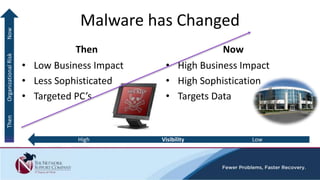
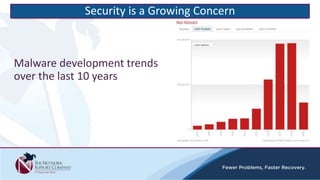
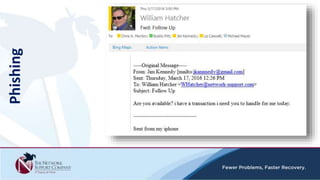
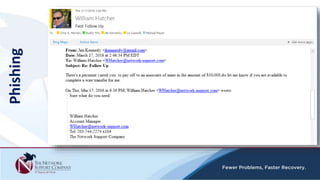
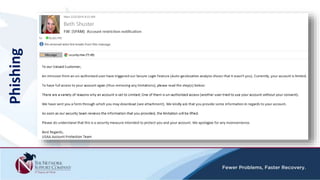
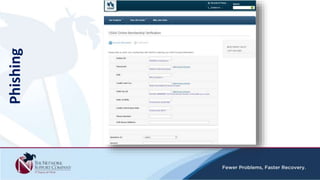
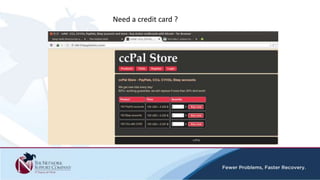
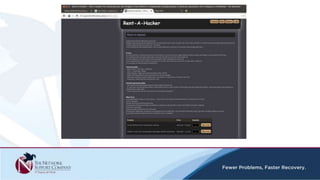
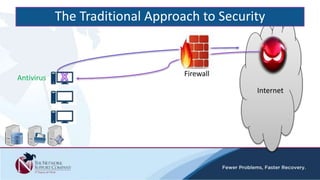
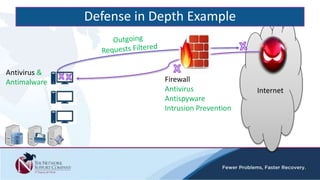
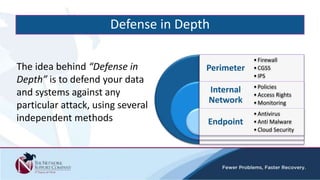
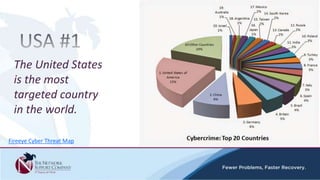
The document discusses security awareness and the growing threat of cyber attacks and data breaches. It notes that malware has become more sophisticated, targeting data and businesses rather than just PCs. The impacts of data breaches can include high costs for businesses. It recommends practicing defense in depth across networks, endpoints, and security tools to balance risk and costs. Cyber/privacy breach insurance can help cover liabilities and costs imposed by laws and regulations in the event of a security incident.