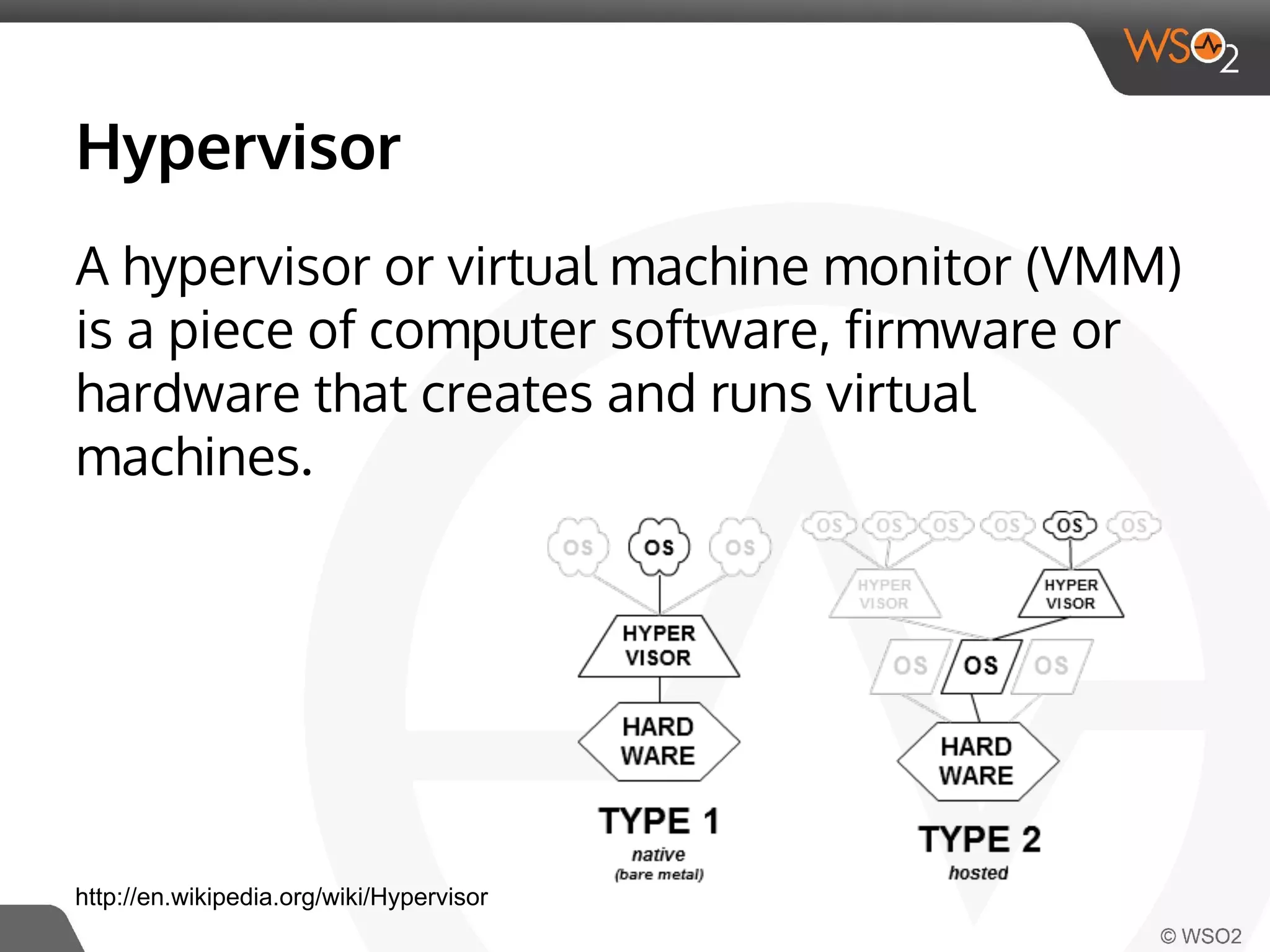
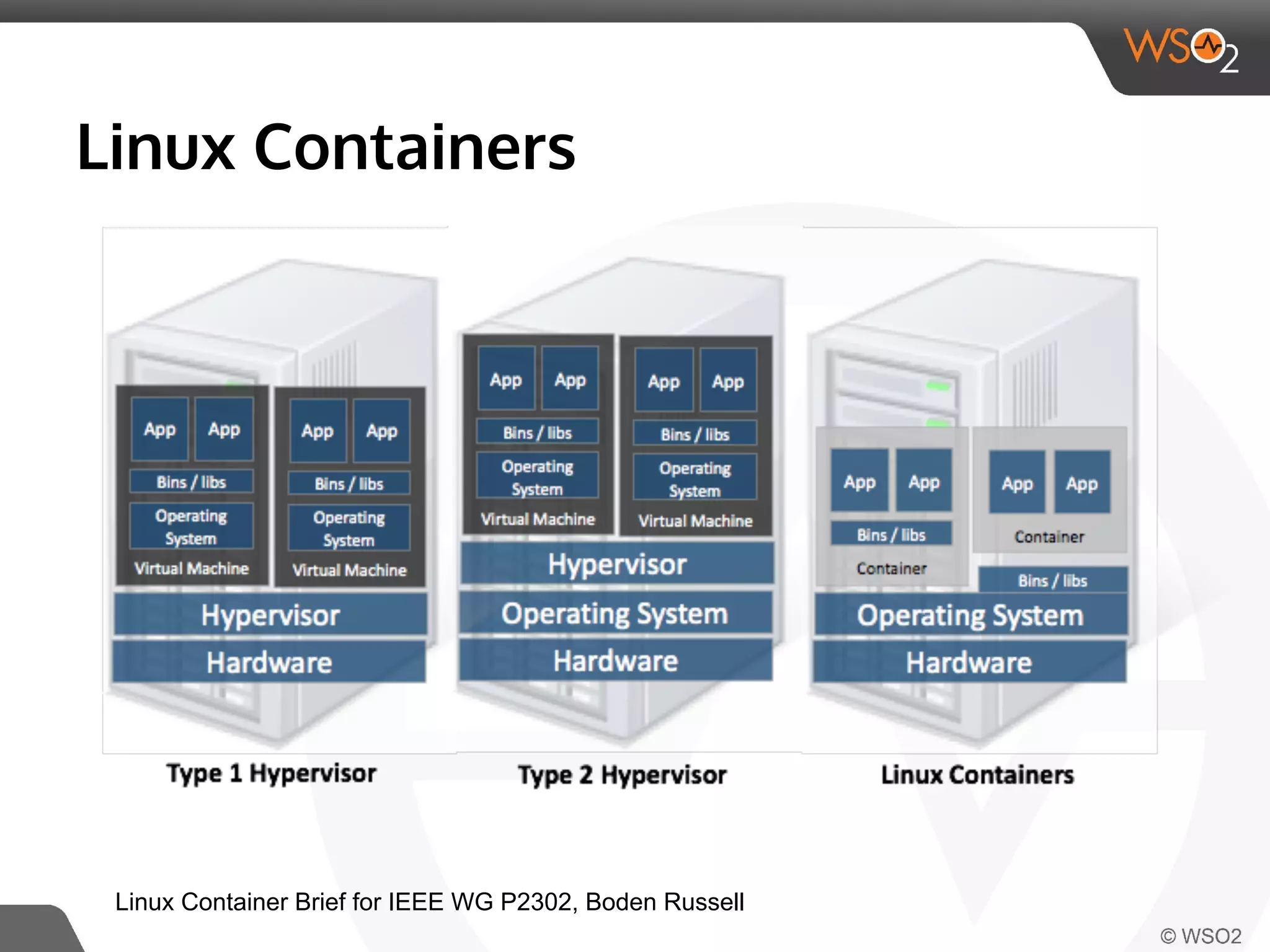
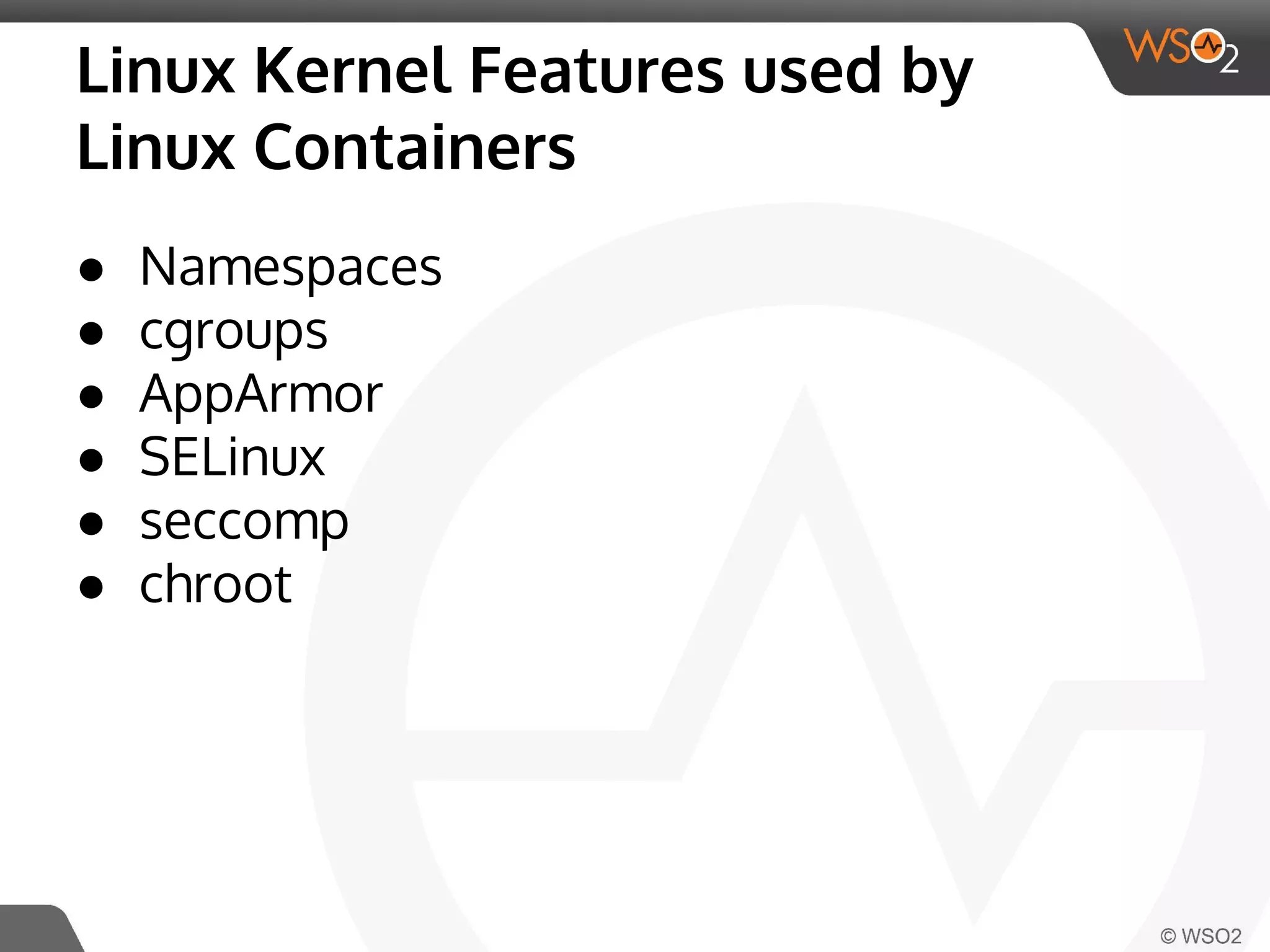
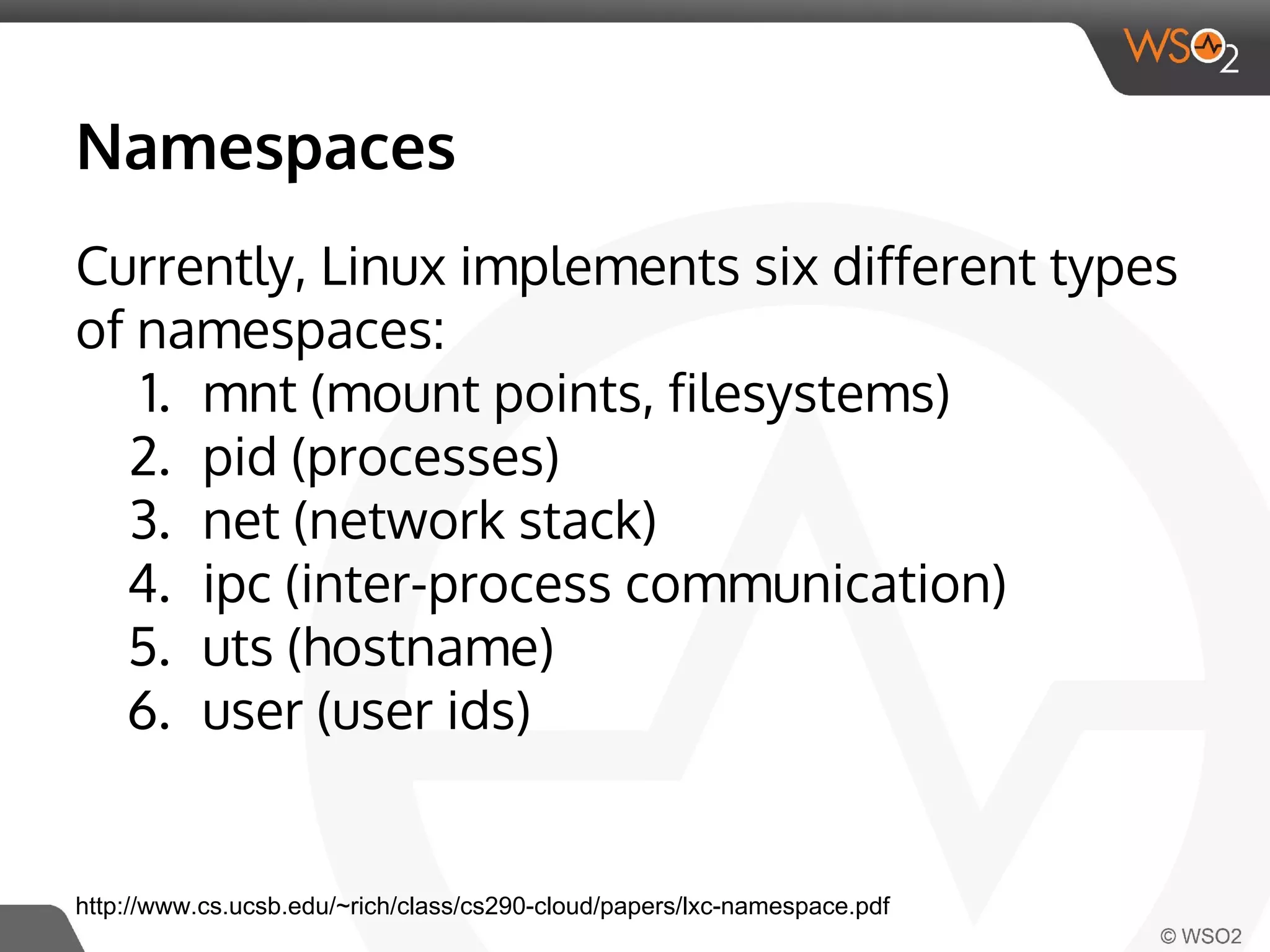
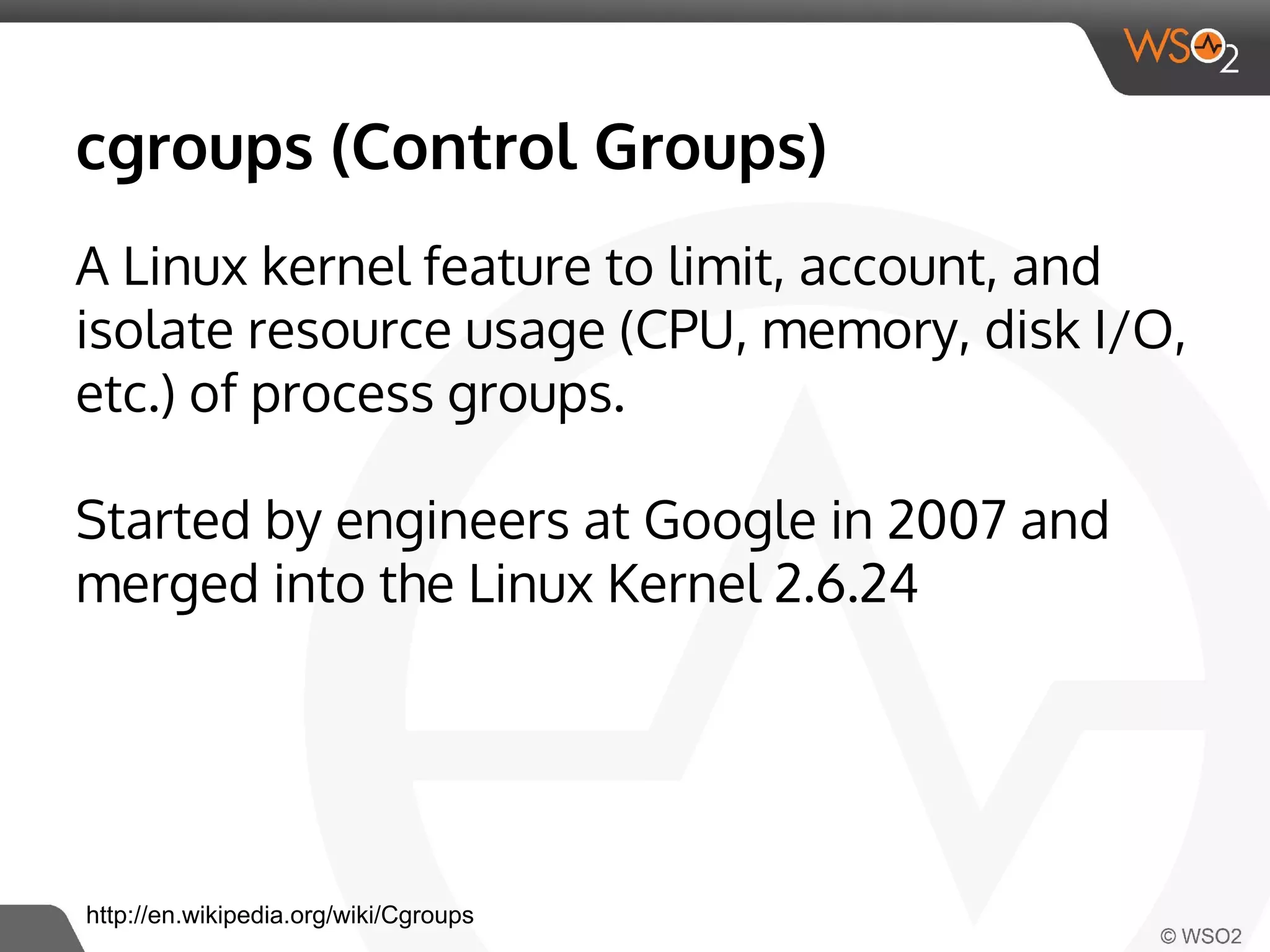
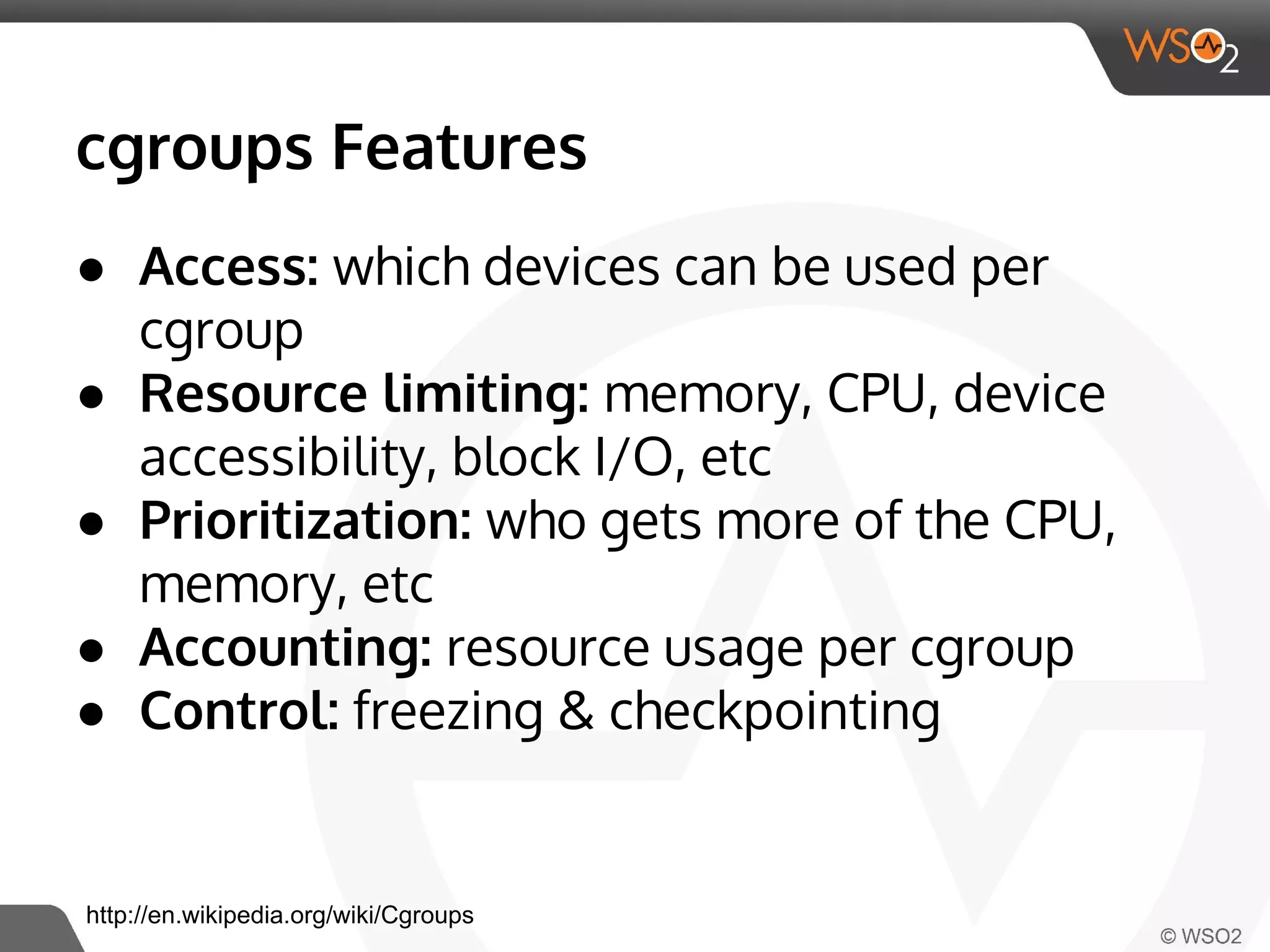
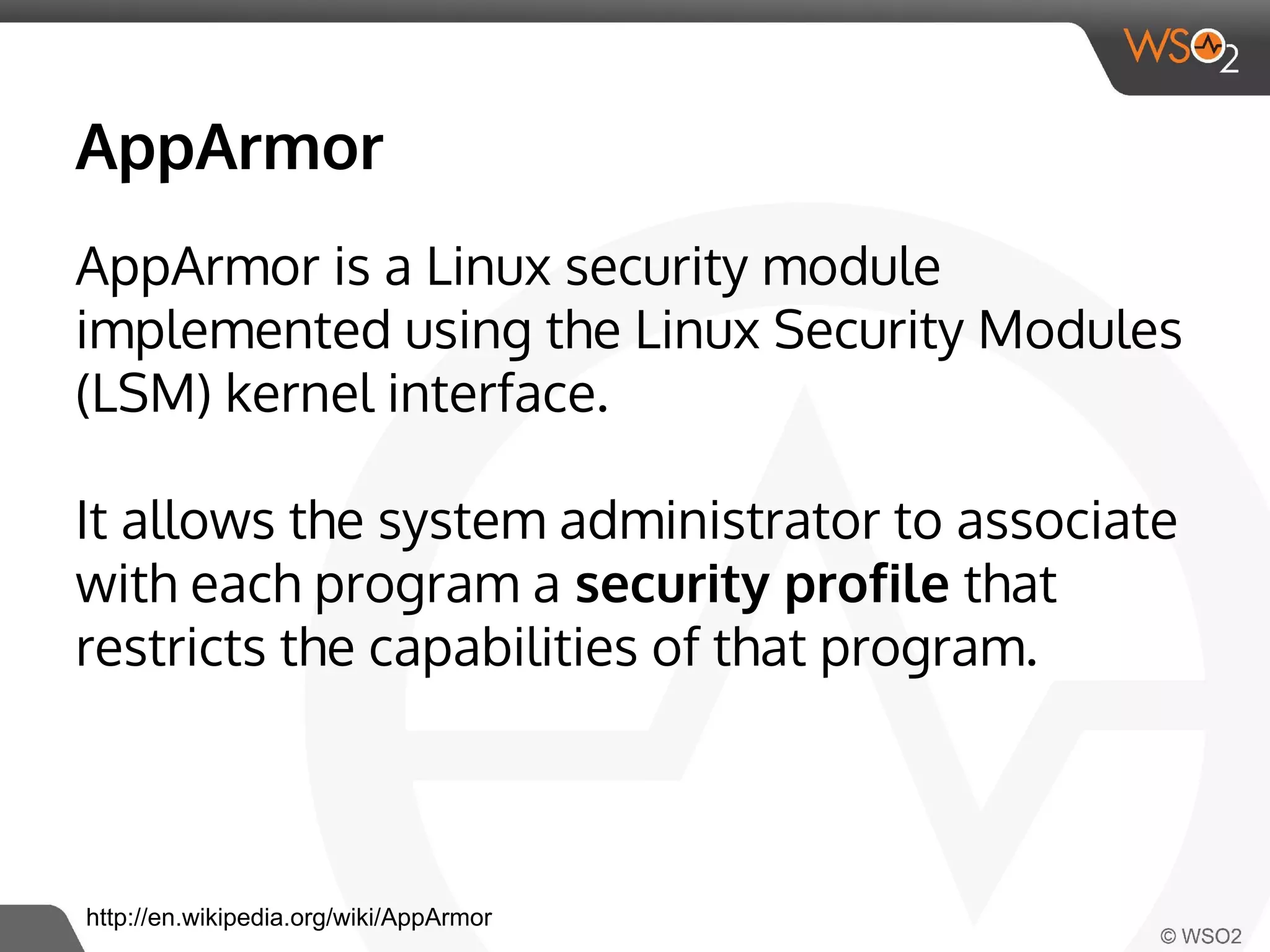
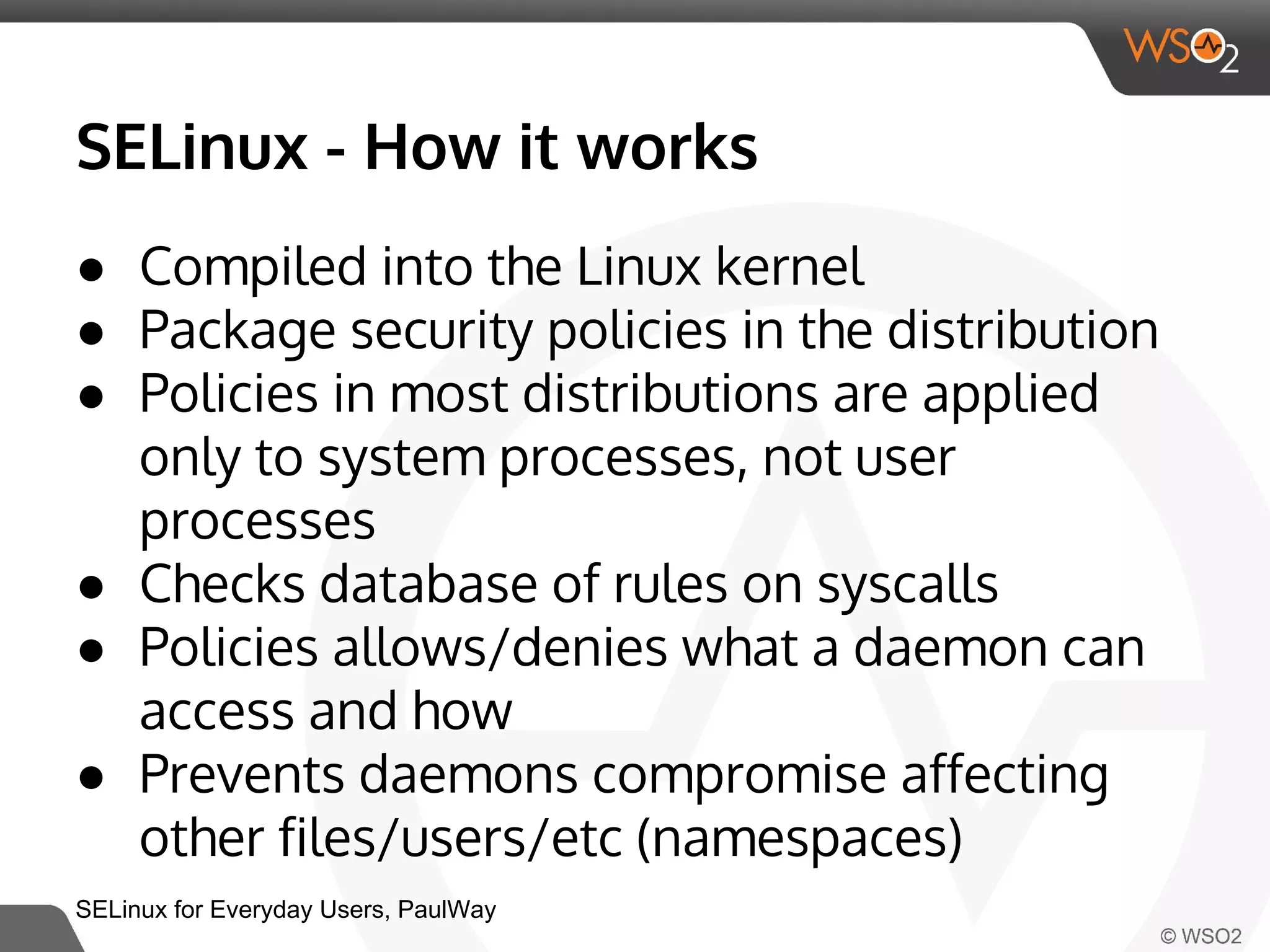
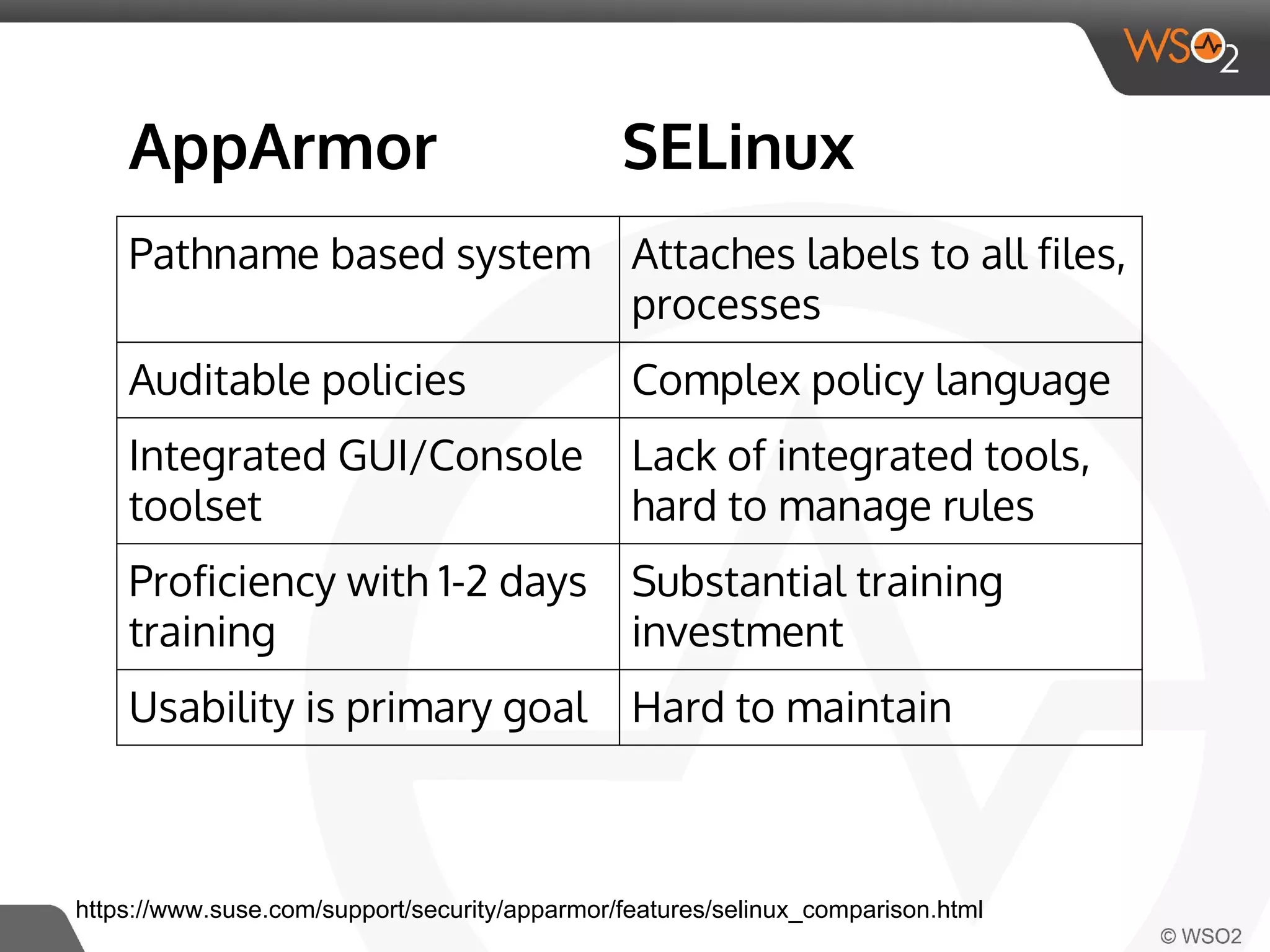
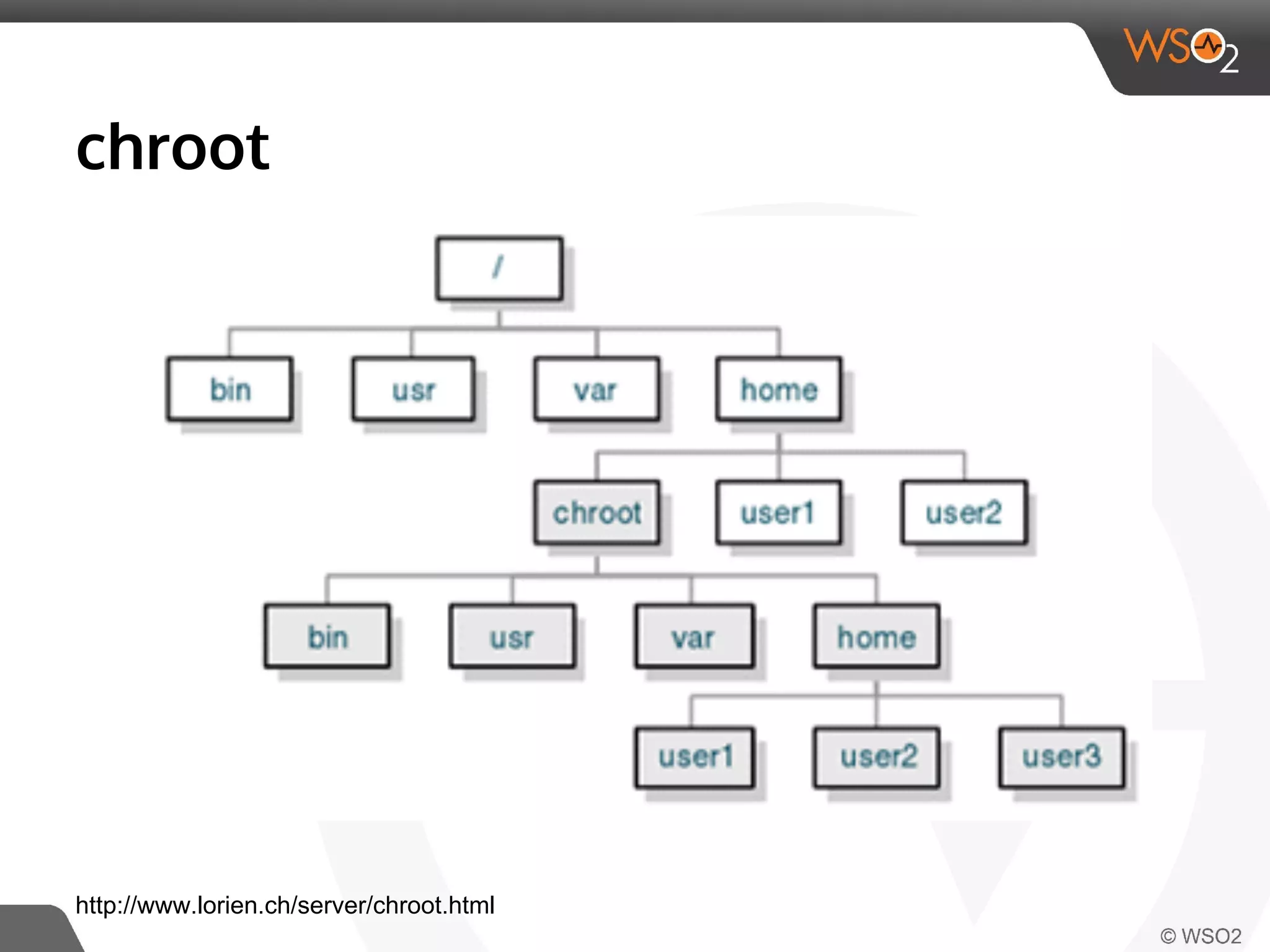
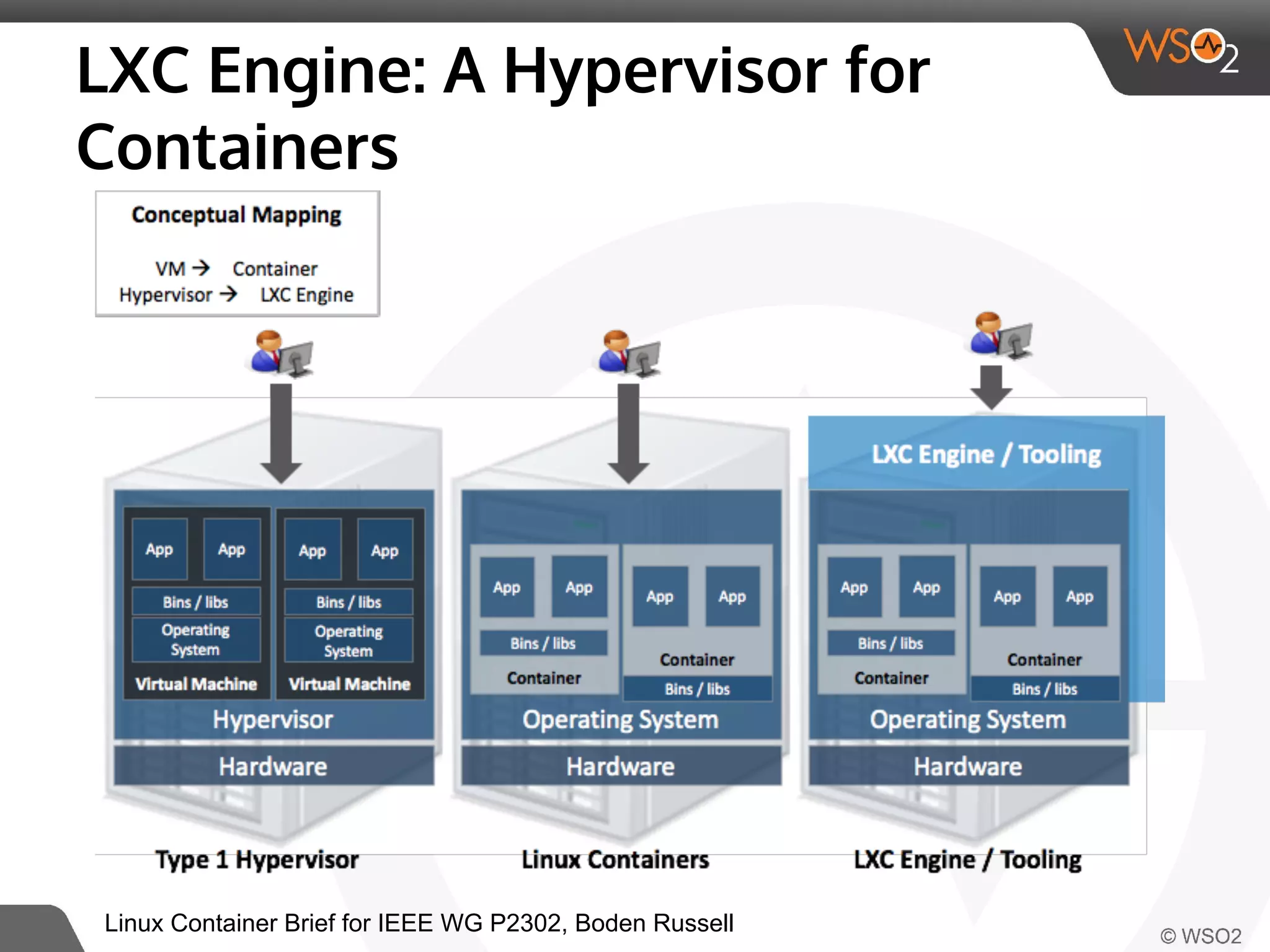
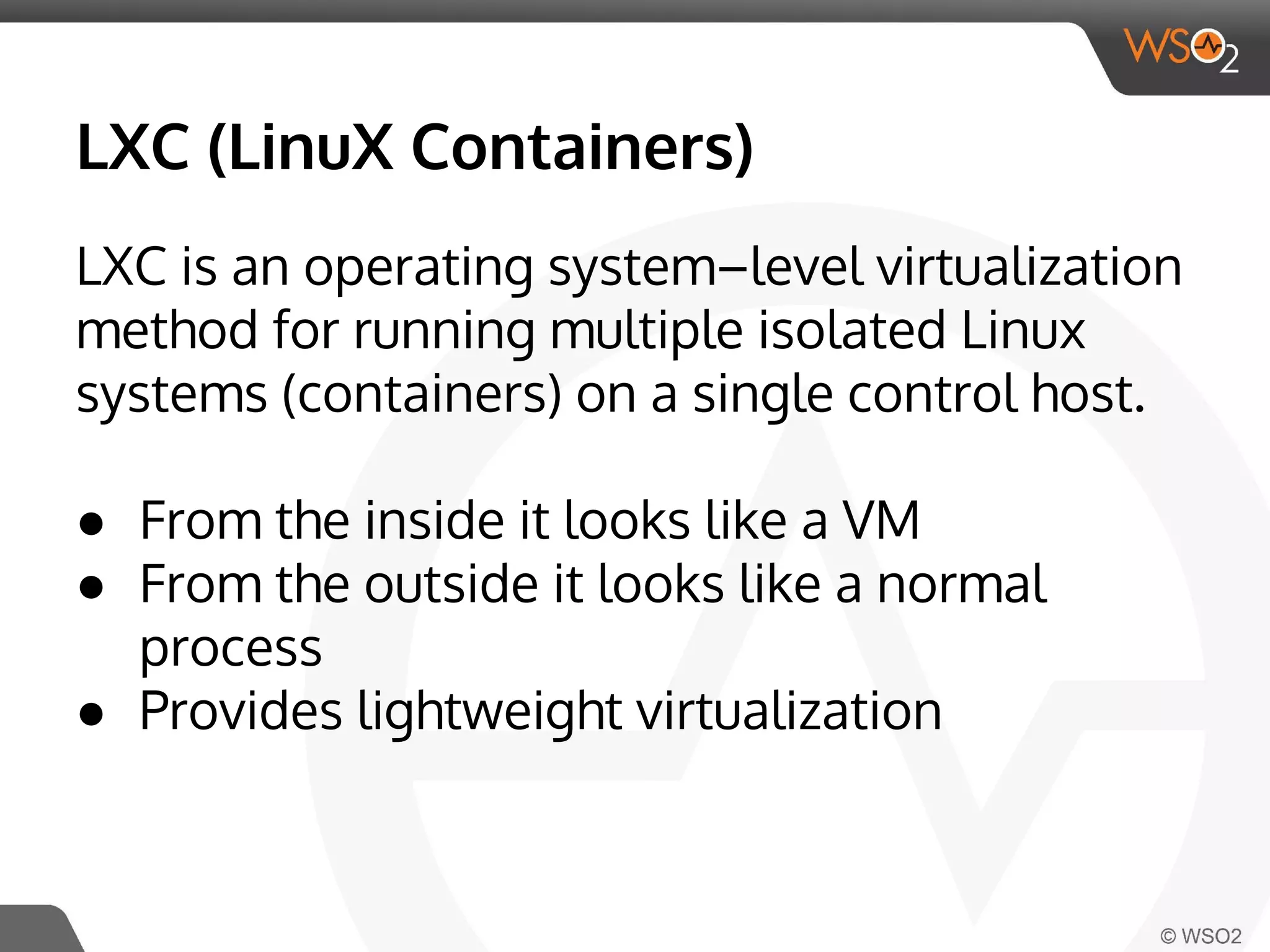
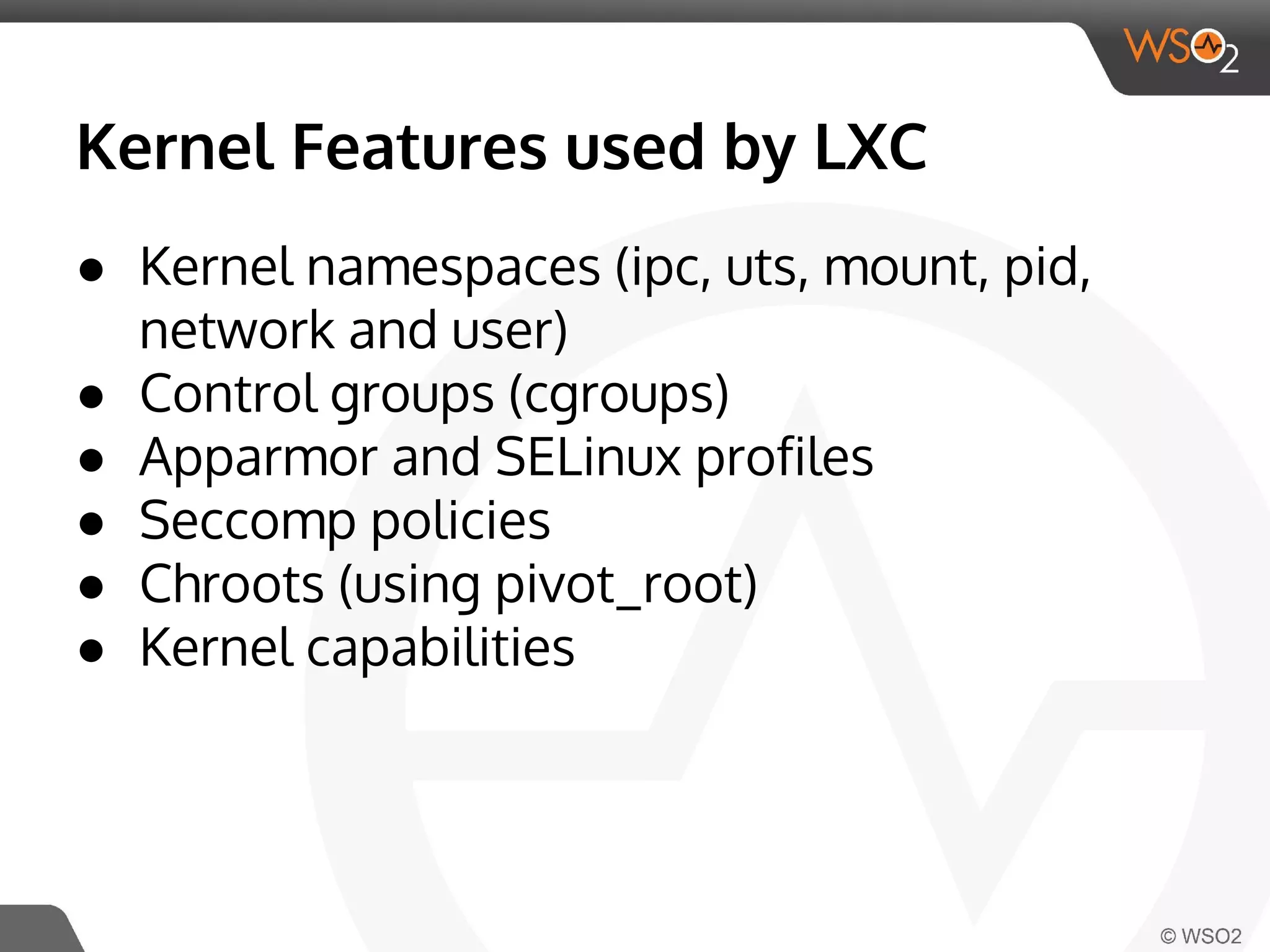
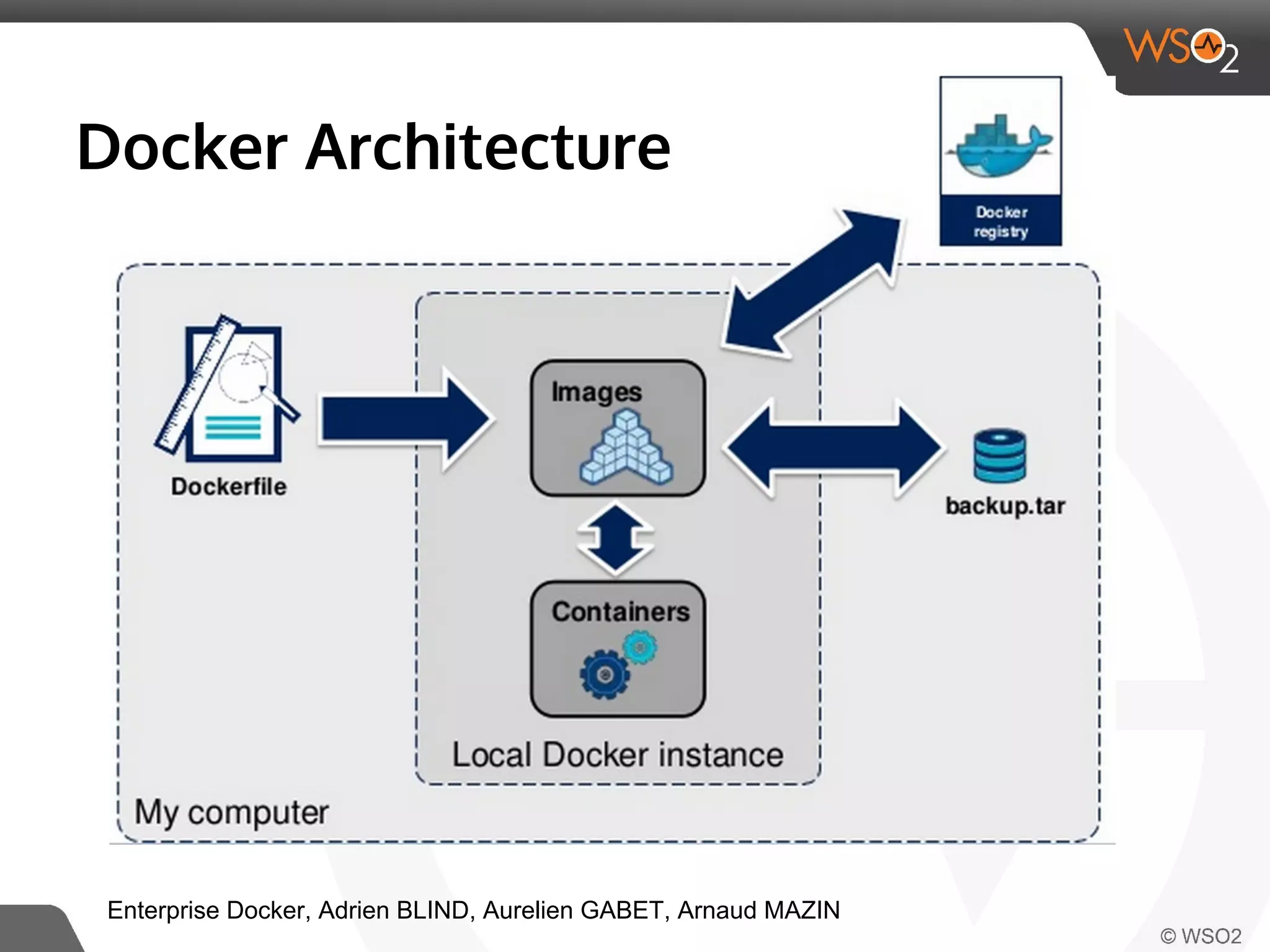
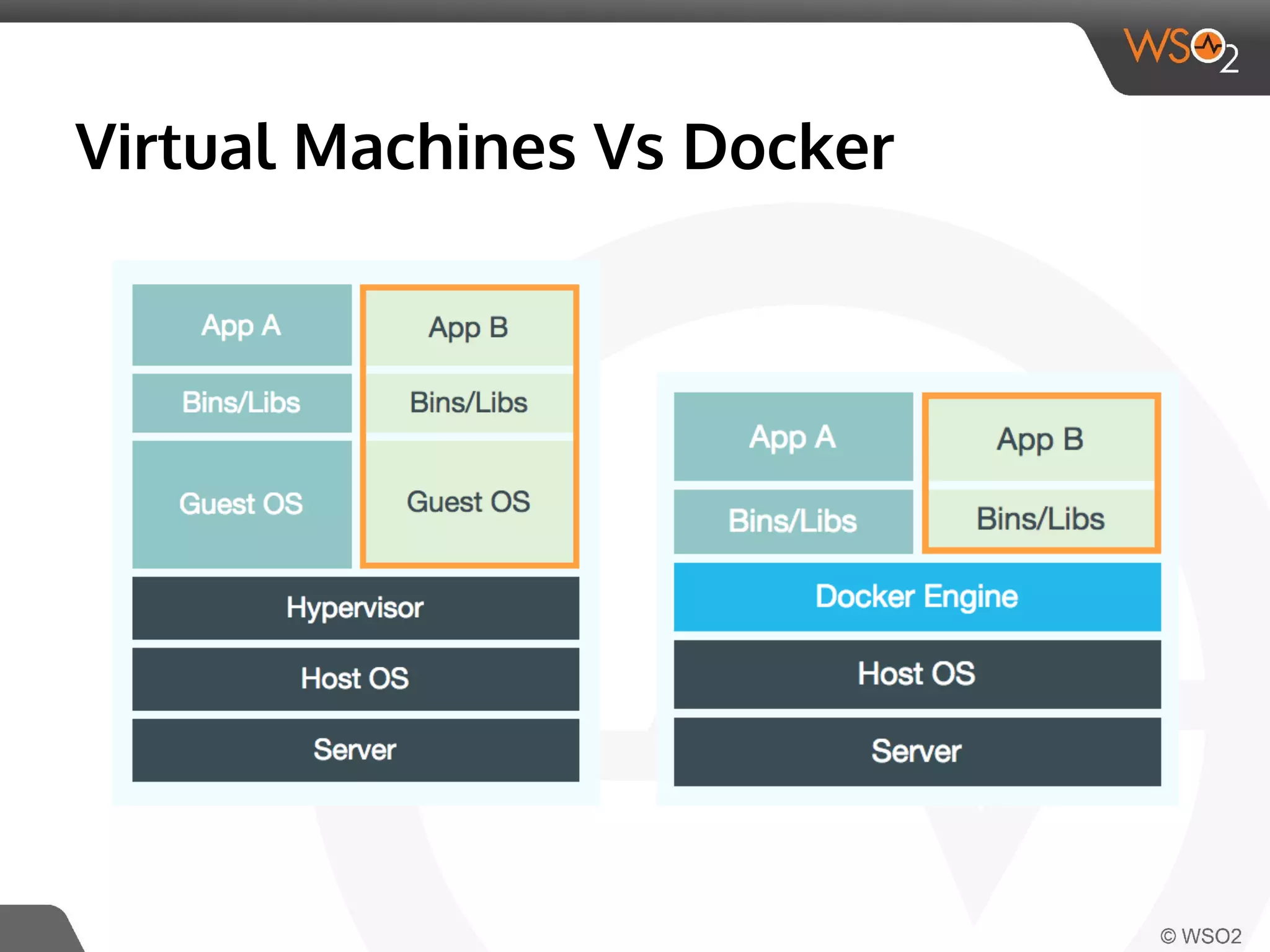
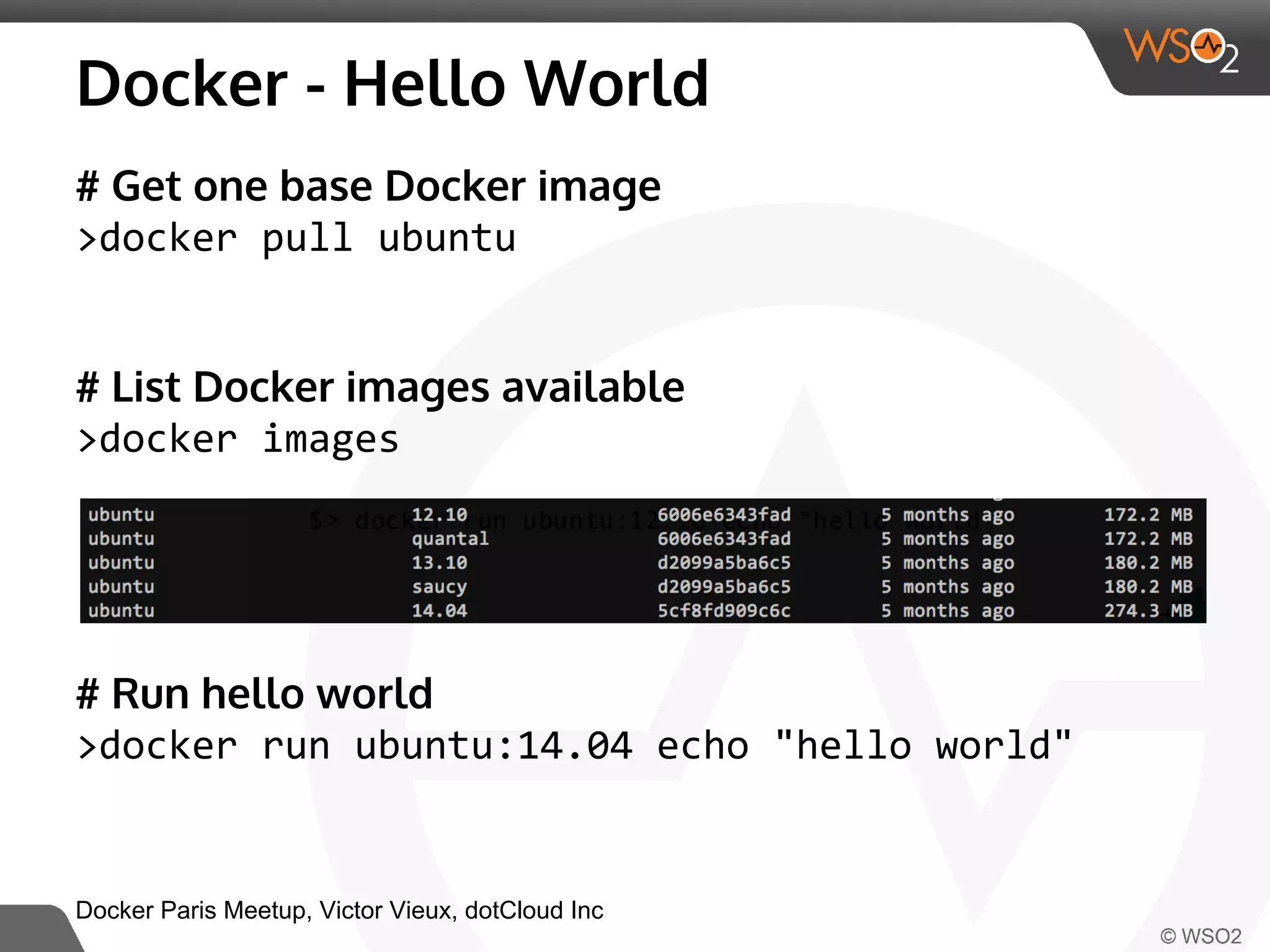
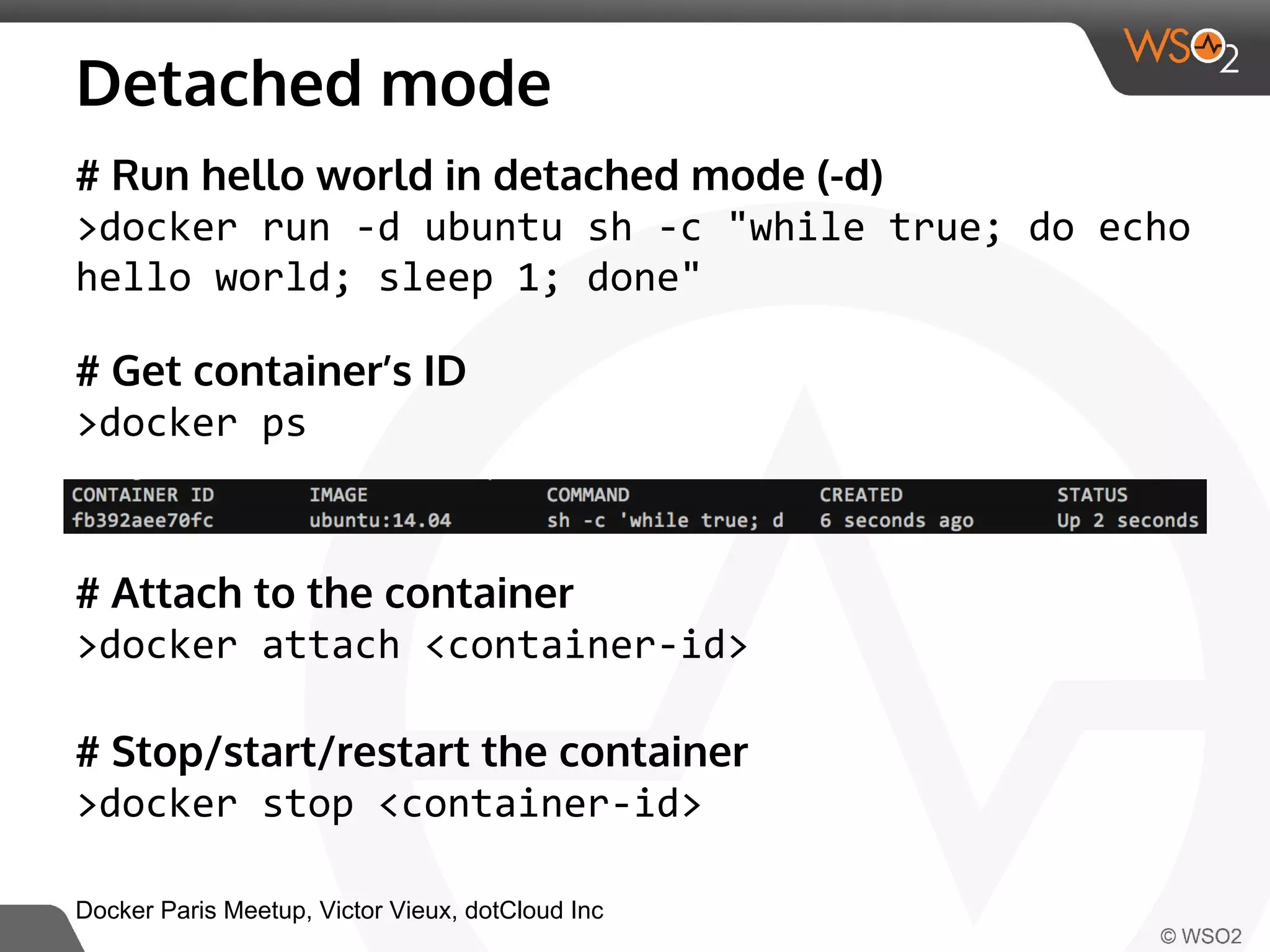
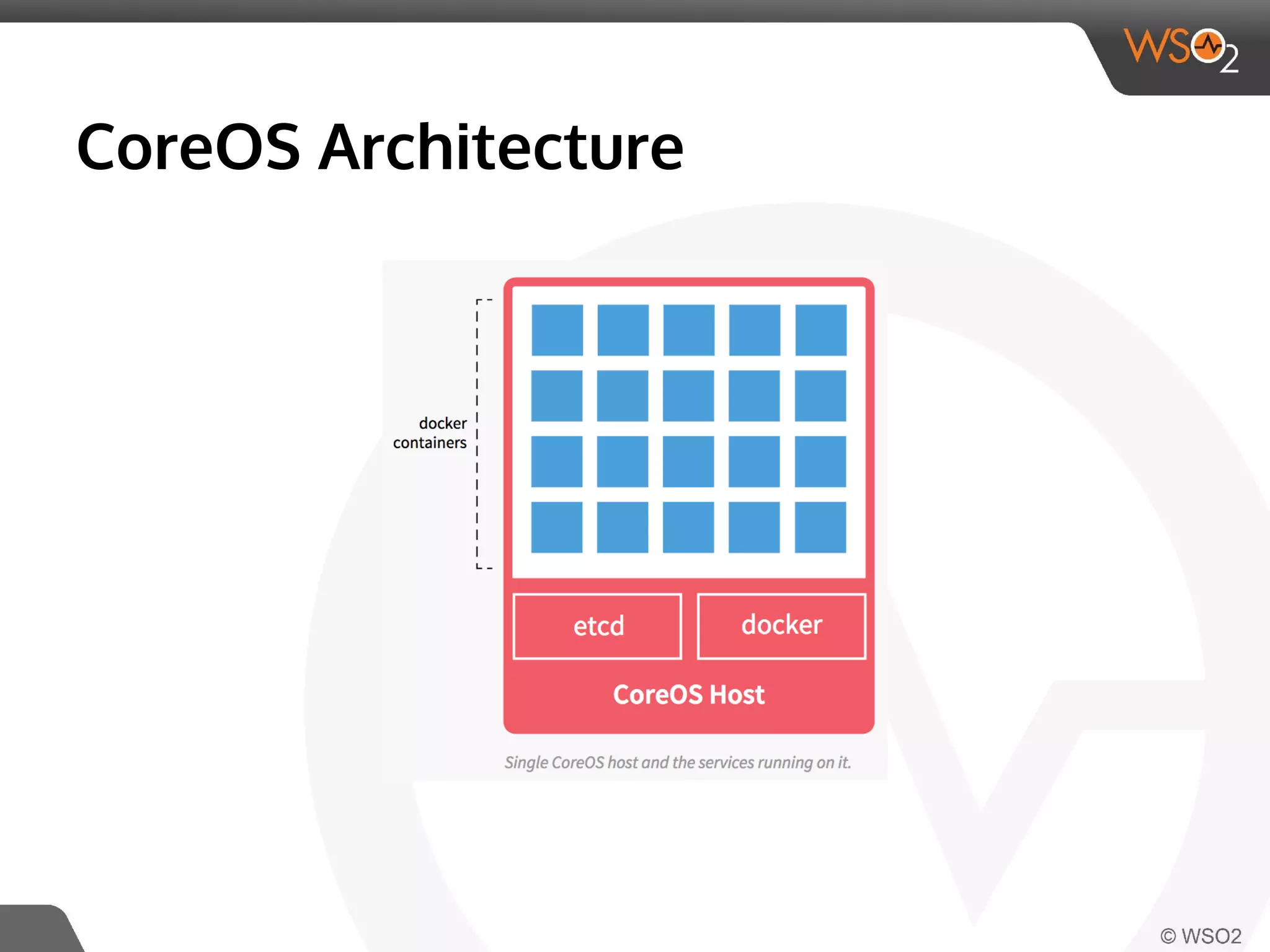
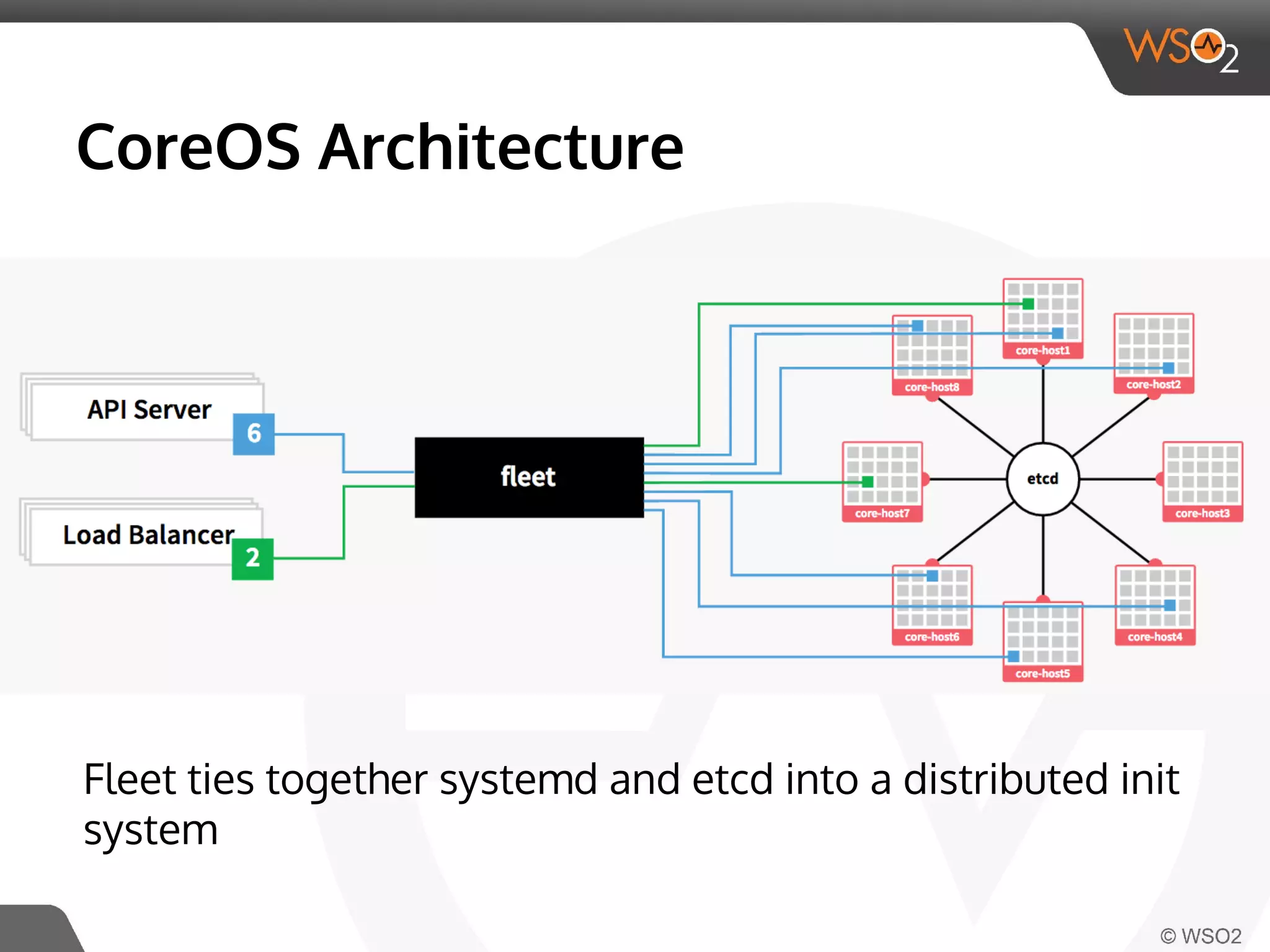
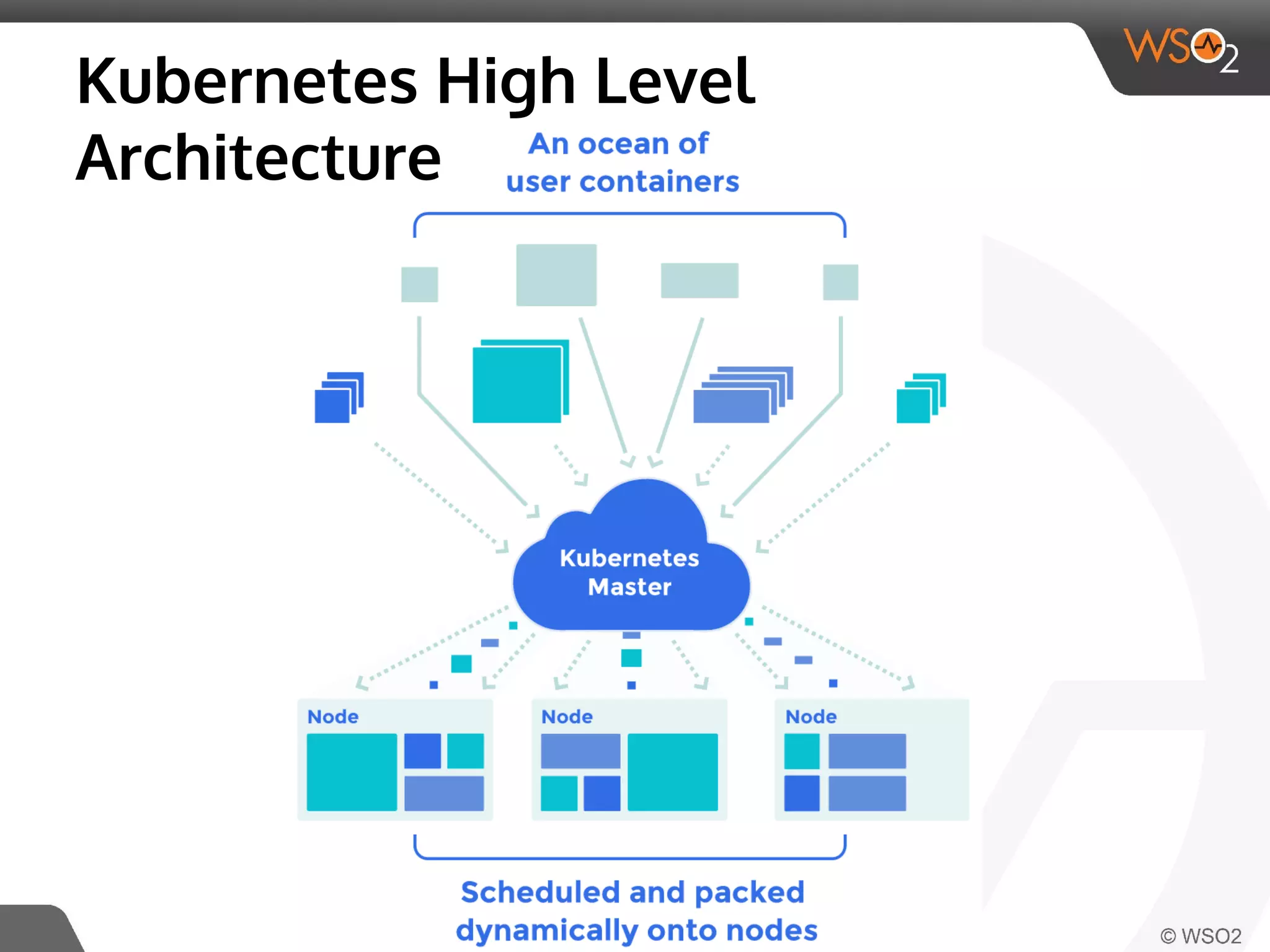
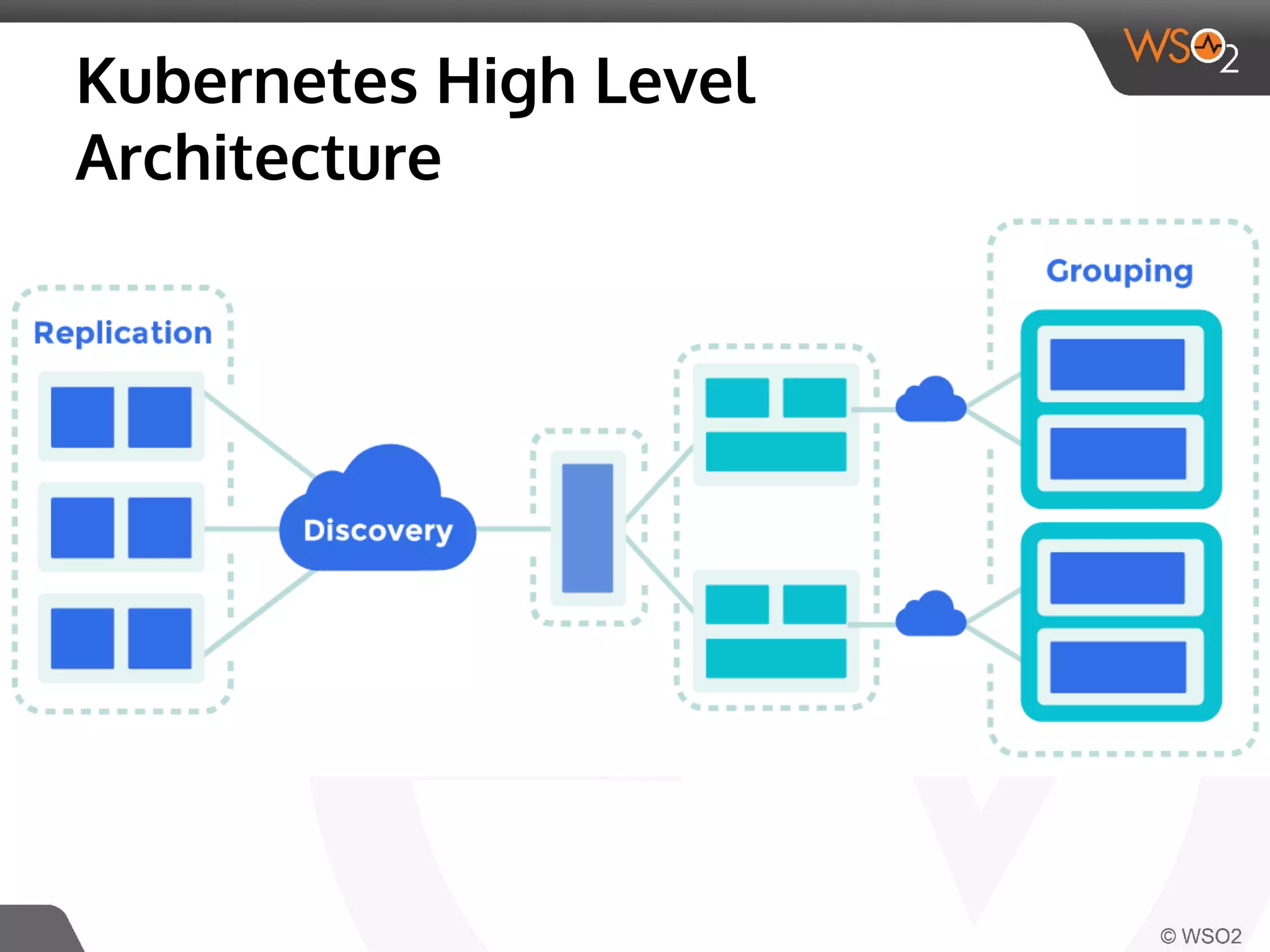
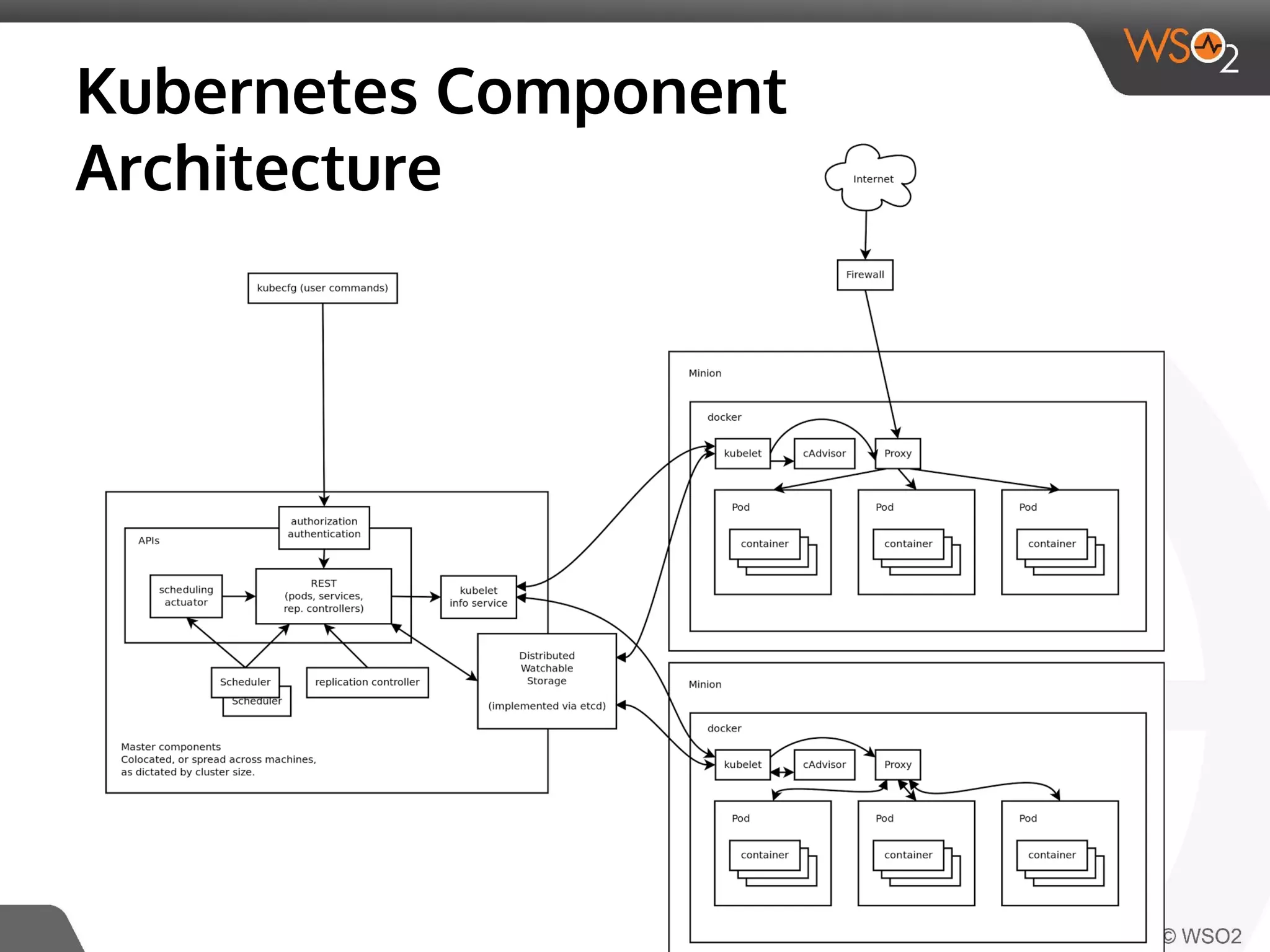
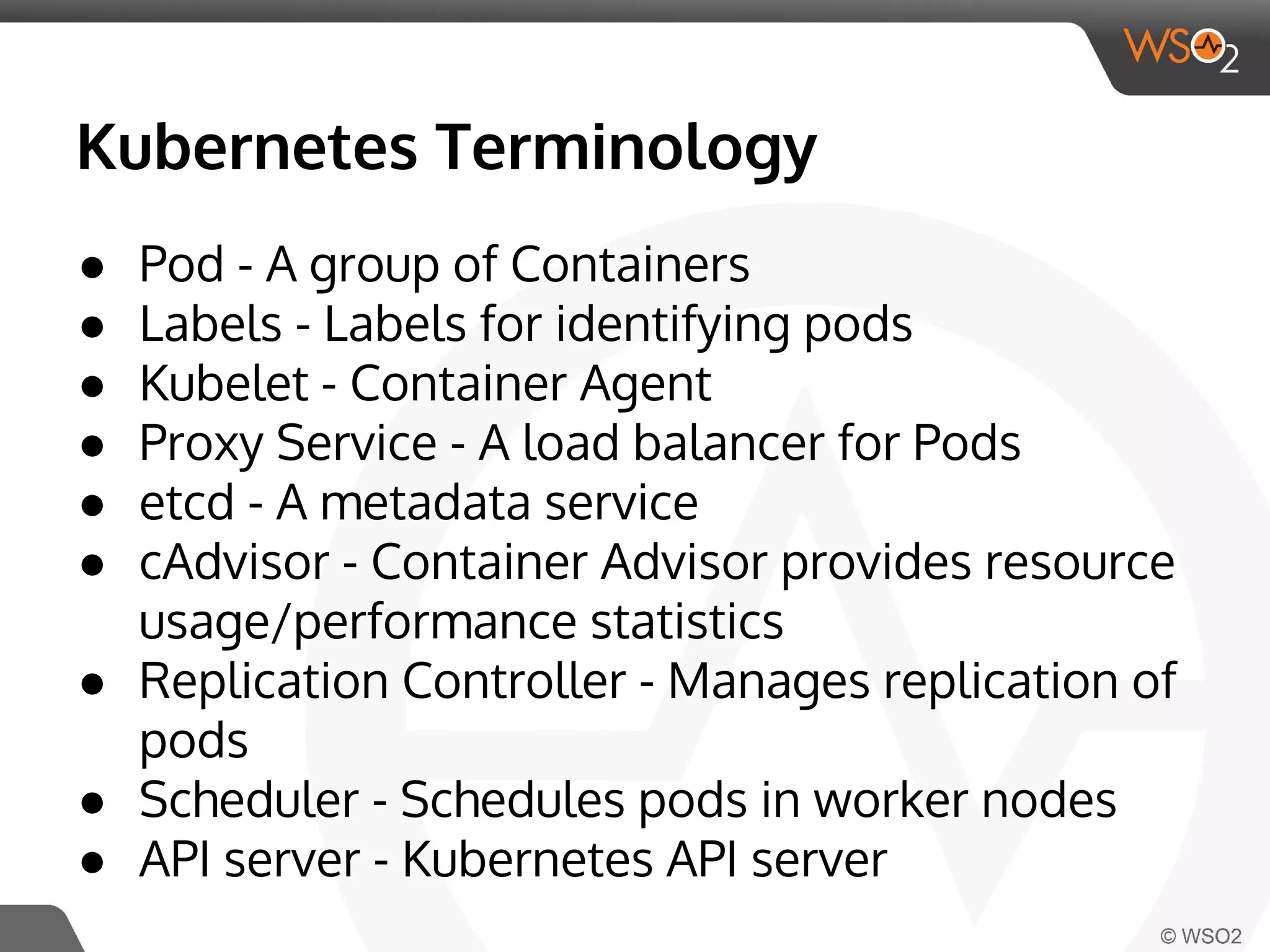
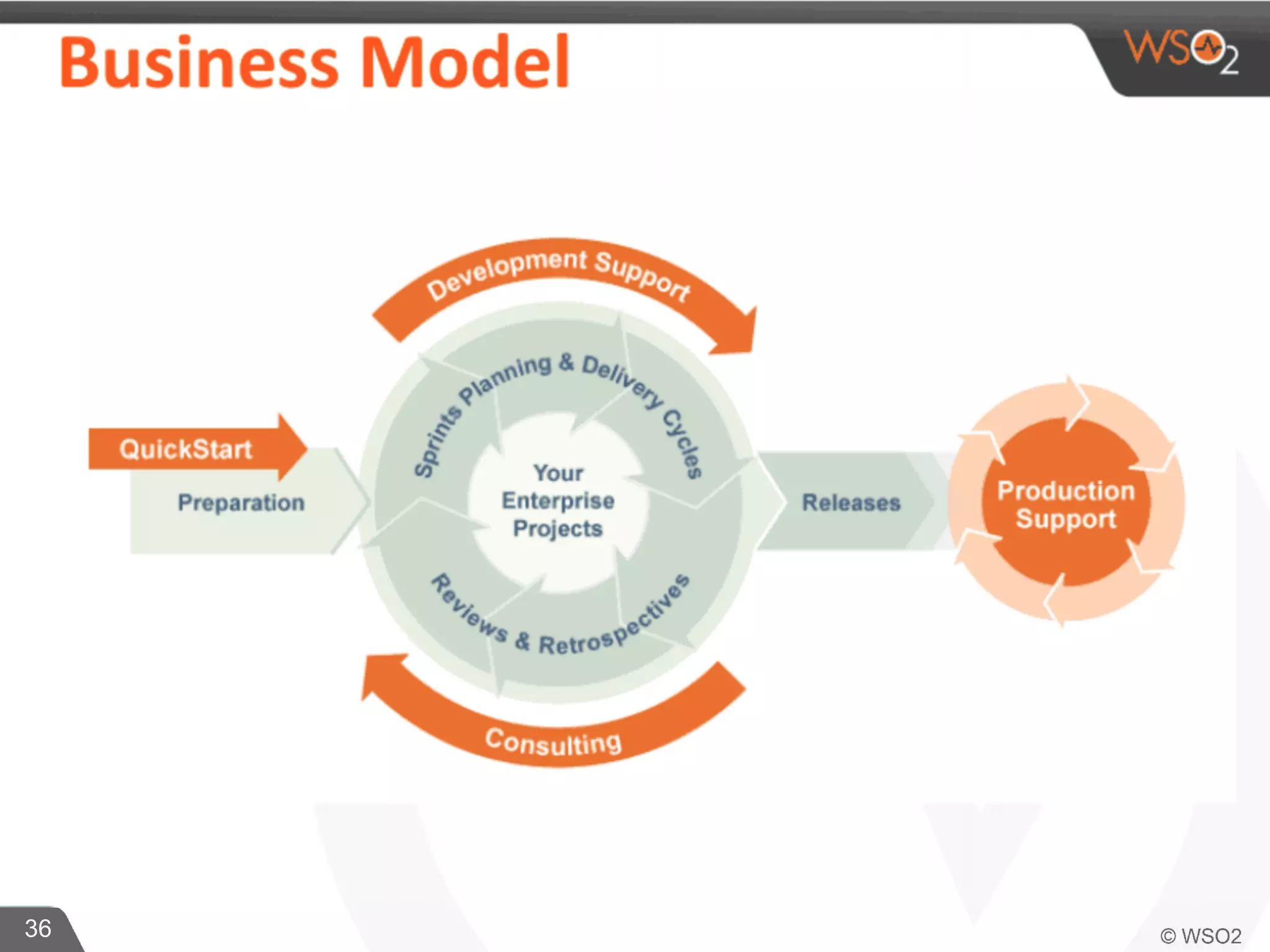
This document discusses container virtualization and key related technologies. It begins with an overview of virtualization and the hypervisor model. It then covers Linux containers and the kernel features they use like namespaces, cgroups, AppArmor, and SELinux. Popular container tools like LXC, Docker, CoreOS, and Kubernetes are introduced. The document argues that containers make it possible to run multiple isolated environments on one host more efficiently than virtual machines, improving cloud deployment.