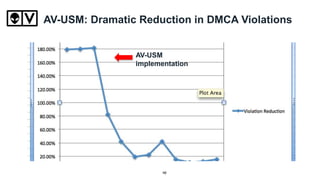
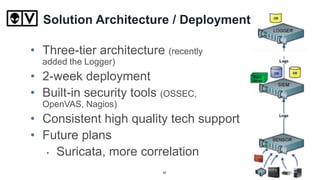
The document discusses the security challenges faced by colleges and universities, specifically focusing on Marquette University's approach to unified security management. It highlights the institution's decentralization, resource limitations, and the successes achieved through open-source security tools, including a significant reduction in DMCA violations and improved incident response. Key benefits of this approach include centralized visibility, customization, and the scalability of security solutions tailored to educational institutions.