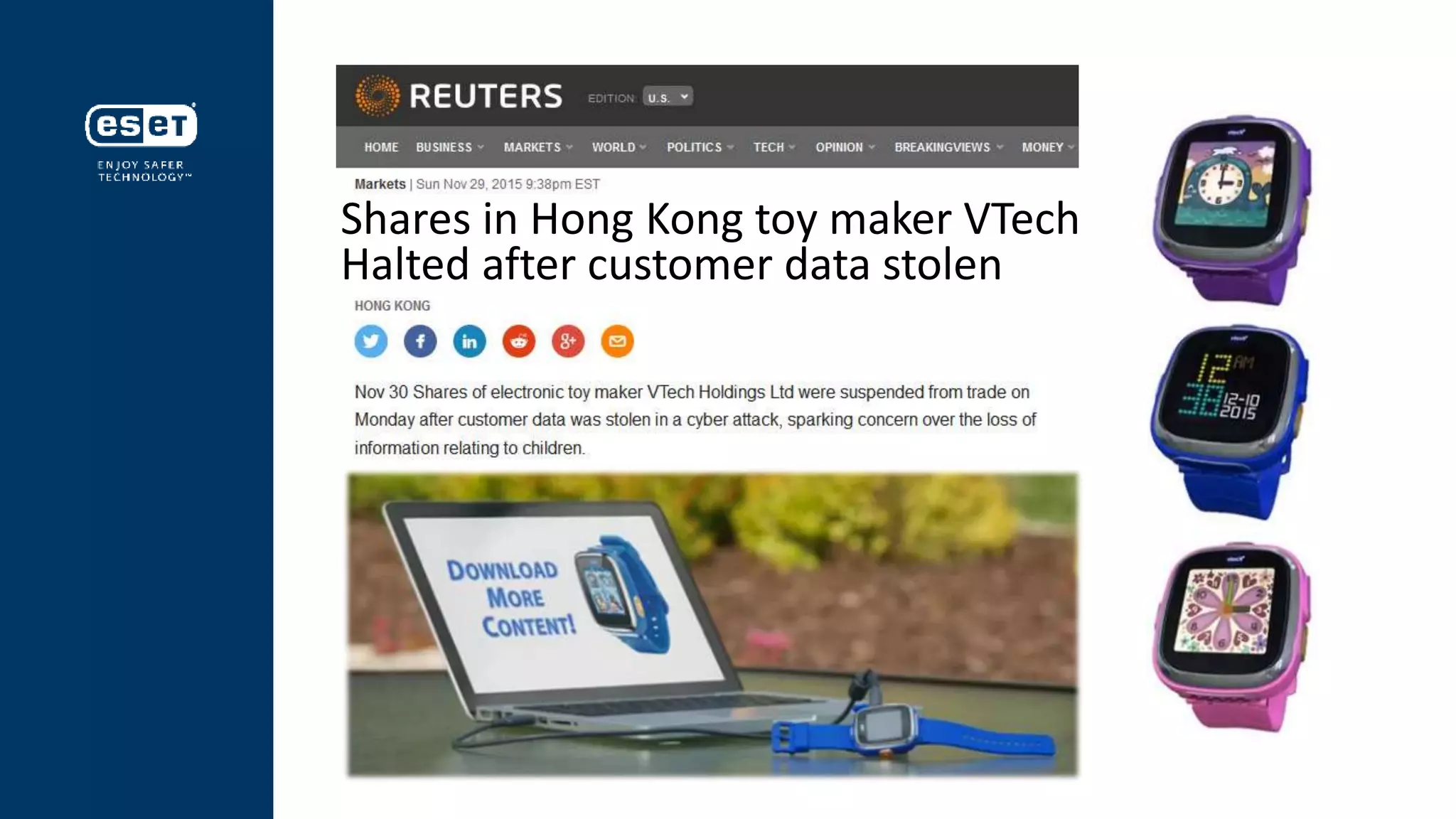
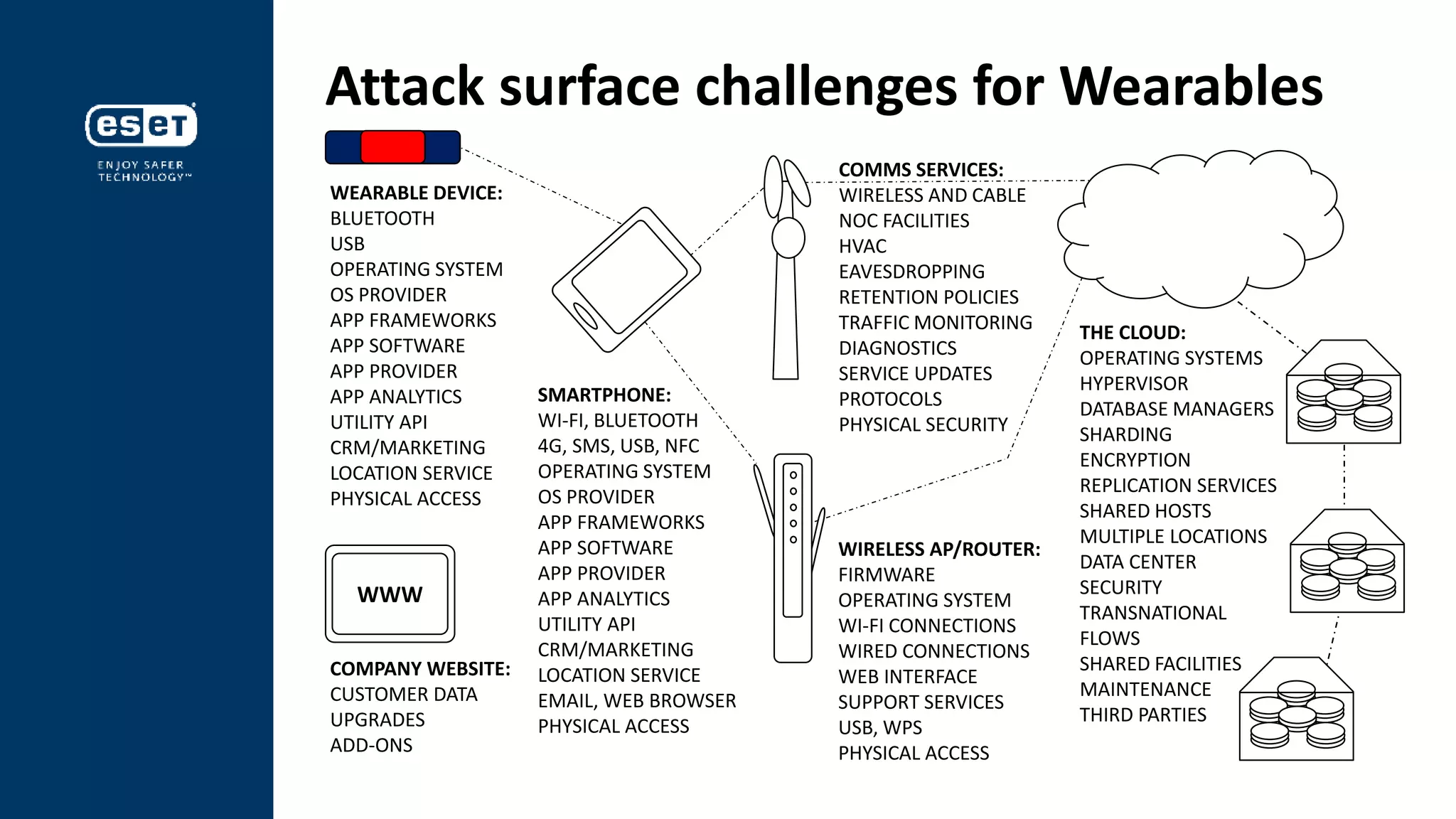
This document discusses security challenges for wearable devices and the importance of data privacy. It notes that lack of security is a major threat to wearable projects and companies, as data breaches can damage brands and share prices. The document outlines the "attack surface" of potential vulnerabilities across wearables, smartphones, wireless networks and cloud infrastructure. It advises following the US Federal Trade Commission's guidelines on reasonable security practices to develop trust with customers and avoid regulatory penalties for data misuse. The key message is that wearable makers must prioritize security and privacy by design to avoid being exploited by "criminal tech" seeking personal data.