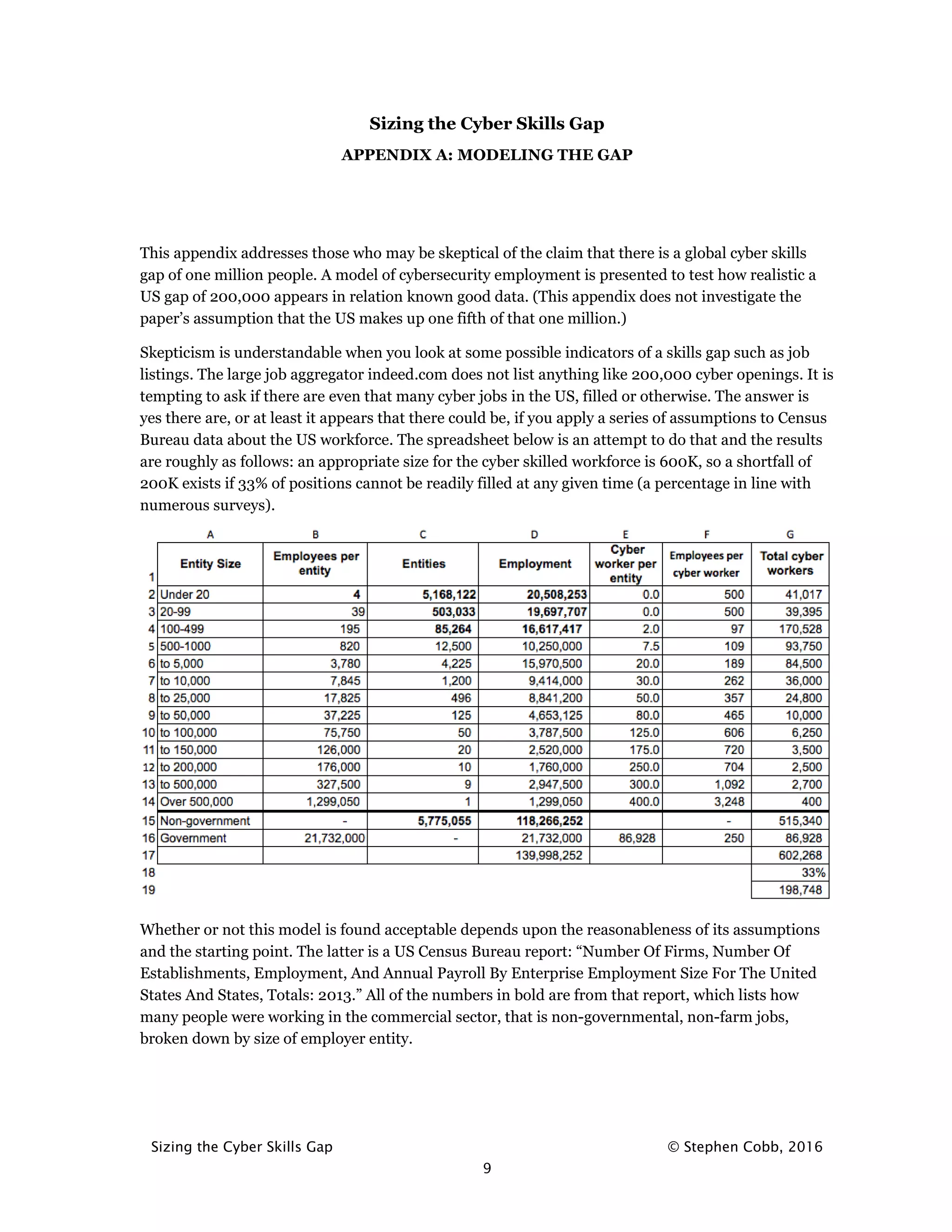
This document summarizes a white paper that evaluates claims of a global shortage of cybersecurity professionals, known as the "cyber skills gap". It discusses the origins of frequently cited estimates that there are 1 million open cybersecurity jobs worldwide. While many organizations report difficulty filling cybersecurity roles, the 1 million number originated from Cisco reports without clear sources. The document traces discussion of a cyber skills gap among US government agencies and non-profits beginning in the late 2000s. While a gap likely exists, the size and implications are worth examining given past exaggerations in the cybersecurity field.


![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
3
Sizing the Cyber Skills Gap: A white paper
Stephen Cobb, CISSP
Abstract: This white paper evaluates claims that there are not enough people in the
world with the necessary cybersecurity knowledge, skills, and abilities to meet
current demand. Frequently quoted estimates of this global “cyber skills gap” range
from 1 million today, to 1.5 million by 2020. If accurate, these numbers have serious
implications for the work of securing and defending the information systems upon
which so much of modern life depends. The origins of these numbers and their
plausibility are thus worthy of examination. The root causes of this alleged gap are
not discussed, nor are the efforts to close it, although suggestions for further
research are presented. The paper concludes that a significant cyber skills gap does
exist and can be modeled.
1. INTRODUCTION
Whether you are in charge of the security of your organization’s data and systems, or working in IT
security, or maybe just looking for a career, it is hard to ignore headlines like this one in Forbes
earlier this year: “One Million Cybersecurity Job Openings In 2016” [1]. The article cites multiple
studies that suggest there is a significant global shortage of skilled information system security
professionals, a 'cybersecurity skills gap' if you will (shortened to ‘cyber skills gap’ in many reports
and in this white paper). If there is a cyber skills gap and it is that big, then there are several serious
implications for cybersecurity:
1. Efforts to defend information systems against criminal hackers are being undermined
because organizations are under-staffed, either numerically, or qualitatively, or both [2].
2. The supply of the cybersecurity-skilled humans needs to be increased.
3. The underlying causes of the shortage of cybersecurity-skilled personnel need to be
understood and addressed.
Fortunately, numerous initiatives are underway to address points #2 and #3 (some of them are
discussed in a paper the author is presenting later this year [3]). There is no doubt that cyber security
education and recruitment efforts are receiving more and more funding [4] [5] [6]. However,
whether or not those efforts will be enough to close the gap is not the subject of this paper. The paper
also avoids discussion of what may have caused a gap although possible causes are listed in Appendix
B. The paper simply seeks to answer these questions: How true is that Forbes headline and others
like it? Does the world really need one million more cyber skilled workers than currently exist?
Why Question the Numbers?
One good reason for questioning numerical claims relating to cybersecurity headlines is the sad
reality that, historically speaking, the computer security industry does not have the best track record
when it comes to quantification. Taber was probably the first to alert the industry and the world to](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-3-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
4
this “number problem” in his landmark 1980 Computer/Law Journal article “A Survey of Computer
Crimes Studies” [7]. From the confusion created by early SRI studies in the 1970s that conflated
computer abuse and computer crime, to the $1 trillion cost of cybercrime cited by President Obama
[8], the industry has been a frequent source of suspect numbers [9]. Some numbers, like “five million
PCs infected with the Michelangelo virus,” [10] have often been repeated as fact by an unsuspecting
and often overeager press, and bent to the will of vendors and politicians. Sadly, Taber was largely
ignored and over the decades the industry has spawned numerous baseless data memes, such as the
80/20 rule of insider/outsider computer crime [11]. It certainly seems prudent to subject the million-
person cyber skills gap to scrutiny.
There can be little doubt that many organizations today are finding it hard to fill cybersecurity
positions and tap cybersecurity expertise. For example, in a 2016 global survey of IT spending, 46
percent of enterprises said they have a “problematic shortage” of cybersecurity skills [12]. A 2016
Spiceworks study found that 59% of businesses with fewer than 500 employees had no access to a
security expert (not internally, nor externally via third-party contractor or managed security
provider) [13]. In its 2015 Global Cybersecurity Status Report, ISACA revealed that 86% of
information security managers interviewed believe there is a shortage of skilled cybersecurity
professionals [14]. But do these opinions really amount to a cyber skills gap, and if so, how wide is it?
THE ONE MILLION GEEK GAP
The oft-cited million-person cyber skills gap appears to have its origins in a section of the Cisco 2014
Annual Security Report, also known as the 2014 CASR [15]. The section was titled “The Security
Talent Shortage and Solutions Gap” and it stated the following: “It’s estimated that by 2014 the
industry will still be short more than a million security professionals across the globe.” This sentence
sounds odd in a 2014 report because it seems to talk about 2014 as the future, implying that the
shortage had reached the one million mark some period prior. Also curious is the lack of a footnote
or other source for this number (despite the report having more three dozen endnotes). These
oddities did not prevent “one million” being picked up and repeated, not only by journalists and
industry experts [16] [17] but also by Cisco itself.
In 2015, the company published a document titled Mitigating the Cybersecurity Skills Shortage
[18]. The first paragraph states: “Cisco estimates there are more than 1 million unfilled security jobs
worldwide.” This time there is a footnote and it points to Cisco Security Capabilities Benchmark
Study (Cisco, Oct. 2014). Tracking down this study is not easy, but it appears to be reported in a
section of the Cisco 2015 Annual Security Report titled “Cisco Security Capabilities Benchmark
Study” [19]. Unfortunately, there is no reference to a shortage of information security professionals
in that section, or indeed that entire report. So where did Cisco get the notion that the 2014 global
shortfall of security professionals was 1 million?
Getting to One Million
In the United States (US), concern about a cyber skills gap originated within federal government
circles, most notably the military. The Air Force added cyberspace to its mission statement in 2005
which now reads: “to fly and fight in Air, Space and Cyberspace” [20], and in 2006 the 8th Air Force
was designated the service’s new cyberspace command, “focused on taking the fight against terrorism](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-4-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
5
to the technological realm” [21]. In 2008 the DoD recognized cyberspace as a warfighting domain in
need of appropriately trained cyber warriors [22]. The need to recruit for cyber roles in the military,
both attack and defense, produced numerous studies pertinent to the skills gap and these will be
discussed later in the Virus Bulletin paper mentioned earlier [3].
Recognizing the need for a federal cybersecurity strategy beyond the military the non-partisan non-
profit Center for Strategic and International Studies (CSIS) created the “CSIS Commission on
Cybersecurity for the 44th Presidency.” In December of 2008 the commission published a report
listing 25 recommendations, the 24th of which was: “Conduct Training for Cyber Education and
Workforce Development” [23]. However, the Commission left no doubt that the cyber skills gap was
an urgent concern:
“The cyber threat to the United States affects all aspects of society, business, and
government, but there is neither a broad cadre of cyber experts nor an established cyber
career field to build upon, particularly within the Federal government.” [21]
In April of 2009, Defense Secretary Robert Gates, speaking at the Air War College about the need to
“increase the throughput of training of experts in cyber” admitted that: “We are desperately short of
people who have capabilities in this area in all the services and we have to address it.” [24] This was
picked up by the New York Times in a May, 2009 article titled: “Cadets Trade the Trenches for
Firewalls” [25].
CSIS continued studying this problem and in July of 2010 published a 50-page analysis starkly titled:
A Human Capital Crisis in Cybersecurity [26]. This report included the following statement from
the founding Director of the CIA’s Clandestine Information Technology Office: “There are about
1,000 security people in the US who have the specialized security skills to operate effectively in
cyberspace. We need 10,000 to 30,000.” The CSIS report went on to describe the problem as one
both of depth and breadth, quality as well as quantity:
“We not only have a shortage of the highly technically skilled people required to operate and
support systems already deployed, but also an even more desperate shortage of people who
can design secure systems, write safe computer code, and create the ever more sophisticated
tools needed to prevent, detect, mitigate and reconstitute from damage due to system
failures and malicious acts.”
In January of 2009 another nonprofit organization, the nonpartisan Partnership for Public Service,
had begun studying the cyber skills shortage. Supported by government contractor Booz Allen
Hamilton, the researchers talked to “69 officials from 18 departments, agencies, subcomponents” to
produce Cyber IN-SECURITY: Strengthening the Federal Cybersecurity Workforce [27]. This
report contained some sobering findings: CISOs and CIOs in a wide range of government agencies,
not just those in the defense realm, said it was hard to find enough good applicants for cybersecurity
openings. Furthermore, and perhaps even more worrying, researchers found:
“…there is no strategic government-wide assessment of the current state of the cybersecurity
workforce, its size, strengths and weaknesses. There is no federal plan projecting how many
cybersecurity specialists will be needed next year or in the next five years to meet individual](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-5-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
6
agency and government-wide needs, what skills and certifications they should possess, how
they should be trained, or how they should be recruited into federal service.”
While there has been progress since 2009 on some of these issues, the Cyber IN-SECURITY report
struck several chords that would resonate over the next seven years, such as differences in opinion
between CIOs and CISOs on the one hand, and the Human Resources (HR) departments charged
with finding cyber-skilled employees for them on the other. HR tended to be pleased with its efforts
at finding candidates, but the CIO/CISO view was much less flattering. For example, only 30% of the
latter said that they were satisfied with the number of applicants supplied by HR, whereas HR was
45% satisfied.
Vested Interests?
The Cyber IN-SECURITY study put the federal cyber skills shortage on the map and, by the end of
2009, the problem was being reported by mainstream media and popular technology journalists like
Brian Krebs [28]. Cyber IN-SECURITY also highlighted the government’s over-reliance on the
private sector for data about cybersecurity (the report itself was not commissioned or funded by the
government). The author has discussed the downsides of such over-reliance elsewhere [9]. To
summarize, it creates a risk that politicians who are looking for reasons not to increase funding for
government activities – like fighting cybercrime or investing in cyber workforce development – may
find it convenient to discount arguments that are based on data from entities who stand to gain from
that increased spending. Such entities include cybersecurity contractors, vendors, consultants, as
well as educational institutions and certification organizations.
For example, any research that shows a need for more cybersecurity education and certification can
be seen as benefiting those who generate revenue by meeting that need, whether they are for-profit,
like Phoenix University and SANS Institute, or non-profit like Norwich University and CompTIA.
This observation does not imply that the ethics or integrity of any entity are necessarily suspect, but
unfortunately the information security industry is no stranger to exaggerations that have
undermined valid messaging about legitimate concerns, sometimes to the detriment of security (for
example, claims that outsider threats had outpaced insider threats in the late 1990s, claims that were
beneficial to firewall vendors, arguably led to complacency about insiders). There is a strong case for
saying that, when it comes to public policy debates, the use of data generated by objective agencies is
better for policymaking than relying on commercial entities for data. That said, there are valuable
insights to be gained from data created outside of government, particularly if it is used carefully, and
especially if it has been subjected to peer review.
Workforce Studies
Beyond the government and military, the cyber workforce in general has arguably been experiencing
a skills gap for some time. Consider the sixth edition of the Global Information Security Workforce
Study (GISWS), a study that has been produced biennially for many years by one of the largest non-
profit cybersecurity certification organizations, (ISC)2. This worldwide survey of more than 12,000
information security professionals, conducted in the fourth quarter of 2012 in partnership with Booz
Allen Hamilton, and with the assistance of Frost & Sullivan, found that:](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-6-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
7
“Even with past annual growth in the double-digits, workforce shortages persist – 56% of
respondents believe there is a workforce shortage, compared to 2% that believe there is a
surplus [29].”
The report went on to make an important point to which CISOs and their IT security staff can surely
attest: “The impact of shortage is the greatest on the existing workforce.”
Early in 2014 the RAND Corporation think tank weighed in on the global cyber skills gap with a
report titled H4ckers Wanted: An Examination of the Cybersecurity Labor Market [30]. Containing
a useful review of previous studies, including some of those mentioned above, this report looked at
numerous government initiatives to address the cyber skills gap, programs set in motion since
alarms were raised in 2008. Most notable among these is the National Initiative for Cybersecurity
Education (NICE), an interagency effort coordinated by the National Institute of Standards and
Technology (NIST) “to improve the nation’s cybersecurity education, including efforts directed at the
federal workforce” [31]. RAND also reviewed fluctuations in enrollment in computer science degree
programs and the role of the NSA in promoting Centers of Cyber Excellence.
Somewhat surprisingly, the RAND report’s recommendations amounted to ‘steady as she goes.’ This
perspective was based in part on RAND’s analysis of the economics of labor markets. RAND
concluded that, given the existing government programs, market forces would remove the cyber
skills gap over time. Unfortunately, that time was put at 5 to 10 years, and RAND seemed unaware
that a timeframe like that is of little practical help to those charged with protecting organizations
from cyber threats today.
Just as worrying was another factor in RAND’s analysis, explained like this: “By then [meaning the 5-
10 year timeframe] the current concern over cybersecurity could easily abate, driven by new
technology and more secure architectures.” While the majority of information security professionals
would welcome such developments – many have other interests they would like to pursue – relying
on “new technology and more secure architectures” to solve the cybersecurity problem is hardly a
practical strategy. The impact of unchecked cyber crime and conflict in the interim has to be
acknowledged, with its potential to erode trust in digital technology, cripple critical infrastructure,
and generally retard economic growth.
Sadly, but perhaps predictably, no evidence for RAND’s optimism was to be found in the 2015
GISWS; this edition of the study reported that the “information security workforce shortfall” was
growing wider [32]. The percentage of respondents who said that their organizations had too few
information security professionals had risen to 62%, from 56% in the 2013 survey. As for the
economics of the labor market, responses to a variety of questions in this study led researchers to
conclude this hiring shortfall was “less about money” and more about “an insufficient pool of suitable
candidates”.
For many years, research consultants Frost & Sullivan assisted (ISC)2 with the GISWS. In 2015,
based on analysis of that data and their in-house tracking, Frost & Sullivan predicted that by 2020
the cyber skills gap would be 1.5 million. This number was described as “the difference between Frost
& Sullivan’s projection of the workforce needed to fully address escalating security staffing needs and
our workforce projection that accounts for workforce supply constraints (e.g., a tightening labor
market among security professionals)” [32].](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-7-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
8
CONCLUSIONS AND IMPLICATIONS
Does that mean we have now reached Cisco’s 1 million mark? This paper concludes that yes, it is
entirely plausible that, in order to secure its digital information systems, the world needs to 1 million
more people than are currently available. Here are some more data points that support this assertion.
In 2015, a news organization at the Stanford Journalism Program reported that, based on their
analysis of Bureau of Labor Statistics, at least 209,000 cybersecurity jobs in the US were unfilled
[33]. Their analysis also showed cybersecurity job postings rising rapidly – “up 74% percent over the
past five years.” That equates to a year-on-year growth rate of 15% in unfilled positions, which is
consistent with numerous surveys of industry hiring intentions.
Rounding down to 200,000 unfilled cybersecurity jobs in the US produces a number that is quite
plausible relative to other stats, some of which are modeled in a spreadsheet in Appendix A. That
200K figure also extrapolates convincingly to 1 million globally. Although the US is one of the
heaviest users of information systems, it arguably accounts for a lot less than one fifth of the global
total of digital technology users, a useful metric for estimating the amount of cybersecurity work that
needs to be done. The consequences of not getting that work done are beyond the scope of this paper,
but it seems reasonable to assert that multiple aspects of the current situation urgently require
further research (and one might argue that this assertion would be equally valid if the gap were found
to be half a million and not a whole million).
Below are suggested topics for further research (some of which may be the subject of current but as
yet unpublished research). The author hopes to revisit the literature next year to review any progress
in these and related areas.
One urgent area for action, not just research, is the improvement of hiring practices for cybersecurity
roles. Despite the size of the cyber skills gap, the author is occasionally aware of individuals skilled in
cybersecurity who are unemployed or underemployed. The causes of this situation, one of which
appears to be immature cybersecurity hiring practices within organizations [34] [35], require urgent
study and remediation.
Suggestions for Further Research:
• How are organizations coping with the shortage of qualified applicants for cybersecurity
vacancies?
• What is the impact of understaffing on the cybersecurity of organizations?
• Can market forces solve close the cyber skills gap or is there a limit to the ability of higher
salaries for cybersecurity roles to draw enough suitable entrants into the field?
• How should “suitable entrant into the field” be defined, in terms of Knowledge, Skills, and
Abilities (KSAs) or is there more, like aptitude, personality, or even g? [3]
• Can cybersecurity roles be made more appealing within society, perhaps as public service
calling or the work of heroes? [36]
• What is the basis of job satisfaction in cybersecurity and is it sustainable?](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-8-2048.jpg)


![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
12
REFERENCES
Note: In the PDF version of this document the http references are clickable URLs.
[1] Morgan, S. (2016) “One Million Cybersecurity Job Openings In 2016” Forbes, January 2, accessed at
http://www.forbes.com/sites/stevemorgan/2016/01/02/one-million-cybersecurity-job-
openings-in-2016/#1ed106a77d27
[2] Drinkwater, D. (2015) “Cyber-security pros blame breaches on skills gap” SC Magazine, April 16
accessed at http://www.scmagazineuk.com/cyber-security-pros-blame-breaches-on-skills-
gap/article/409393
[3] Cobb, S. (2016) “Mind This Gap: Criminal hacking and the global cybersecurity skills shortage, a
critical analysis” Virus Bulletin, in process, to be accessed at
https://www.virusbulletin.com/conference/vb2016/abstracts/mind-gap-criminal-hacking-and-
global-cybersecurity-skills-shortage-critical-analysis
[4] White House (2016) “FACT SHEET: Cybersecurity National Action Plan” White House, accessed at
https://www.whitehouse.gov/the-press-office/2016/02/09/fact-sheet-cybersecurity-national-
action-plan
[5] Curtis, J. (2015) “UK Gov will double cybersecurity funding to fend off ‘ISIS cyber attacks’” IT Pro UK,
November 17, accessed at http://www.itpro.co.uk/security/25611/uk-gov-will-double-
cybersecurity-funding-to-fend-off-isis-cyber-attacks.
[6] Peters, S. (2016) “New White House Cybersecurity Plan Creates Federal CISO” Dark Reading,
February 9, accessed at http://www.darkreading.com/risk/new-white-house-cybersecurity-plan-
creates-federal-ciso---/d/d-id/1324243
[7] Taber, J. (1980) “A Survey of Computer Crime Studies” Computer/Law Journal, 275, accessed at
http://repository.jmls.edu/jitpl/vol2/iss1/15
[8] Maass, P. and Rajagopalan, M. (2012) “Does Cyber Crime Really Cost $1 Trillion?” Pro Publica.
accessed at: http://www. propublica. org/article/does-cybercrime-really-cost-1-trillion
[9] Cobb, S. (2015) “Sizing Cybercrime: Incidents and accidents, hints and allegations” Virus Bulletin,
accessed at https://www.virusbulletin.com/blog/2016/02/vb2015-paper-sizing-cybercrime-
incidents-and-accidents-hints-and-allegations/
[10] Rosenberger, R. (1995) Computer Viruses and False Authority Syndrome, accessed at
http://vmyths.com/mm/fas/fas.pdf
[11] Bejtlich, R. (2009) “Insider Threat Myth Documentation” TaoSecurity, accessed at
http://taosecurity.blogspot.com/2009/05/insider-threat-myth-documentation.html](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-12-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
13
[12] Oltsik, J. (2016) “High-demand cybersecurity skill sets” Network World, May 10, accessed at
http://www.networkworld.com/article/3068177/security/high-demand-cybersecurity-skill-
sets.html
[13] Lemos, R. (2016) “IT Security Skills Gap More Harmful for SMBs Than Larger Firms” eWeek, July 3
accessed at http://www.eweek.com/security/it-security-skills-gap-more-harmful-for-smbs-than-
larger-firms.html
[14] ISACA (2015) “2015 Global Cybersecurity Status Report” ISACA, accessed at
http://www.isaca.org/cyber/Documents/2015-Global-Cybersecurity-Status-Report-Data-
Sheet_mkt_Eng_0115.pdf
[15 Cisco (2014) “Cisco 2014 Annual Security Report” Cisco, accessed at
http://www.cisco.com/web/offer/gist_ty2_asset/Cisco_2014_ASR.pdf
[16] Morgan, S. (2016) “One Million Cybersecurity Job Openings In 2016” Forbes, January 2, accessed at
http://www.forbes.com/sites/stevemorgan/2016/01/02/one-million-cybersecurity-job-
openings-in-2016/#1ed106a77d27
[17] Bednarz, A. (2015) “Cisco estimates a million unfilled security jobs worldwide” Network World,
March 9, accessed at http://www.networkworld.com/article/2893365/security0/shortage-of-
security-pros-worsens.html
[18] Cisco (2015a) “Mitigating the Cybersecurity Skills Shortage” Cisco, accessed at
http://www.cisco.com/c/dam/en/us/products/collateral/security/cybersecurity-talent.pdf
[19] Cisco (2015b) “Cisco 2015 Annual Security Report” Cisco, access [gated] at
http://www.cisco.com/web/offers/lp/2015-annual-security-report/index.html
[20] U.S. Air Force (2005) “Cyberspace as a Domain In which the Air Force Flies and Fights: Remarks as
delivered to the C4ISR Integration Conference, Nov. 2, 2006” U.S. Air Force website, accessed
ahttp://www.af.mil/AboutUs/SpeechesArchive/Display/tabid/268/Article/143968/cyberspace-
as-a-domain-in-which-the-air-force-flies-and-fights.aspx
[21] Wood, S. (2006) “New Air Force Command to Fight in Cyberspace” American Forces Press Service,
accessed ahttp://archive.defense.gov/news/newsarticle.aspx?id=2014
[22] U.S. Air Force (2009) “The Cyber Menace” AIR FORCE Magazine, March, accessed at
http://www.airforcemag.com/magazinearchive/documents/2009/march%202009/0309cyber.pd
f
[23] CSIC (2008) Securing Cyberspace for the 44th Presidency Report of the CSIS Commission on
Cybersecurity for the 44th Presidency, Center for Strategic and International Studies, accessed at
https://csis-prod.s3.amazonaws.com/s3fs-
public/legacy_files/files/media/csis/pubs/081208_securingcyberspace_44.pdf
[24] Real Clear Politics (2009) “Secretary Gates Talks to Troops in Alabama” Real Clear Politics accessed
at
http://www.realclearpolitics.com/articles/2009/04/15/gates_talks_to_troops_in_alabama_96023.
html#ixzz4DNvqTeHg
[25] Kilgannon, C. and Cohen, N. (2009) “Cadets Trade the Trenches for Firewalls” New York Times, May
10, accessed at http://www.nytimes.com/2009/05/11/technology/11cybergames.html](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-13-2048.jpg)
![Sizing the Cyber Skills Gap © Stephen Cobb, 2016
14
[26] Evans, K. and Reeder, F. (2010) “A human capital crisis in cybersecurity: A report of the CSIS
commission on cybersecurity for the 44th presidency” Center for Strategic & International Studies,
accessed at https://csis-prod.s3.amazonaws.com/s3fs-
public/legacy_files/files/publication/100720_Lewis_HumanCapital_WEB_BlkWhteVersion.pdf
[27] Partnership for Public Service (2009) Cyber IN-SECURITY: Strengthening the Federal Cybersecurity
Workforce, Booz Allen Hamilton, accessed at
https://www.boozallen.com/content/dam/boozallen/media/file/CyberIn-Security_2009.pdf
[28] Krebs, B and Nakashima, E. (2009) “As attacks increase, U.S. struggles to recruit computer security
experts” Washington Post, December 23, accessed at http://www.washingtonpost.com/wp-
dyn/content/article/2009/12/22/AR2009122203789.html
[29] (ISC)2 (2013) 2013 Global Information Security Workforce Study (ISC)2 accessed at
https://www.isc2cares.org/uploadedFiles/wwwisc2caresorg/Content/2013-ISC2-Global-
Information-Security-Workforce-Study.pdf
[30] Libicki, M. C., Senty, D. and Pollak, J. (2014) Hackers Wanted: an examination of the cybersecurity
labor market. Rand Corp. accessed at
http://www.rand.org/content/dam/rand/pubs/research_reports/RR400/RR430/RAND_RR430.p
df
[31] NICE (2014) National Cybersecurity Workforce Framework, website and link to the interactive
version accessed at http://csrc.nist.gov/nice/framework
[32] (ISC)2 (2015) 2015 Global Information Security Workforce Study (ISC)2 accessed at
https://www.isc2cares.org/uploadedFiles/wwwisc2caresorg/Content/GISWS/FrostSullivan-
(ISC)%C2%B2-Global-Information-Security-Workforce-Study-2015.pdf
[33] Satelvad,(2015) A. “Demand to fill cybersecurity jobs booming” Peninsula Press, March 31, accessed
at http://peninsulapress.com/2015/03/31/cybersecurity-jobs-growth/
[34] Schwartau, W. (2016) “Hiring the Unhireable” RSA Conference, San Franciso (video), March 15
accessed at https://www.rsaconference.com/videos/hiring-the-unhireable
[35] Cobb, S. (2016) “What the CISSP? 20 years as a Certified Information Systems Security Professional”
We Live Security, May 28, accessed at http://www.welivesecurity.com/2016/05/28/cissp-
certified-information-systems-security-professional/
[36] Collar Jr, E. (2015) “Where is the Cybersecurity Hero? Practical Recommendations for Making
Cybersecurity Heroism More Visible in Organizations” International Journal of Computer Science
and Information Security, 13(4), 1. accessed at
http://www.academia.edu/download/37479983/01_Paper_31031505_IJCSIS_Camera_Ready_pp._
1-5.pdf](https://image.slidesharecdn.com/sizing-cyber-skills-gap-v1-160718233132/75/Sizing-the-Cyber-Skills-Gap-14-2048.jpg)