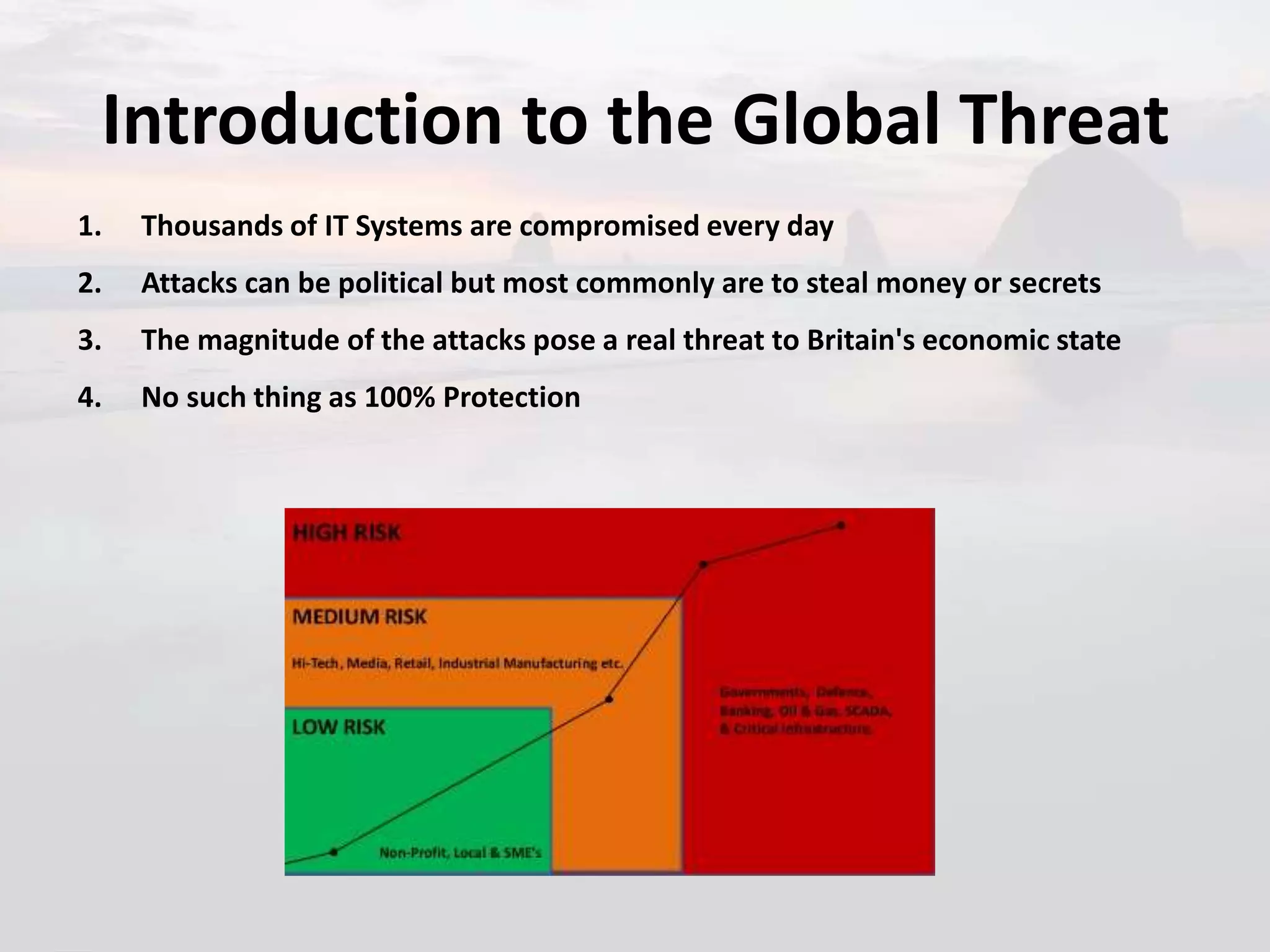
1. The document discusses the global threat landscape, including that thousands of IT systems are compromised daily and attacks are usually for monetary or espionage purposes, posing a real threat.
2. It defines advanced persistent threats as long-term network attacks to steal data rather than cause damage and distinguishes APTs by being targeted, persistent, evasive and advanced.
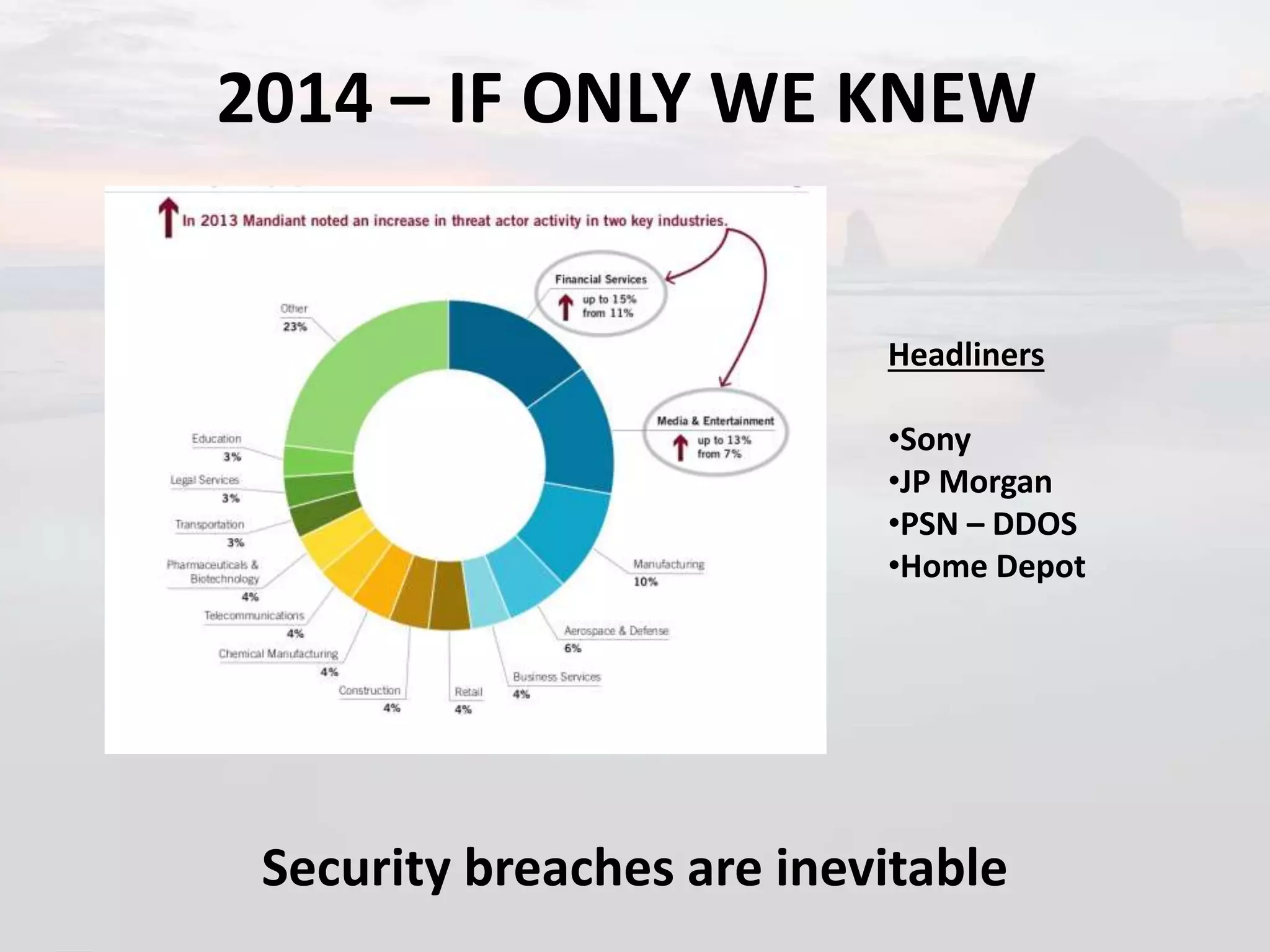
3. Major security breaches of 2014 are highlighted like Sony, JP Morgan and Home Depot to illustrate that breaches are inevitable and why organizations should care about security due to impacts like data loss, lawsuits, and brand and reputational damage.