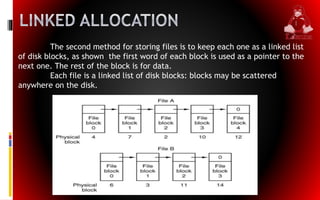
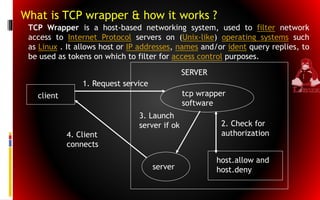
This document discusses file system implementation and Linux security. It begins by describing how file systems are typically stored on disks with partitions and sectors. It then explains how files are created, opened, read, written to, and deleted in a file system. Two common allocation methods are also summarized - contiguous allocation and linked allocation. Finally, it outlines some common security threats like intruders, malicious programs, and generic attacks and how TCP wrappers can be used to filter network access on Linux servers.