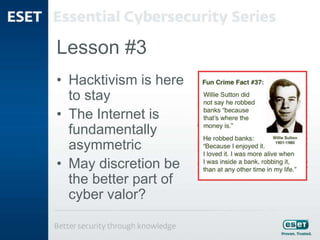
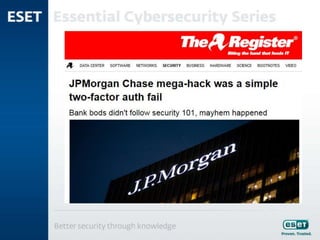
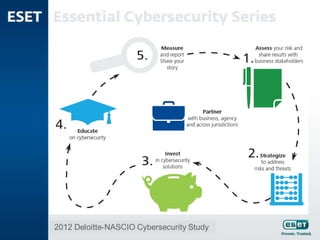
The document outlines the evolving cyber threats businesses will face in 2015, stressing the importance of learning from past incidents like the Sony Pictures and JPMorgan Chase hacks. Key lessons include the necessity of robust security measures, awareness of potential crime displacement due to new technologies, and the need for comprehensive business continuity and incident response planning. It emphasizes the importance of compliance and proactive engagement in security strategies to mitigate risks.