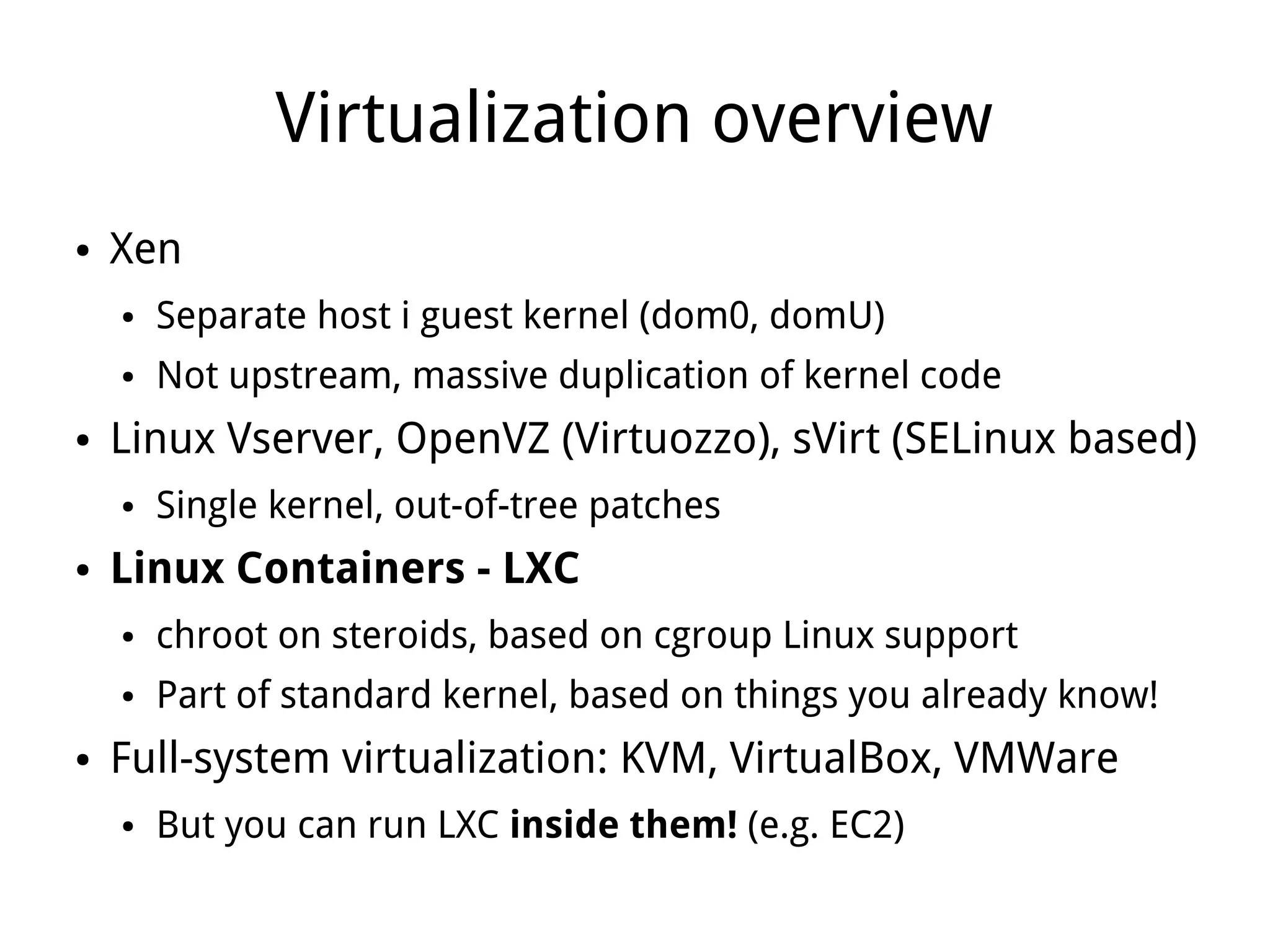
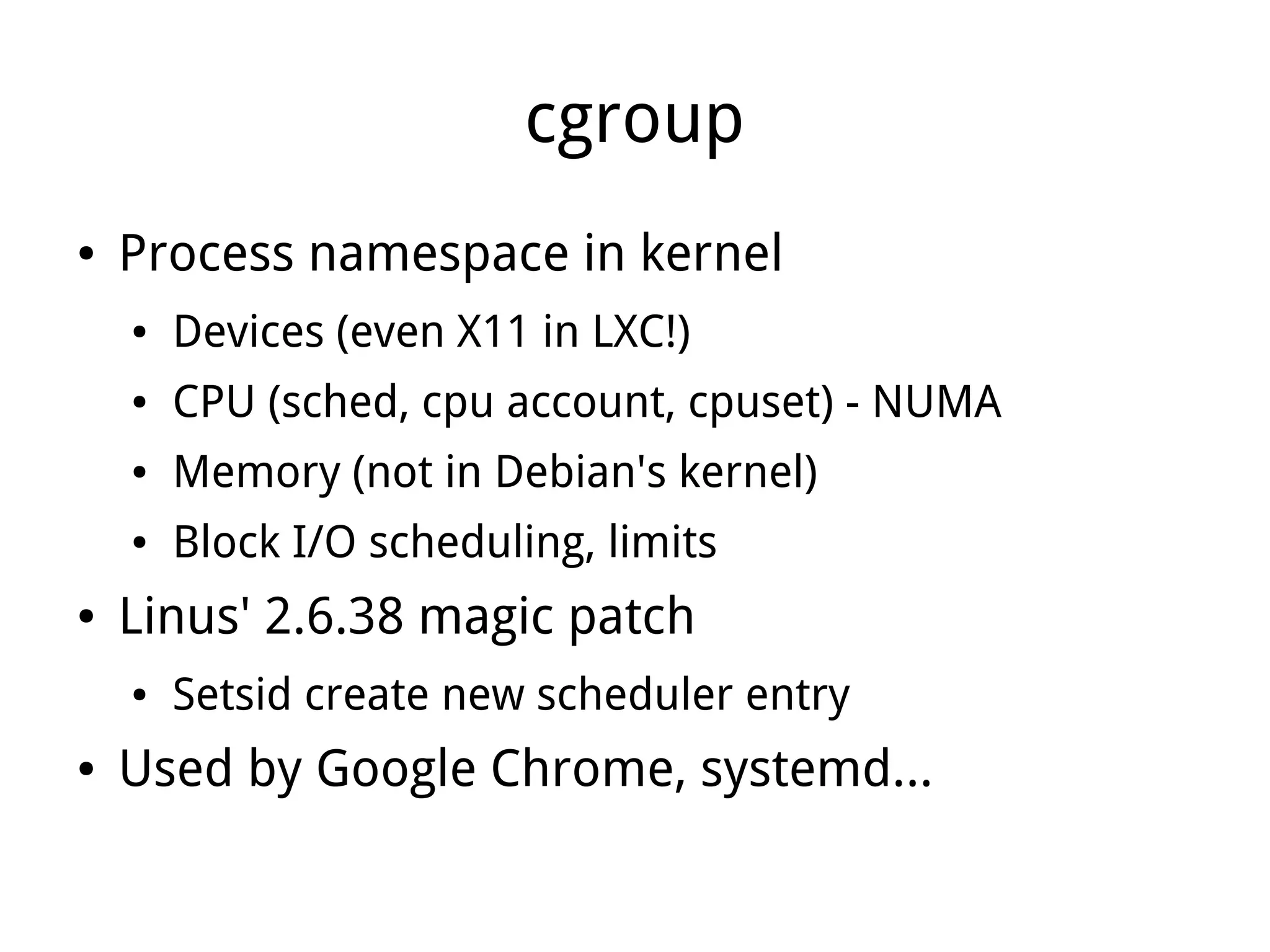
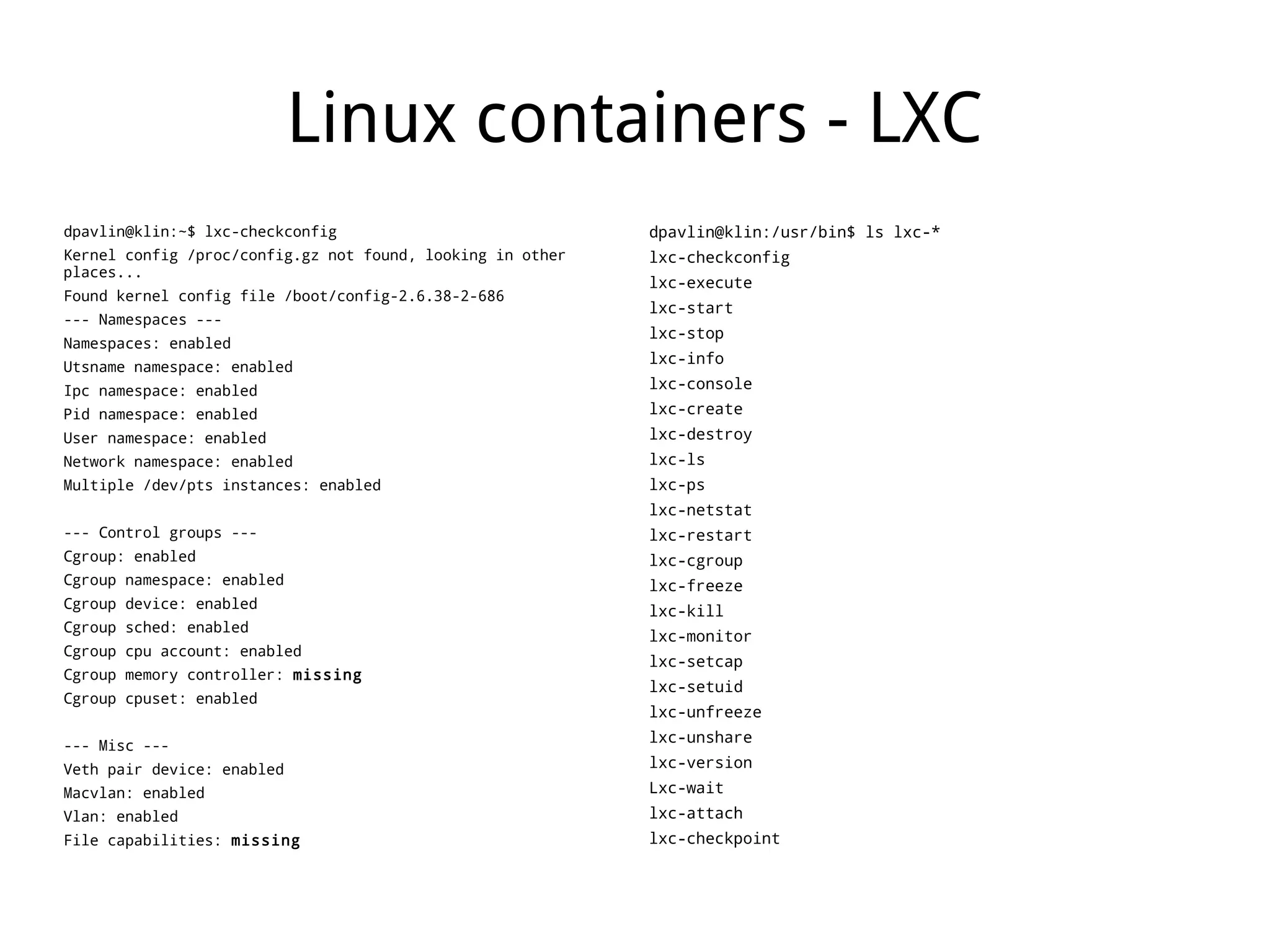
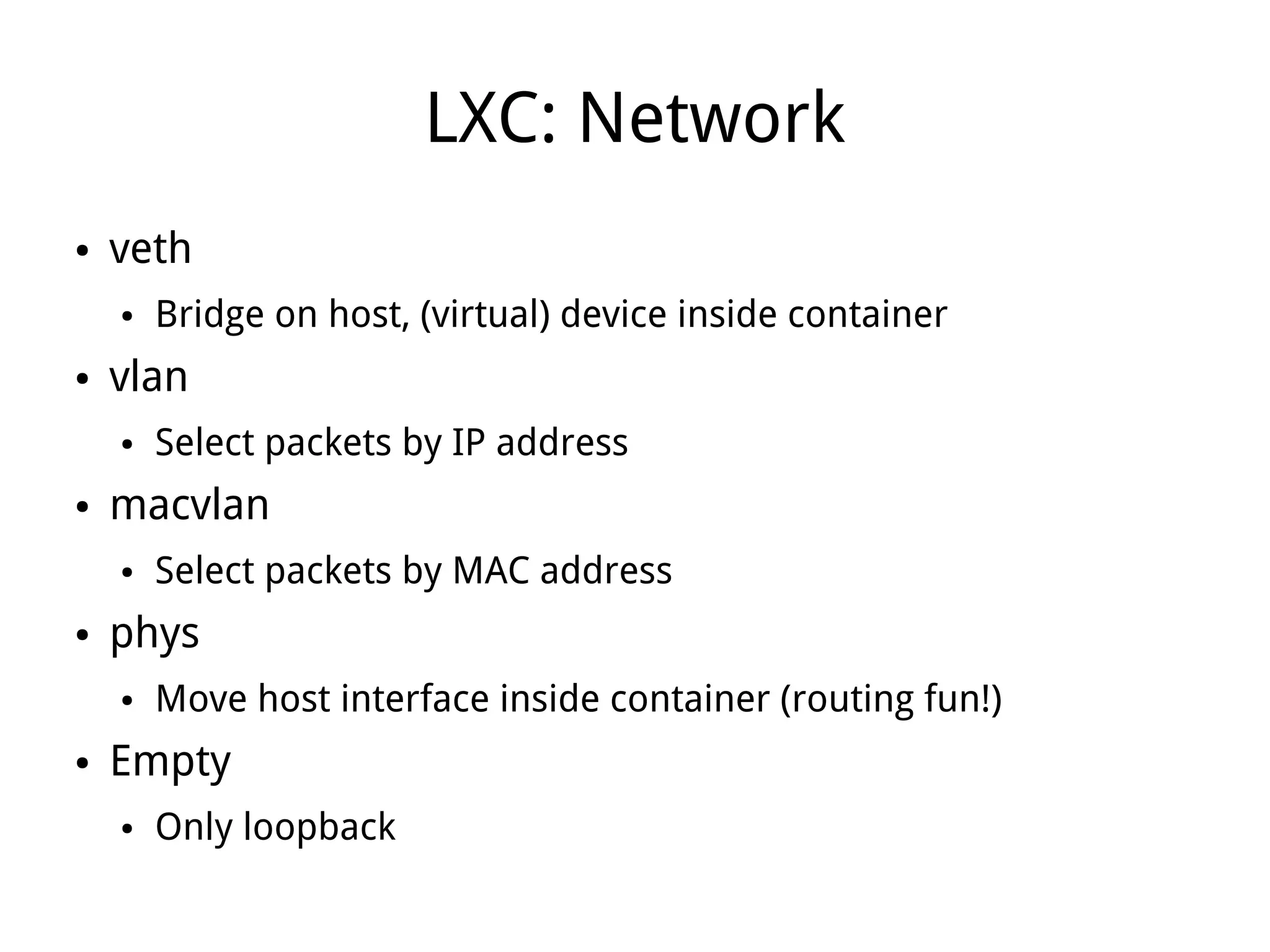
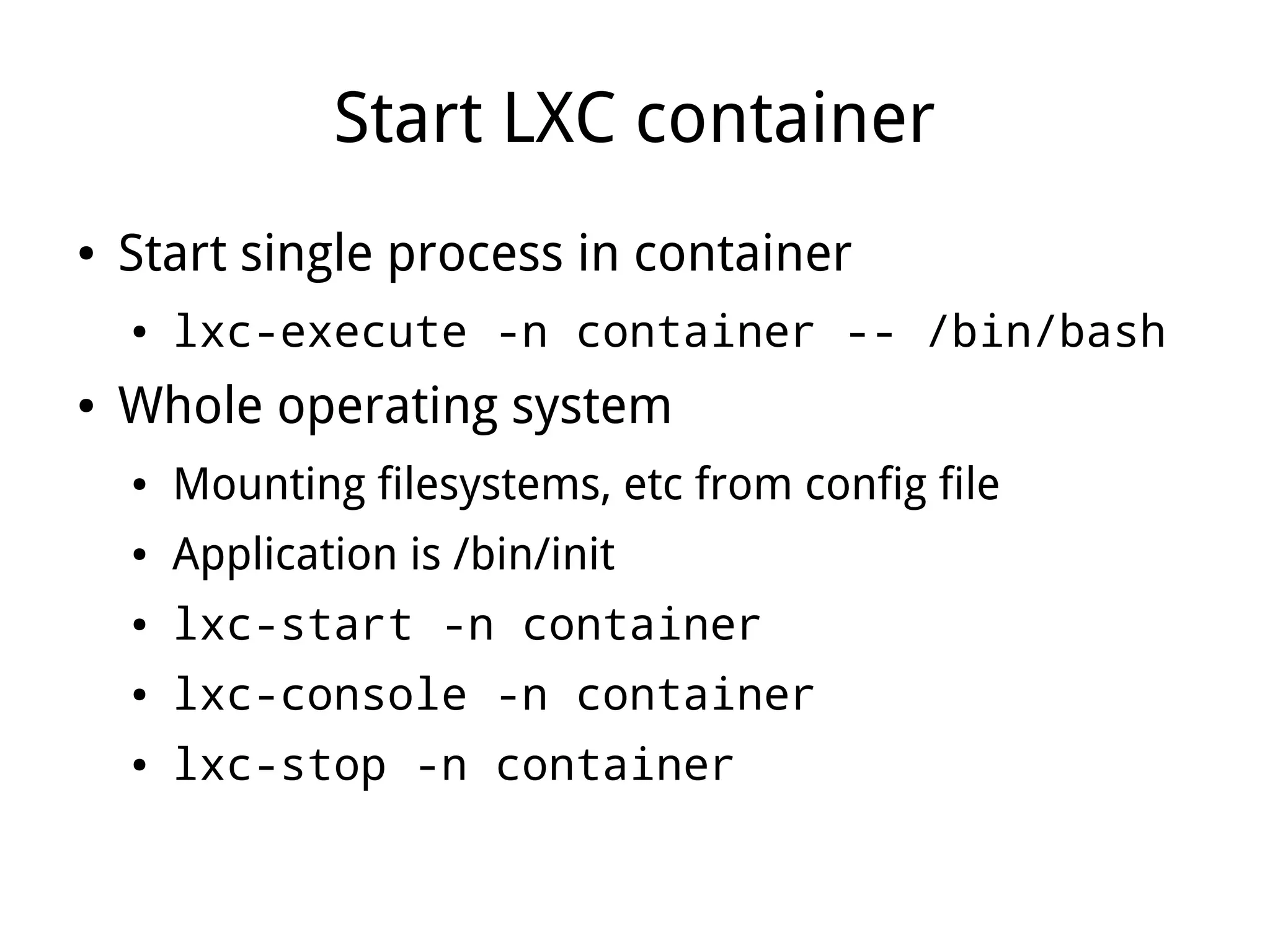
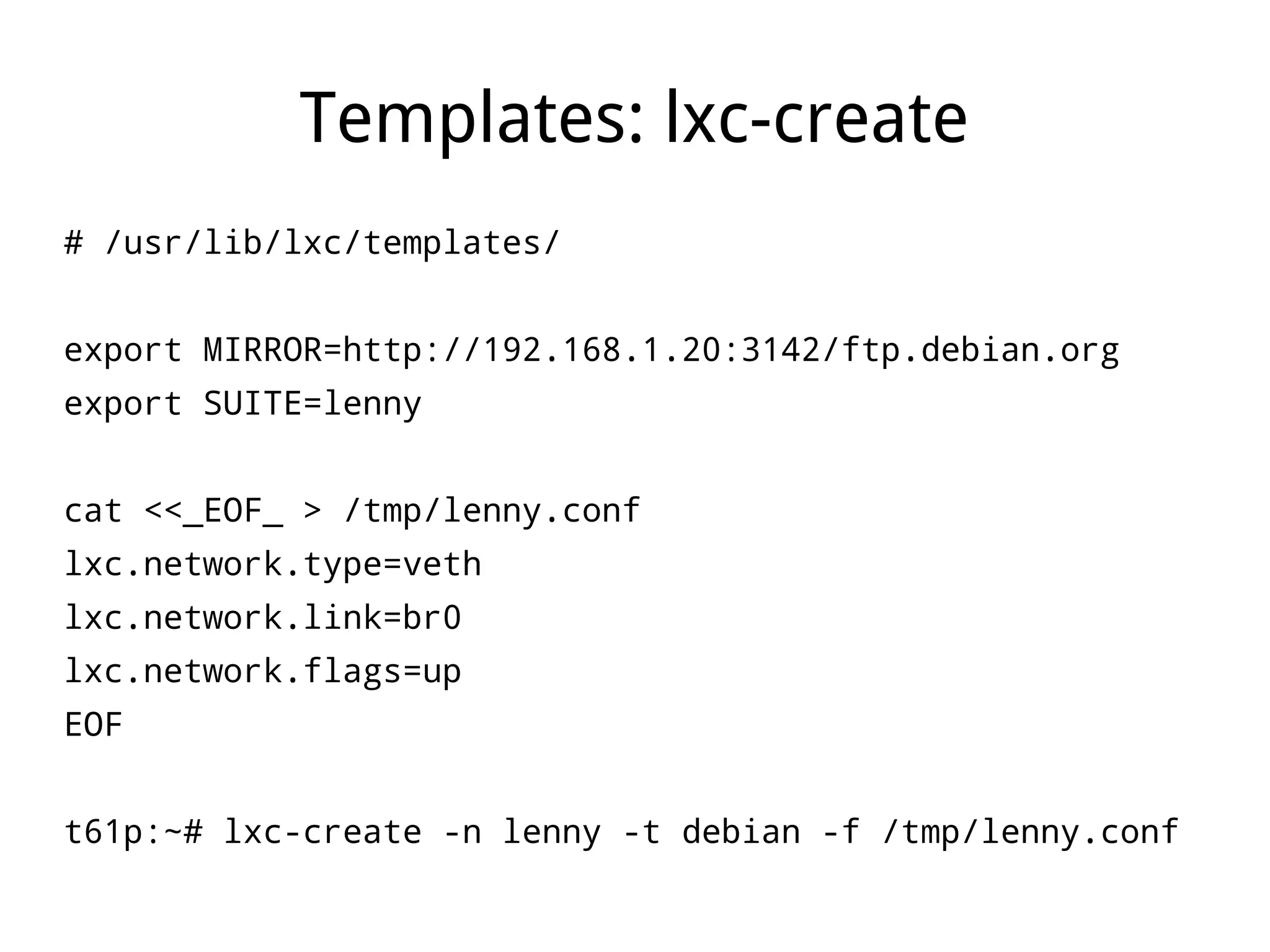
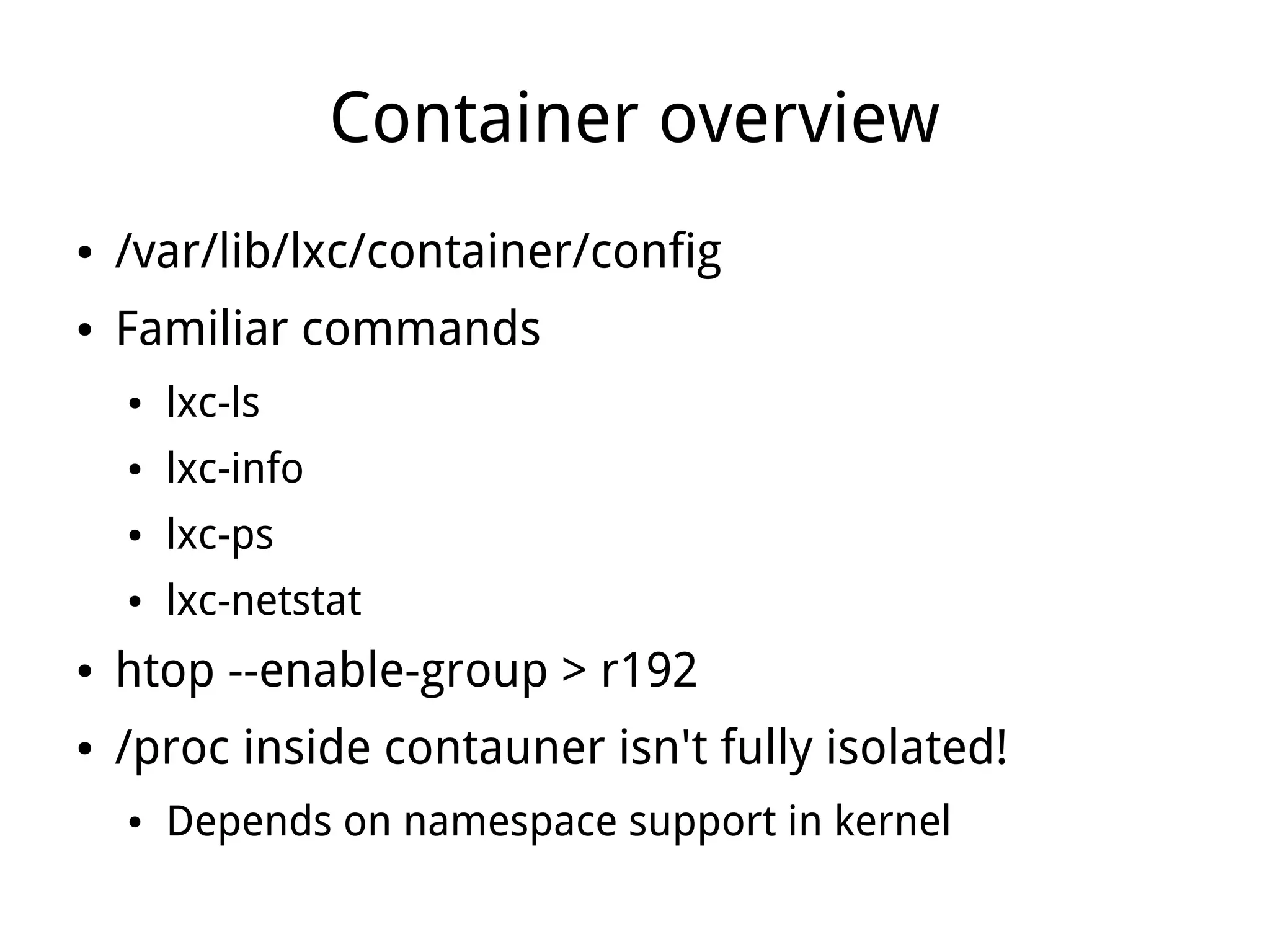
LXC (Linux Containers) provides operating-system-level virtualization without the overhead of full virtualization. It isolates processes into containers using kernel namespaces and control groups. Containers can be limited in their CPU, memory, storage, and network usage. Common commands like lxc-start are used to deploy whole operating systems within containers. LXC provides many of the benefits of virtualization with less overhead since it leverages existing Linux kernel features rather than requiring a separate kernel like traditional virtualization.