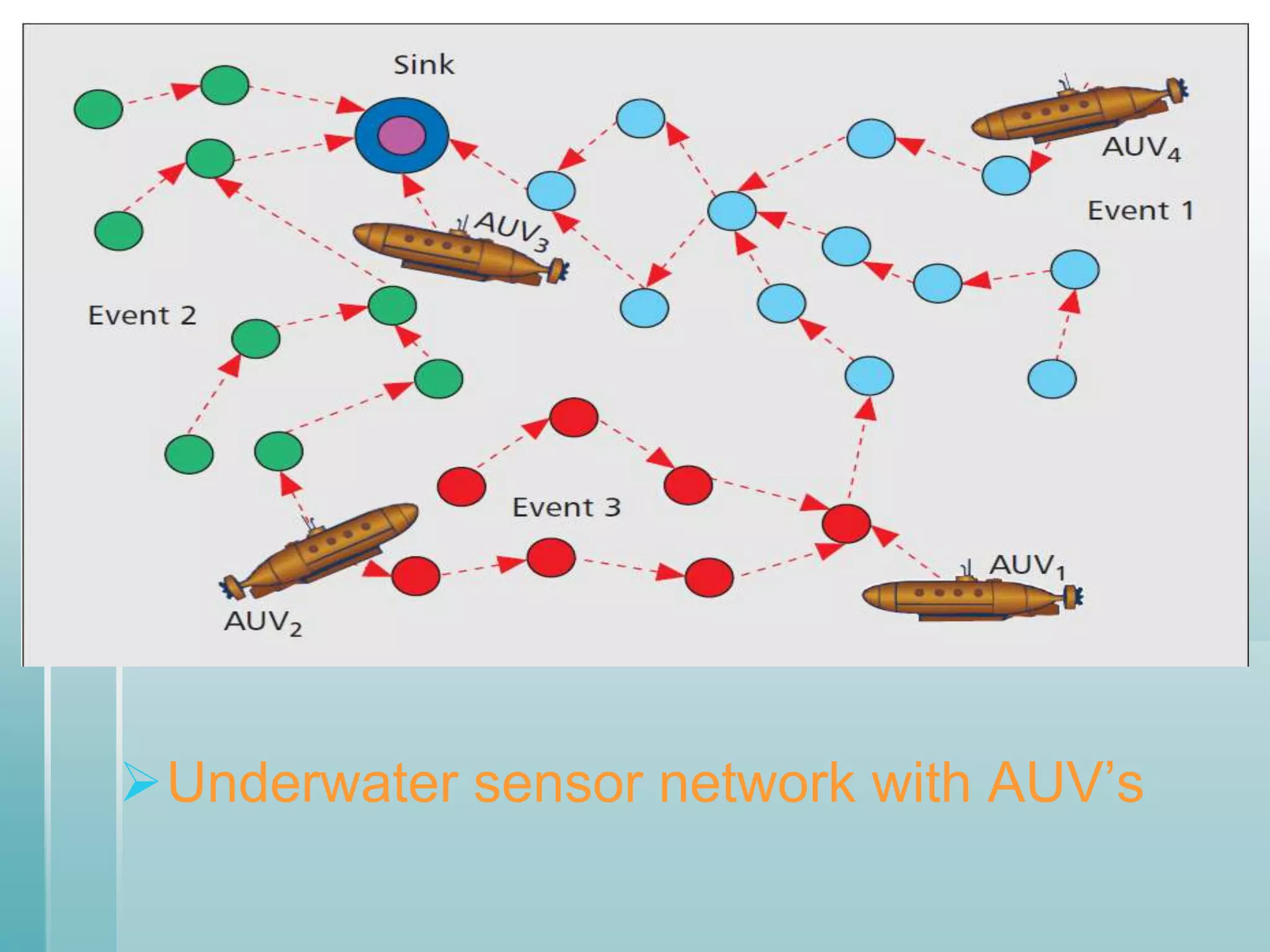
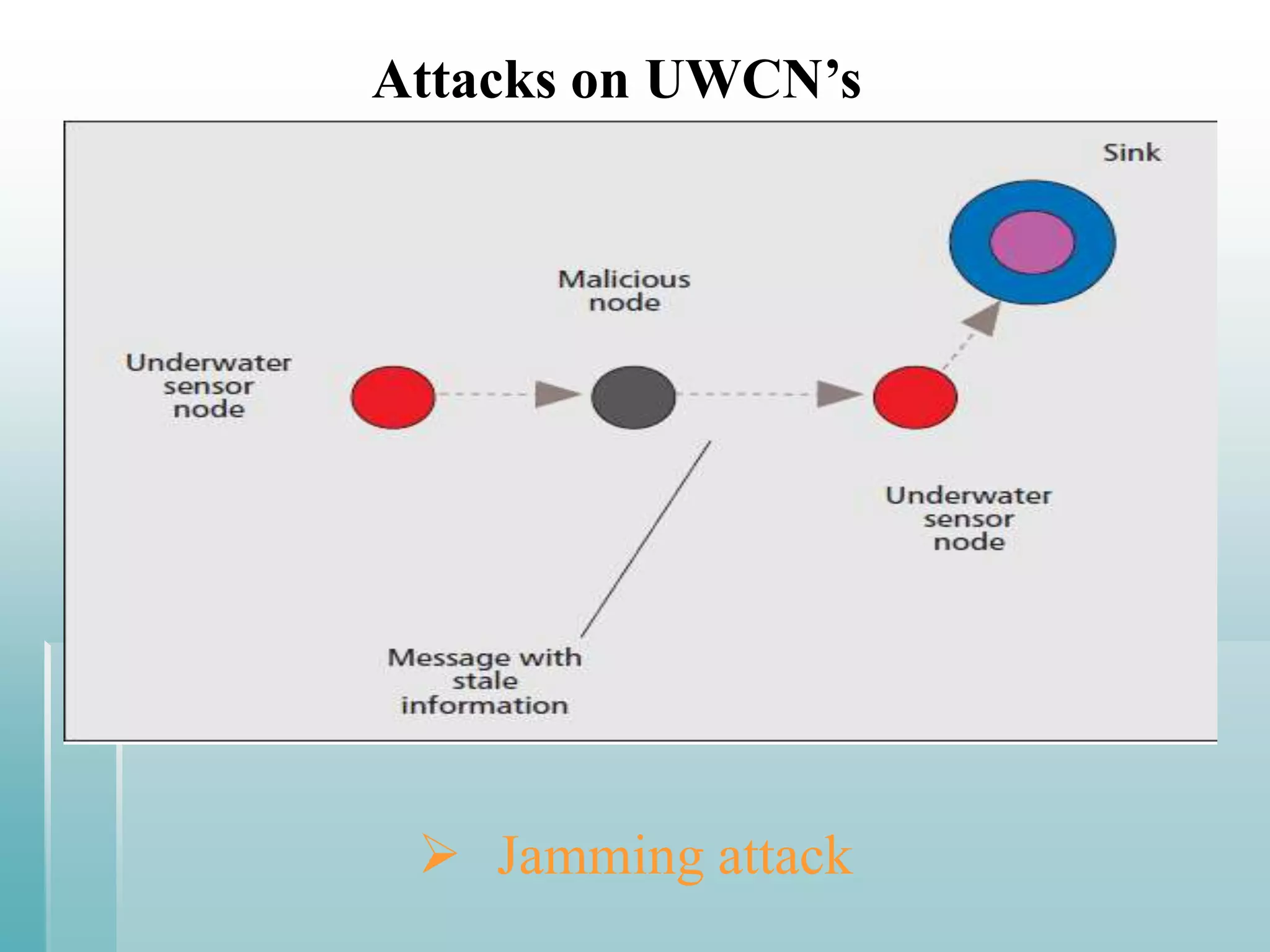
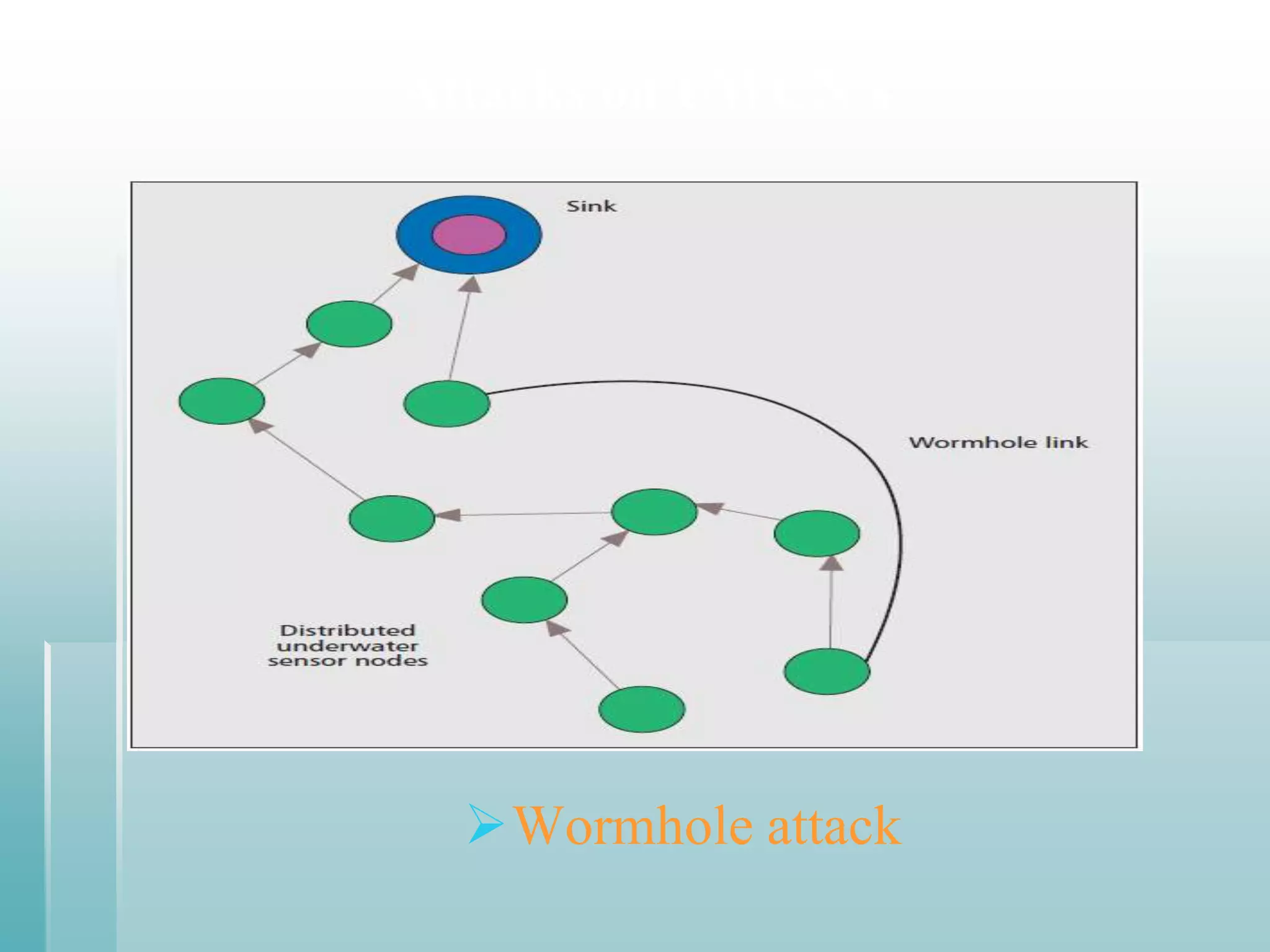
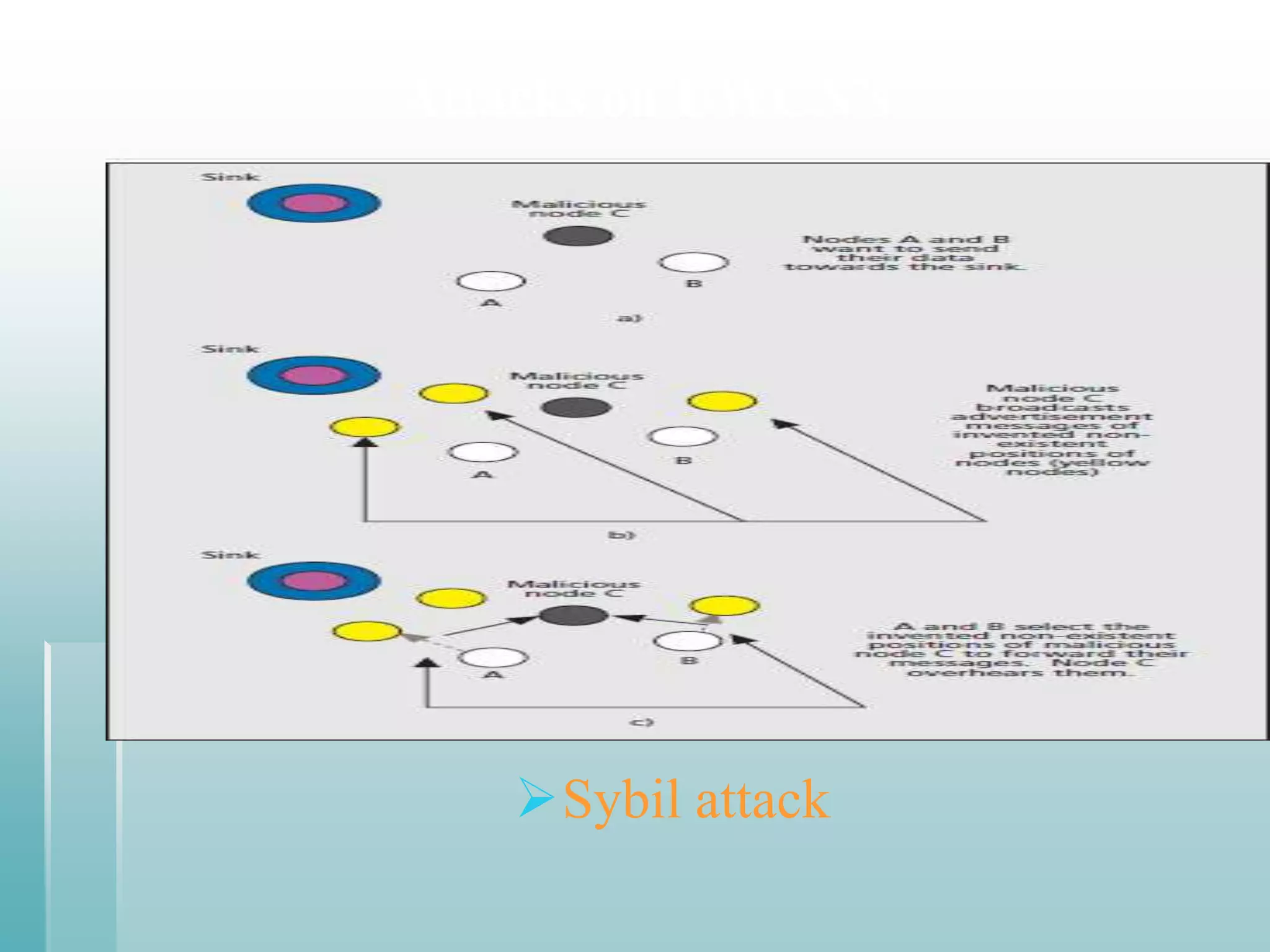
This document summarizes a seminar presentation on securing underwater wireless communication networks. It discusses the existing challenges with underwater wireless networks including high bit error rates, propagation delays, and low bandwidth. It proposes three schemes for securing such networks: secure time synchronization to enable power saving; secure localization for location information and data tagging; and secure routing to reject paths with malicious nodes. The techniques aim to provide secure data transmission and are based on mechanisms like time synchronization, localization using time/signal information, and routing protocols.