Embed presentation
Downloaded 31 times
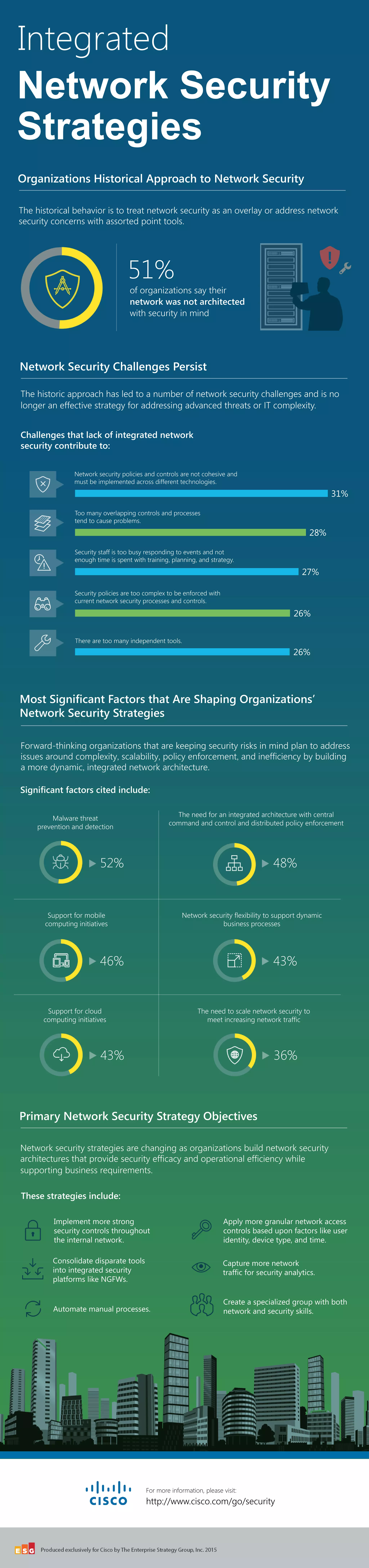

Organizations are moving towards more integrated network security strategies to address challenges posed by traditional approaches. Forward-thinking organizations see the need for dynamic, integrated network architectures that provide security efficacy, operational efficiency, and support business needs. Primary objectives of modern network security strategies include malware prevention and detection, support for mobile and cloud initiatives, and implementing strong security controls through an automated, integrated platform.
