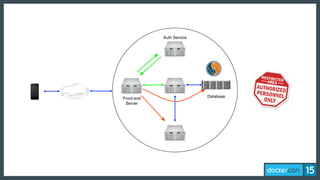
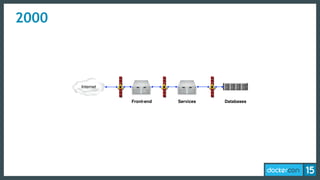
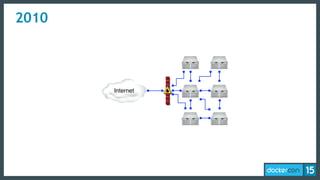
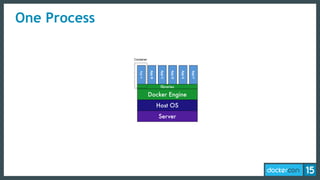
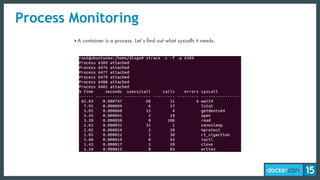
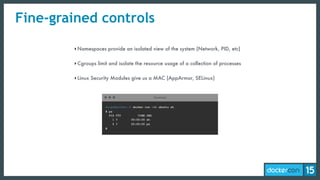
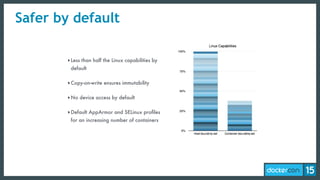
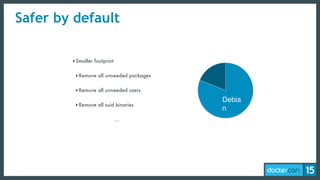
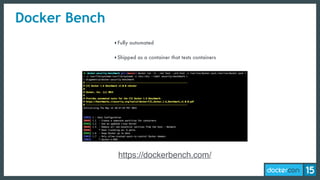
The document discusses the concept of least-privilege in microservices, emphasizing the need for processes to access only necessary resources for their tasks. It outlines the evolution of container security with Docker, focusing on mechanisms such as namespaces, cgroups, and security modules to enforce fine-grained control. The document concludes that while Docker is progressing towards supporting least-privilege microservices, more user-friendly tools for defining security profiles are still required.