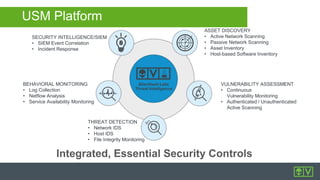
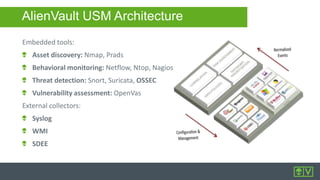
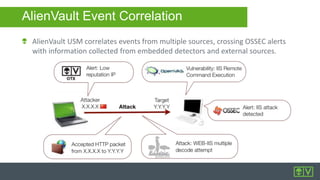
AlienVault provides mid-sized businesses with unified security products, intelligence, and community resources for modern threat defense. The document details AlienVault's capabilities, including OSSEC features like log analysis and vulnerability assessment, along with an overview of the USM architecture and integrated tools. It also offers insights into event correlation and management through a comprehensive GUI for effective security monitoring.