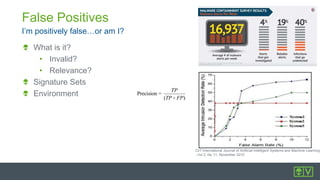
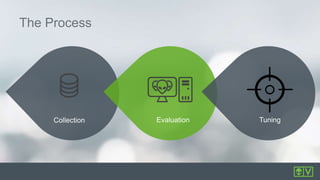
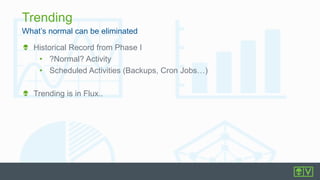
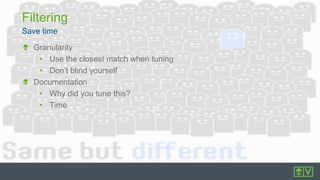
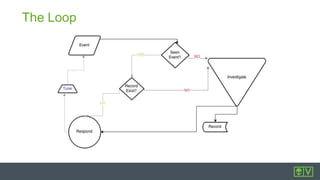
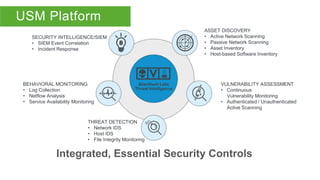
The document discusses best practices for intrusion detection systems (IDS). It recommends a three phase process: collection, evaluation, and tuning. In the collection phase, an IDS gathers baseline data for 2 weeks. In evaluation, valuable and actionable events are identified based on policy, risk, and environment. Trending helps eliminate normal activity. Tuning removes unnecessary events to reduce false positives and save time through threshold adjusting and awareness of network details. Updates may require periodic re-evaluation and tuning to account for changes.



![It’s where you put things….
Installation [Day 0]
1. Pre-install checklist
2. Where (inside/outside, core/perimeter)
3. Tap/span/port-mirror
4. How much traffic can you handle / ROI](https://image.slidesharecdn.com/ids-analyst-prezo-3-150317121304-conversion-gate01/85/IDS-for-Security-Analysts-How-to-Get-Actionable-Insights-from-your-IDS-5-320.jpg)