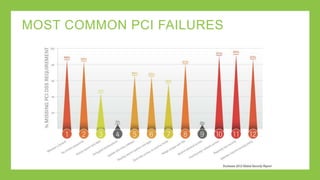
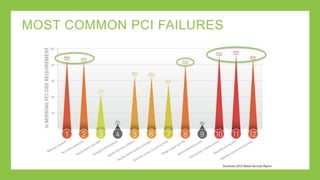
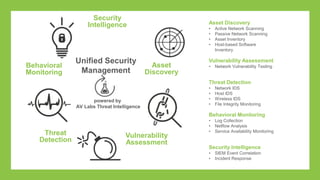
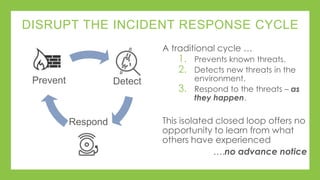
The document outlines a presentation on simplifying PCI DSS compliance using AlienVault USM, addressing key aspects such as compliance challenges, necessary capabilities, and the steps for maintaining compliance. It highlights the importance of monitoring network resources, documenting vulnerabilities, and maintaining security as part of daily operations. Additionally, the document emphasizes the use of various USM functionalities to track compliance and manage risk effectively.