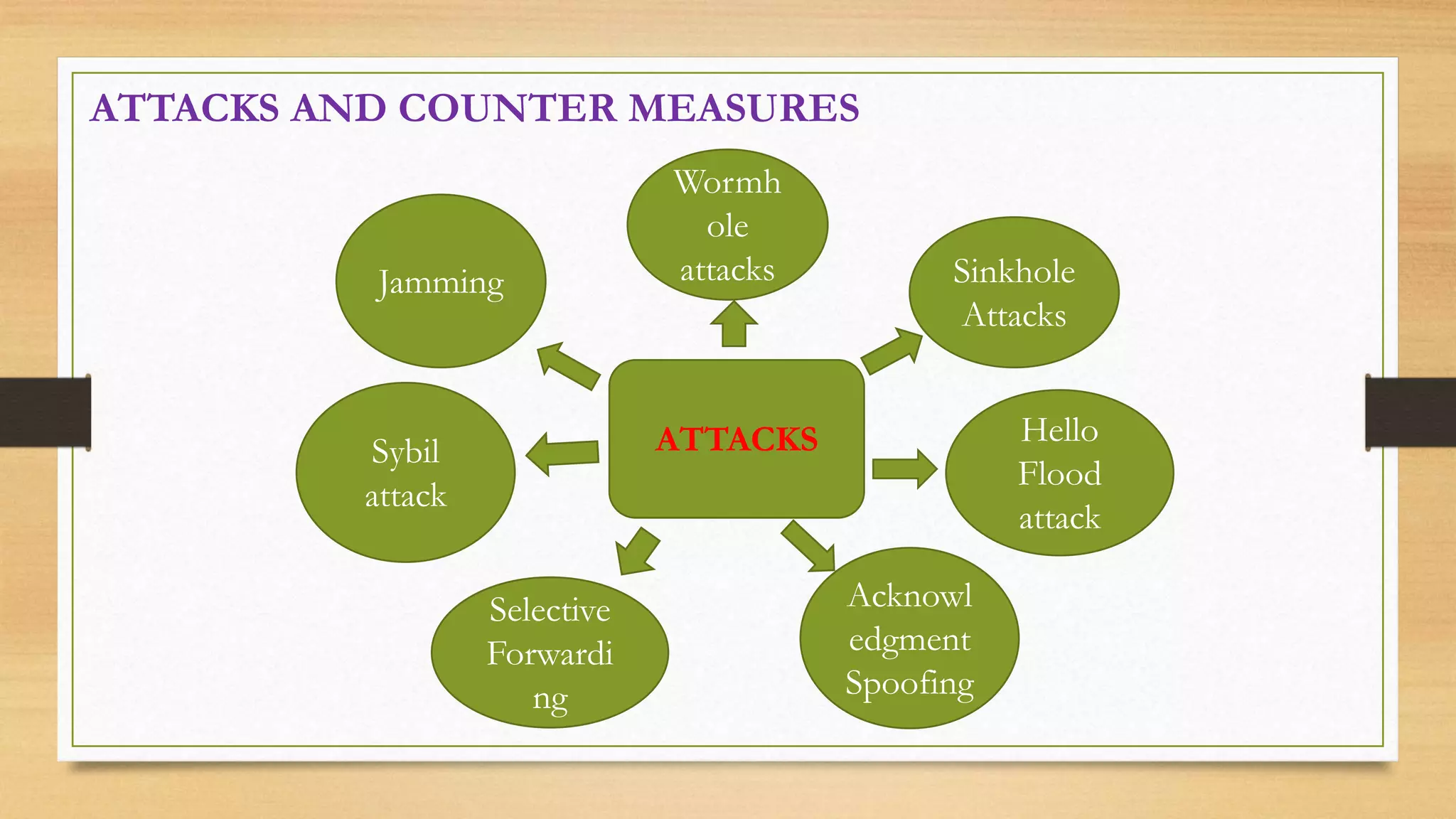
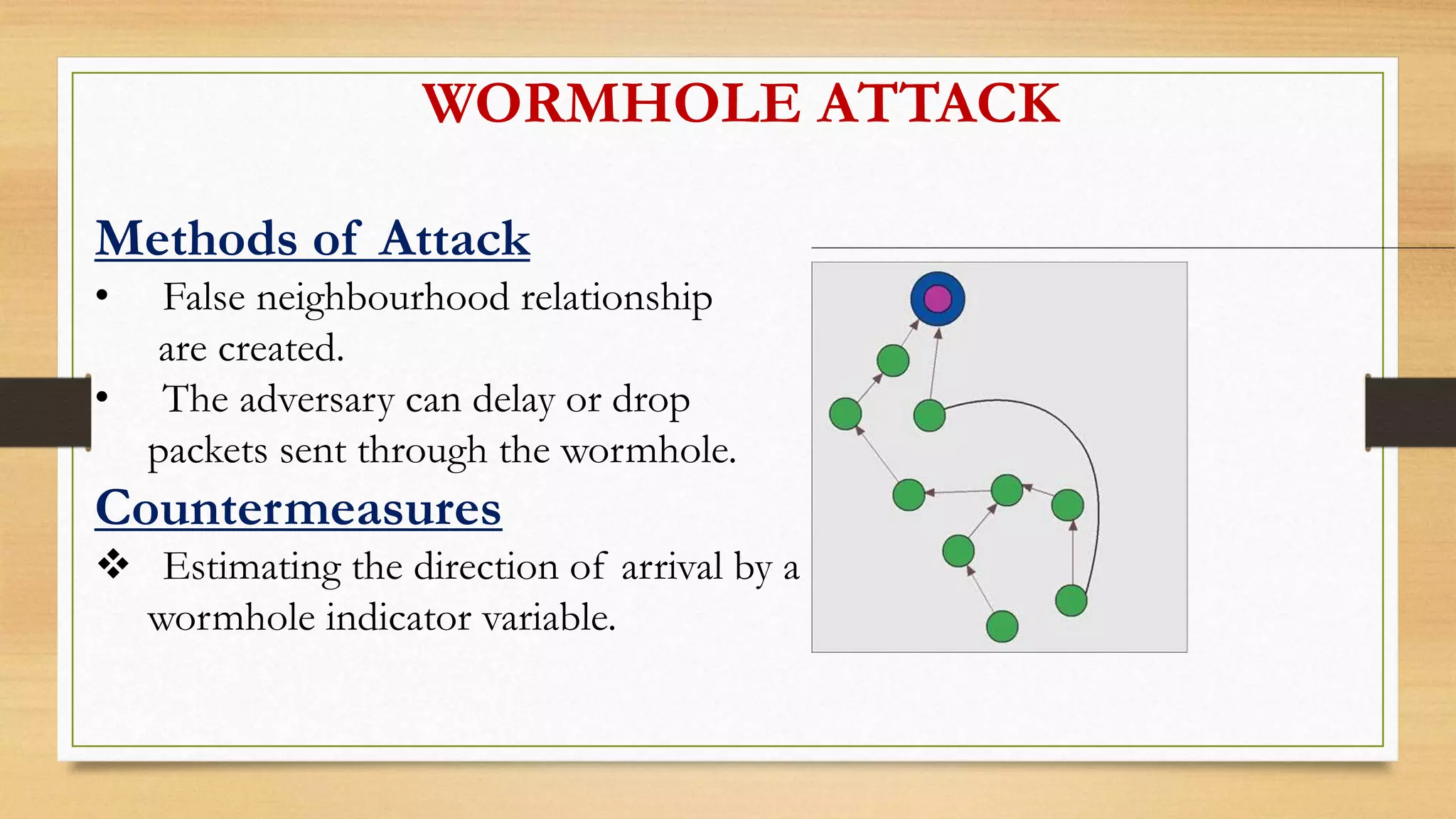
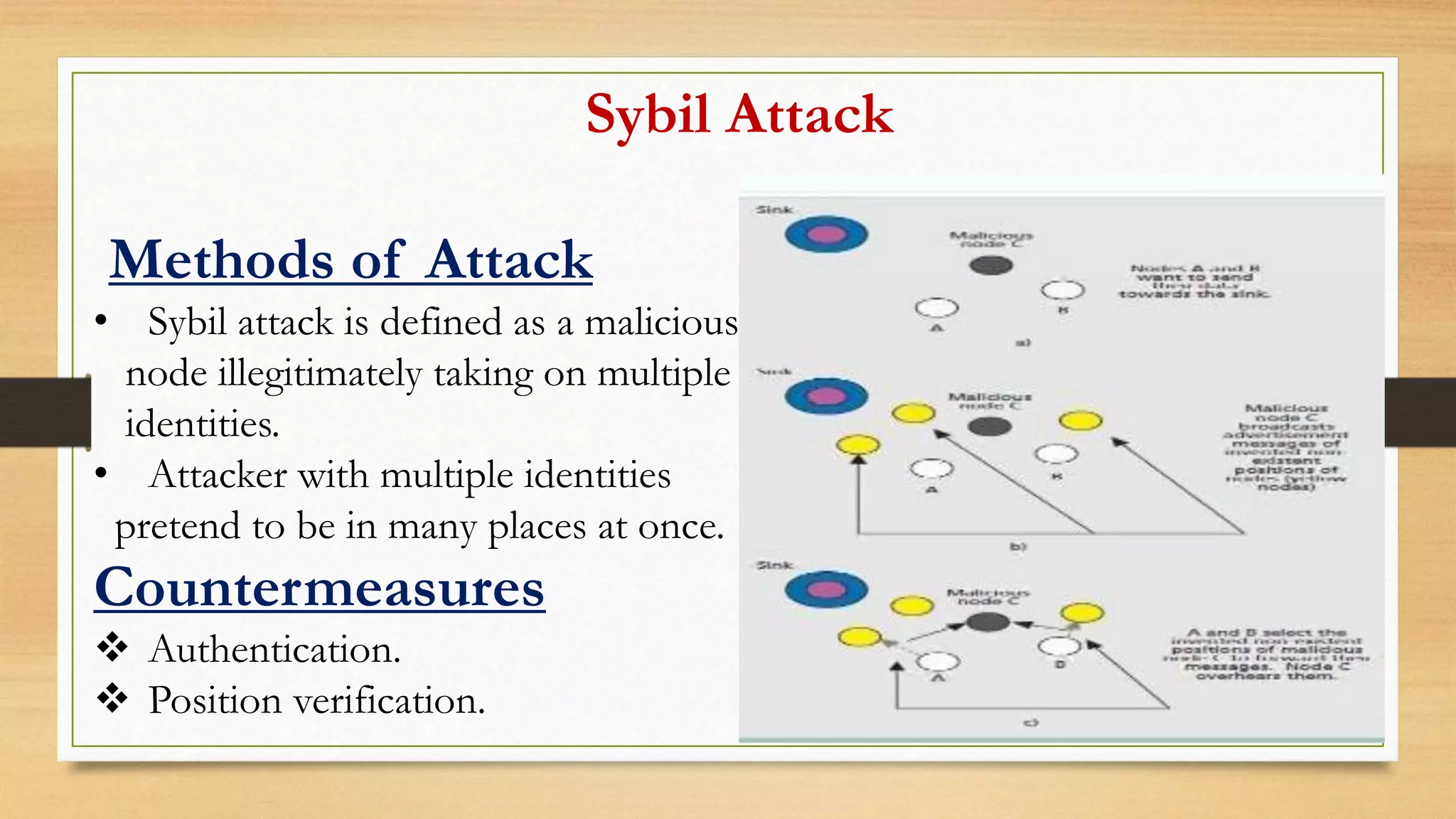
This document outlines securing underwater wireless communication networks. It discusses the necessity of underwater communication networks (UWCNs) due to limitations of wired networks underwater. It describes various attacks on UWCNs like jamming, wormhole attacks, and selective forwarding. It proposes countermeasures like spread spectrum techniques and multipath routing. The document also discusses requirements for secure UWCNs like authentication, confidentiality, and integrity. It proposes mechanisms for secure time synchronization, localization, and routing in UWCNs. Applications of UWCNs include search and rescue missions, environmental monitoring, and marine archaeology.