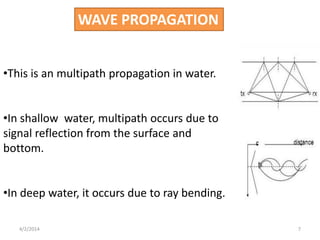
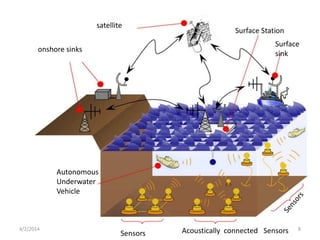
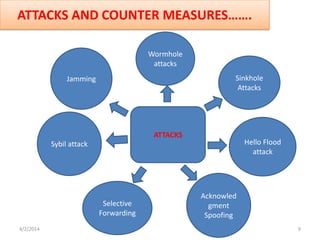
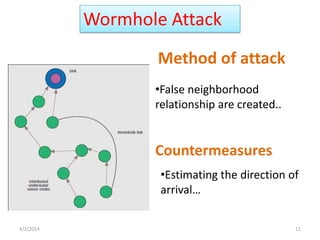
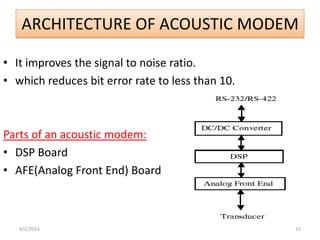
This seminar presentation discusses underwater wireless communication technology. It provides an introduction and history of underwater acoustics, describes the technology including how acoustic signals propagate underwater and are used to transmit data. It also discusses attacks such as jamming and wormholes that can occur underwater, and necessary security countermeasures. Finally, it outlines the necessity of underwater wireless communication for applications like pollution monitoring and search and rescue, as well as advantages and disadvantages compared to wired solutions.