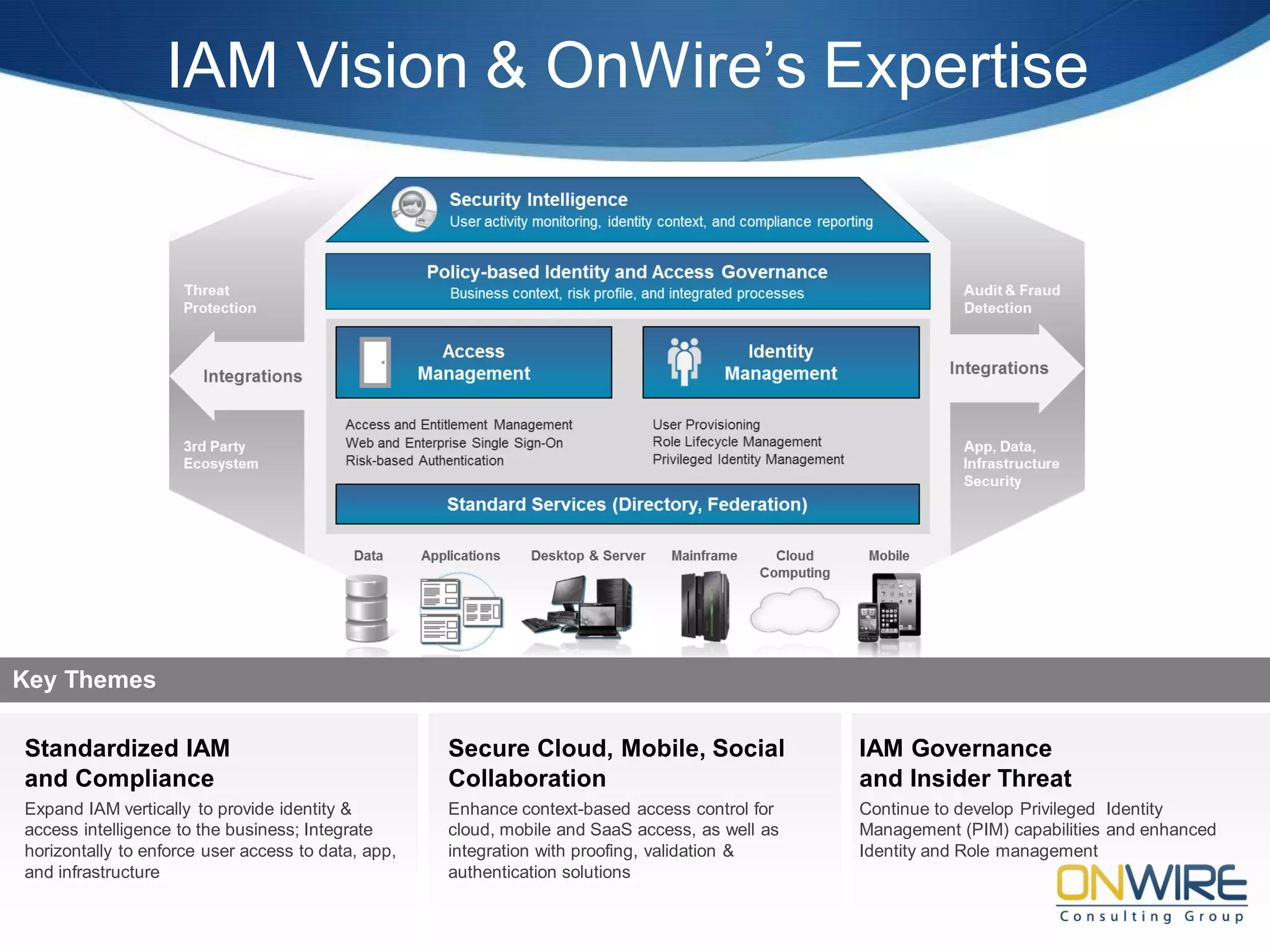
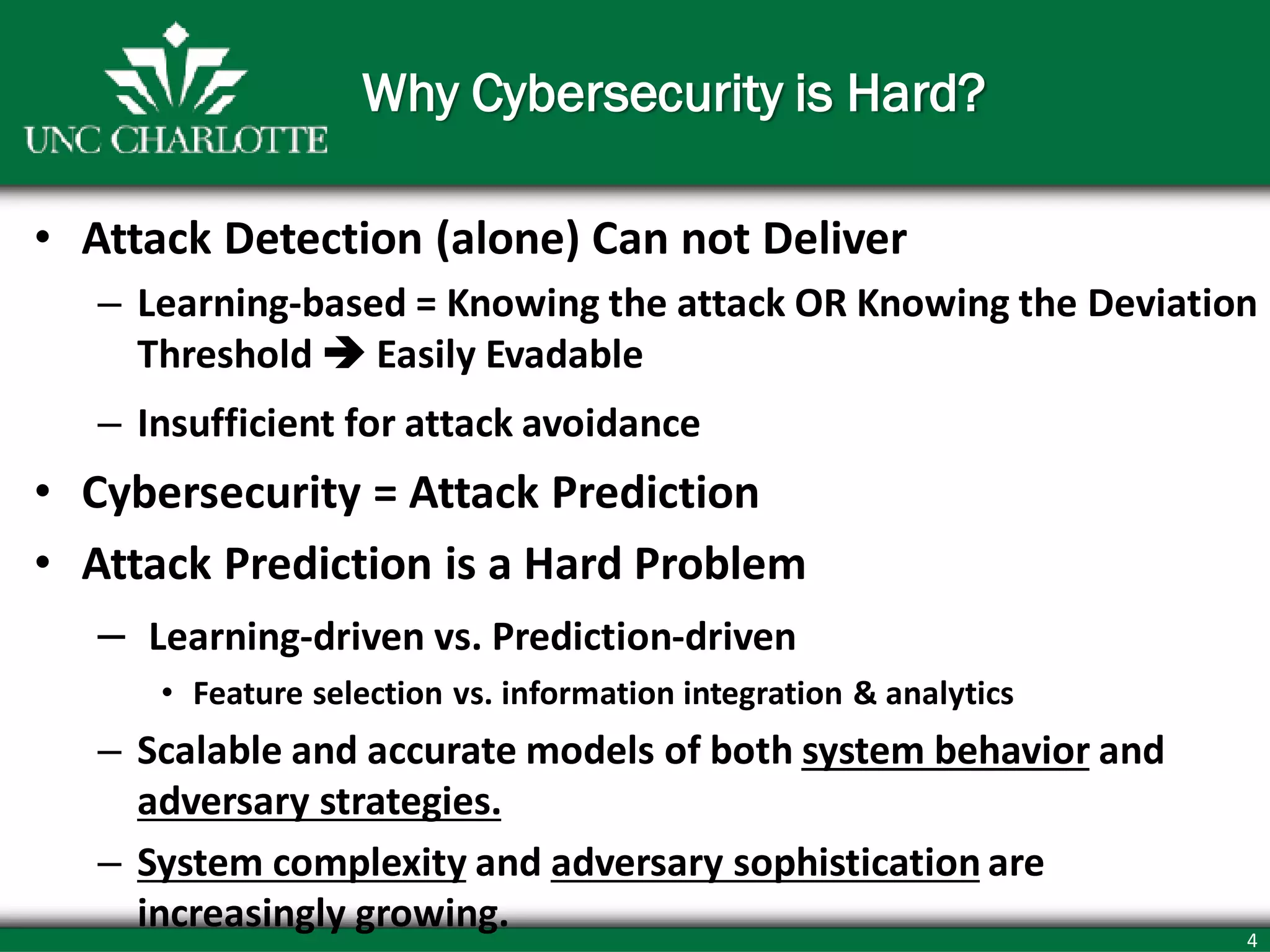
• Vision: Making Cybersecurity measurable, provable and usable
• Research Team:
– Multi-disciplinary team of 11 faculty members and 35 PhD students Areas
– security, networking, data mining, economics, power and control, behavior science/HCI.
• Active Funding: > 8.2M from NSF, NSA, ARO, AFRL, DHS, Bank of America, BB&T,
DTCC, Duke Energy, Cisco, Intel
• Prof. Al-Shaer was featured as Subject Matter Expert (SME) in Security
Configuration Analytics and Automation [DoD Information Assurance Newsletter,
2011].
• NSF Industry/University Collaborative Research Center on (Security) Configuration
Analytics and Automation (CCAA) Lead by UNC Charlotte and George Mason Univ
– Members include NSA, NIST, Bank of America, BB&T, DTCC, MITRE, Northrop Grumman
• Tools and Technology transfer projects for Cisco, Intel, Duke Energy, ..
• Research Long and solid track record on many areas particularly
– Security configuration analytics (verification and synthesis) for enterprise,
cloud and smart grid
– Security metrics and risk estimation
– Agility and resiliency for Cyber, clouds and Cyber-Physical](https://image.slidesharecdn.com/fatscybersecurity-130517073100-phpapp01/75/Cyber-Security-3-2048.jpg)
![6
The Need for Security Configuration
Analytics
• December 2008 report from Center for Strategic and International Studies
"Securing Cyberspace for the 44th Presidency" states that "inappropriate
or incorrect security configurations were responsible for 80% of Air Force
vulnerabilities"
• May 2008 report from Juniper Networks "What is Behind Network
Downtime?" states that "human factors [are] responsible for 50 to 80
percent of network device outages".
• BT/Gartner[3] has estimated that 65% of cyber-attacks exploit systems
with vulnerabilities introduced by configuration errors. The Yankee
Group[4] has noted that configuration errors cause 62% of network
downtime.
• A 2009 report[5] by BT and Huawei discusses how service outages caused
by “the human factor” themselves cause more than 30% of network
outages, “a major concern for carriers and causes big revenue-loss.](https://image.slidesharecdn.com/fatscybersecurity-130517073100-phpapp01/75/Cyber-Security-5-2048.jpg)
![7
Ehab Al-Shaer , Science of Security Configuration
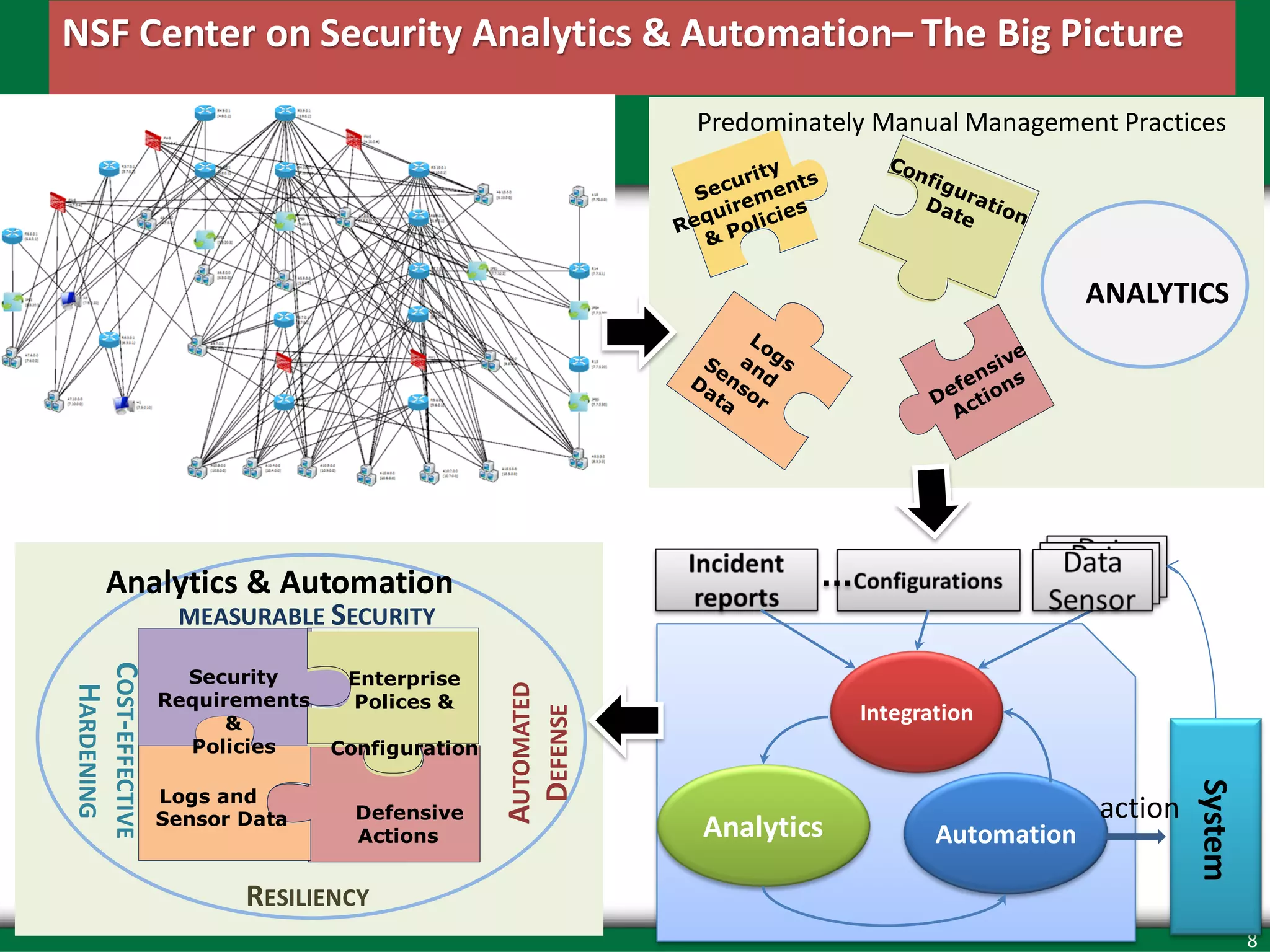
Complexity of Configuration Analytics
• Scale – thousands of devices and million of rules.
• Distributed, yet Inter-dependent Devices and Rules.
• Policy semantic gap -- device roles (e.g., Rule-order semantics vs.
recursive ACL, single-trigger vs. multi-trigger policies)
• Multi-level and multi-layer Network configuration
– Overlay networks, groups/domains in cloud (e.g., EC2/VPC, security
groups)
– network access control, OS, application level etc
• Dynamic changes in networks and threat
• Security design trade-offs: risk vs mission, usability, cost, and
performance
[Source: Security Analytics and Automation, DoD IA Newsletter, Oct 2011]
7](https://image.slidesharecdn.com/fatscybersecurity-130517073100-phpapp01/75/Cyber-Security-6-2048.jpg)
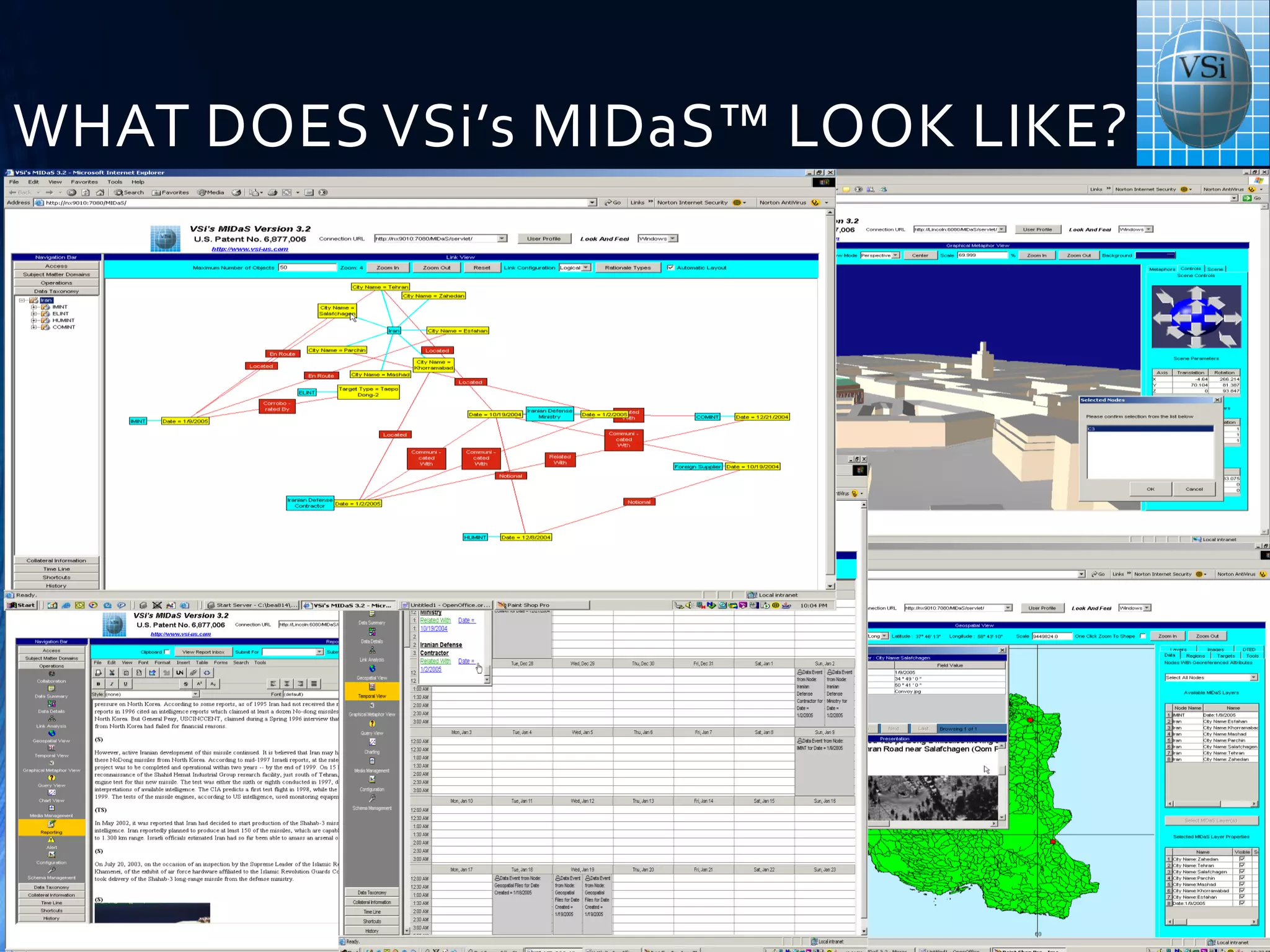
![9
Policy
Violation
Threat
Prediction
Risk
Estimation
ConfigChecker: Security Analytics
Magic Box [ICNP09]
Risk
Mitigation
Attack
DiagnosisAgility
Actions
Resiliency
measure
ConfigChecker](https://image.slidesharecdn.com/fatscybersecurity-130517073100-phpapp01/75/Cyber-Security-8-2048.jpg)



![INTRUSION DETECTION
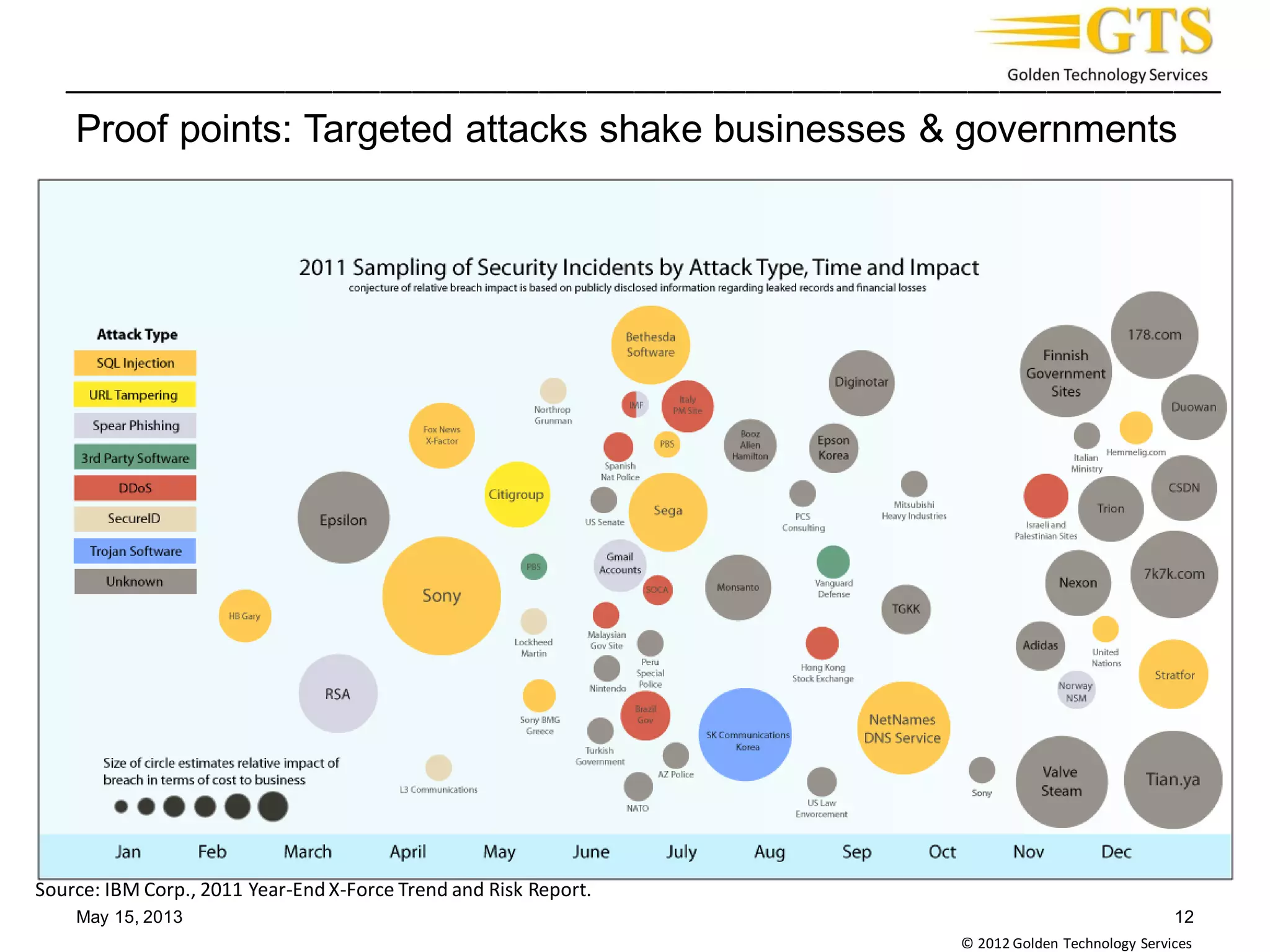
• Traditional protection technologies have matured
• National Vulnerability Database (http://nvd.nist.gov) vulnerability disclosures
across the industry in 1H2011 were down 37.1% from 2H2008[1]
• Class of tools
• e-Sentinel
• Host Based Security System
@2013 SECURBORATION, INC. COMPANY
PROPRIETARY
17
VulnerabilityDisclosures](https://image.slidesharecdn.com/fatscybersecurity-130517073100-phpapp01/75/Cyber-Security-16-2048.jpg)