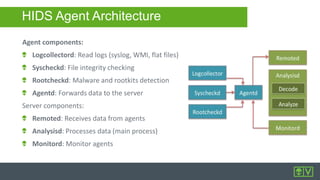
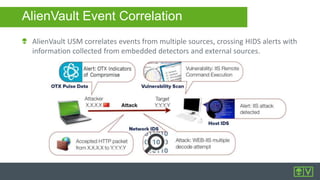
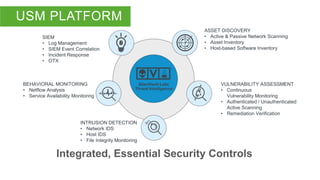
The document outlines the features and capabilities of AlienVault's Unified Security Management (USM) platform, designed for efficient threat detection and incident response for IT teams. It highlights the integration of threat intelligence, compliance, and various security monitoring and event correlation functionalities. Additionally, it offers insights into the hosting and operational architecture of the system, including its components and management interface.