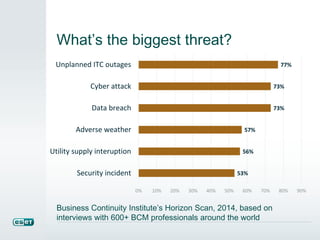
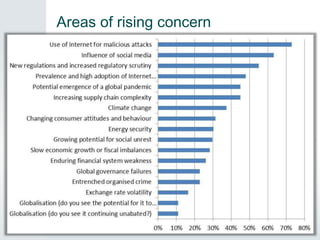
The document outlines the importance of business continuity management (BCM) for organizations to survive disruptive incidents such as natural disasters and cyber attacks, emphasizing the need for a comprehensive business continuity plan. It provides a step-by-step approach to BCM, including identifying threats, conducting business impact analysis, and developing a recovery plan, along with practical strategies for testing and refining the plan. The document also highlights emerging threats and offers resources for small to mid-sized businesses seeking assistance in disaster protection and recovery planning.