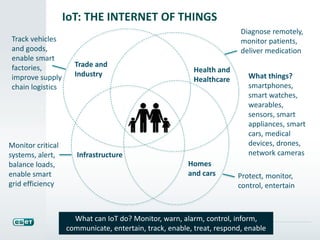
National Cyber Security Awareness Month (NCSAM) occurs every October, highlighting themes of shared responsibility and the importance of cybersecurity in various sectors, including health and the Internet of Things. Resources for improving cybersecurity skills and standards are provided, such as the NIST cybersecurity framework and various educational initiatives. The event encourages participation from individuals, organizations, and communities to enhance online safety and awareness.