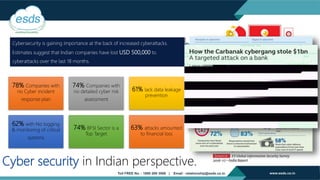
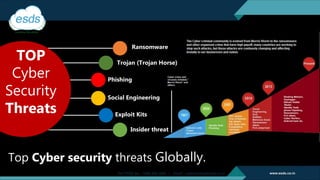
The document discusses the necessity of Security Operations Center (SOC) services in response to increasing cyber threats, emphasizing the evolution of cybersecurity from a luxury to a necessity for organizations. It highlights the offerings of ESDS' SOC services, including cost-effective, subscription-based models that provide 24/7 monitoring and management of security functions, aiming to protect organizations from potential cyber threats. Additionally, the document showcases ESDS's experience, industry recognition, and certifications, reinforcing its credibility as a trusted provider in the cybersecurity landscape.