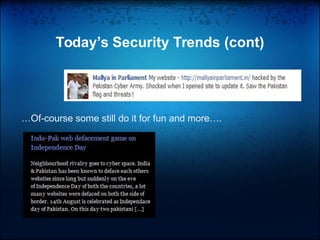
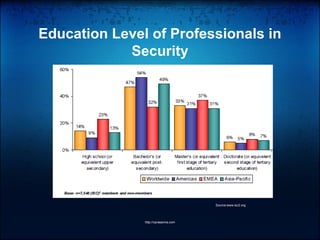
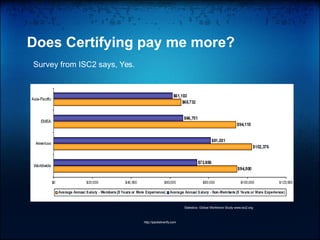
The document outlines the current trends in information security, highlighting a growing demand for skilled professionals due to the rise of cybercrime and the need for robust security measures. It details the necessary skills, fields of work, and certifications for various job titles within security roles, such as security engineer, administrator, and manager. Additionally, it emphasizes the importance of continuous learning and obtaining relevant certifications to enhance career prospects in the security domain.